Network spoofing performance evaluation method based on dynamic Bayesian attack graph
A dynamic Bayesian and effectiveness evaluation technology, applied in the field of cyberspace security, can solve problems such as lack of, deception defense effectiveness evaluation method, single defense level, etc., to achieve the effect of ensuring usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below in conjunction with the implementation examples and the accompanying drawings.
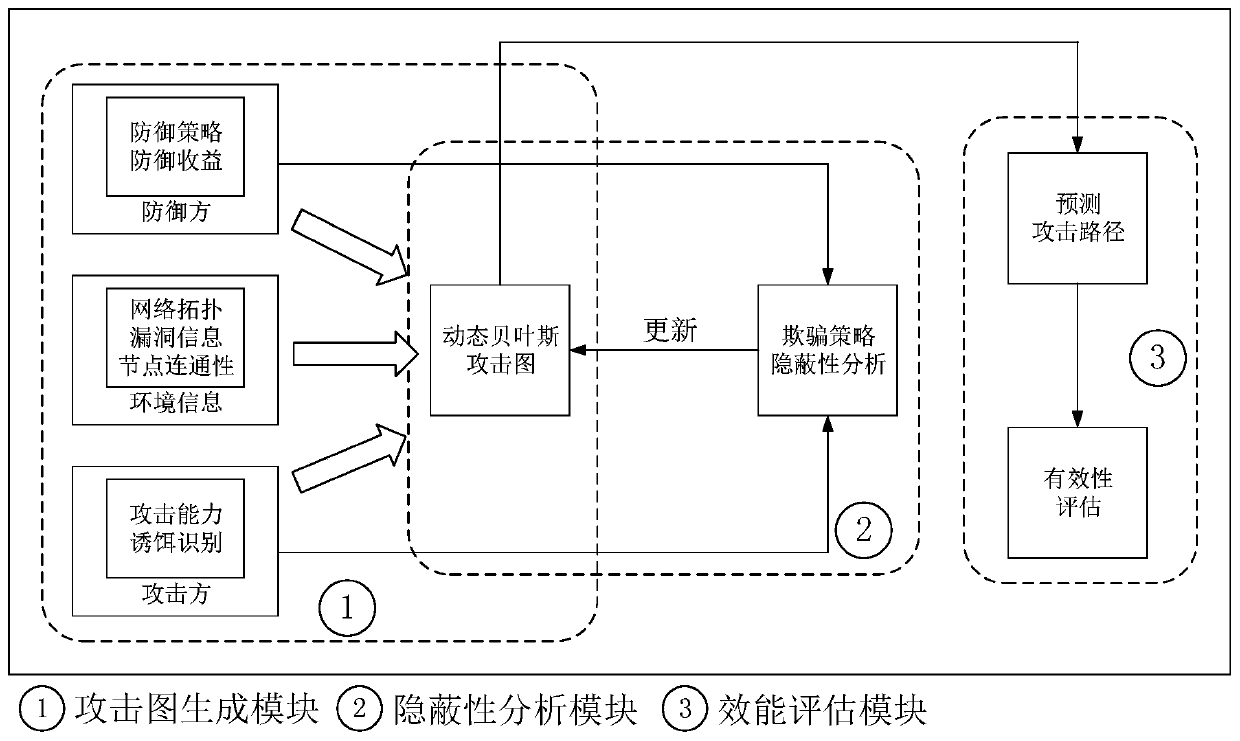
[0030] Step 1: Before evaluating network deception, attack graph modeling of the target network is first performed.
[0031] Use the Common Vulnerability Scoring System CVSS to conduct threat analysis on the vulnerabilities existing in the network;
[0032] For example, according to the formula for calculating the probability of successful exploitation of a vulnerability, the probability of successful exploitation of the vulnerability numbered CVE-2009-0180 is: P s =0.5, wherein, the vulnerability exploiting method AV is Network, the access complexity AC is Low, no authentication of the attacker is required, that is, AU is None.
[0033] After determining the network topology, node connectivity and other elements, traverse the complete node state and attack path to realize the construction of Bayesian attack graph.
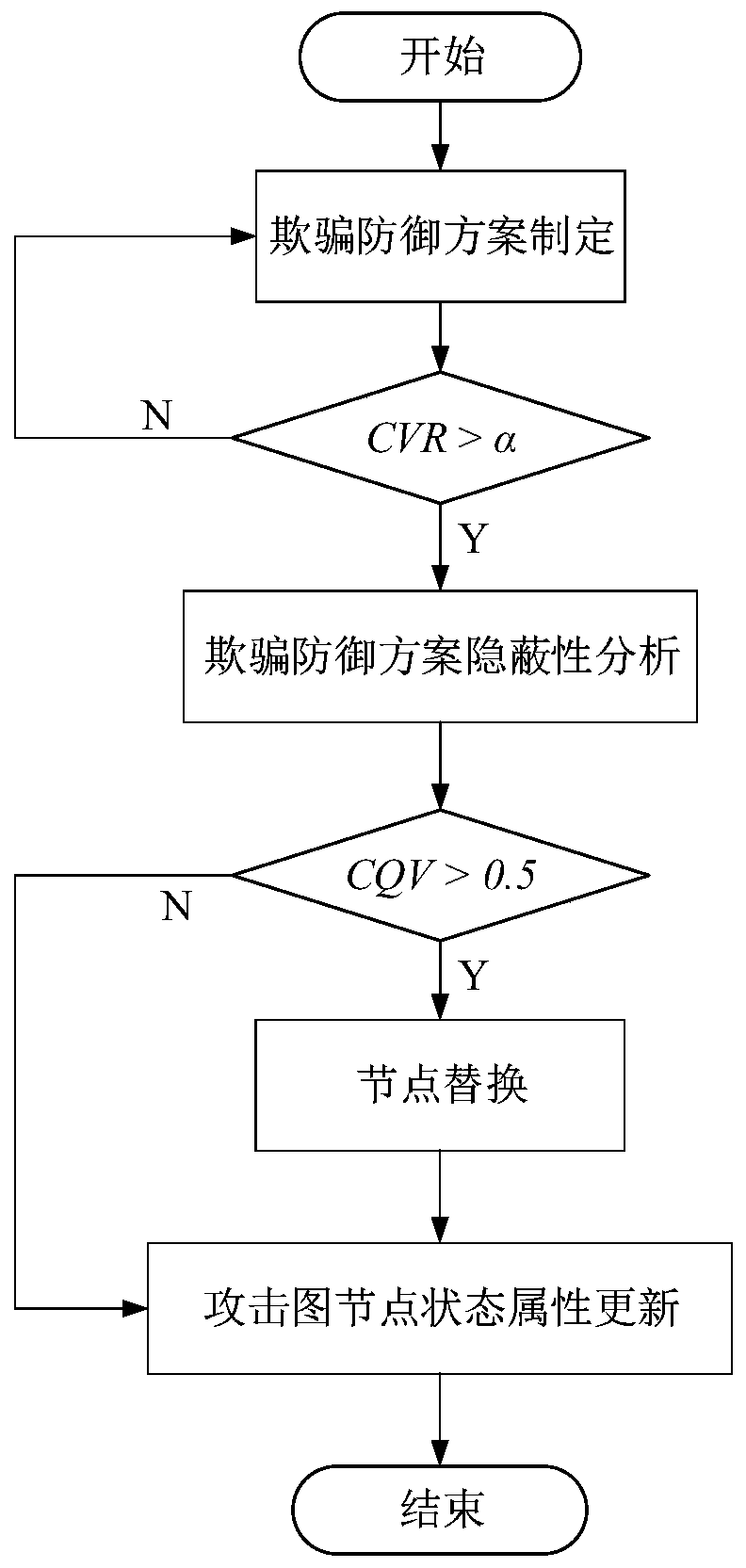
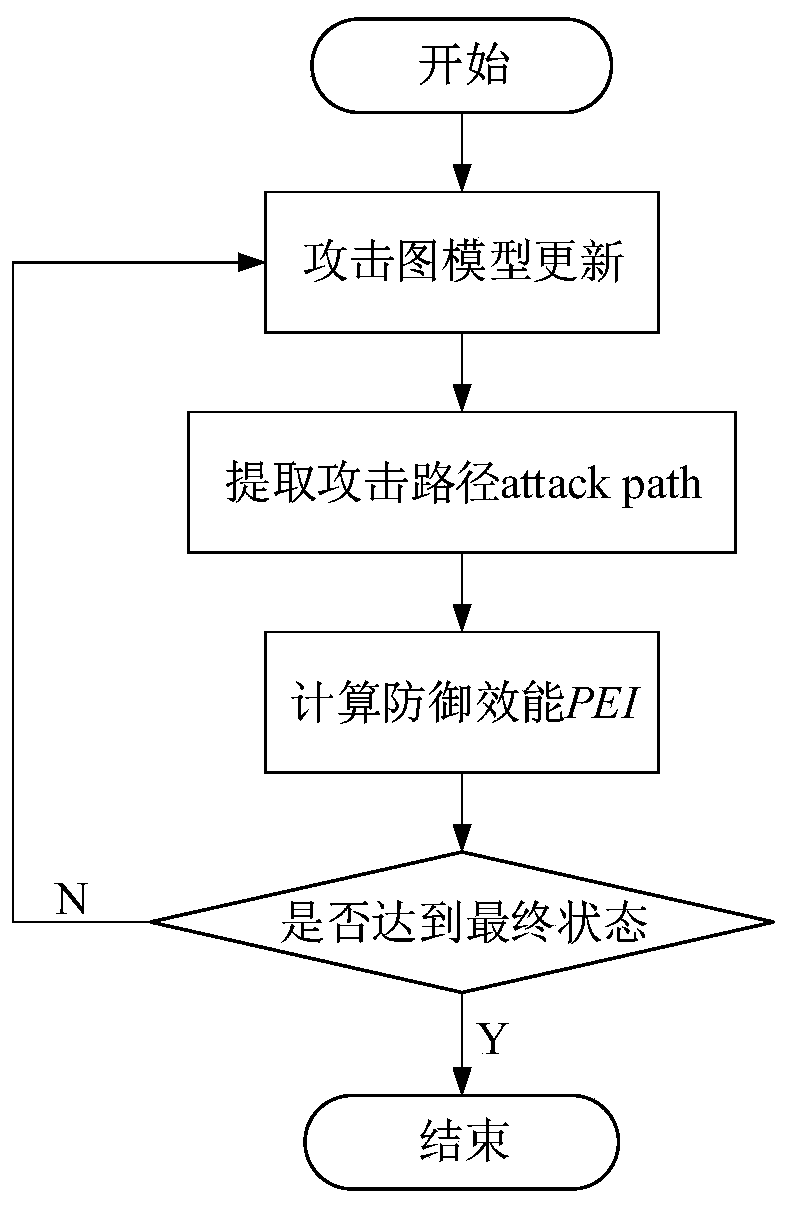
[0034] Step 2: Ver...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com