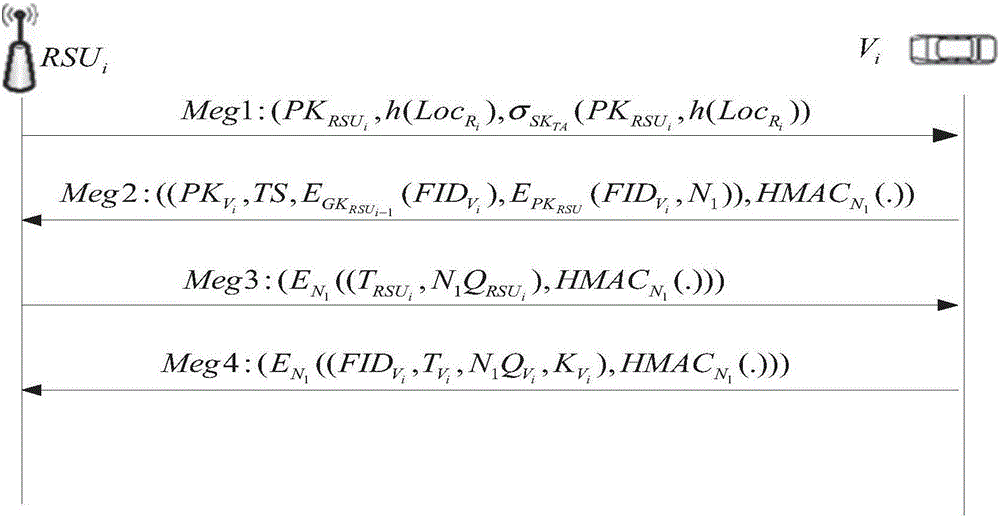Method for designing vehicle network group negotiation communication protocol
A communication protocol and design method technology, applied in secure communication devices and key distribution, can solve problems such as inefficiency and insecurity, and achieve the effects of reducing workload, reducing the number of authentication times, and eliminating single-point failure problems.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
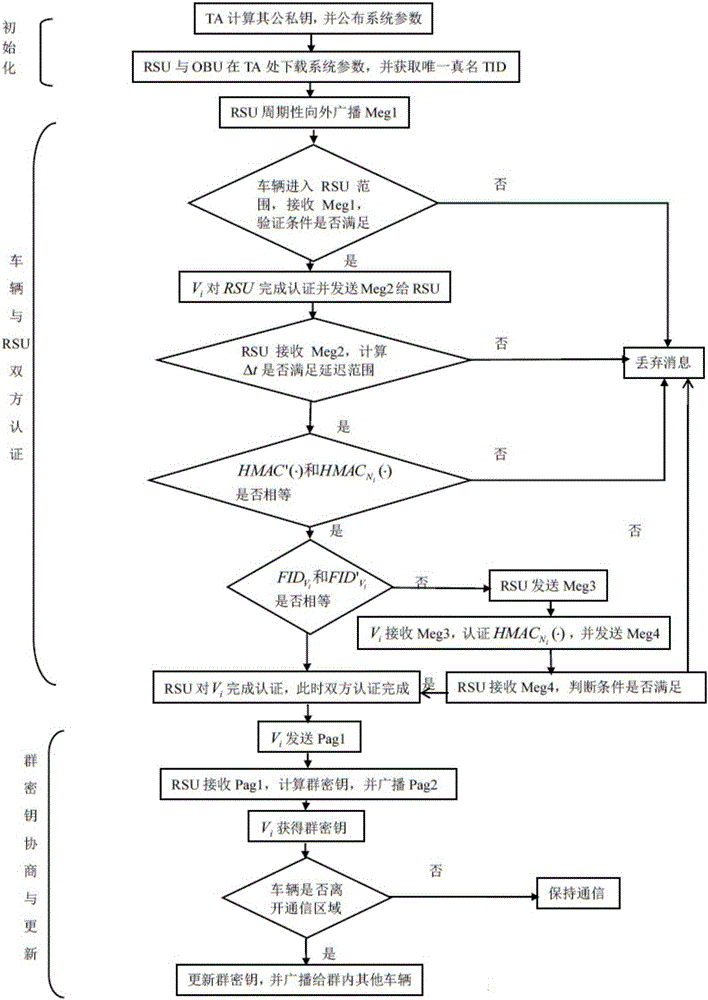
[0041] Method of the present invention mainly comprises following four parts:
[0042] 1. System initialization
[0043]The trusted authentication center TA selects parameters and generates its own public and private keys with random numbers, defines a hash function and a secure symmetric cryptographic algorithm, and then announces the system parameters and downloads the system parameters to the roadside unit RSU and the on-board unit OBU.
[0044] 2. Both vehicle and RSU certification
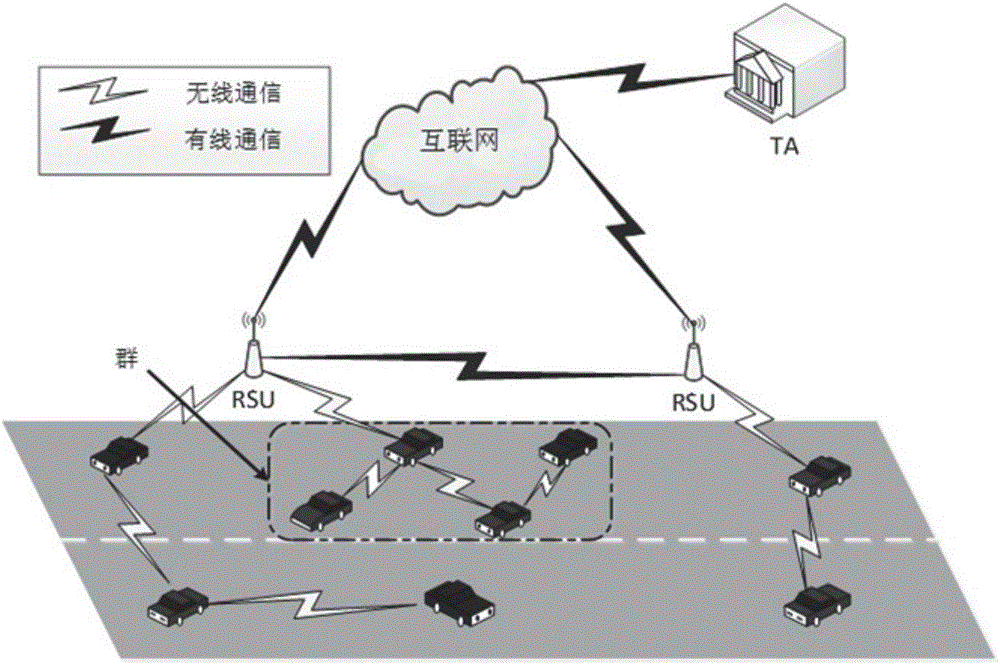
[0045] On the road, groups are formed according to geographic regions centered on RSUs with a wide range of communication and strong computing capabilities. In order to communicate with nearby vehicles and RSUs, vehicle users need to perform identity authentication and key negotiation to join the group after entering the communication range of the roadside unit. In this protocol, vehicles and RSUs self-authenticate each other without the participation of a third-party TA. At the same time, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com