DDOS attack detection method in cloud environment
A DDOS and attack detection technology, applied in the field of information security, can solve the problems of low coverage and accuracy, and achieve the effects of improving accuracy, reducing false alarm rate, and relieving pressure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
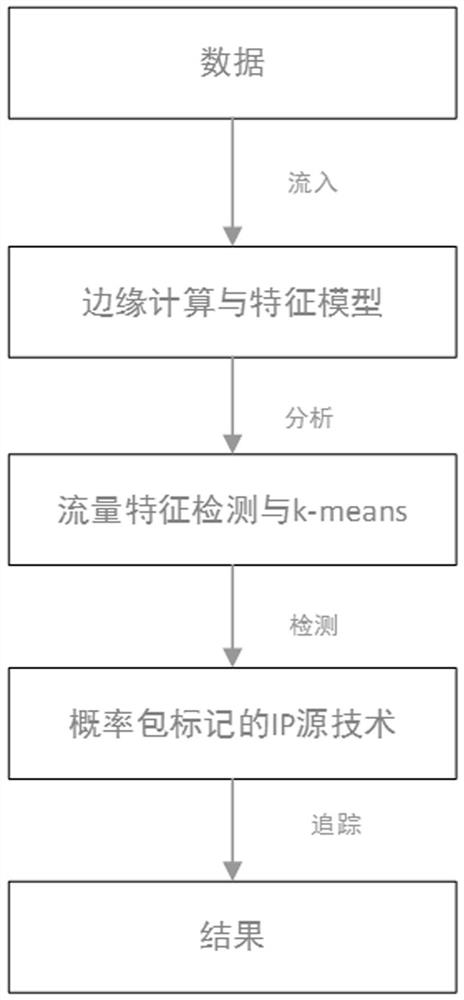
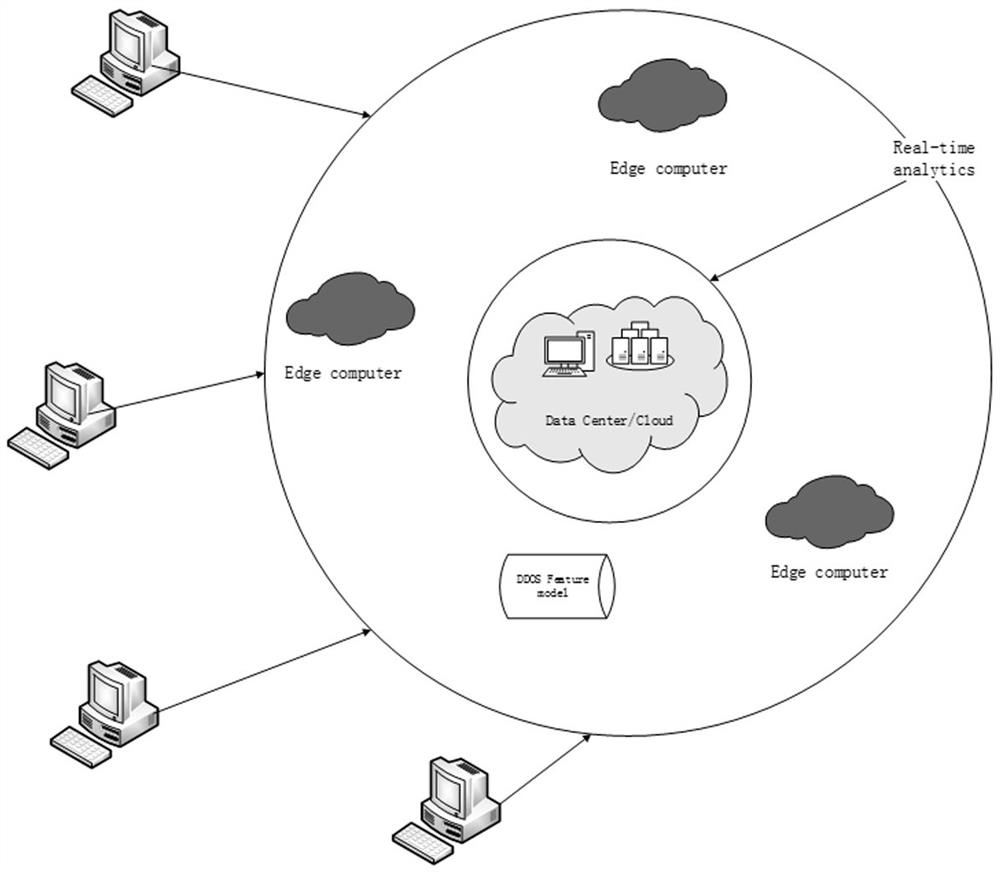
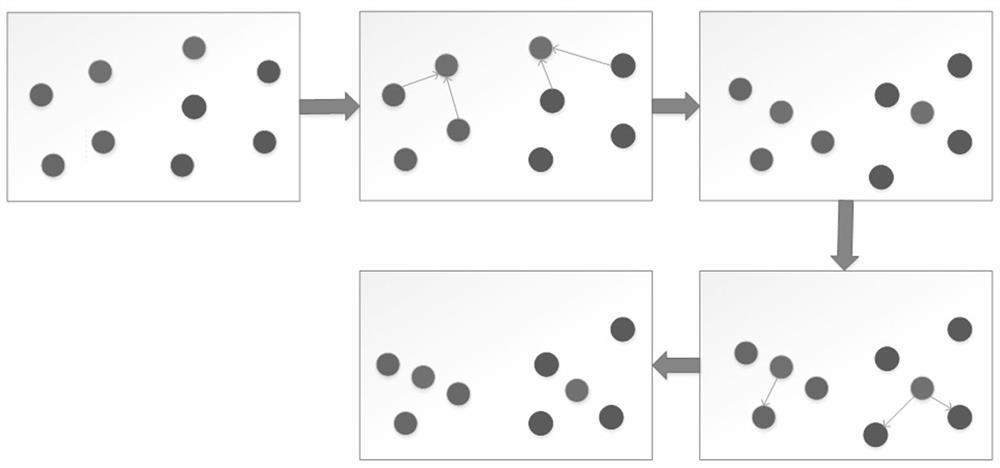
[0019] DDOS attack detection method in the cloud environment, including the deployment of edge computing and features, such as figure 2 As shown, the data, especially the DDOS attack data, is simply processed and monitored in real time through different functions in the edge computing architecture. Using K-means clustering algorithm and its process analysis such as image 3 As shown, it is integrated with the DDOS feature model technology to complete the clustering of DDOS attack data, improve the detection rate, and greatly reduce the false negative rate and false positive rate of detection of known and unknown attack types.
[0020] The above-mentioned DDOS attack detection method under the cloud environment comprises the following steps:
[0021] Step 1: Arrange the edge computing model on the edge side of the cloud platform. When the cloud platform enters the traffic data, use the edge nodes in the edge computing to realize the information collection and simple processin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com