Agent signcryption method and system
A proxy signcryption and proxy signature technology, which is applied in the field of proxy signcryption methods and systems, can solve the problems of a large amount of calculation of proxy signcryption schemes, easy to be impersonated, and difficult to verify proxy signcryption schemes, and achieves security. Guaranteed, removes the dependence of the secure channel, the effect of easy storage space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The present invention will be further described below with reference to the accompanying drawings and examples, but it is not intended to limit the present invention.
[0054] The entities involved in the technical solution of the present invention are as follows:
[0055] (1) Original sender: The entity entrusting the proxy sender to exercise the signcryption authority.
[0056] (2) Proxy sender: An entity that accepts the authorization of the original sender and sends a signcrypted message to the receiver on behalf of the original sender.
[0057] (3) Receiver: The recipient of the message sent by the proxy sender.
[0058] (4) Third party: When the proxy sender denies having sent a certain message to the receiver, the receiver can show evidence to the third party, and the third party will make a ruling.
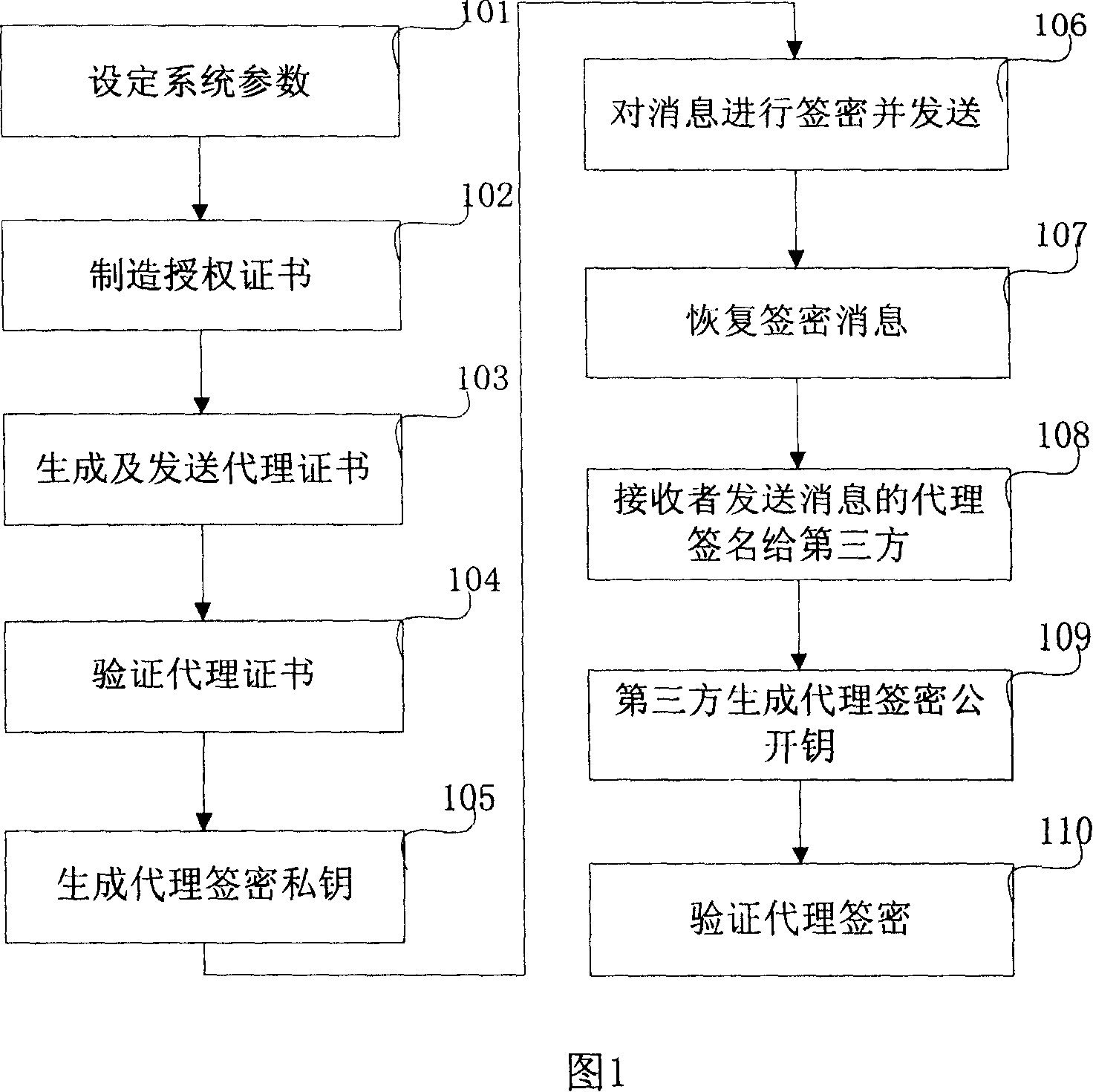
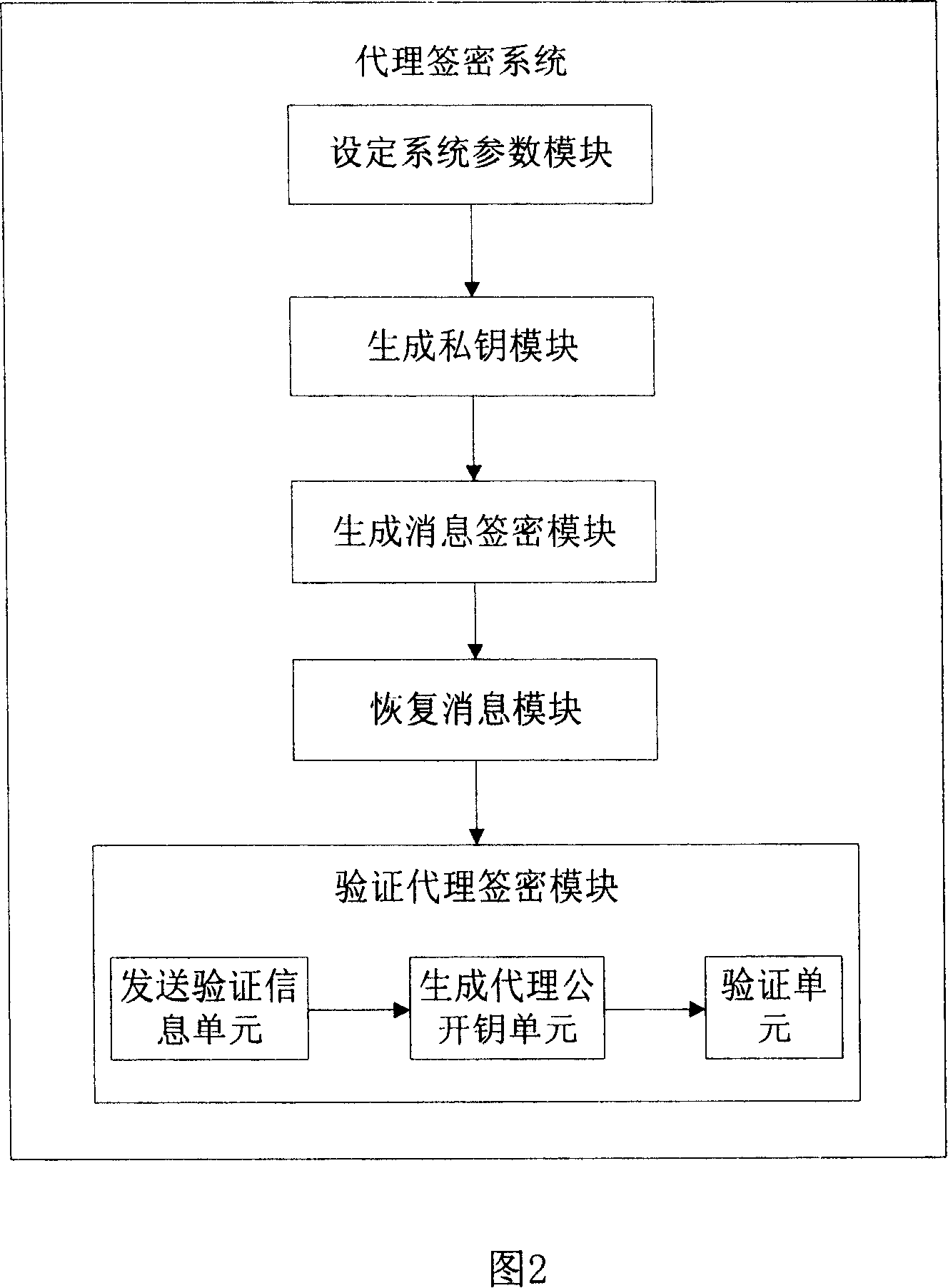
[0059] Referring to Fig. 1, the present invention provides a kind of method of proxy signcryption, and described method step is as follows:
[0060] Step A: Set ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com