Risk monitoring method for a physical protection system of a key infrastructure
A technology for physical protection and infrastructure, applied in the field of risk monitoring of key infrastructure physical protection systems, can solve problems such as immature risk monitoring methods, and achieve the effect of improving effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
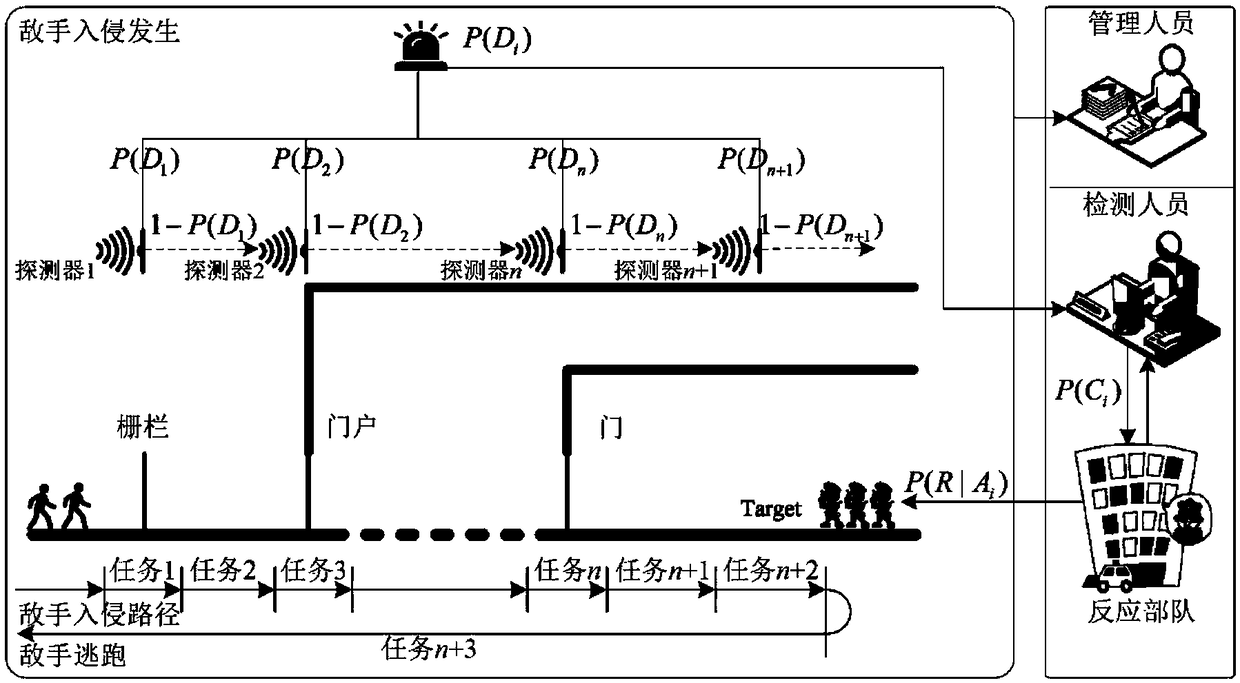
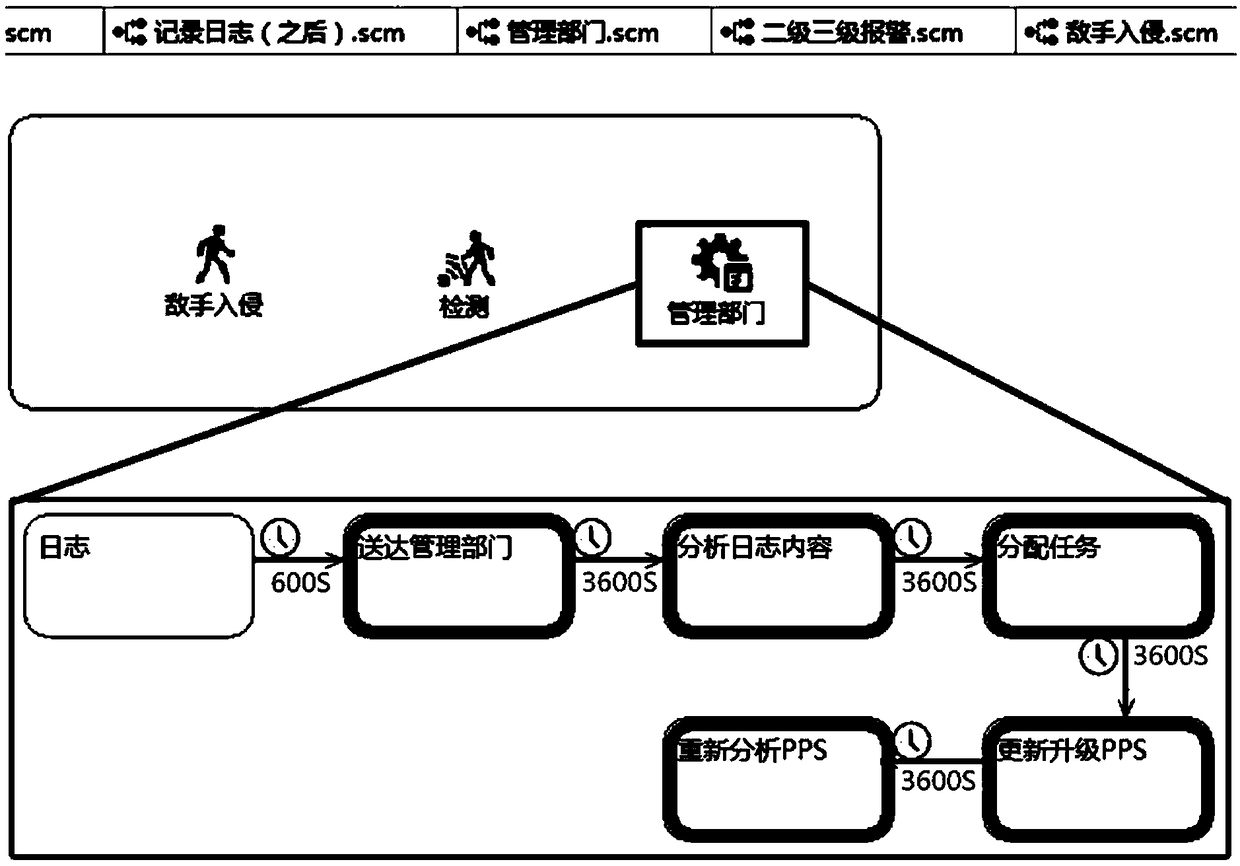
[0056] This embodiment discloses a risk monitoring method for a physical protection system of critical infrastructure. The general process of the method of the present invention is as follows: analyze physical protection system regulations, modularize the regulations, sort out external events and internal events contained in the regulations; establish physical protection system risk knowledge base; establish physical protection system risk interaction simulator.
[0057] The present invention adopts following technical scheme:
[0058] 1. Carry out procedure analysis and modular processing on the physical protection system;
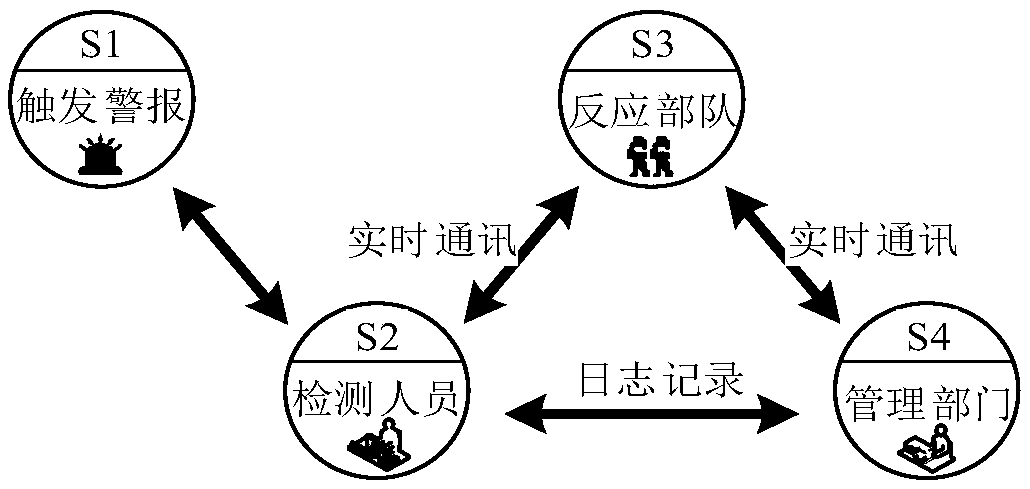
[0059] The physical protection system effectively links management personnel, testing personnel, and response forces through risk monitoring to achieve real-time linkage, comprehensive information exchange, and emergency response.
[0060] Key personnel involved in the physical protection system include critical infrastructure managers, detection personn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com