Defense method and system for virus or malicious program
A malicious program and virus technology, applied in the field of virus or malicious program defense, can solve the problems of slow system speed, consumption of large system resources, low hit rate, etc., achieving small resource requirements, less memory resources, avoiding disk I/ Effects of O and CPU consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0062] One of the core concepts of the embodiments of the present invention is to analyze the running environment information of the virus or malicious program, and pre-occupy the running environment of the virus or malicious program on the client, which can prevent the virus or malicious program from entering the system and cause the virus or malicious program to The program cannot complete the attack normally.
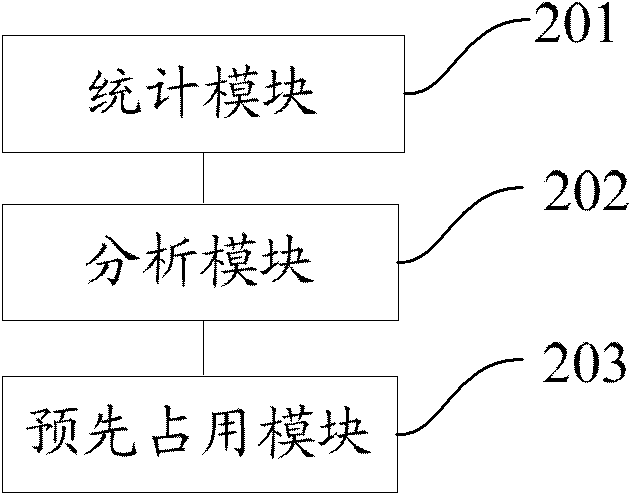
[0063] refer to figure 1 , which shows a flow chart of an embodiment of a method for defending against viruses or malicious programs in the present invention, which may specifically include:
[0064] Step 101, the server side counts the virus or malicious program data of all clients;
[0065] The invention is applicabl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com