Method and system for detecting network security
A security and network technology, applied in the field of network security, which can solve the problems of inaccurate results, incomplete model description, and failure to consider the human behavior of network attacks, and achieves enhanced description capabilities, a wide range of applications, and high accuracy. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
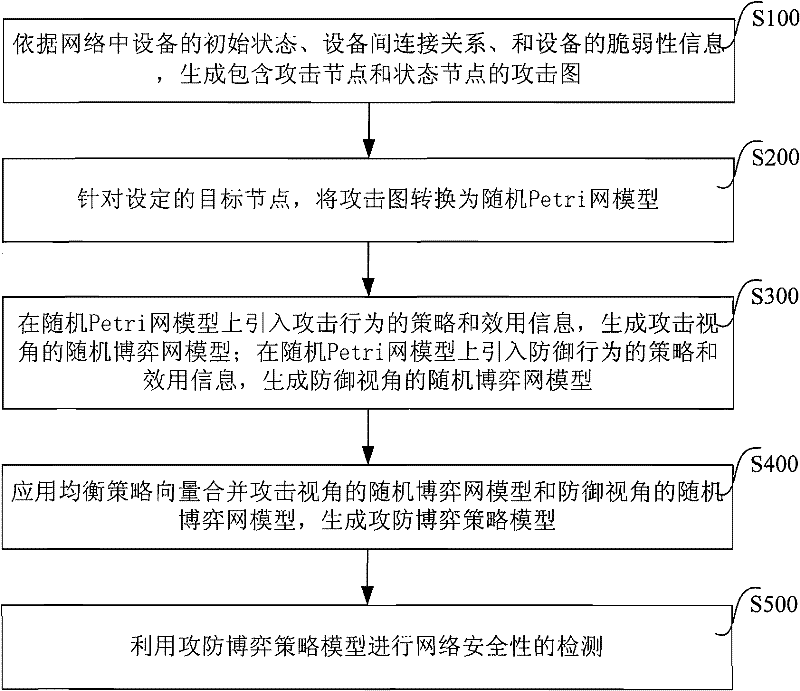
[0039] Specific examples are as follows.
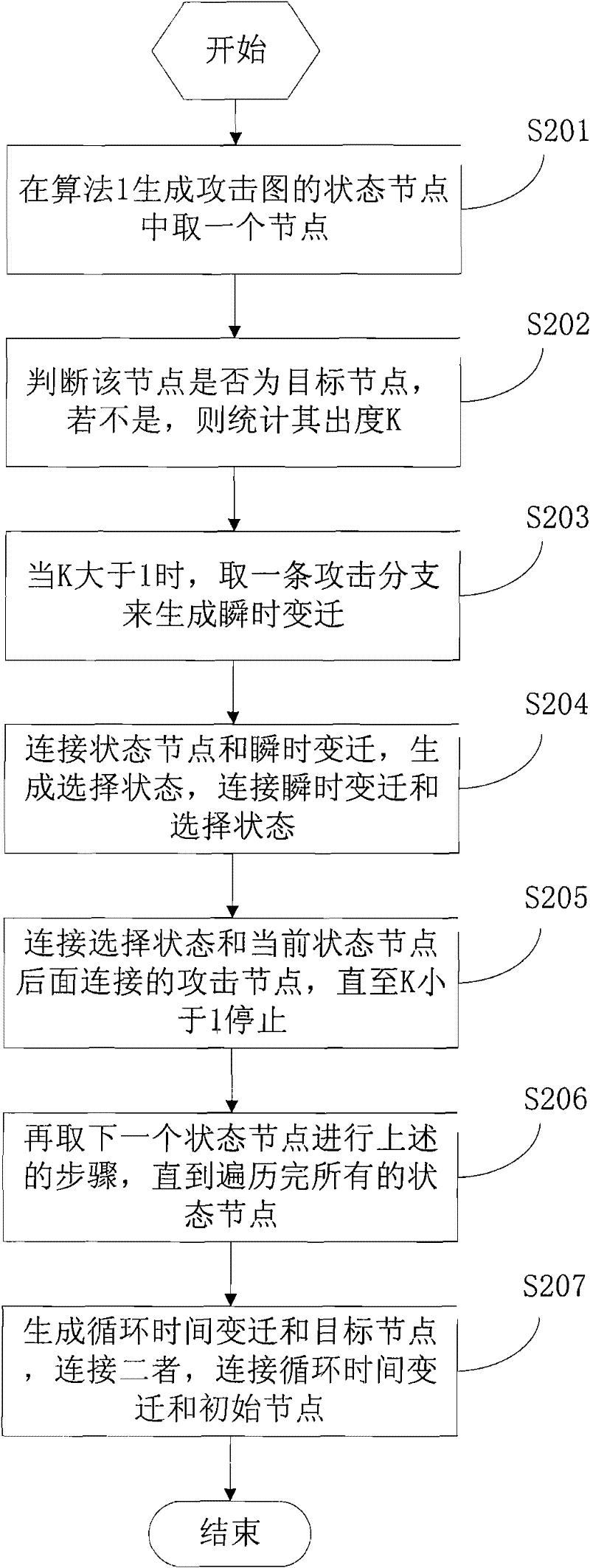
[0040] Algorithm 1 - attack graph generation algorithm, such as figure 2 shown.
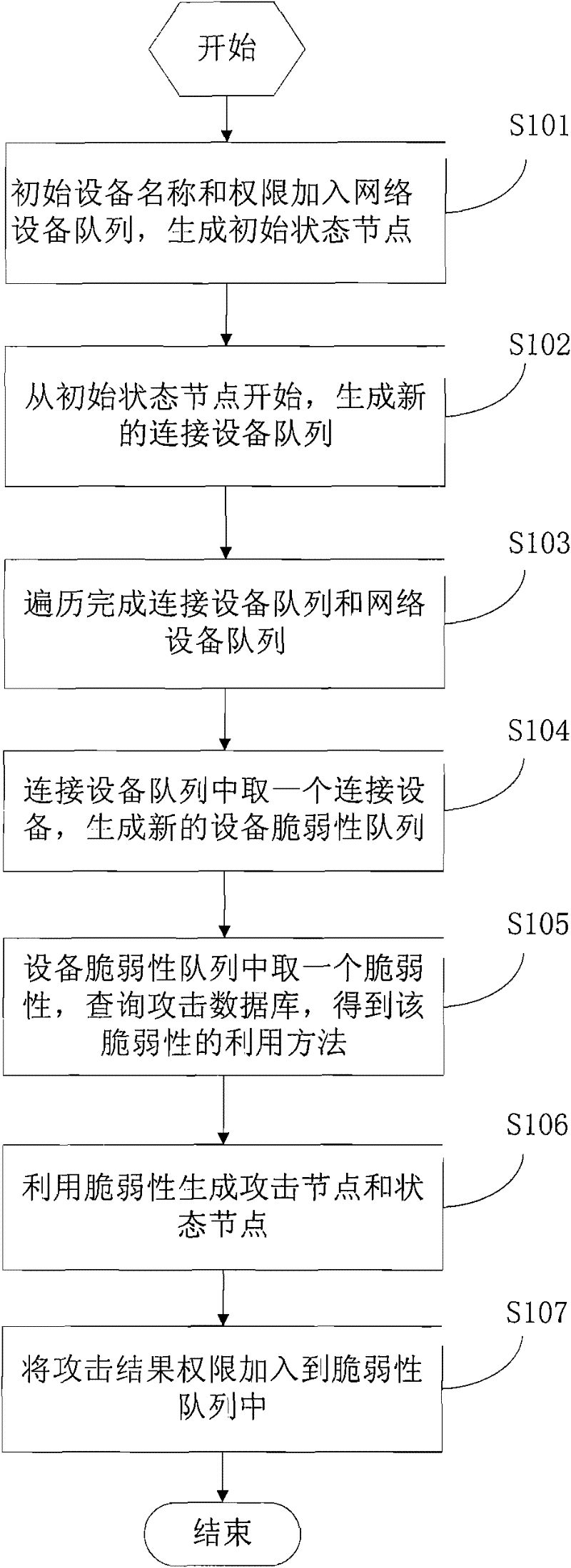
[0041] Step S101, first generate an attack graph describing the attack relationship, add the initial device name and authority to the network device queue, and generate an initial state node at the same time.
[0042] Step S102, start from the initial state node, take a device and its authority in the network device queue, and generate a new connected device queue.
[0043] Step S103, query the device connection relationship according to the current device name, obtain all connected device names of the device and add them to the connected device queue, and add the connected device names not in the network device queue to the network device queue.
[0044] Step S104, taking a connected device from the connected device queue to generate a new device vulnerability queue.
[0045] Step S105, take a vulnerability from the device vulnerability queue, query...
specific Embodiment approach 1
[0208] In the first specific embodiment, the network security detection module 500 is further used to
[0209] Calculate the steady-state parameters of the attack-defense game strategy model, the steady-state parameters are the selection of the attack path, and generate a set of attack target locations;
[0210] For the attack-defense game strategy model, for the stochastic Petri net model, there is an arc (p i ,t)(t,p i+1 ), and the loopholes between devices cannot be exploited, then delete the arc (p i ,t)(t,p i+1 ), otherwise, remain unchanged; traverse all transitions, and delete isolated transitions; attack behavior a according to the transitions given in the attack information i The relationship with the current position determines whether there is an attack relationship. If the attack behavior can act on position p, and the set of previous attack target positions of position p is not empty, then add the mark a to all transitions in the set of previous attack target p...
specific Embodiment approach 2
[0220] In the second specific embodiment, the network security detection module 500 is further used to
[0221] Calculate the average number of signs m in each position in the steady state of the attack-defense game strategy model i ;
[0222] Establish the node set {IPi} that appears in the possible attack path, and mark the same node {IPi(1,...,n j )};
[0223] Calculate the vulnerability weight σ according to the following formula i And sort the network nodes according to the vulnerability weight;
[0224] σ i = Σ j = 1 n j m i j
[0225] Among them, IPi(1,...,n j ) means the nth j The node IPi under the path.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com