A malicious domain name identification method and device
A domain name, malicious technology, applied in transmission systems, electrical components, etc., can solve problems such as low accuracy, inability to respond to malicious domain names in time, and large lag
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
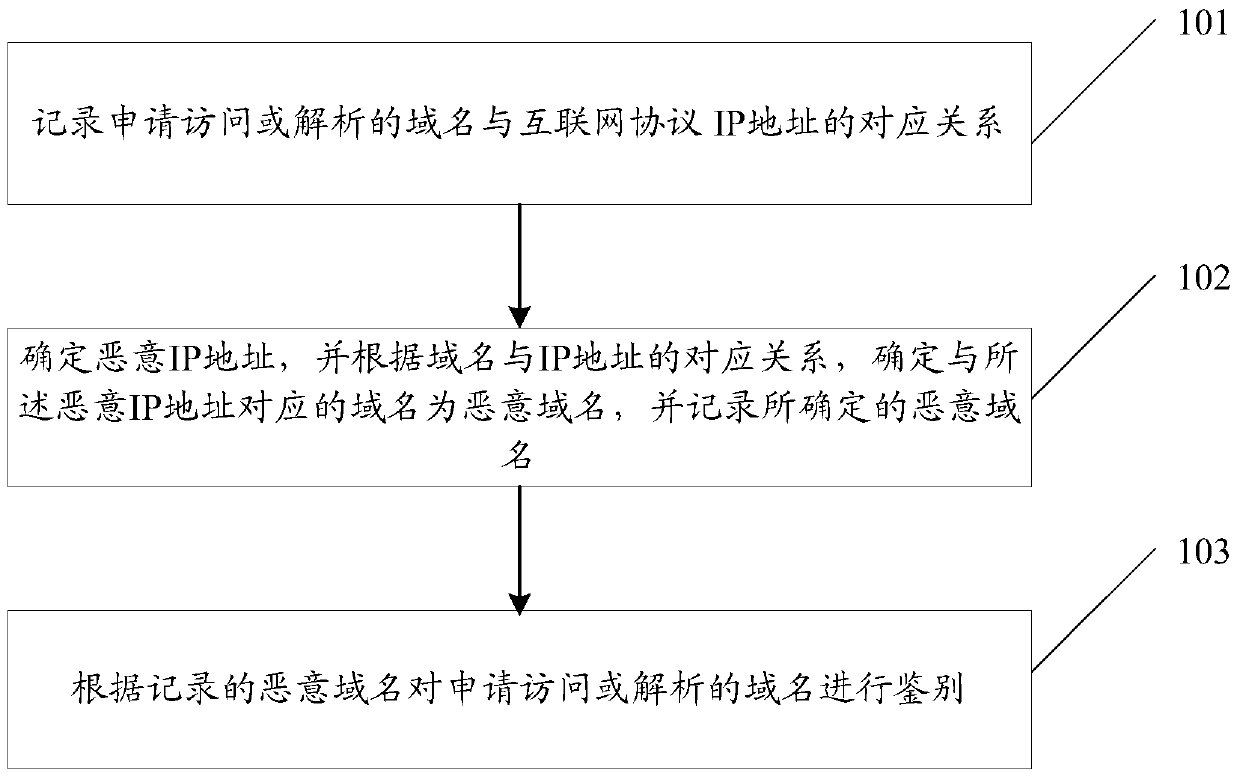
[0042] figure 1 It is a schematic flow diagram of a malicious domain name identification method according to an embodiment of the present invention. The subject of execution of the method may be a server, such as: Domain Name System (DNS, Domain Name System) server or Intrusion Prevention System (IPS, Intrusion Prevention System) server , and the server may be a virtual machine.
[0043] Such as figure 1 As shown, the malicious domain name identification method includes:
[0044] Step 101: record the corresponding relationship between the domain name and the IP address of the application for access or resolution;
[0045] Specifically, the DNS server resolves the domain name requested for access or resolution, and obtains the IP address corresponding to the domain name; records the correspondence between the domain name and the IP address.
[0046] Wherein, recording the corresponding relationship between the domain name and the IP address may be to establish a domain name ...
Embodiment 2
[0067] figure 2 It is a schematic diagram of a malicious domain name identification device in Embodiment 2 of the present invention, such as figure 2 As shown, the device includes: a recording module 21, a determination module 22 and an identification module 23; wherein,
[0068] The recording module 21 is used to record the corresponding relationship between the domain name and the IP address of the application for access or resolution;
[0069] The determining module 22 is configured to determine the malicious IP address, and determine the malicious domain name corresponding to the malicious IP address according to the correspondence between the domain name and the IP address, and add the malicious domain name to the malicious domain name database;
[0070] The identification module 23 is configured to identify the domain name that is applied for access or resolution according to the malicious domain name database.
[0071] In order to explain more clearly, each module w...
Embodiment 3
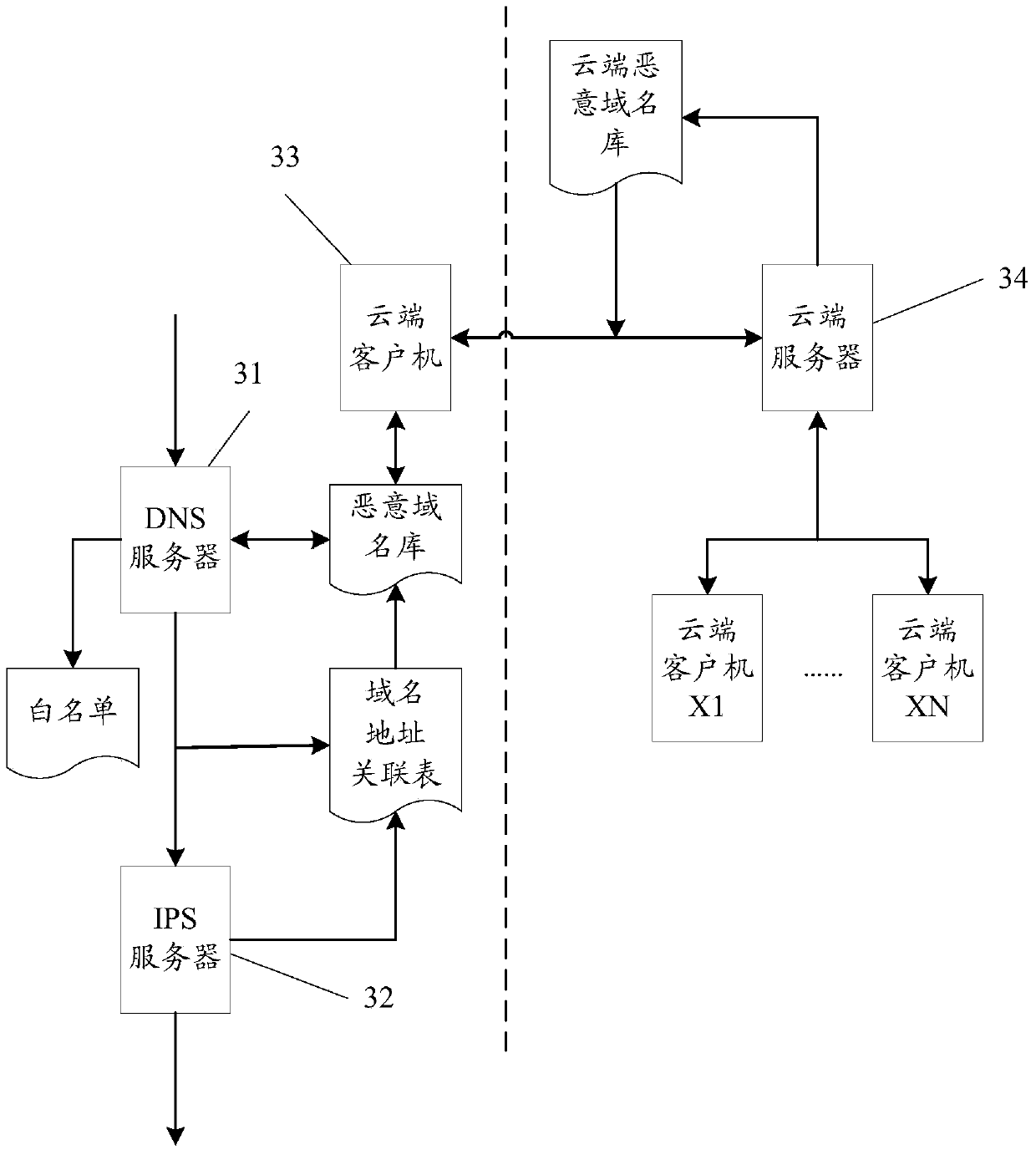
[0096] Based on the malicious domain name identification device of the second embodiment, in practical application, a malicious domain name identification system can be provided.
[0097] image 3 It is a schematic diagram of the third malicious domain name identification system in the embodiment of the present invention, such as image 3 As shown, the malicious domain name identification system includes: DNS server 31, IPS server 32, cloud client 33, cloud server 34, wherein,
[0098] Described DNS server 31 is used for: identifying the domain name that applies for visit or resolution, if described domain name is in the whitelist, then directly ignore, allow it to enter IPS server 32;
[0099] If the domain name is a domain name in the malicious domain name database, corresponding processing is carried out, such as prohibiting entry, etc.;
[0100] If the domain name is neither in the white list nor in the malicious domain name database, it is analyzed, and the correspondin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com