Behavior characteristics-based network attack detection method and device
A network attack and detection method technology, applied in the field of information security, can solve problems such as lack of interoperability of the system and insufficient network attack detection capabilities, and achieve the effect of reducing the number, reducing the false alarm rate, and improving processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] All features disclosed in this specification, or all disclosed steps in a method or process, may be combined in any way except mutually exclusive features and / or steps.
[0061] Any feature disclosed in this specification, unless expressly stated otherwise, may be replaced by other equivalent or alternative features serving a similar purpose. That is, unless expressly stated otherwise, each feature is but one example of a series of equivalent or similar features.
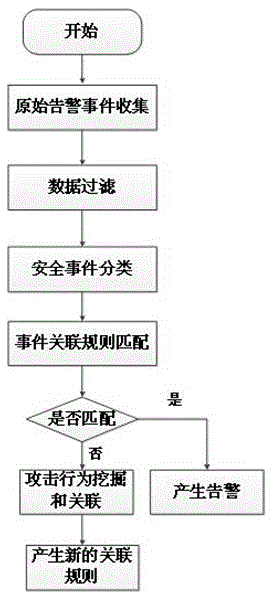
[0062] This embodiment describes a specific behavior correlation-based network attack detection method including the following steps, see figure 1 :
[0063] step 1:
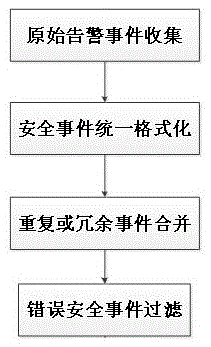
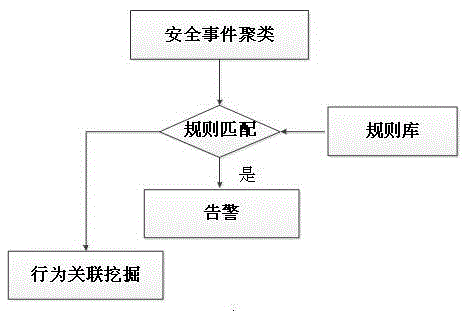
[0064] The present invention obtains the original security information by using a security device, and the security device includes but is not limited to a firewall, an intrusion detection system, a vulnerability library, an antivirus software, a host monitoring system, and the like. Among them, the intrusion detection system can be Snort, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com