Quantitative evaluation method of network security situation based on attack graph
A technology for network security and quantitative evaluation, applied in the field of information security, can solve problems such as subjectivity, inability to overcome the acquisition of Bayesian network prior probability, and non-scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0075] According to the above technical solution, the technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings and implementation examples.
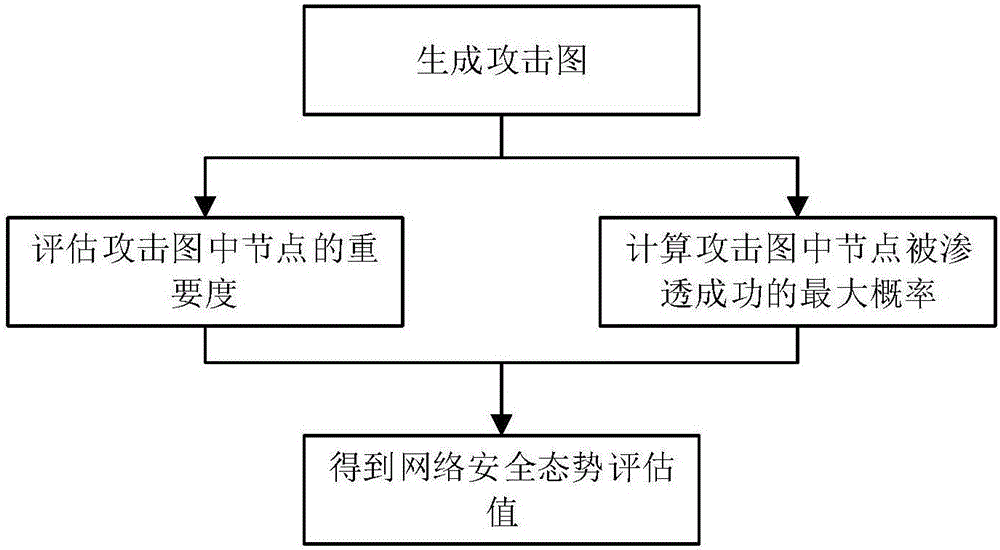
[0076] The network security situation assessment method based on the attack graph proposed by the present invention is used to evaluate the network security situation, and its operation process is as follows figure 1 As shown, the specific operation steps are:
[0077] Step 1: Generate an attack graph. Specifically:
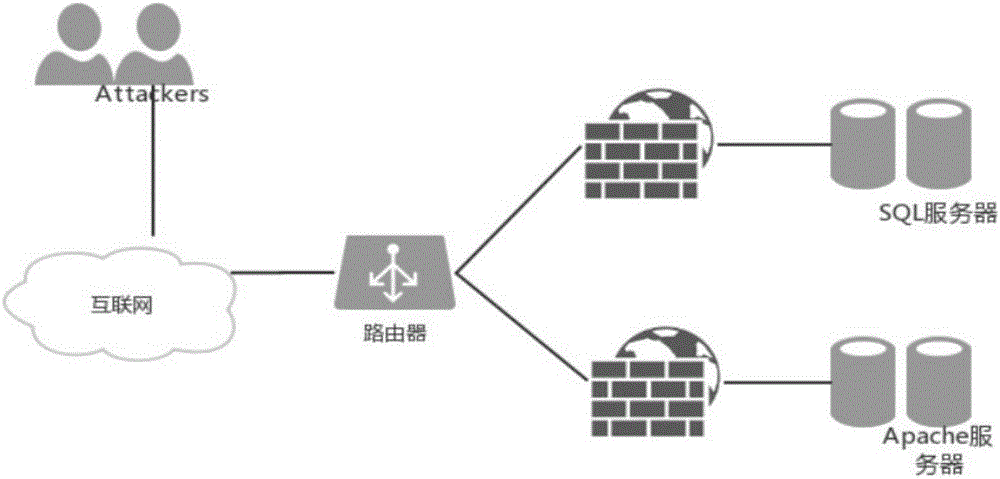
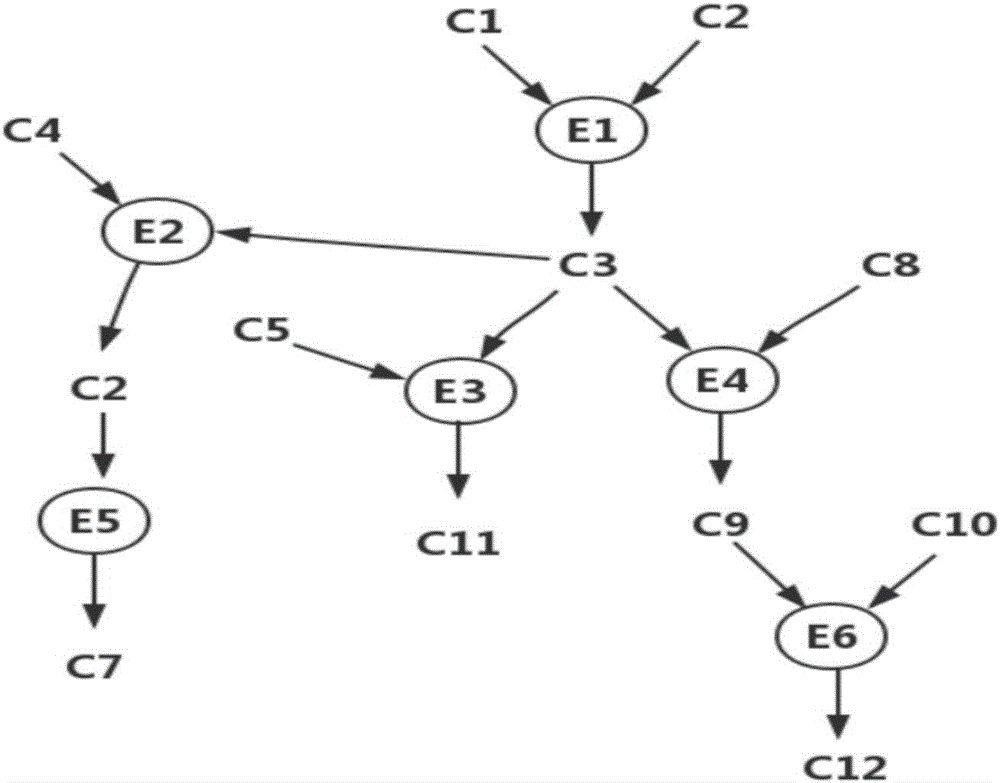
[0078] Step 1.1: The network architecture diagram used in the experiment is as follows figure 2 As shown, the CVE name of the vulnerability in the network is obtained through the X-san scanning tool, and the vulnerability information is searched in the CVE-compatible database to form a list of vulnerability information, which is represented by the symbol VulExploitList, as shown in Table 1. Then, for each vulnerability in the vulnerability information li...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com