Secure certificateless hybrid signcryption method without pairing
A certificateless, symmetric encryption algorithm technology, applied in the field of certificateless hybrid signcryption, can solve problems such as low efficiency, achieve the effect of improving computing efficiency, eliminating computing consumption, and improving security level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
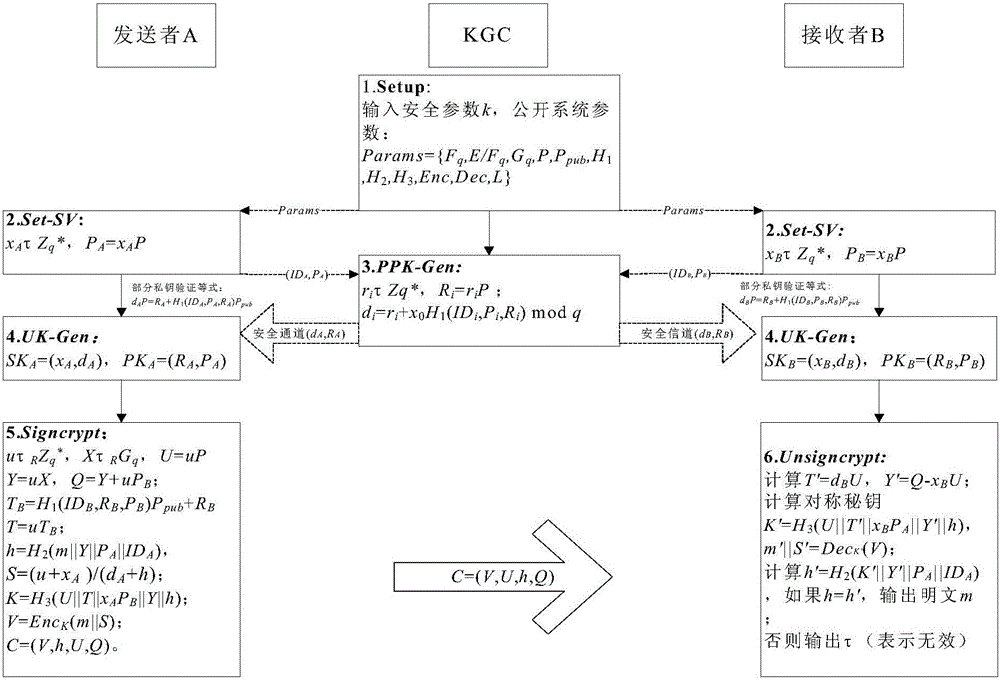
[0041] Glossary.
[0042] KGC: Key Generation Center;
[0043] Setup: system establishment;
[0044] Set-SV: secret value setting;
[0045] PPK-Gen: partial key generation;
[0046] UK-Gen: user key generation;
[0047] Signcrypt: sign encryption;
[0048] Unsigncrypt: decrypt signcryption;
[0049] k: system security parameters;
[0050] Z + : group of positive integers;
[0051] q: a k-bit prime number;
[0052] f q : a finite field containing q elements;
[0053] E / F q : In the finite field F q An elliptic curve E selected above;
[0054] G q : additive cyclic group;
[0055] Z q * : Integer multiplicative group modulo q;
[0056] P: additive cyclic group G q generator of
[0057] x 0 : The random number selected by KGC;
[0058] msk: system master key;
[0059] L: positive integer, indicating the length of the symmetric key space;
[0060] n: positive integer, indicating the length of the plaintext;
[0061] P pub : system master public key;
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com