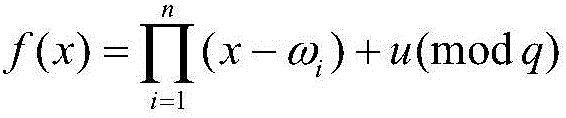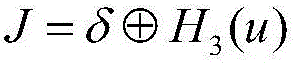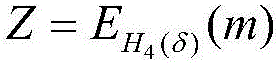Multi-receiver signcryption method based on keyless trusteeship problem of elliptic curve
An elliptic curve, multi-receiver technology, applied to the public key and key distribution of secure communication, which can solve the problems of key escrow, inability to obtain private keys, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0090] Glossary.
[0091] KGC: Key Generation Center, a trusted third party, is responsible for generating the public and private keys of the sender and receiver;
[0092] λ: the security parameter selected by the key generation center KGC;
[0093] q: the prime number selected by the key generation center KGC;
[0094] G q : The cyclic group selected by the key generation center KGC;
[0095] E: elliptic curve;
[0096] P: point on the elliptic curve E;
[0097] p: The order of point P, which is a large prime number;
[0098] s: cryptographic system master key;
[0099] ∈: limited domain symbol, such as y∈Z q * , indicating that y is Z q * an element in
[0100] h j : cryptographic one-way hash function, where j=0,1,2,3,4,5;
[0101] A→B: mapping from domain A to value domain B;
[0102] {0,1} * : A string of arbitrary length "0" or "1";
[0103] ×: Cartesian product;
[0104] Z q * : Non-zero multiplicative group based on prime number q;
[0105] m: plain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com