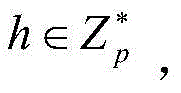Certificateless-based signcryption method and certificateless-based signcryption system
A technology without certificates and system parameters, which is applied in the field of certificateless signcryption methods and systems, and can solve problems such as low efficiency and poor security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
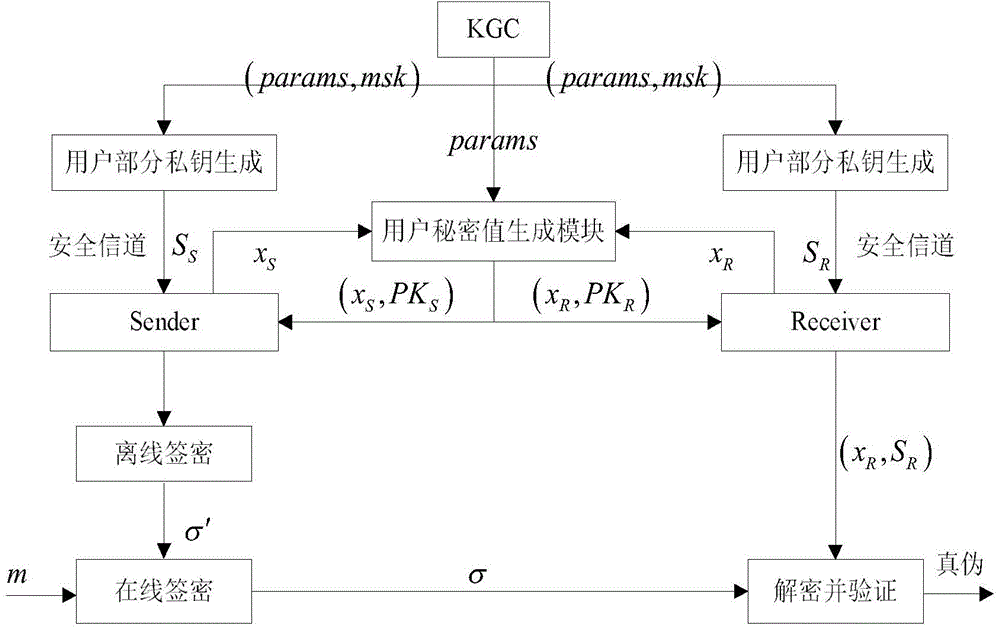
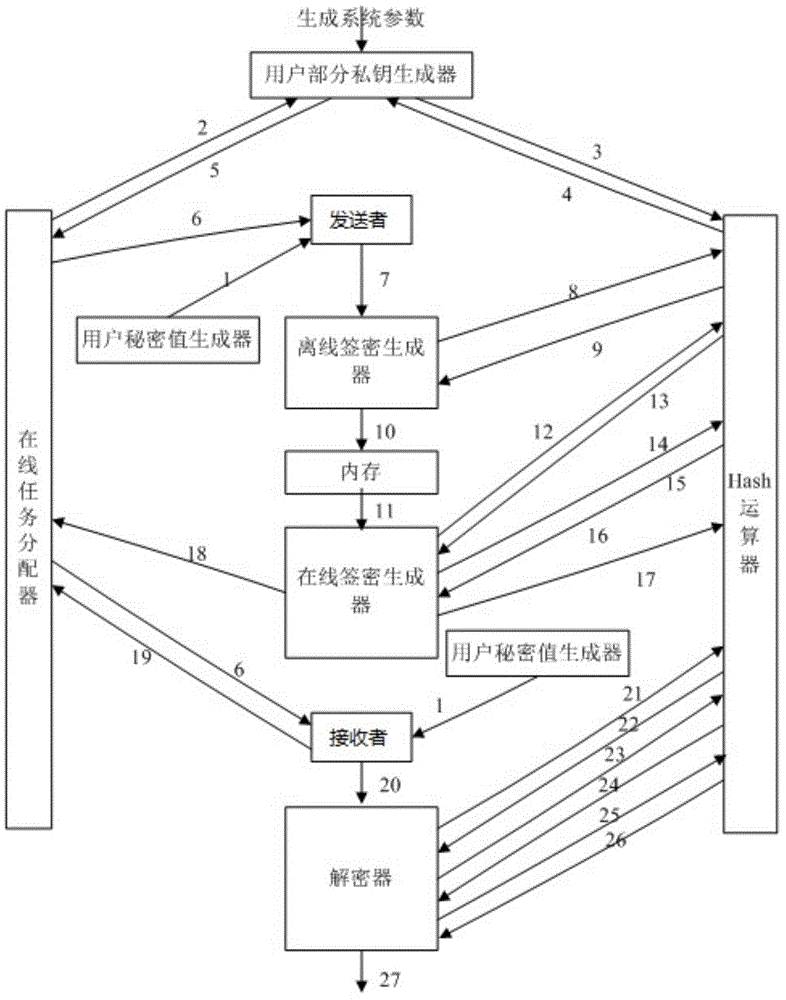
Embodiment 1
[0056] Let's first explain the related concepts:
[0057] Bilinear Pairing
[0058] Here we introduce the basic definition of a bilinear map and the properties it needs to satisfy.
[0059] Let P,Q∈G 1 , G 2 are two cyclic groups of order p, where p is a prime number and P is G 1 generator of . Define the bilinear map on two groups as: e:G 1 ×G 1 →G 2 , and satisfy the following properties:
[0060] Double mapping.e(aP,bP)=e(P,P) ab , for all are established.
[0061] Nondegenerate. There exists P such that e(P,P)≠1.
[0062] Computability. Efficient algorithms exist to compute e(P 1 ,P 2 ), where P 1 ,P 2 ∈G 1 .
[0063] It can be noticed that the bilinear pairing operation is commutative, because e(aP,bP)=e(P,P) ab =e(bP, aP).
[0064] 2. Difficult Problem Assumptions
[0065] Definition 1CDH (Computational Diffie-Hellman)-Problem: Given a p-order cyclic group G 1 , where p is a prime number and P is G 1 the generator of , then the group G 1 The CDH-p...
Embodiment 2
[0128] Embodiment 2 is basically the same as Embodiment 1, the difference is that the secure channel is constructed by a symmetric cryptographic algorithm, step 27, Bob verifies the equation e(P pub +q A P,Tt)=e(U,hP)e(U,PK A ), e(C 1 , P) α = W is not established, the message m is illegal, refuse to receive it.
Embodiment 3
[0130] Embodiment 3 is basically the same as Embodiment 1, except that the secure channel is constructed through a key exchange protocol.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com