Advanced persistent threat attack detection method and device
An attack detection and persistence technology, applied in the field of communications, can solve the problems of difficult detection of defense systems and complex attack methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
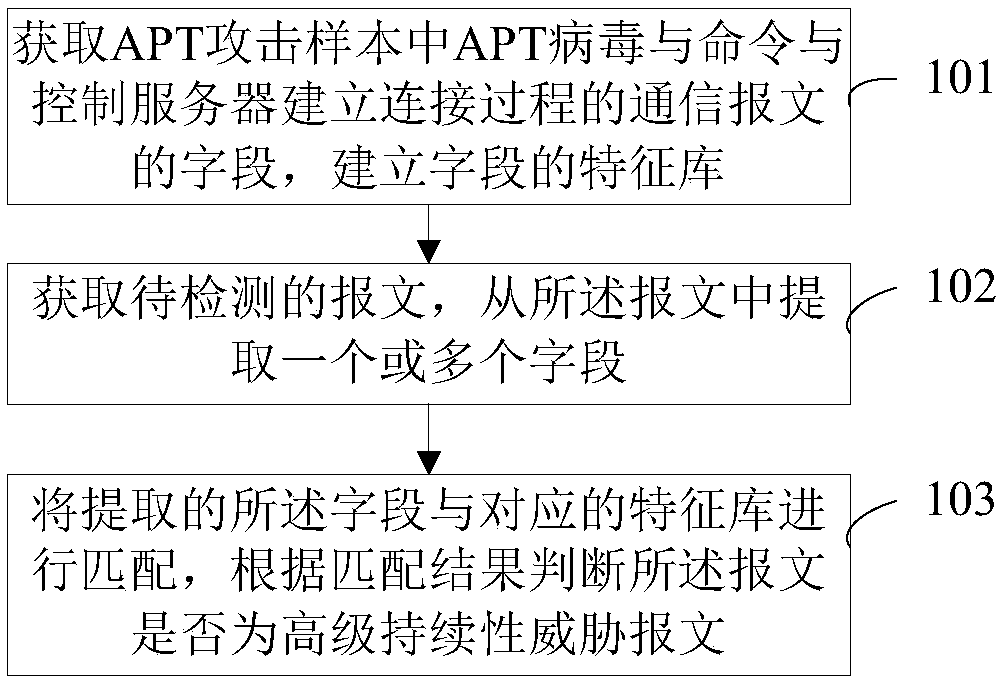
[0056] This embodiment provides a method for detecting advanced persistent threat attacks, such as figure 1 shown, including:
[0057] Step 101, obtaining the communication message in the stage of establishing a connection between the APT virus and the command and control server in the APT attack sample, and establishing a field feature library according to the fields of the communication message;
[0058] Step 102, obtaining the message to be detected, and extracting one or more fields from the message;
[0059] Wherein, the message to be detected can be acquired in an online or offline manner. When the message to be detected is obtained online, the obtained message can be stored for subsequent offline use.
[0060] Step 103, matching the extracted fields with the corresponding signature database, and judging whether the packet is an advanced persistent threat packet according to the matching result.
[0061] Wherein, in step 101, the advanced persistent threat packet samp...
Embodiment 2
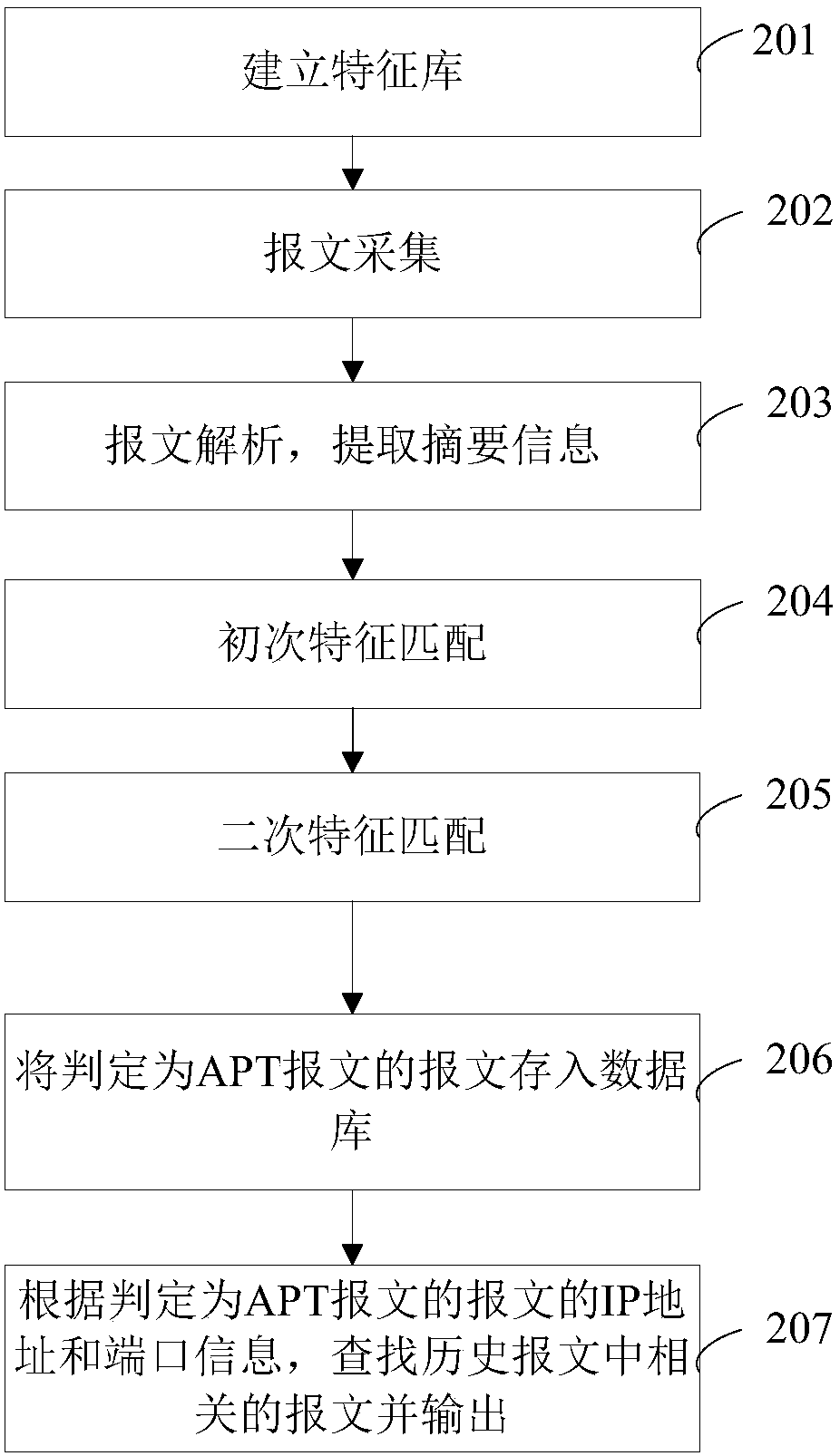
[0079] figure 2 It is a flow chart of the advanced persistent threat detection method provided by Embodiment 2 of the present invention. Such as figure 2 As shown, the advanced persistent threat detection method provided in this embodiment includes:
[0080] Step 201, establishing a feature library;
[0081] In this embodiment, two feature databases are established for one field, the first feature database and the second feature database. See the subsequent description for the specific establishment method.
[0082] Step 202, collect message data.
[0083] Among them, if the online mode is used for the detection, libpcap can be used to collect network data packets for the monitored target IP. If the detection adopts the offline mode, read the offline data. Among them, libpcap is a network data packet capture function package under the unix / linux platform, and most network monitoring software is based on it. Of course, other methods may also be used to obtain network d...
Embodiment 3
[0146] This embodiment provides an advanced persistent threat attack detection device, such as Figure 7 shown, including:
[0147] The feature library building module 701 is configured to obtain the communication message in the stage of establishing a connection between the advanced persistent threat virus and the command and control server in the advanced persistent threat attack sample, and establish a field feature library according to the fields in the communication message ;
[0148] The field extraction module 702 is configured to obtain the message to be detected, and extract one or more fields from the message;
[0149] The matching module 703 is configured to match the extracted fields with their corresponding feature databases, and judge whether the message is an advanced persistent threat message according to the matching result.
[0150] In an optional embodiment of the present invention, the analysis module 704 may also include, configured to, for a message jud...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com