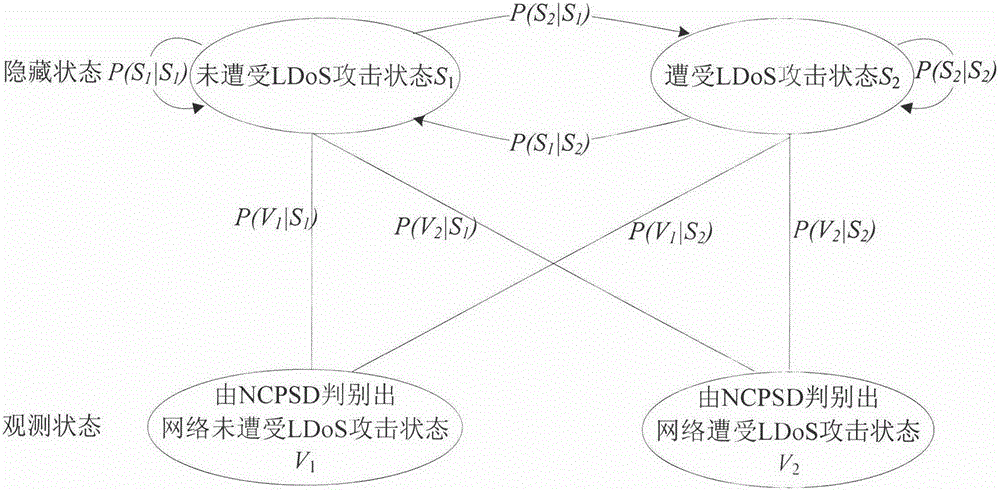
Method of using hidden Markov model to detect LDoS (Low-Rate Denial of Service) attack
A hidden Markov, model detection technology, applied in electrical components, transmission systems, etc., can solve problems such as large amount of calculation and low detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
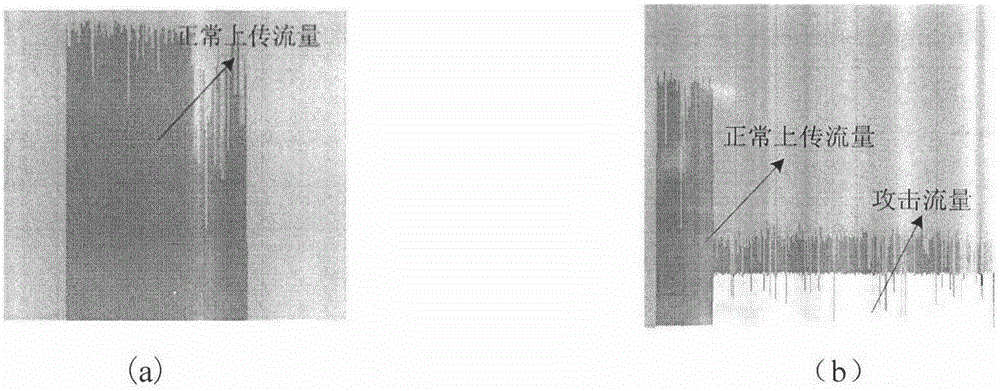
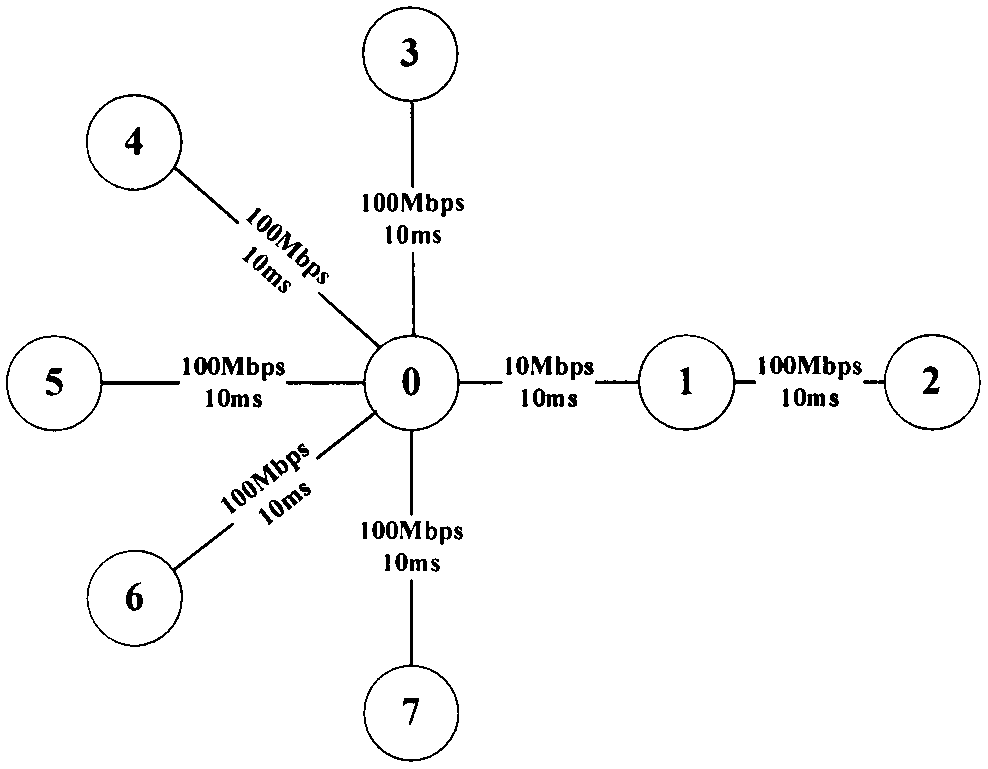
[0037] 1. First verify the LDoS attack detection effect, use NS-2 to build a test environment, Figure 5 The topology structure is a dumbbell-shaped structure, which can represent the characteristics of the actual network. Nodes 0 and 1 are routers, nodes 2 are FTP servers, nodes 3 and 4 are attackers, nodes 5, 6, and 7 are normal users. The link bandwidth between the legitimate user, the LDoS attacker and the router is 100Mbps, the one-way delay is 10ms, the link bandwidth between the routers is 10Mbps, the one-way delay is 10ms, and the link bandwidth between the router and the server is 100Mbps, one-way delay is 10ms. The send queue size of the router is 100 packets. The experiment starts at 0s and ends at 150s. The 3 normal traffic starts at 0s and ends at 150s, and the attack traffic starts at 100s and ends at 150s. Nodes 3 and 4 are attackers with an attack rate of 6Mbps, an attack period of 1150ms, and an attack pulse width of 200ms. 3, 4 nodes start attacking at t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com