Repeated machining process concealment attack detection method based on hidden Markov model
A hidden Markov and repetitive processing technology, applied to complex mathematical operations, electrical components, transmission systems, etc., can solve problems such as undetectable hidden attacks, and achieve the effects of wide application range, improved accuracy, and simple training
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] In order to make the technical scheme and design idea of the present invention clearer, we describe it in detail in conjunction with the accompanying drawings.
[0054] The research object is a repetitive processing process, and the sampling data is the position information of the X and Y axes, which is periodic and has natural disturbances.
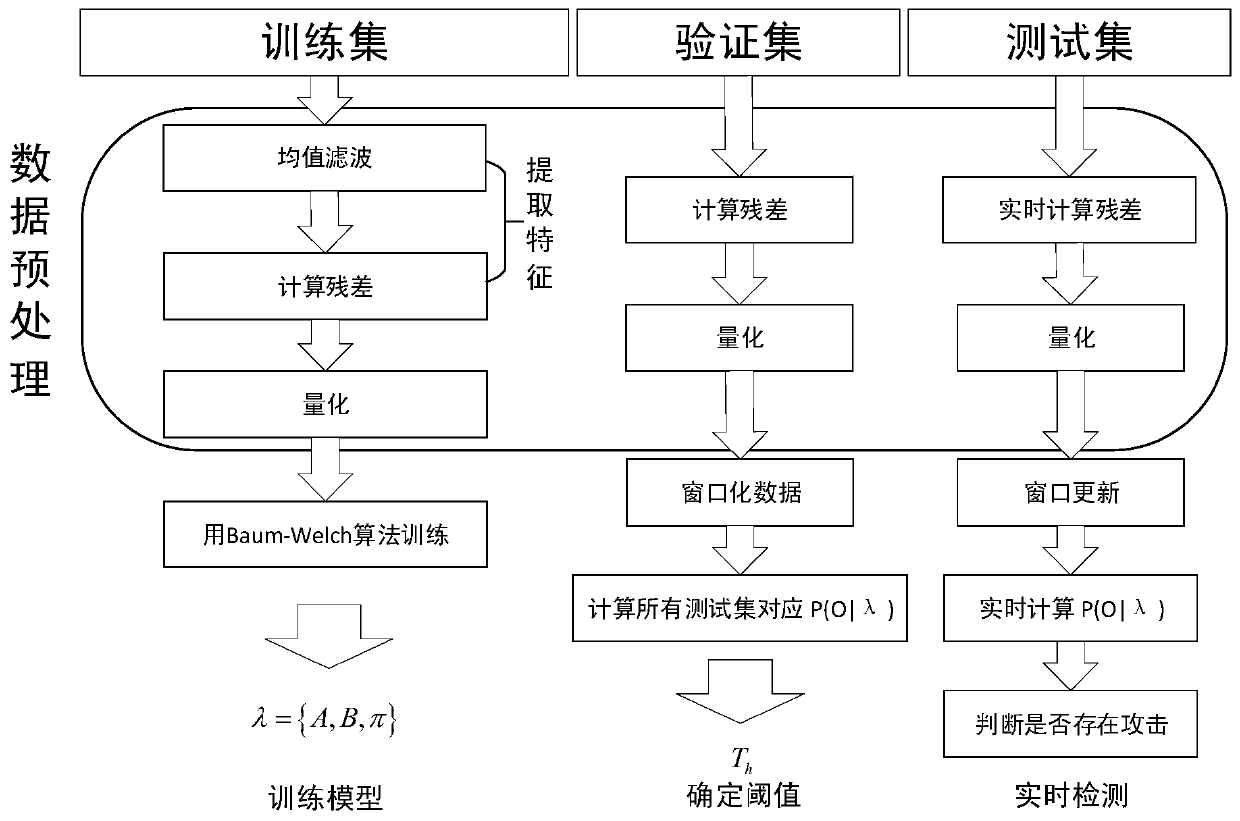
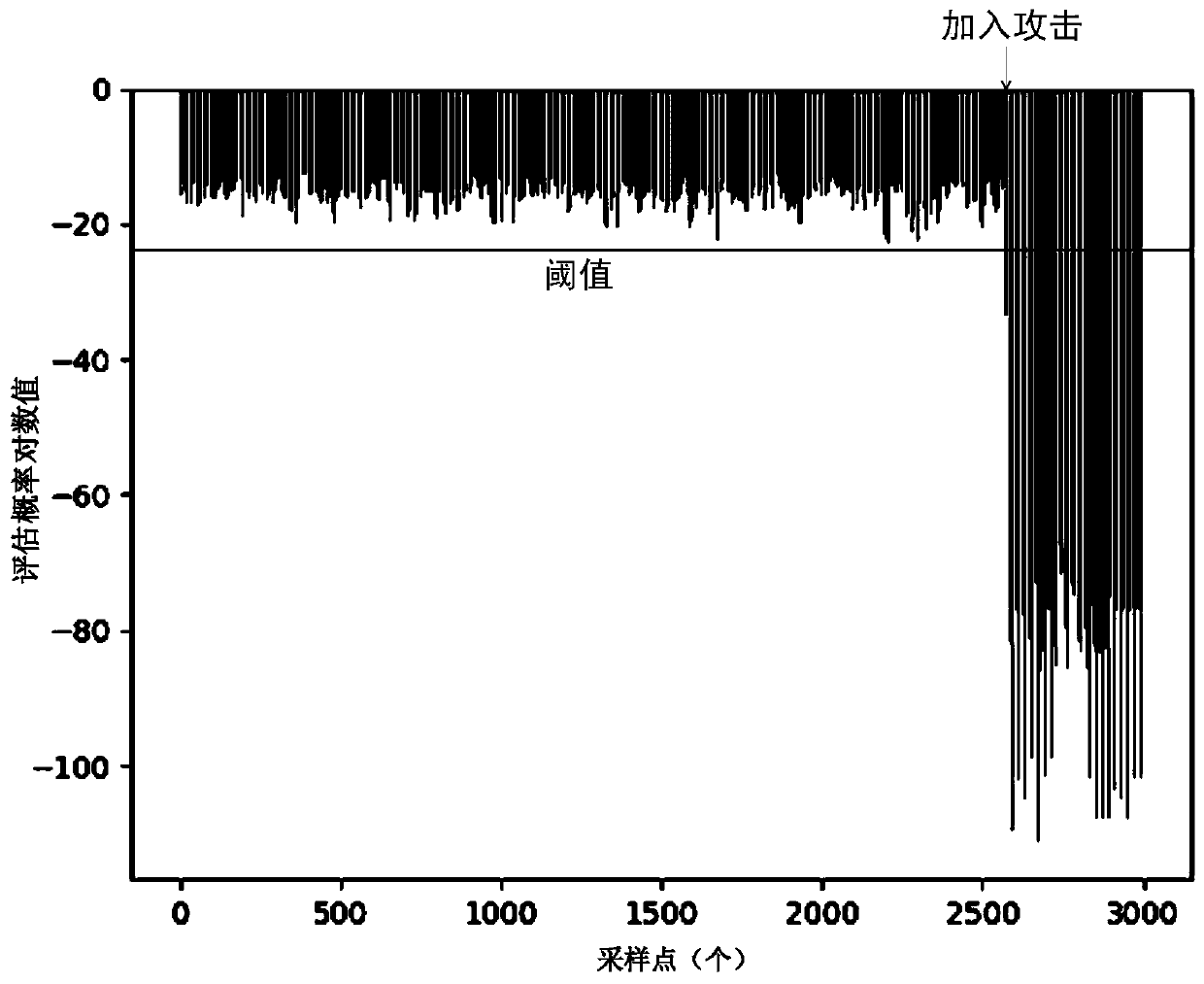
[0055] refer to Figure 1 ~ Figure 3, a hidden Markov model-based concealment attack detection method for repeated processing processes. The implementation process is divided into three stages: model training, threshold determination, and intrusion detection, and each stage requires data preprocessing.
[0056] 1) In the model training phase, the process is as follows:
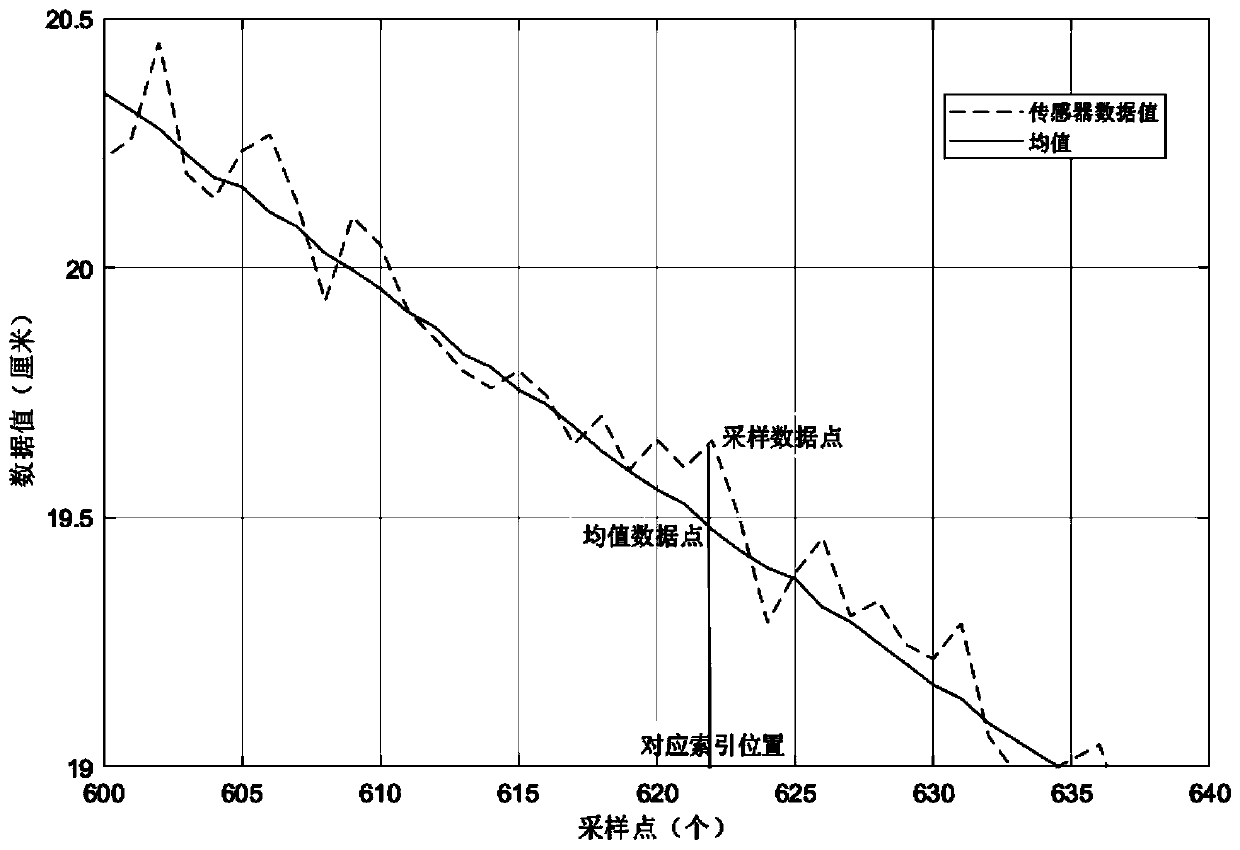
[0057] Step 1.1) Mean filtering
[0058] The processing of the X and Y axes in the repetitive machining process is similar. We take the X axis as an example, select N sampling periods, and T sampling points in each period. Because in each cycle, the data at e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com