System for generating assaulting chart facing network safety alarm incident
A network security and generation system technology, applied in the field of attack graph generation system, can solve the problems of potential attack path loss, inability to fully contain knowledge, etc., and achieve the effect of easy engineering implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The embodiments of the present invention are described in detail below in conjunction with the accompanying drawings: this embodiment is implemented on the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to the following the described embodiment.
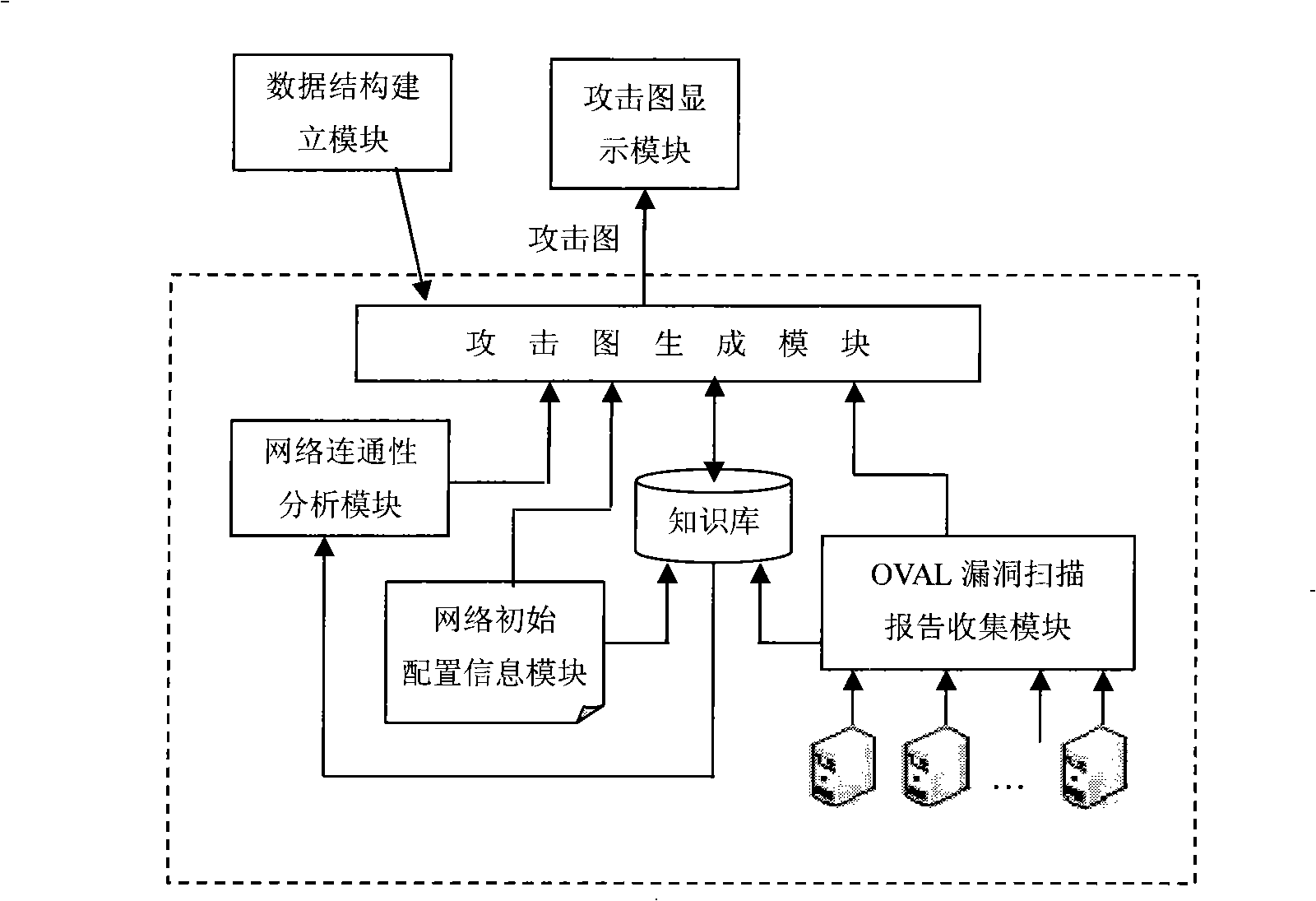
[0040] Such as figure 1 As shown, the present embodiment includes: a network initial configuration information module, an OVAL vulnerability scanning report collection module, a knowledge base, a network connectivity analysis module, a data structure establishment module, an attack graph generation module and an attack graph display module, wherein:
[0041] The network initial configuration information module receives the network topology, gateway filtering rules, etc. input by the user, and stores them in the knowledge base;
[0042] The OVAL vulnerability scanning...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com