Architecture accessing trusted network for tolerating untrusted components and access method thereof
A network access, untrusted technology, applied in the field of trusted network access architecture, can solve the problems of complex protocols, restricting TNC applications, and not considering the security of policy enforcement points, and achieves improved flexibility and convenience. Achievable, safety-enhancing effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
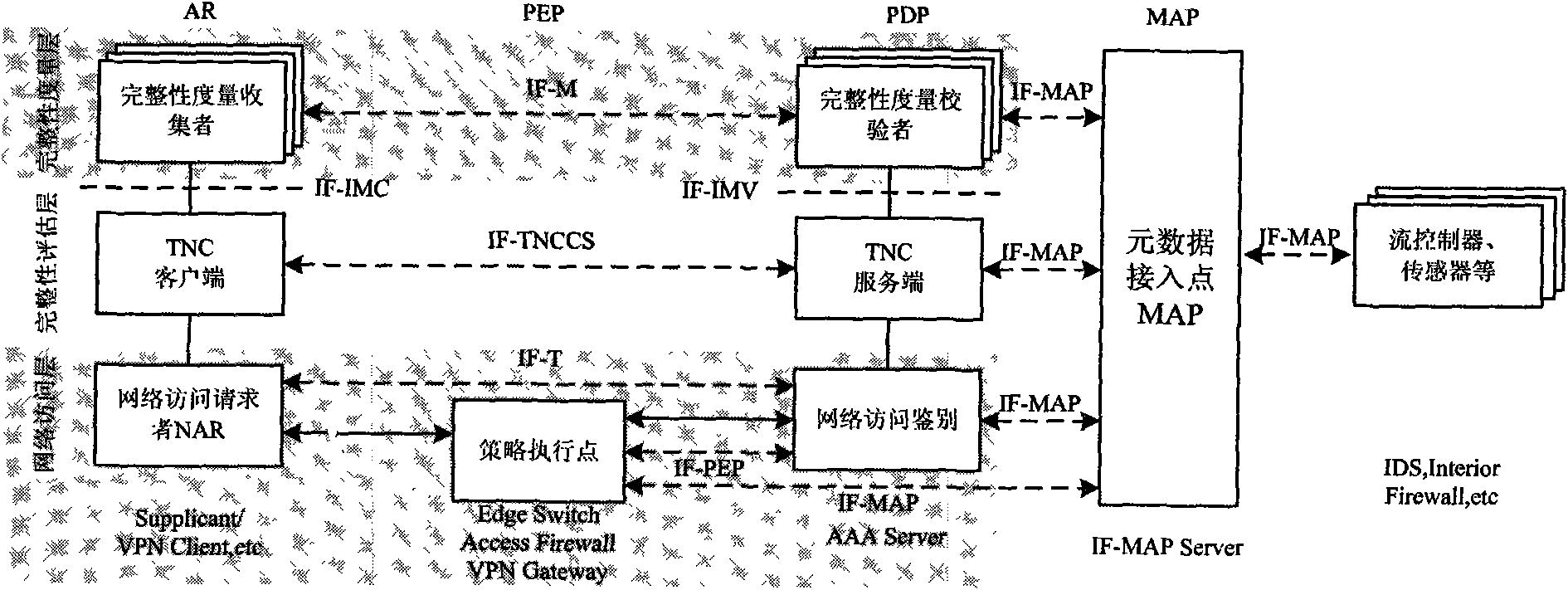
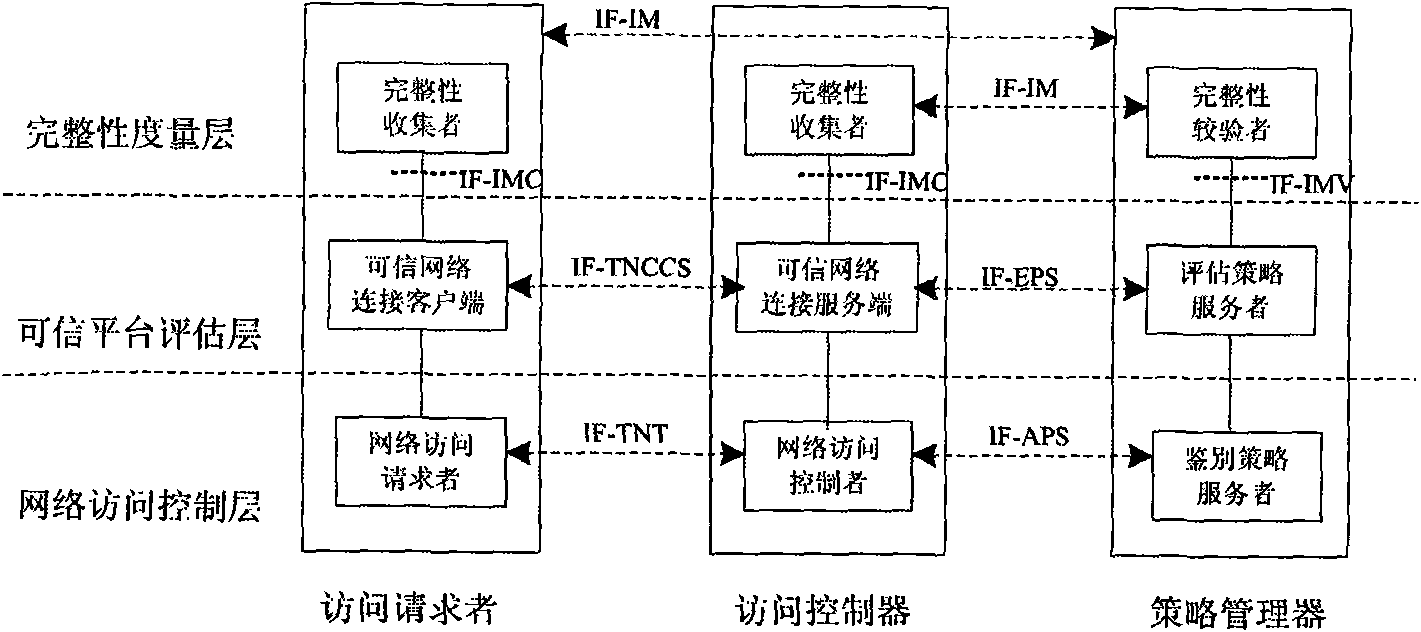
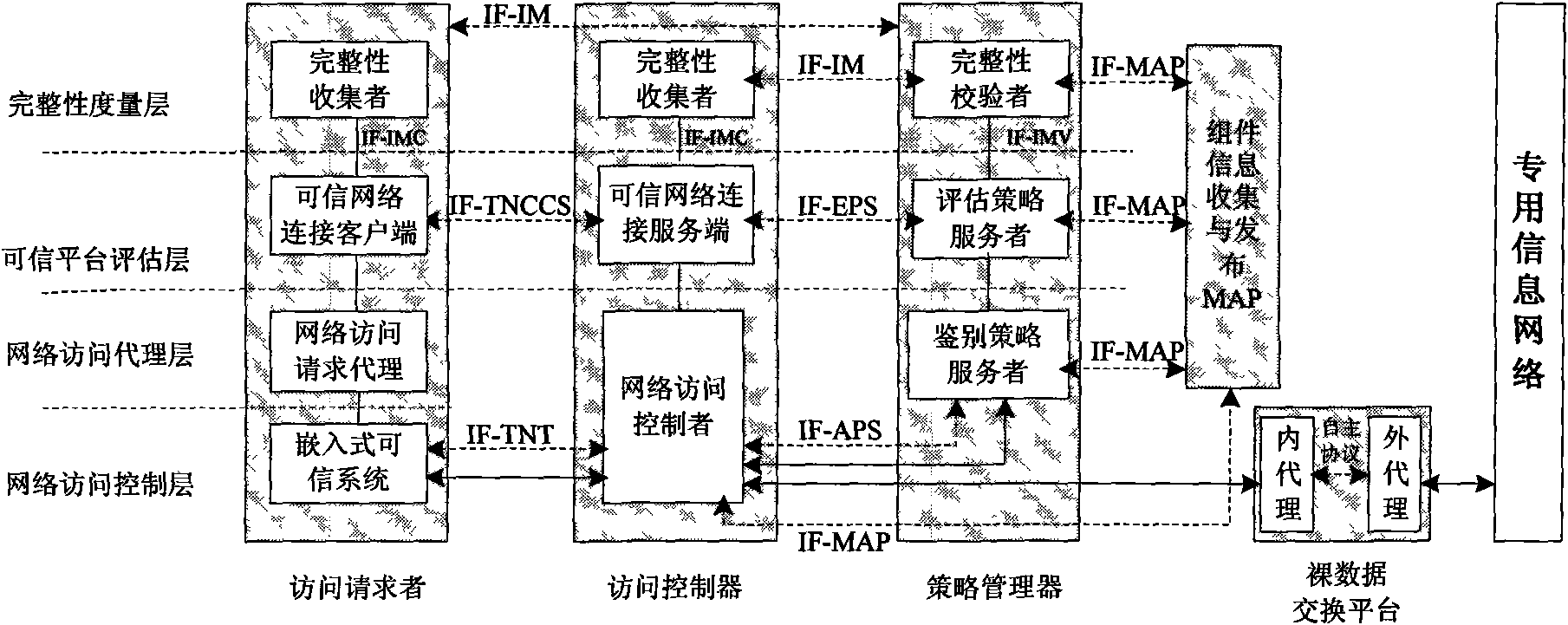
[0069] The following takes the public security information network as an example to illustrate the specific network deployment architecture and working principles of the trusted network access architecture that can tolerate untrusted components when accessing the public security information private network. Figure 5 shown. The entire architecture is divided into two parts: the access network and the public security information network. The public security information network and the access network exchange data through a data security exchange platform to prevent security attacks based on protocol loopholes or protocol defects and ensure the security of the public security information network. The access network includes trusted mobile terminals, trusted access gateways, authentication management servers, and audit monitoring servers.
[0070] The terminal is a mobile terminal device such as a mobile phone or a notebook equipped with a secure SIM card or PCMCIA card. These se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com