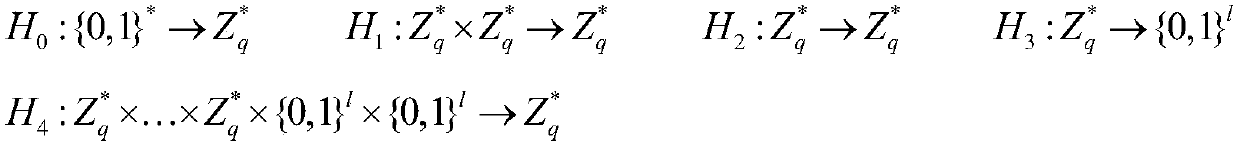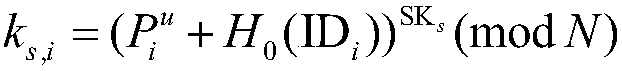A multi-receiver signcryption method that can explicitly verify the public key
A multi-receiver, receiver technology, applied to the public key and key distribution of secure communication, can solve the problems of being vulnerable to public key replacement attacks, unable to resist malicious KGC attacks, and existing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
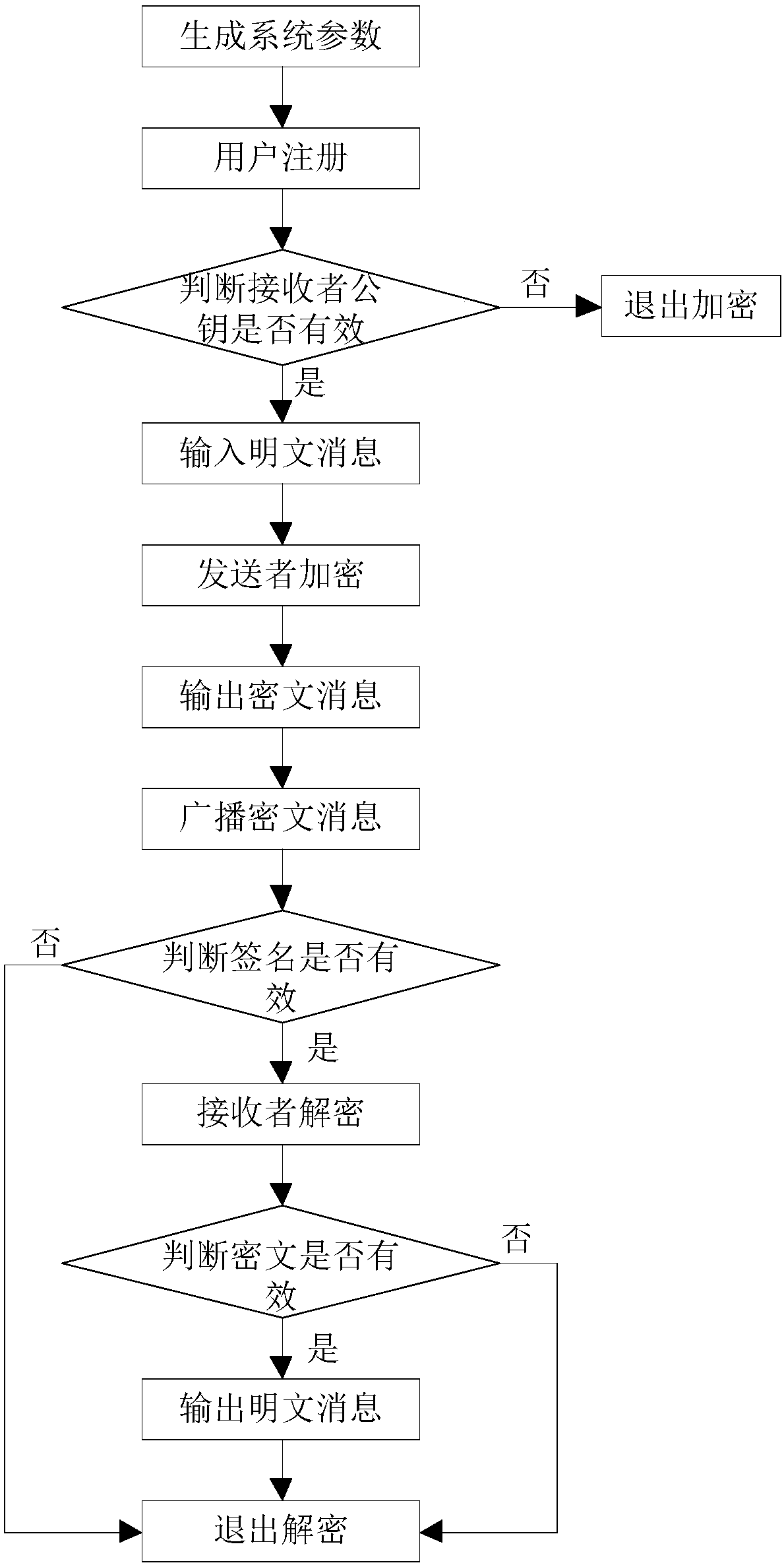
[0073] Attached below figure 1 The present invention is further described.
[0074] Step 1, generate system parameters.
[0075] The key generation center KGC randomly selects a public modulus N=a*b according to the system security parameters, where a and b are large prime numbers of equal length, and * represents the multiplication operation of numbers. Randomly select a large prime number q, and q is an integer greater than the public modulus N. Select a public exponent u that satisfies the mutual prime between u and φ(N), where φ(N) represents the Euler function, φ(N)=(a-1)*(b-1). The cryptographic system master key d is randomly selected to satisfy u*d=1(modφ(N)), where mod represents a modulo operation. Choose a public integer g such that g has the largest multiplicative order. The length of the plaintext message M is l, and five cryptographic one-way Hash functions are constructed, recorded as:
[0076]
[0077] The key generation center KGC constructs and disc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com