Patents
Literature
48results about How to "Avoid parity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
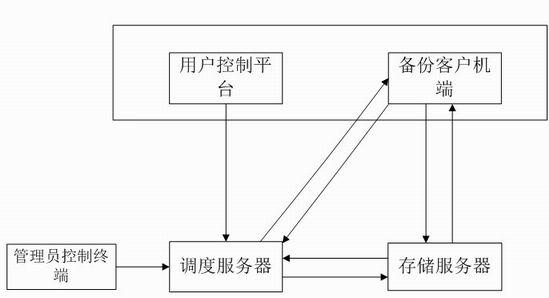
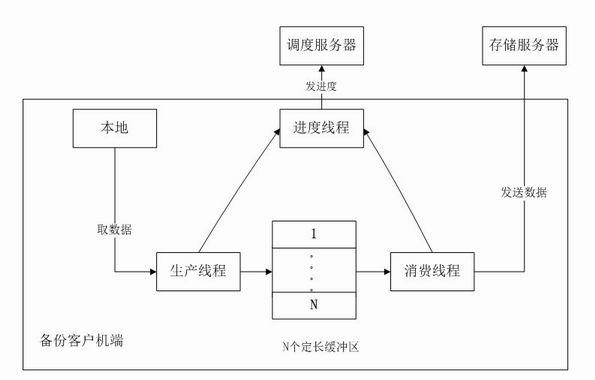
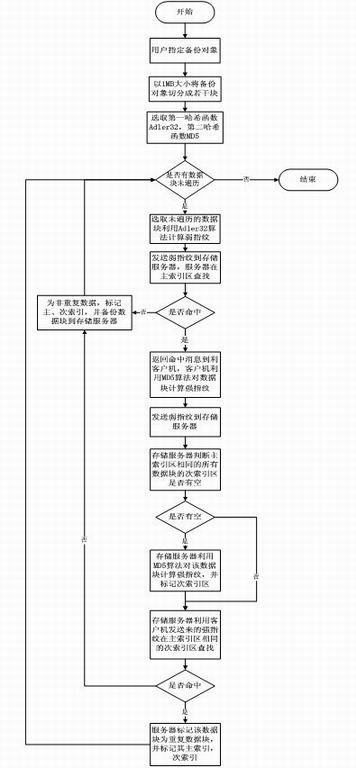
Method for deleting repeated data by using double-fingerprint hash check
InactiveCN102156727AAvoid parityReduce the amount of fingerprint calculationSpecial data processing applicationsRedundant operation error correctionComputer hardwareHash function
The invention provides a method for deleting repeated data by using double-fingerprint hash check. The method comprises the following steps of: dividing an object to be backed up into data blocks to be backed up with equal lengths; judging whether the weak fingerprint of one of the data blocks to be backed up is the same as the weak fingerprint of any data block in a server; if the weak fingerprint of one of the data blocks to be backed up is different from the weak fingerprint of any data block in the server, backing up the data block; if the weak fingerprint of one of the data blocks to be backed up is the same as the weak fingerprint of any data block in the server, judging whether the strong fingerprint of the data block is the same as the strong fingerprint of any data block in the server; if the strong fingerprint of the data block is different from the strong fingerprint of any data block in the server, backing up the data block; and performing the operation on all data blocks to be backed up. In the method for deleting the repeated data, a hash function with low calculation amount is adopted at the first time to perform weak check on every data block and a has function with high calculation amount is adopted then to perform strong check, so the problem that all the data are checked by the hash function with the high calculation amount is avoided, the fingerprint calculation amount during checking is reduced greatly, the series performance is enhanced, and the appreciable transmission performance is provided for data backup based on mass data storage.
Owner:HUAZHONG UNIV OF SCI & TECH
Log based structured data synchronization method
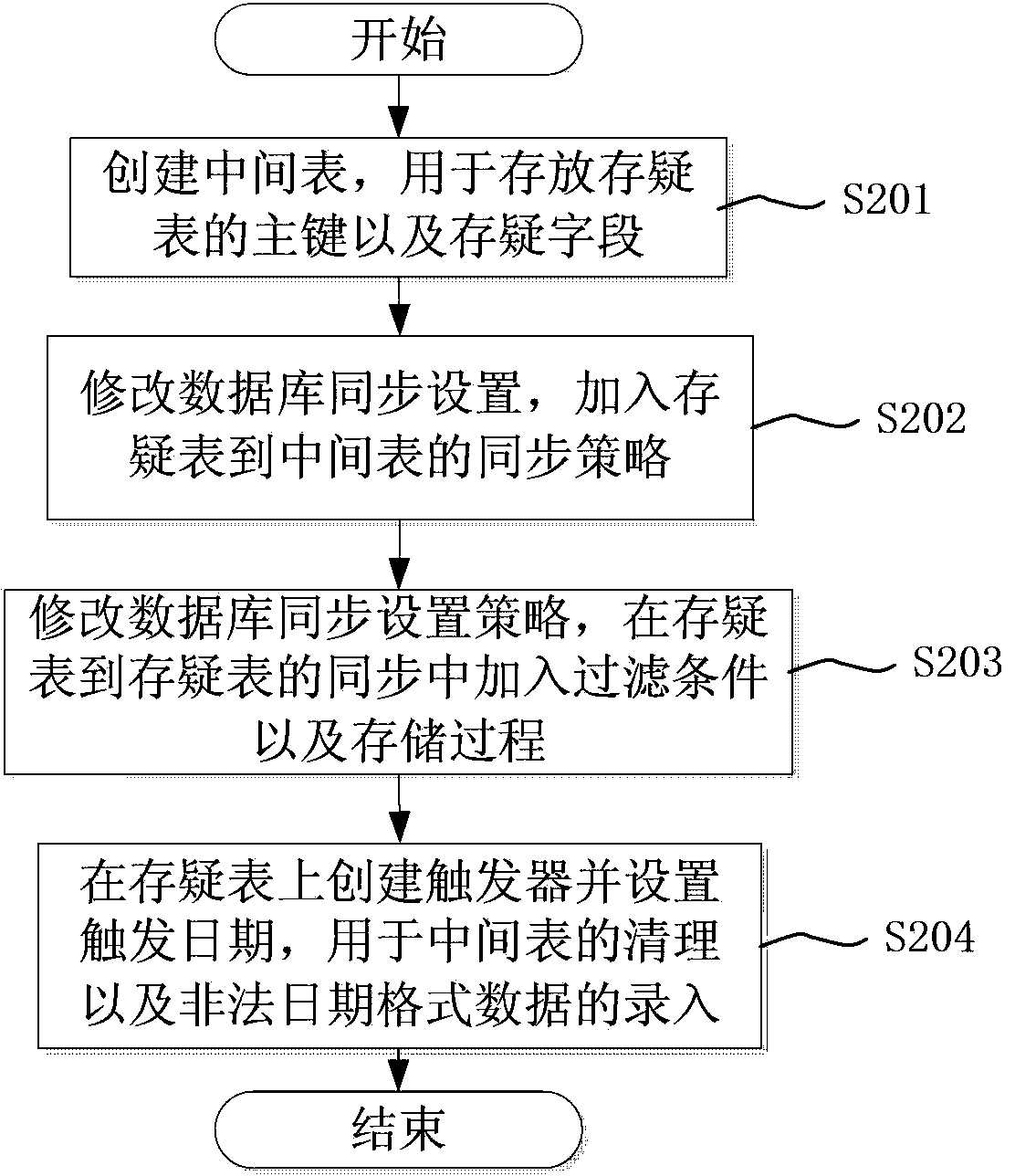
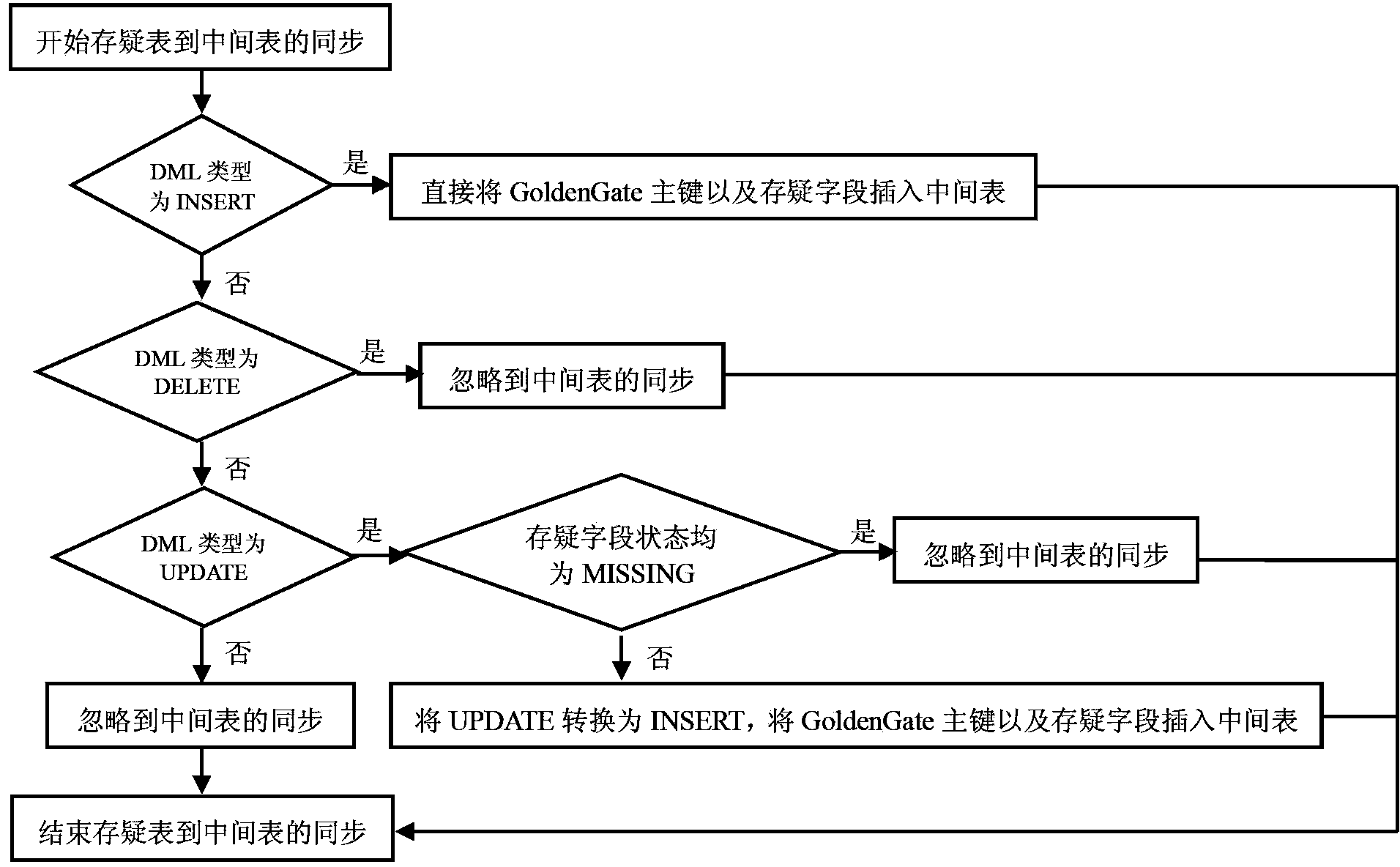
ActiveCN103455557AAvoid parityAvoid Synchronous ExceptionsSpecial data processing applicationsData synchronizationData format
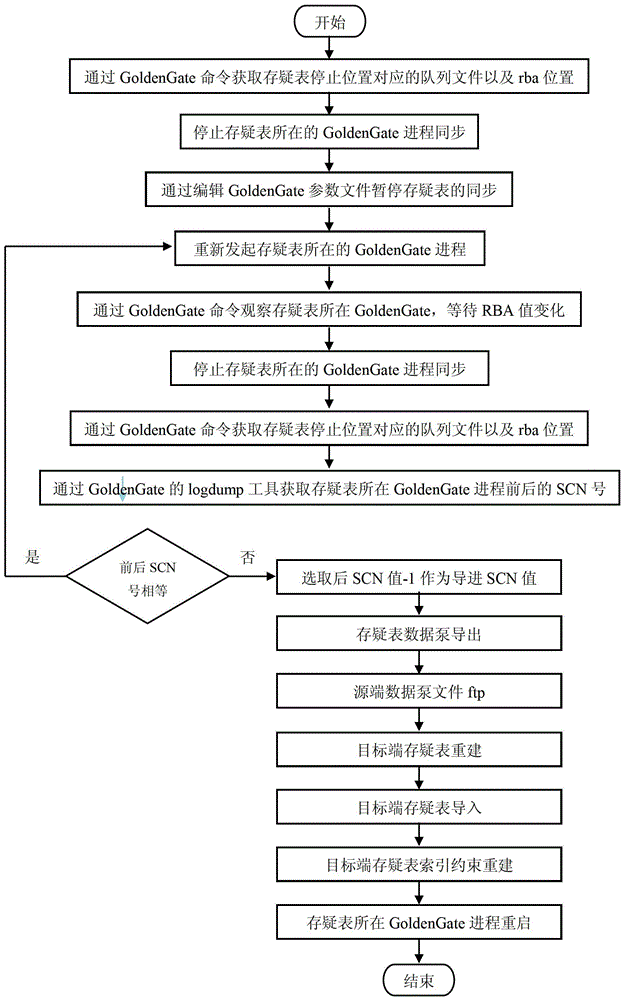
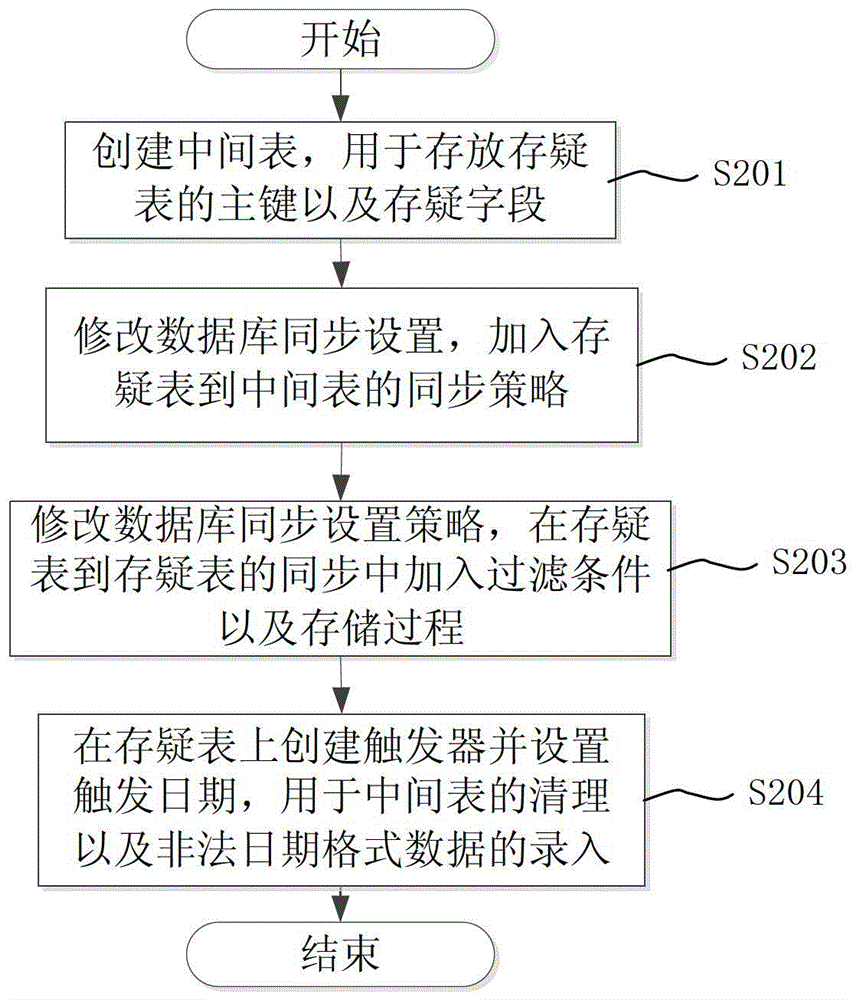
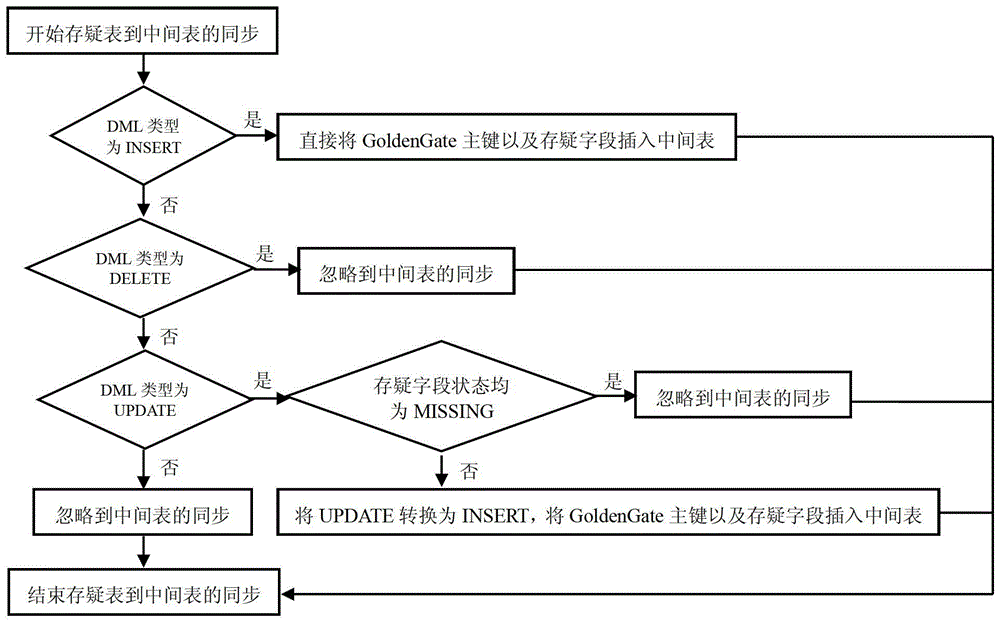
The invention discloses a log based structured data synchronization method. The log based structured data synchronization method includes the steps of a), establishing a middle table for storing major keys and doubt fields of a doubt table; b), modifying database synchronization settings and adding the doubt table to a synchronization strategy of the middle table; c), modifying a database synchronization setting strategy and adding filter conditions and store procedures during doubt table synchronization of the doubt table; d), establishing a trigger on the doubt table and setting trigger date for clearing of the middle table and entering of illegal data format data. By the log based structured data synchronization method, data synchronization can be realized by avoiding the verification mechanism of a database, data consistency of corresponding records between a source library and an object library can be kept, and synchronous exception caused by data type report errors can be avoided.
Owner:上海新炬网络技术有限公司
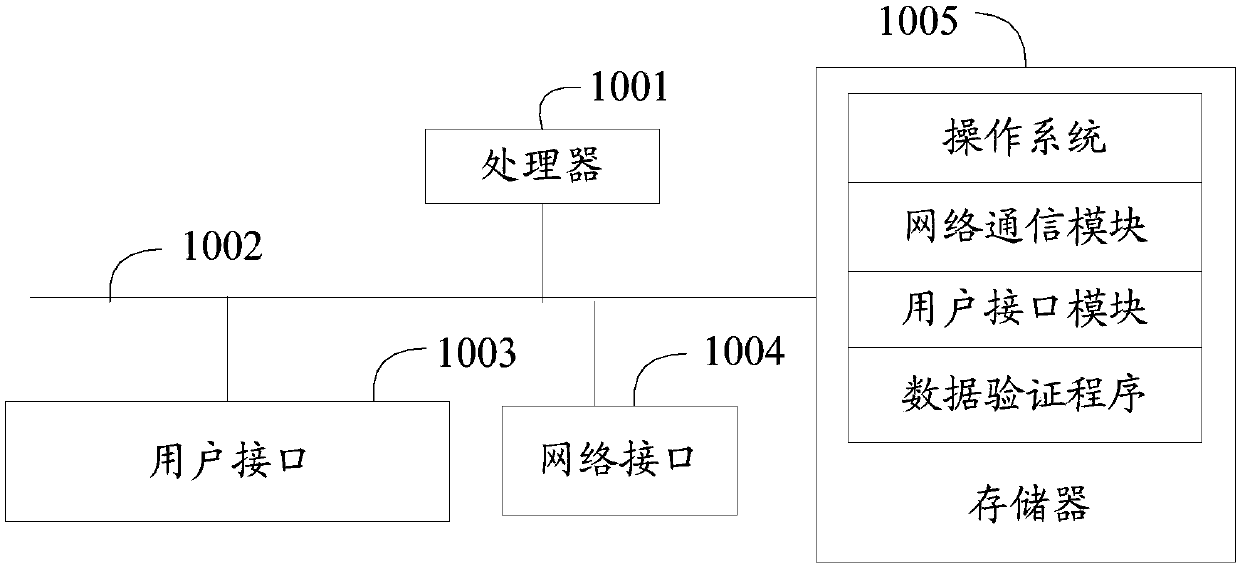
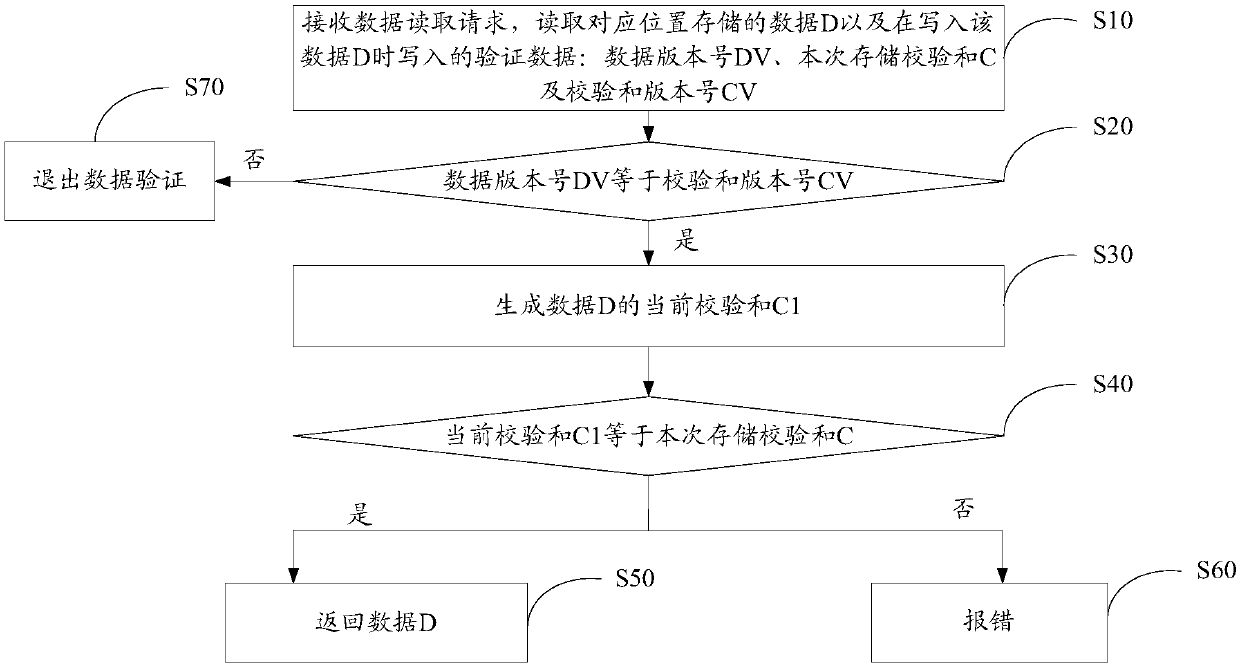
Data verification method and device and readable storage medium
ActiveCN107861832AAvoid parityAvoid misjudgmentRedundant data error correctionSource Data VerificationChecksum
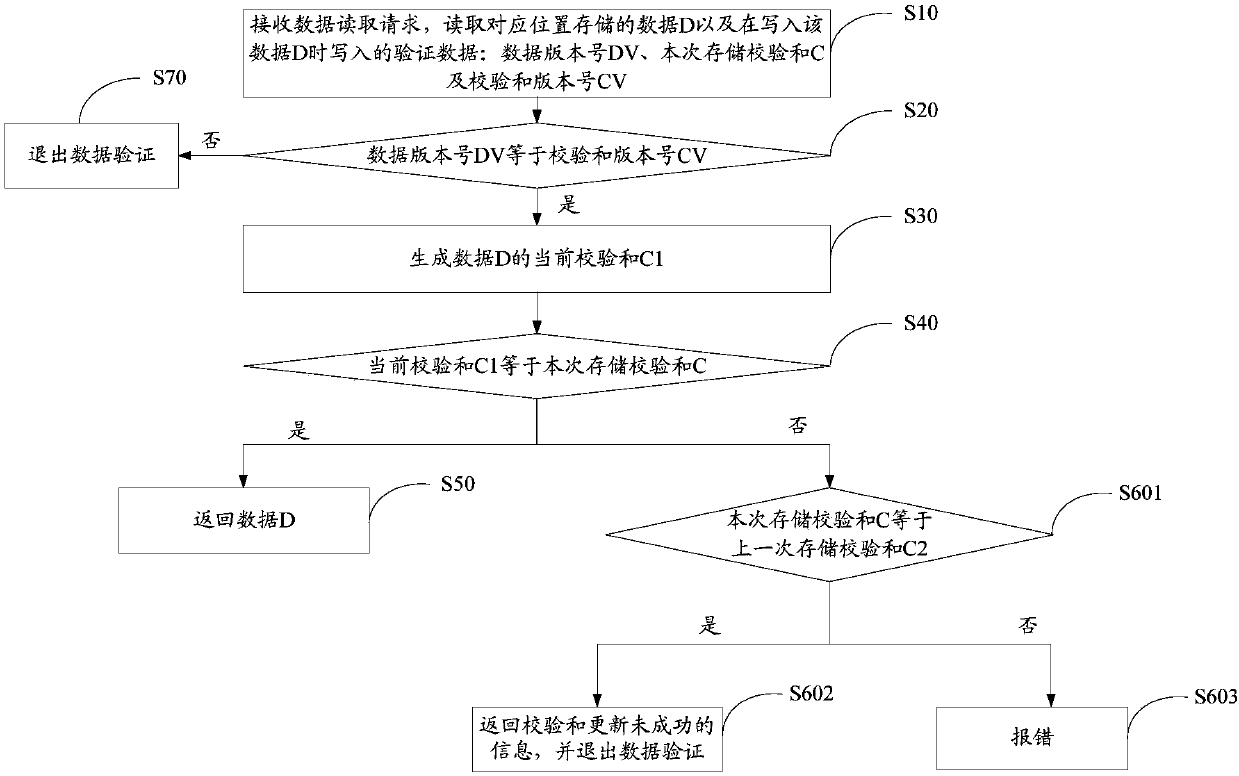
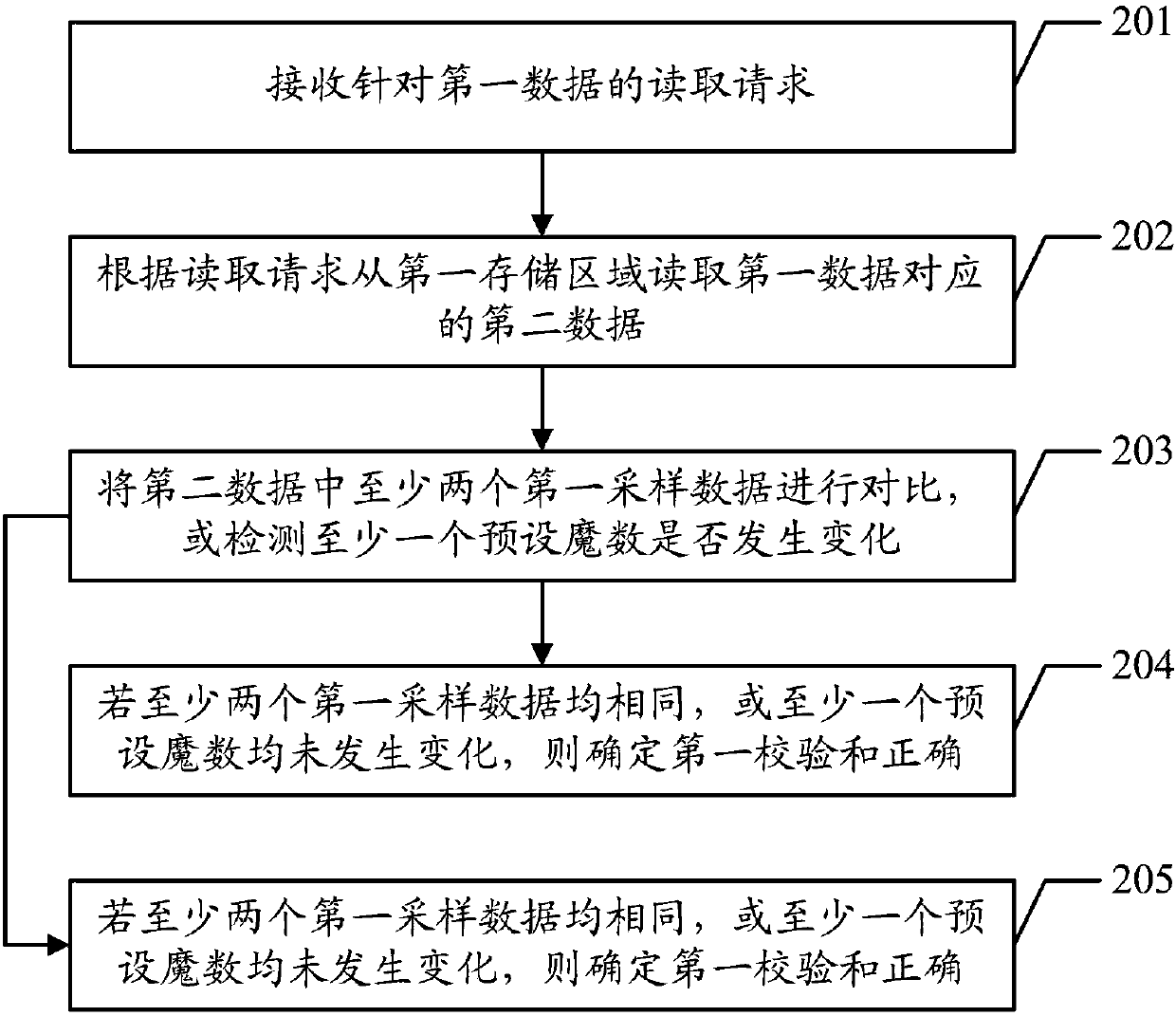
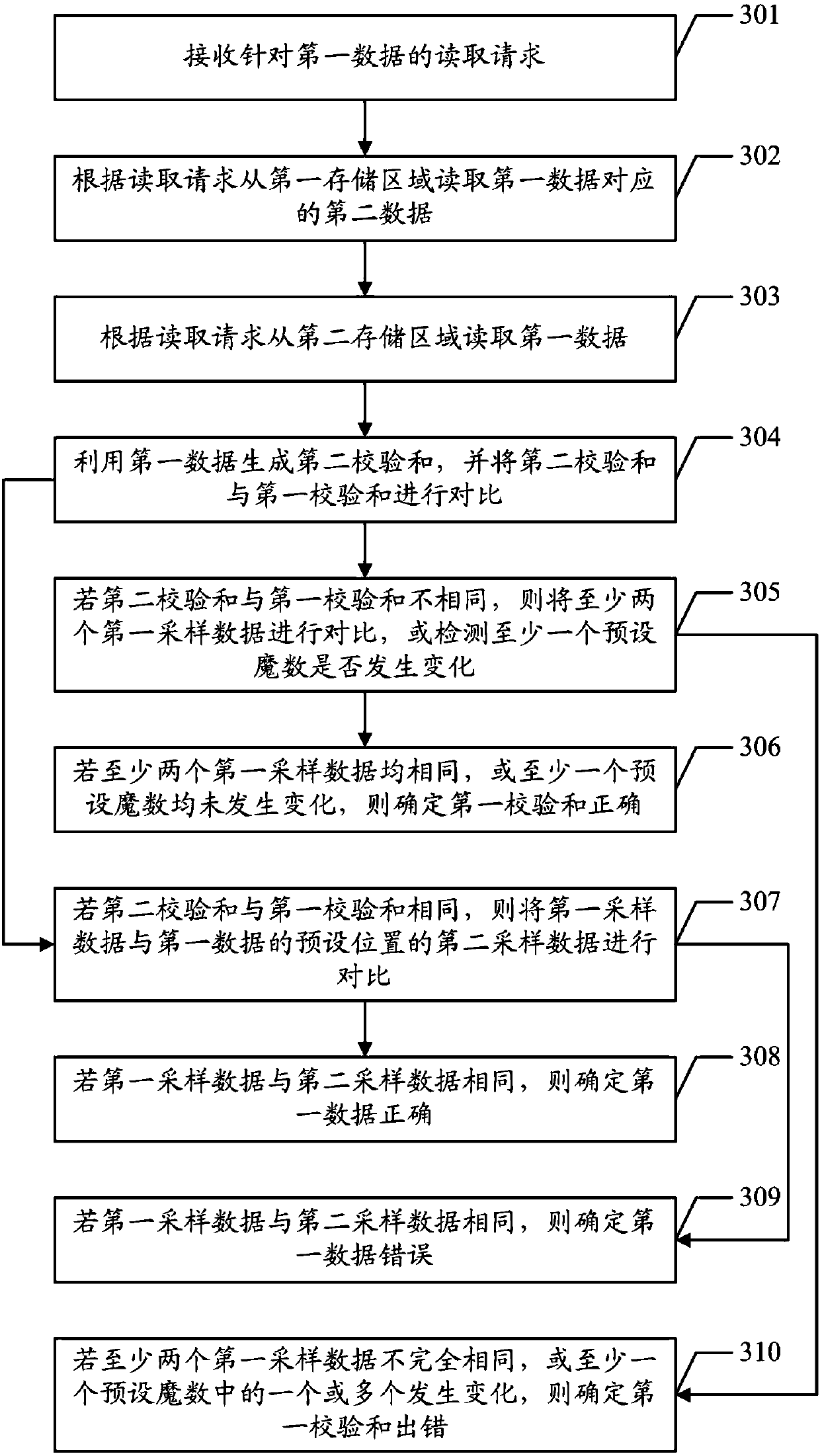
The invention discloses a checksum-based data verification method. The method comprises the following steps of: receiving a data reading request, and reading data D which is stored at a correspondingposition and verification data which is written when the data D is written, wherein the verification data at least comprises a data version number DV, a storage checksum C and a checksum version number CV; judging whether the data version number DV is equal to the checksum version number CV or not; if the judging result is positive, generating a current checksum C1 of the data D, and otherwise, exiting the data verification; and judging whether the current checksum C1 is equal to the storage checksum C or not, if the judging result is positive, returning the data D, and otherwise, carrying outerror report. The invention furthermore discloses a checksum-based data verification device and a computer readable storage medium. According to the method, the device and the computer readable storage medium, erroneous judgement of checksums can be effectively detected and avoided, the precision of detecting data errors by using checksums is improved, and the negative effects on systems are decreased.
Owner:SANGFOR TECH INC
Method and device for verifying identifying code
ActiveCN106572074AAvoid parityReduce operating frequencyTransmissionComputer scienceOperating frequency
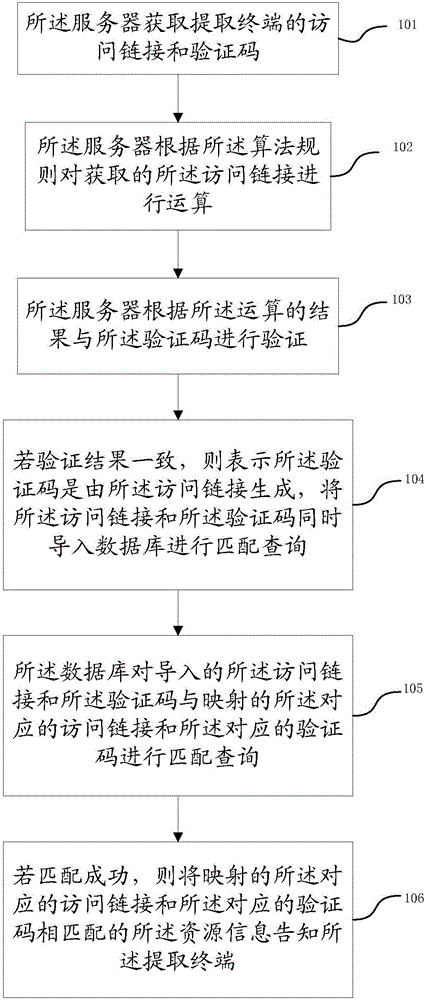
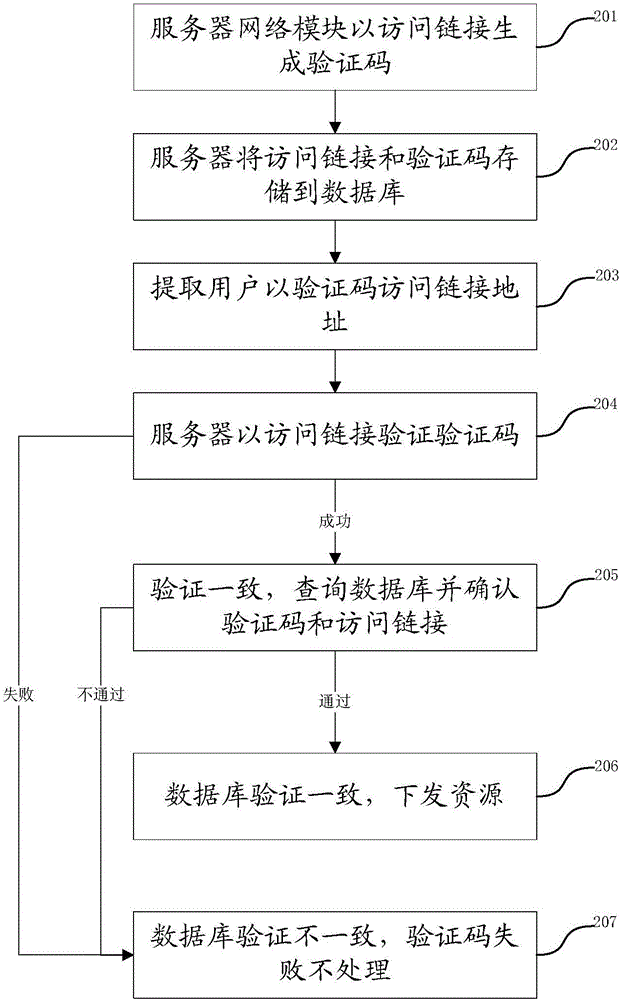
The embodiment of the invention discloses a method and device for verifying an identifying code. The method presets an algorithm rule for a corresponding relation between an access link and the identifying code, calculating the access link of an extraction terminal according to the algorithm rule, verifies a calculation result and the identifying code of the extraction terminal. If a verification result indicates consistency, it means that the identifying code is generated by the access link and the access link and the identifying code are simultaneously imported into a database for matching query. According to the method, the algorithm rule is preset in a server, the server firstly performs algorithm preprocessing on the identifying codes when acquiring the identifying codes, filters out the invalid identifying codes, and sends the left identifying code sent to the database for operation. Thus, the server is prevented from getting access to the database multiple times to verify the identifying code and the operating frequency of the database is reduced, thereby enhancing the server performance.
Owner:QINGDAO HISENSE MOBILE COMM TECH CO LTD
Reminding method and apparatus, terminal and storage medium
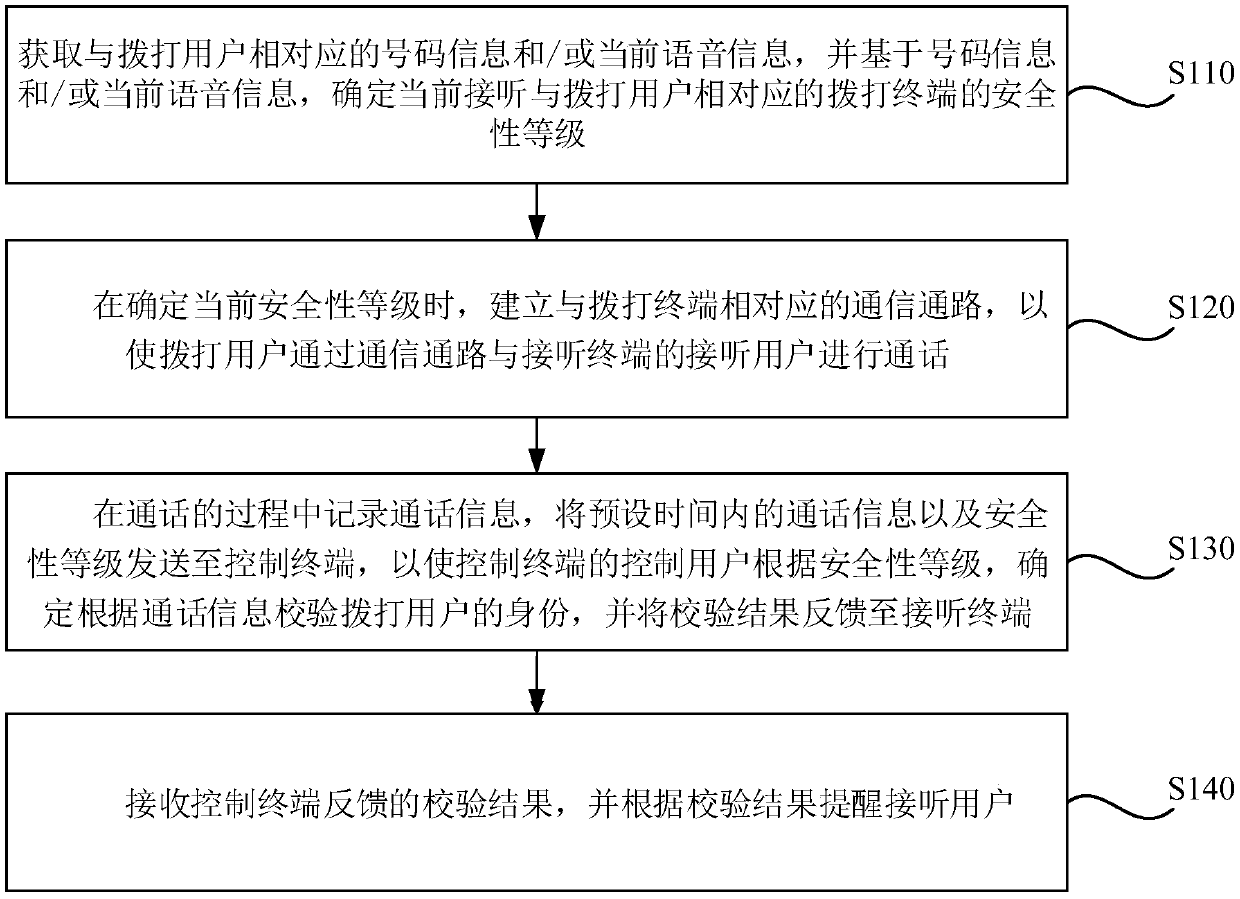
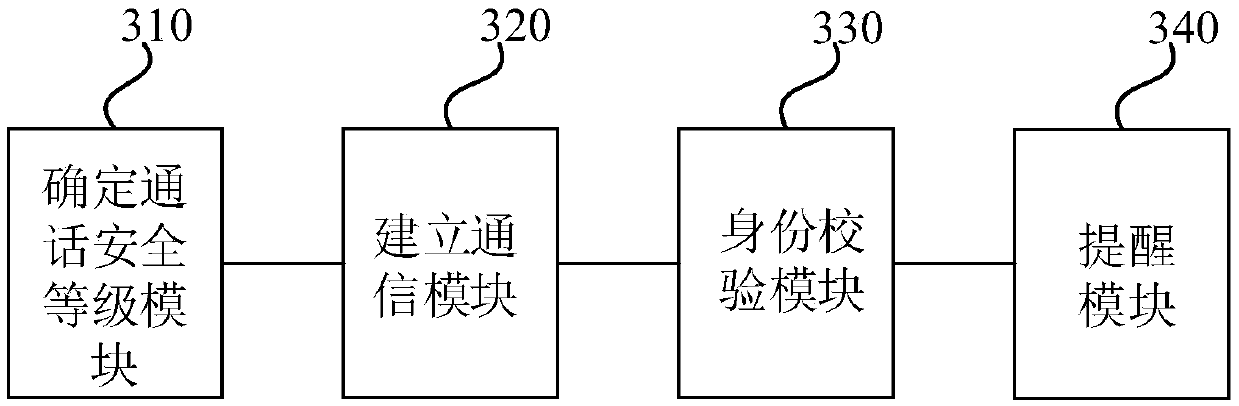
ActiveCN109688273ARemind in timeEffective reminderSubstation equipmentComputer hardwareSecurity level
The embodiment of the invention discloses a reminding method and apparatus, a terminal and a storage medium. The method comprises the following steps: obtaining number information and / or current voiceinformation corresponding to a dialing user, and determining a security level of a dialing terminal corresponding to the dialing user based on the number information and / or the current voice information; when the current security level is determined, establishing a communication path corresponding to the dialing terminal, so that the dialing user makes a call with an answering user of an answering terminal through the communication path; and recording call information in a call process, sending the call information within a preset time and the security level to a control terminal, so that a control user of the control terminal verifies the identity of the dialing user according to the security level and the call information, and feeds back a verification result to the answering terminal;and receiving the verification result fed back by the control terminal, and reminding the answering user according to the verification result. By adoption of the scheme, the technical effect of reminding the user effectively in time is achieved.
Owner:SHANGHAI DROI TECH CO LTD
Contract file risk verification method and device, computer device and storage medium
PendingCN110826321ARisk check to avoidAvoid parityFinanceSemantic analysisAlgorithmBusiness enterprise
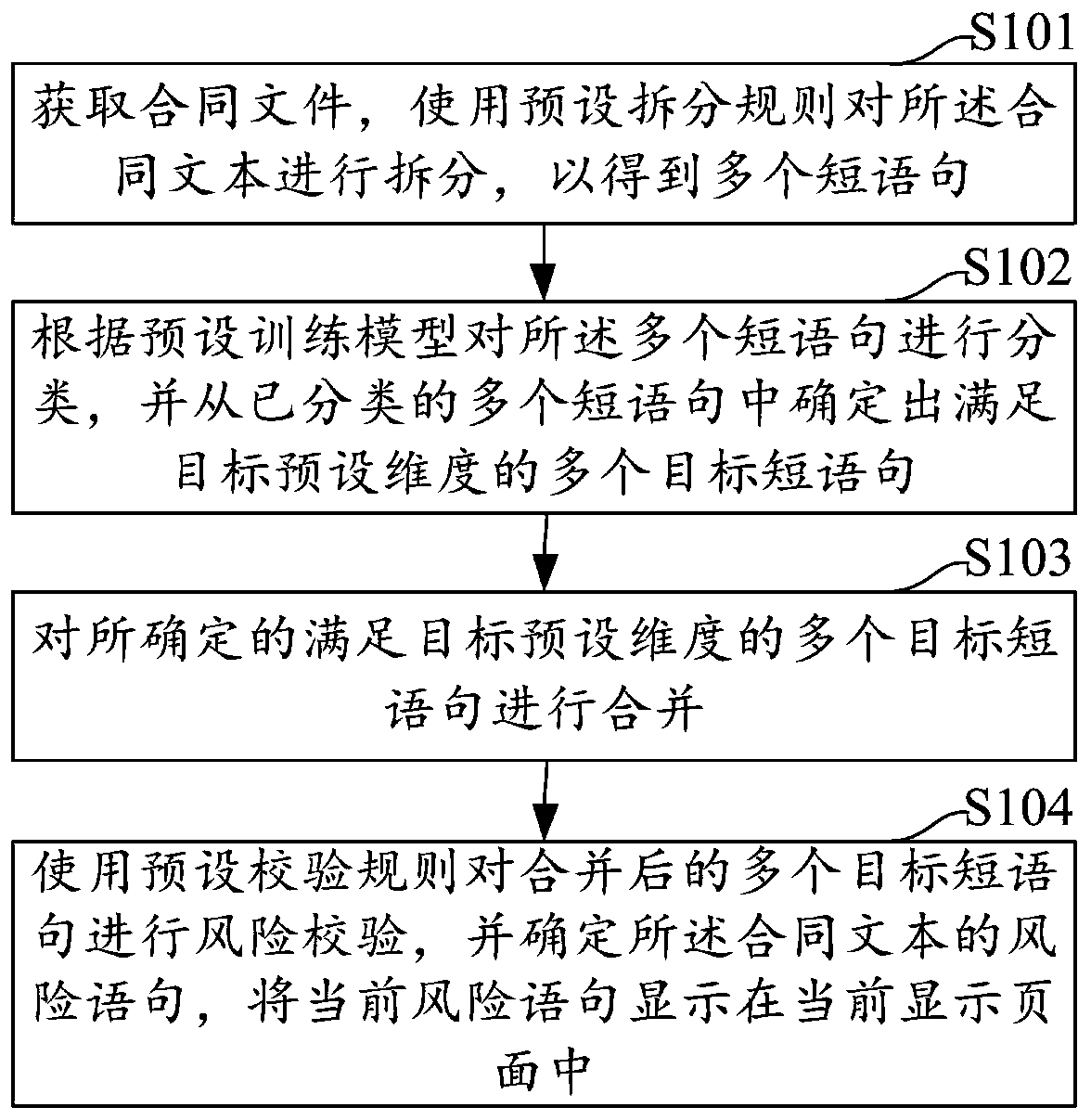
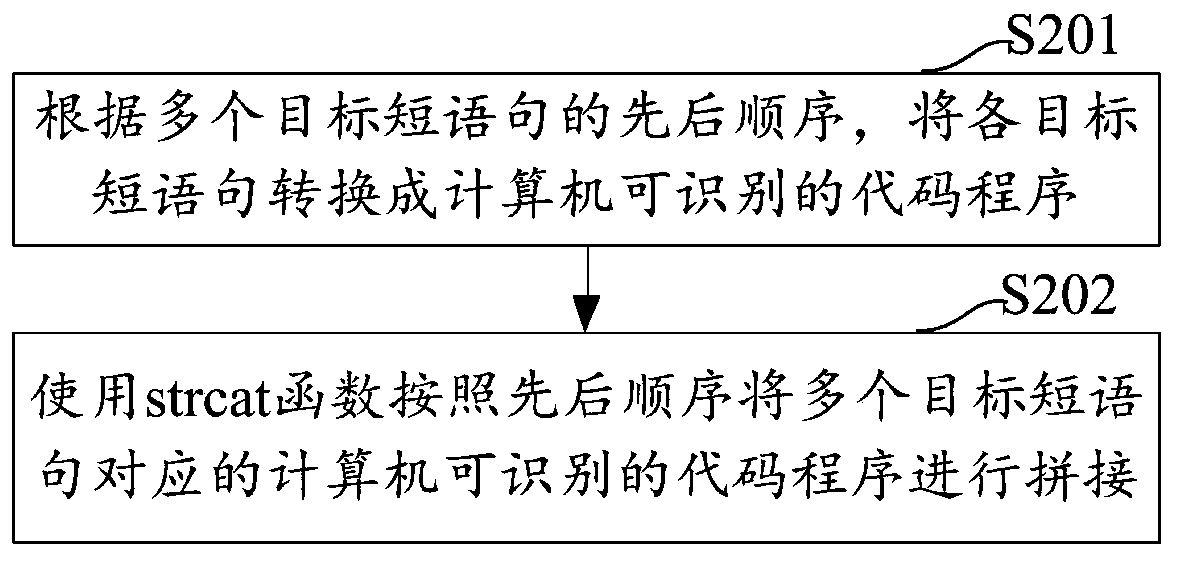
The embodiment of the invention discloses a contract file risk verification method and device, a computer device and a storage medium, and the method comprises the steps: obtaining a contract file, and carrying out the splitting of a contract text through a preset splitting rule, so as to obtain a plurality of short sentences; classifying the plurality of short sentences according to a preset training model, and determining a plurality of target short sentences meeting a target preset dimension from the plurality of classified short sentences; combining the plurality of determined target shortsentences meeting the target preset dimension; and performing risk verification on the combined target short statements by using a preset verification rule, determining a risk statement of the contract text, and displaying the current risk statement in a current display page. According to the contract file risk verification method based on data processing, risk verification of the contract text is realized, and use of a contract with risks by an enterprise is avoided.
Owner:PING AN TECH (SHENZHEN) CO LTD
Product configuration data monitoring method and device, apparatus and storage medium
ActiveCN110245049AImprove accuracyAvoid it happening againFinanceHardware monitoringEmbedded systemData monitoring
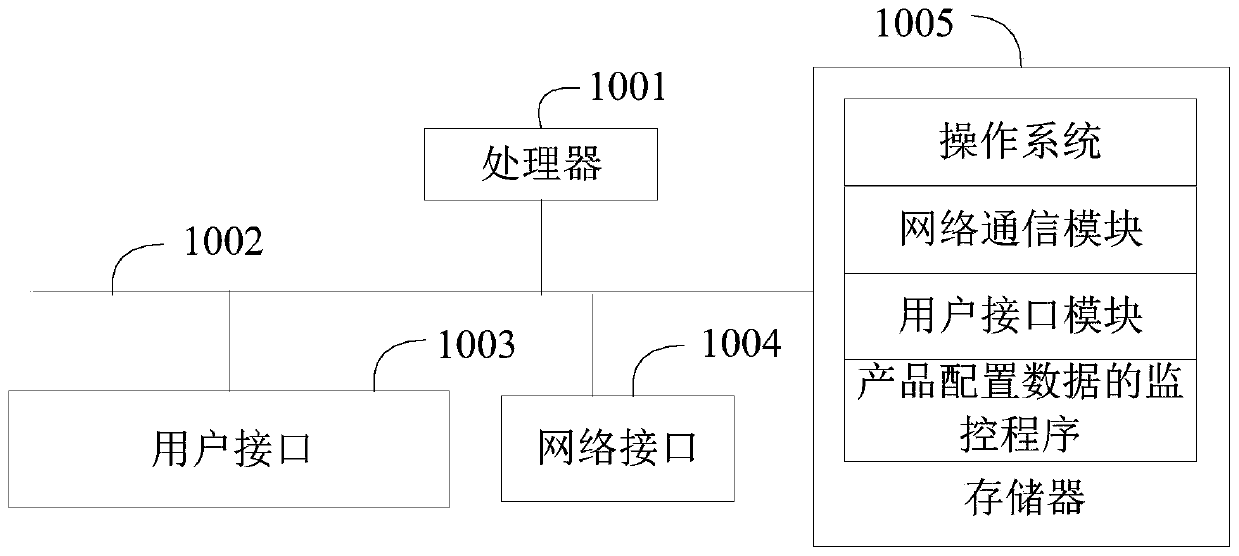
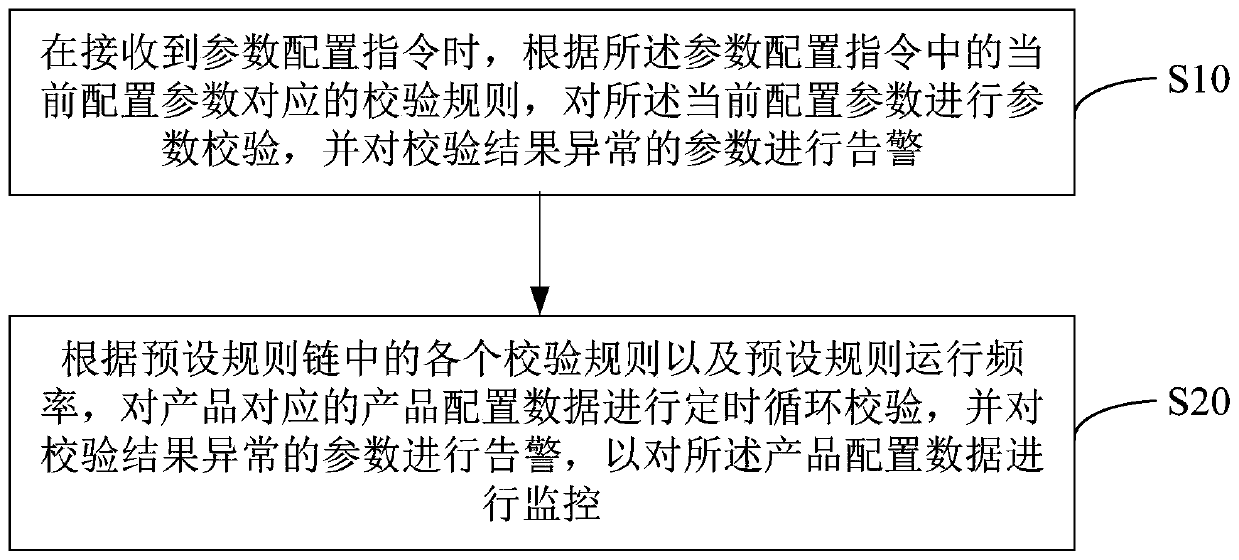
The invention discloses a product configuration data monitoring method and device, an apparatus and a storage medium, and relates to the field of financial technology. The method comprises the following steps of when a parameter configuration instruction is received, carrying out parameter verification on a current configuration parameter according to a verification rule corresponding to the current configuration parameter in a parameter configuration instruction, and giving an alarm on a parameter with an abnormal verification result; and according to each verification rule in the preset rule chain and the preset rule operation frequency, carrying out timing cycle verification on the product configuration data corresponding to the product, and giving an alarm on the parameters with the abnormal verification results so as to monitor the product configuration data. According to the method, the current configuration parameters are firstly verified in real time, and then the product configuration data of the product is periodically and repeatedly verified in a circulating mode, so that the verification of some configuration parameters is prevented from being omitted, the problem data is prevented from being generated, the accuracy of the financial technology product configuration data is improved, and the manual operation is reduced.
Owner:WEBANK (CHINA)
Data writing method and device and verification method and device
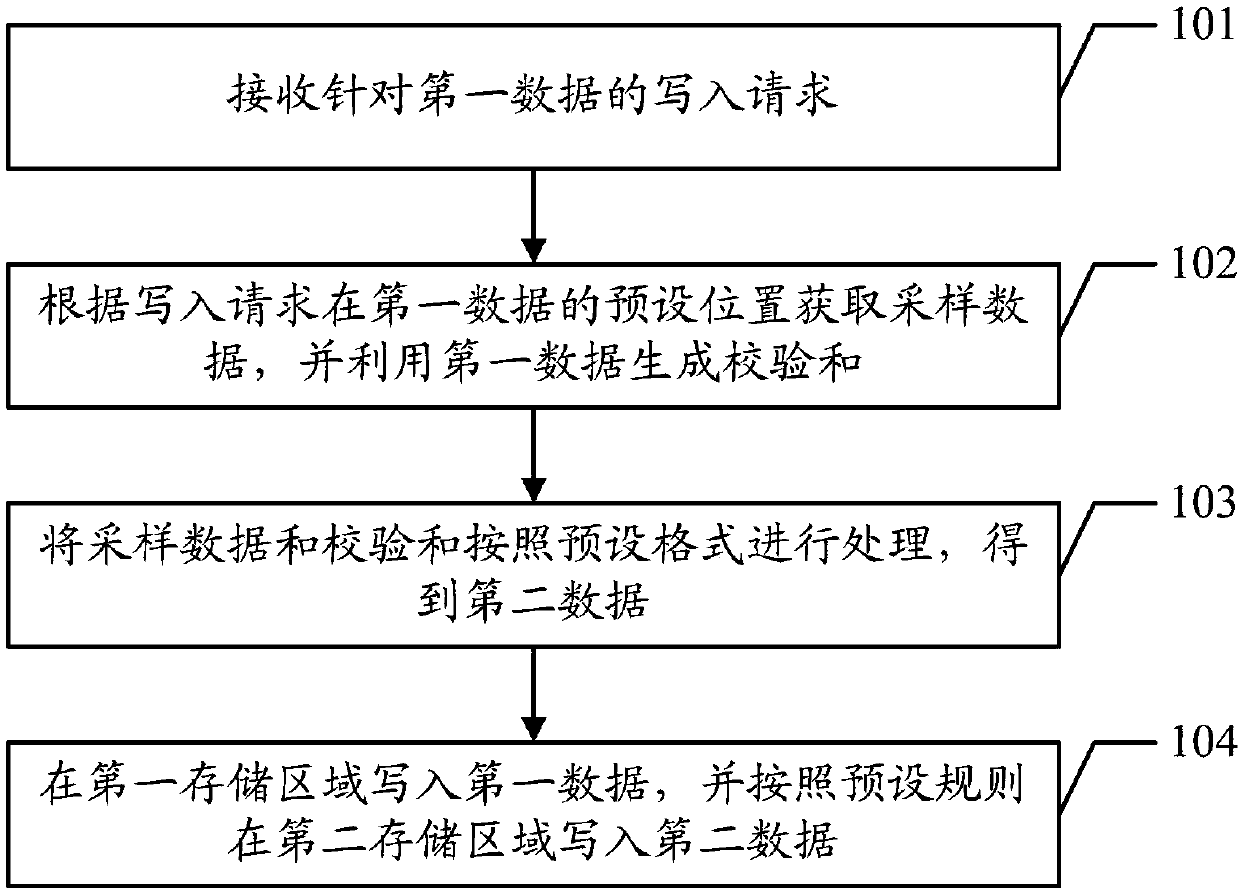
ActiveCN107844273AAvoid parityAvoid mistakesInput/output to record carriersValidation methodsChecksum
The embodiment of the invention discloses a data writing method and device, a verification method and device, a computer device and a readable storage medium, and aims to avoid misjudgment of checksum, improve the precision of data error detection by means of the checksum and reduce a negative influence on the system. The data writing method comprises the steps that a writing request aiming at first data is received; based on the writing request, sampling data is acquired in the preset position of the first data, and the checksum is generated by means of the first data; the sampling data and the checksum are processed according to a preset format, and second data is obtained, wherein the second data comprises at least two pieces of sampling data and at least one preset sum; the first datais written into a first storage area, and the second data is written into a second storage area according to a preset rule.
Owner:SANGFOR TECH INC
Verification method and device, electronic device and medium
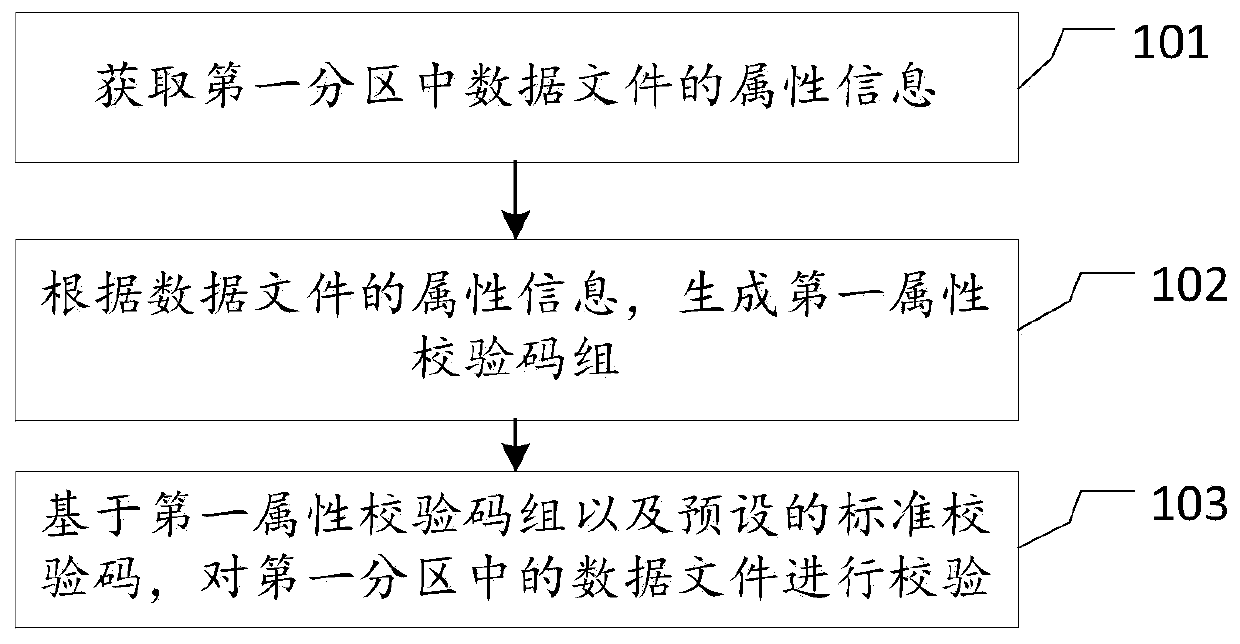
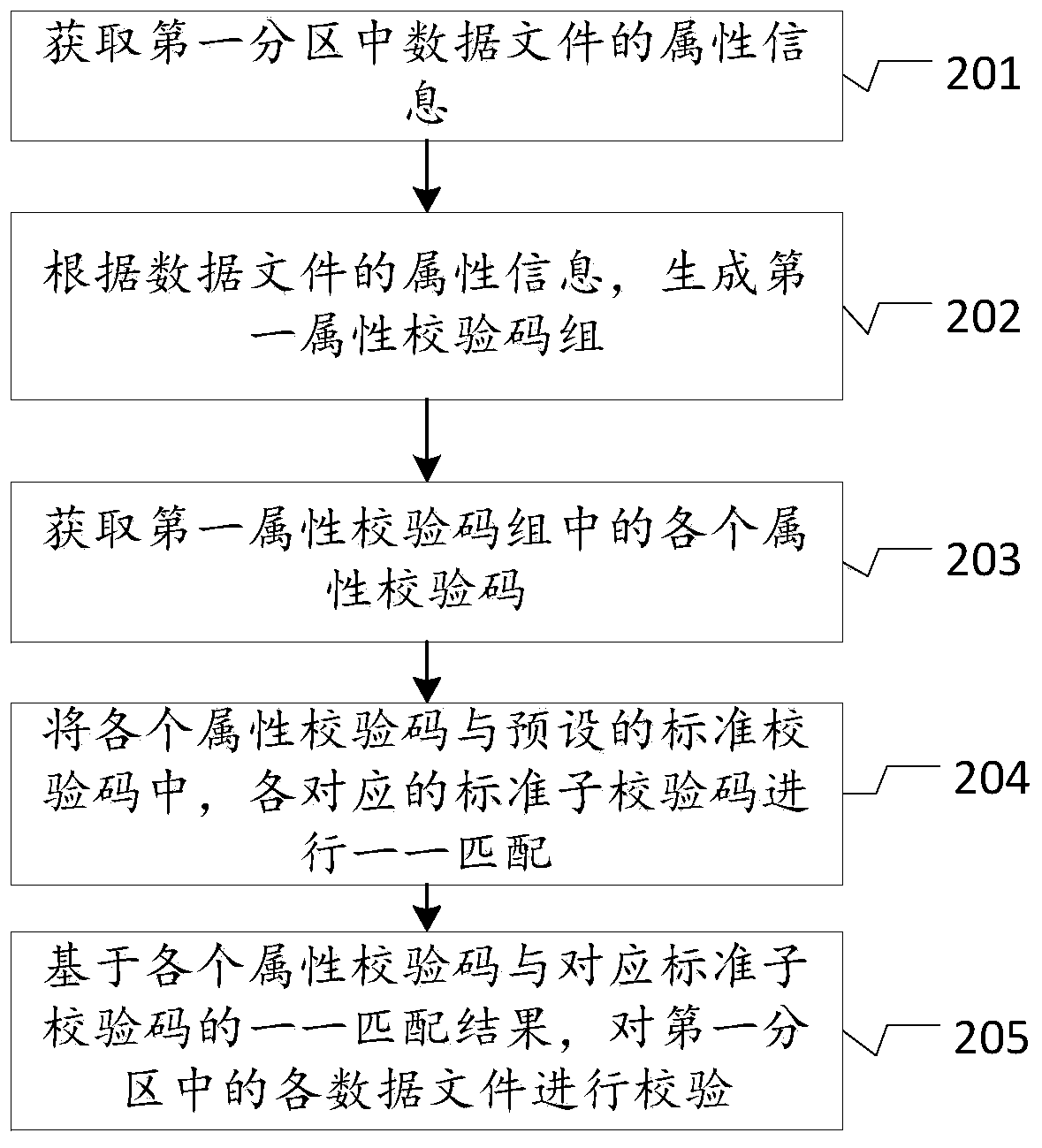
ActiveCN109889325AAvoid generatingGenerate first attribute check avoidEncryption apparatus with shift registers/memoriesUser identity/authority verificationData fileData content
The invention discloses a verification method and device, an electronic device and a medium. The method comprises the following steps: obtaining attribute information of each data file in a first partition, generating a first attribute check code group according to the attribute information of each data file, and checking the data files in the first partition based on the first attribute check code group and a preset standard check code. By applying the technical scheme of the invention, the corresponding attribute check code can be generated according to the attribute information of the datafile, and the check of the data file is completed based on the attribute check code. Therefore, the process of generating the check code according to all the data content information of the data fileand checking the check code in the related technology can be avoided, and the operation resources of the equipment are saved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
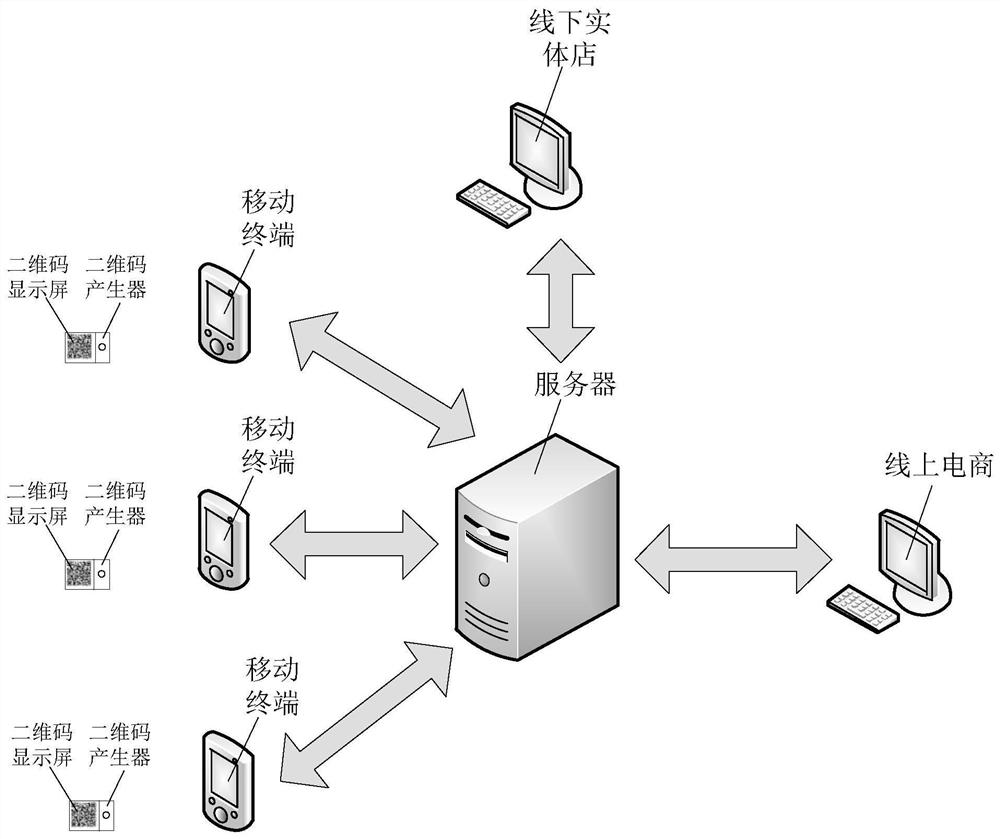
Tracking method of counterfeit products based on big data
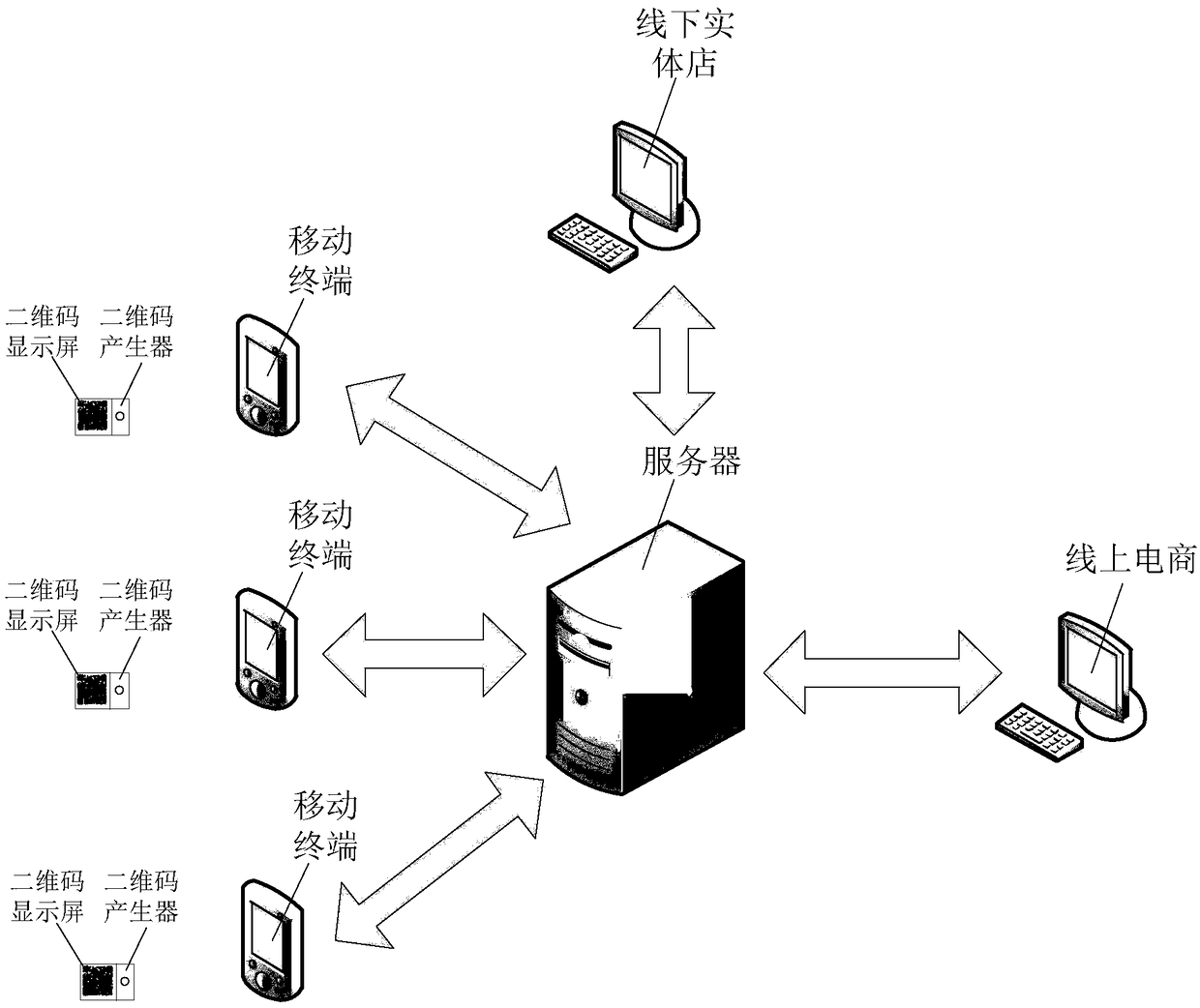
ActiveCN109461010AAvoid copy forgeryCounterfeiting is easy to be exposedCo-operative working arrangementsCommerceWeb pageBig data
The invention provides a counterfeit product tracking method based on big data, The system comprises a server, mobile terminal, Web page QR code set on the product, The two-dimensional code generatorand the two-dimensional code display screen. By counting verification frequency and sold product quantity, whether the counterfeit products are mainly sold online or offline is determined according tothe difference between the number of calibration times and the number of sold products, so that the counterfeit products can be tracked based on different situations, and the accuracy of the trackingof the counterfeit products can be improved.
Owner:CHONGQING TECH & BUSINESS INST
Quick adjustment technology for gaps between grinding rollers of coal mill and liner plate of grinding bowl
ActiveCN105080664AAvoid repeated adjustmentsAvoid successive measurementsGrain treatmentsEconomic benefitsEngineering
The invention discloses a quick adjustment technology for gaps between grinding rollers of a coal mill and a liner plate of a grinding bowl, and belongs to the technical field of maintenance technologies of coal mills. The quick adjustment technology is used for quickly adjusting the gaps between the grinding rollers and the liner plate of the grinding bowl. According to the quick adjustment technology, the gaps between the grinding rollers of the bowl type coal mill and the liner plate of the grinding bowl are limited through asbestos boards, the grinding rollers go down slowly till the grinding rollers make contact with the asbestos boards and the asbestos boards slightly resist pulling, then, the gaps between the grinding rollers and the liner plate of the grinding bowl are limited within the needed gaps, and therefore, the gaps between the grinding rollers and the liner plate of the grinding bowl are quickly adjusted. The quick adjustment technology for the gaps between the grinding rollers of the coal mill and the liner plate of the grinding bowl is innovative in the industry; the process is simplified, and the adjustment process is completed in one step; the tedious measurement and adjustment process is avoided; maintenance time is shortened, and the labor efficiency of maintainers is improved; the continuous workability of a coal pulverizing system is improved, and it is guaranteed that the whole production process is smooth; and the quick adjustment technology provides guarantees for high-efficiency production of enterprises, has remarkable economic benefits and has great application and popularization value.
Owner:WUYANG IRON & STEEL
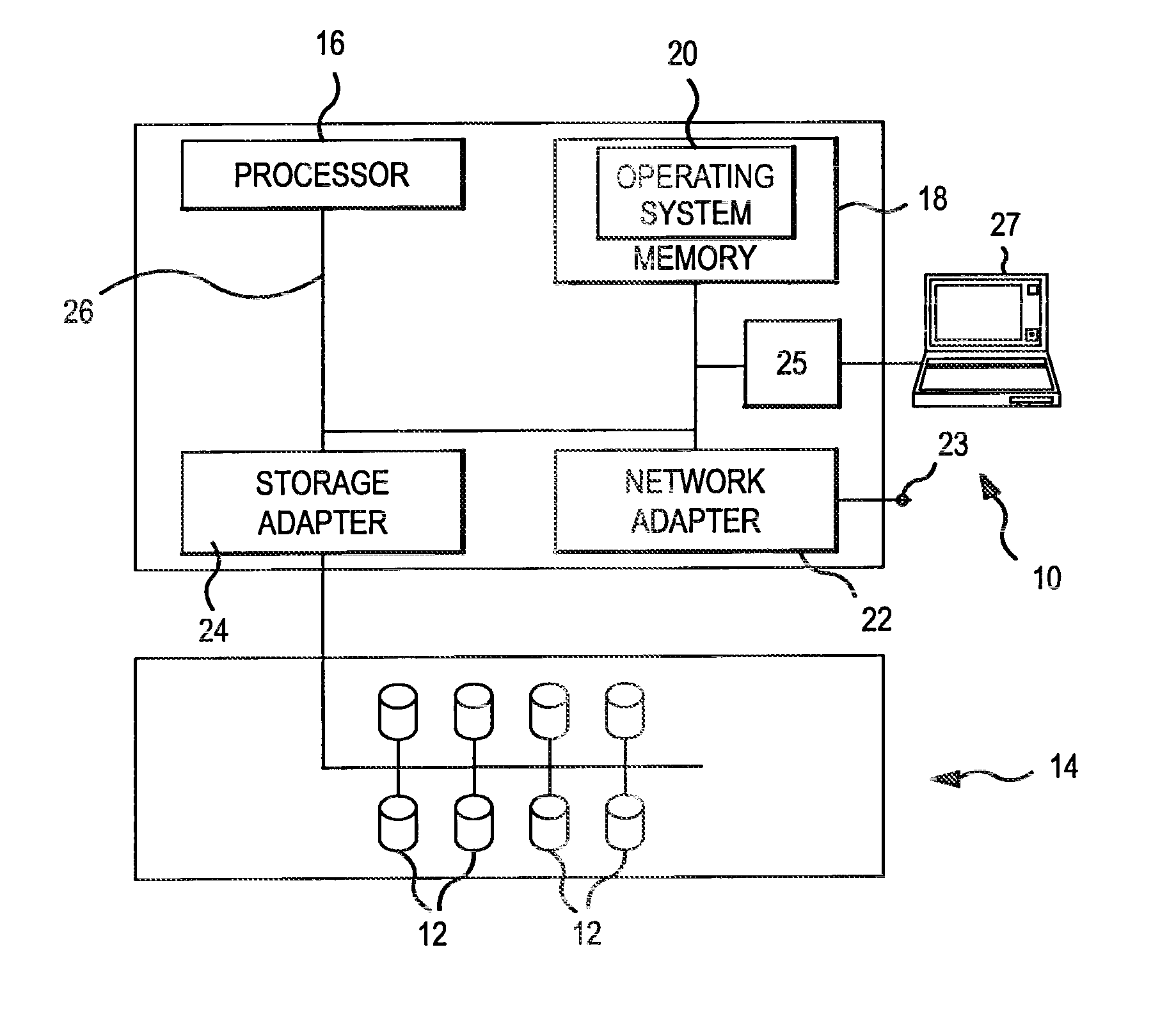
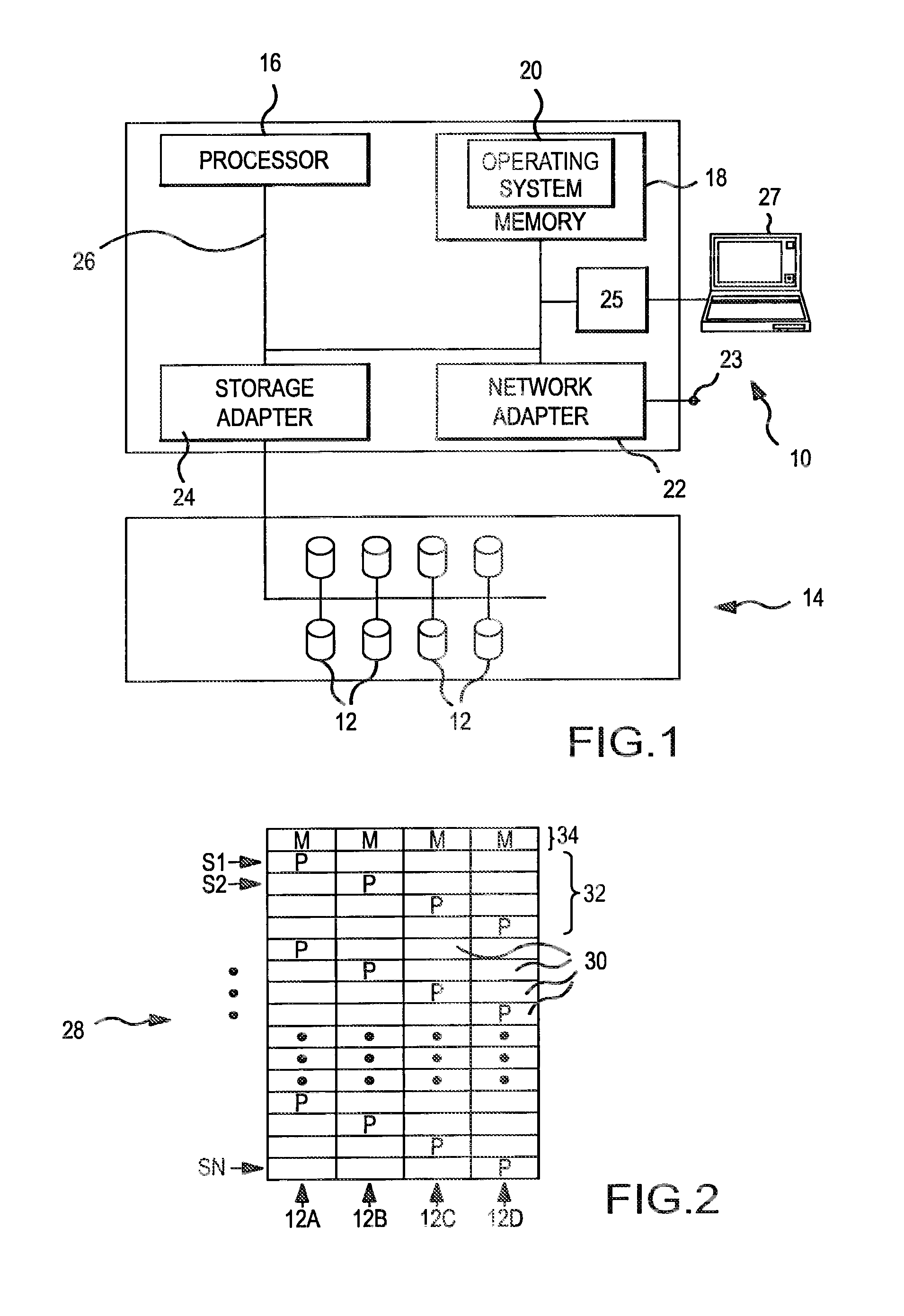
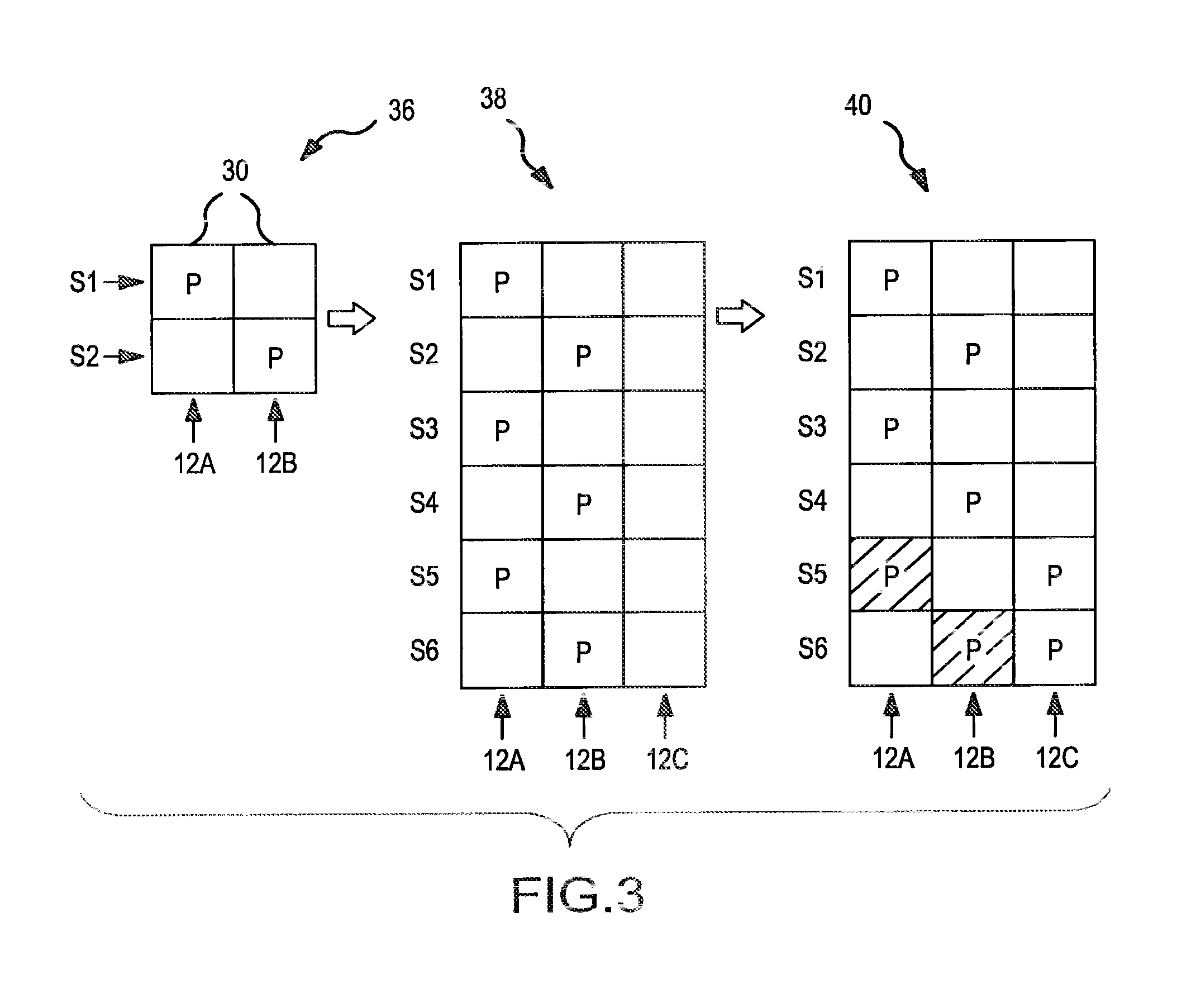
Dynamic load balancing of distributed parity in a raid array
ActiveUS20130304987A1Avoid parityEqually distributedError detection/correctionMemory systemsRAIDDynamic load balancing
A parity pattern defines a repeated distribution of parity blocks within a distributed parity disk array (“DPDA”). The parity pattern identifies on which disks the parity block or blocks for a stripe are located. When a new disk is added to the DPDA, the parity pattern is modified so that the distribution of parity blocks within the parity pattern is even. Parity blocks within the DPDA are then redistributed to conform with the modified parity pattern.
Owner:NETWORK APPLIANCE INC
Method for generating a secret or a key in a network
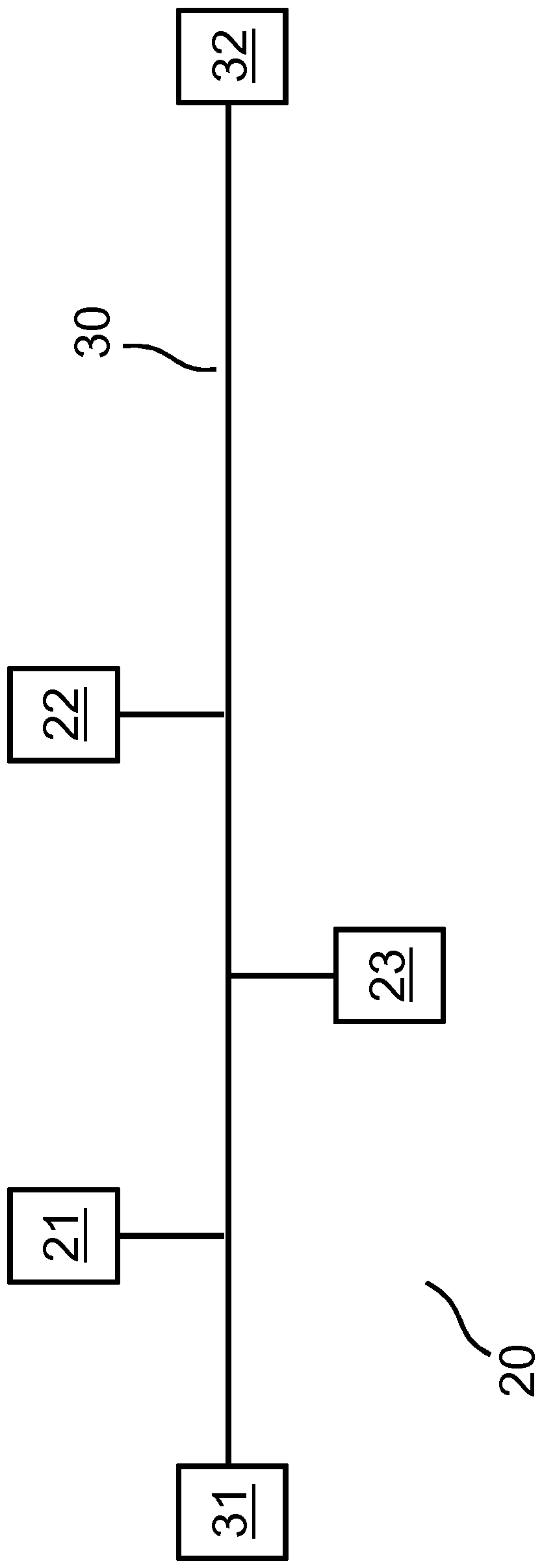
ActiveCN107836095AIncrease spawn rateRealize the automation structureKey distribution for secure communicationTelecommunicationsTransmission channel
Disclosed is a method for generating a secret or a key in a network (20). The network (20) comprises at least a first subscriber (21) and a second subscriber (22) and a common transmission channel (30) between at least the first (21) and second subscribers (22). The first subscriber (21) can output at least a first value (1) and a second value (0) and the second subscriber (22) can output at leastthe first value (1) and the second value (0) on the transmission channel, the first subscriber (21) generating a first sequence of subscriber values and the second subscriber (22) generating a secondsequence of subscriber values in order for the transmission to occur largely synchronously on the transmission channel (30); and the first subscriber (21) and the second subscriber (22) each generatea common secret or a common key, the first subscriber (21) doing so on the basis of information about the first sequence of subscriber values and on the basis of a sequence of superposed values resulting from a superposition of the second sequence of subscriber values onto the first sequence of subscriber values on the transmission channel (30), and the second subscriber (22) doing so on the basis of information about the second sequence of subscriber values and on the basis of the sequence of superposed values resulting from the superposition of the second sequence of subscriber values ontothe first sequence of subscriber values on the transmission channel (30). At least the first subscriber (21) and the second subscriber (22) determine a sequence of test values in accordance with the resulting sequence of superposed values and output same on the transmission channel (30).
Owner:ROBERT BOSCH GMBH
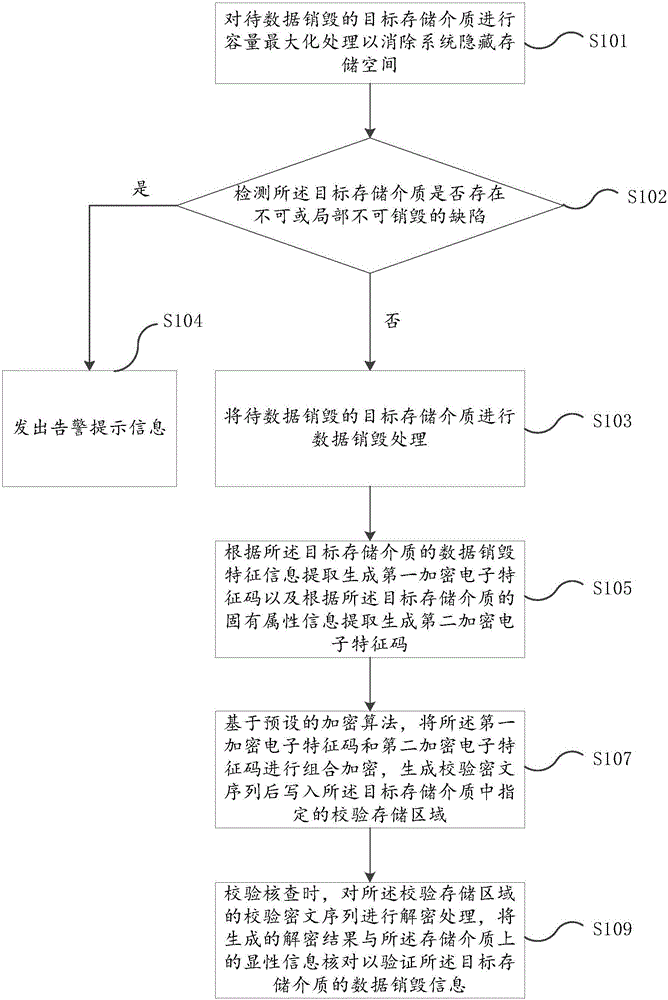
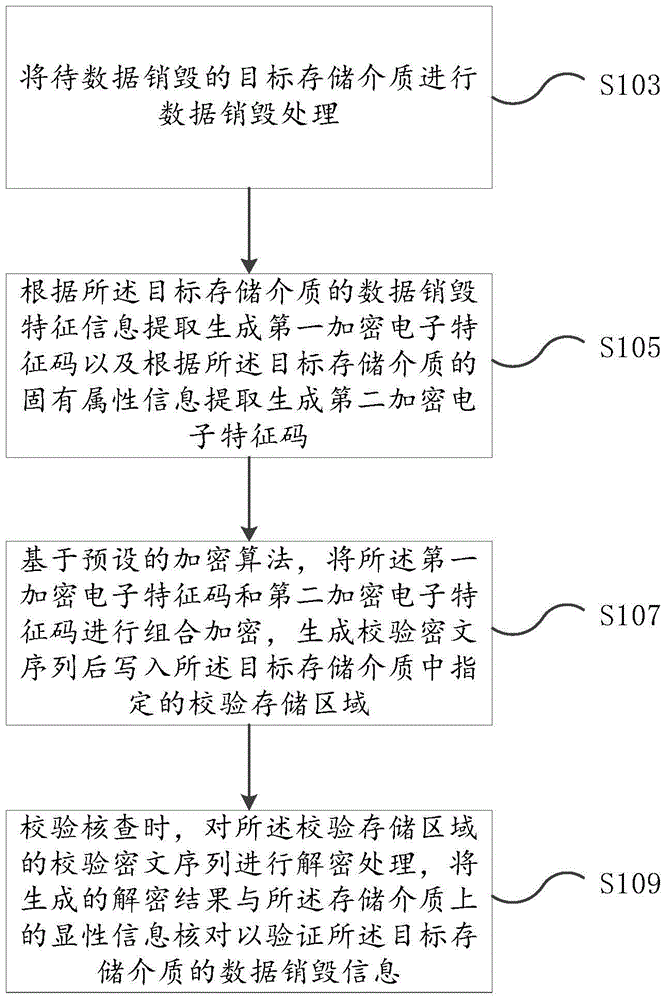
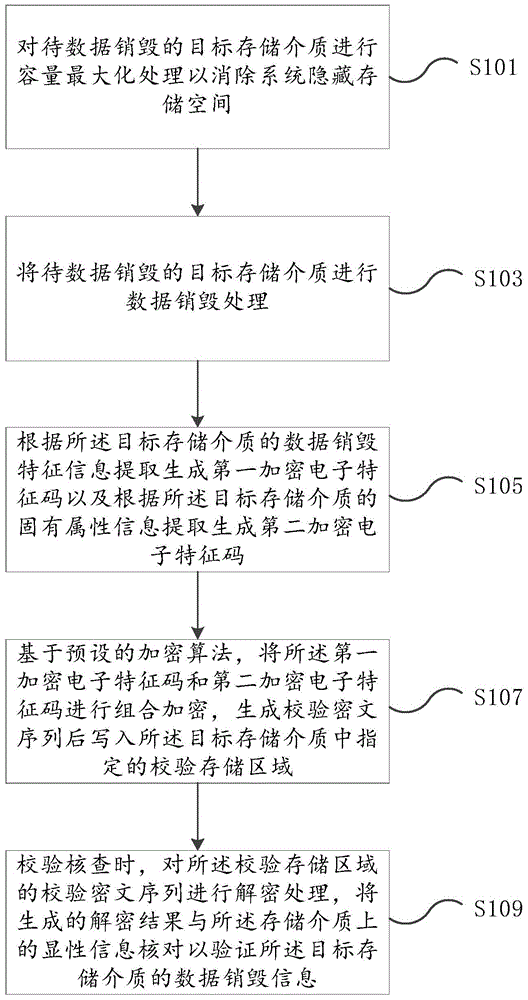
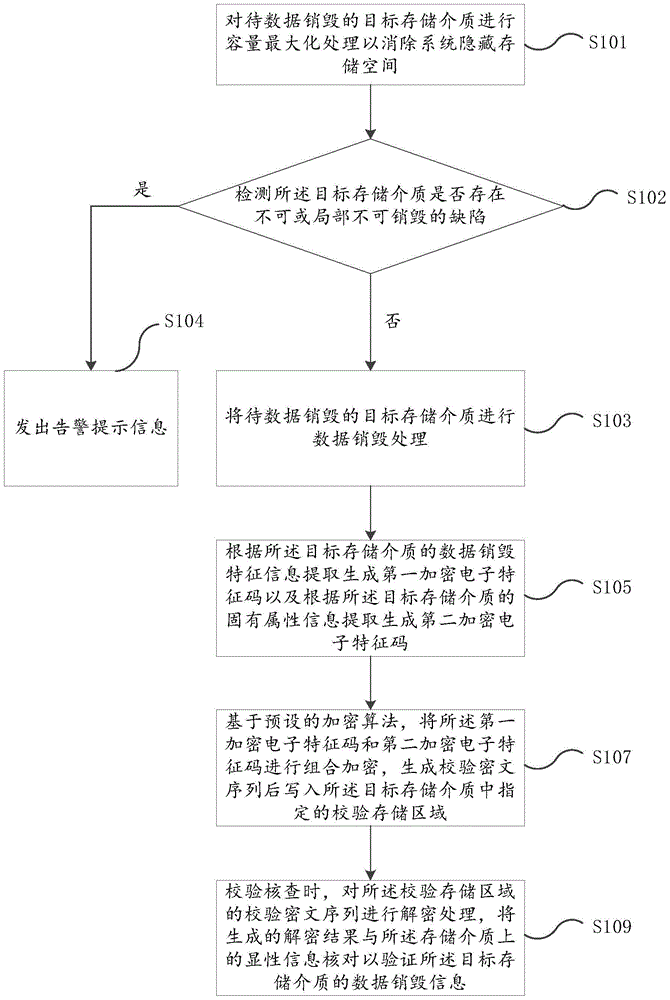
Verification method for data destruction of storage medium
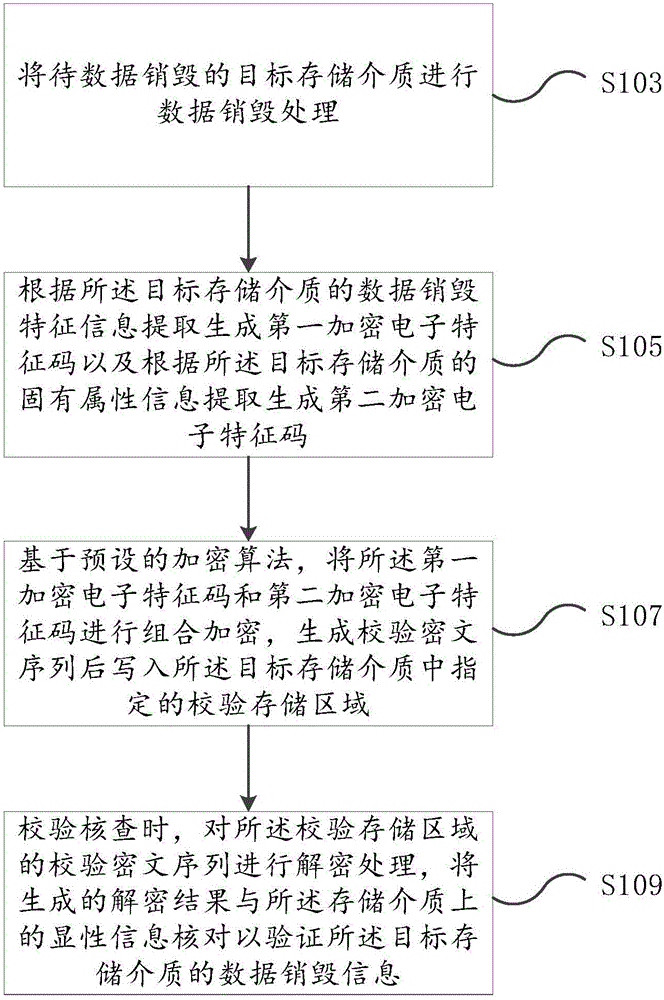
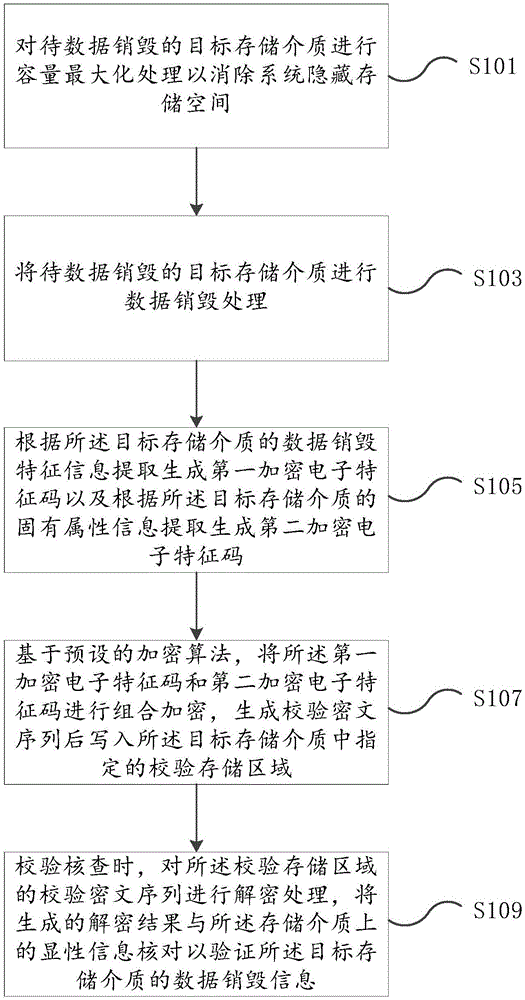
ActiveCN105117302AAvoid parityReliable calibrationRedundant data error correctionCiphertextFeature code
The embodiment of the invention provides a verification method for data destruction of storage medium. The method comprises the following steps of: destructing data of a target storage medium to be subjected to data destruction; extracting and generating a first encryption electronic feature code according to data destruction feature information of the target storage medium and extracting and generating a second encryption electronic feature code according to inherent attribute information of the target storage medium; based on a preset encryption algorithm, performing combined encryption on the first encryption electronic feature code and the second encryption electronic feature code, and generating a verification ciphertext sequence and writing the sequence into a specified verification storage area in the target storage medium; while verifying and checking, decrypting the verification ciphertext sequence in the verification storage area, and checking the generated decryption result with display information on the storage medium to verify the data destruction information of the target storage medium. With the method provided by the invention, by technological means, an existing problem of data leakage caused by artificial negligence or deliberate inaccuracy of verification can be solved.
Owner:深圳青柠存储技术有限公司
Method of and system for constructing valid data for memory-based tests
Owner:AGILENT TECH INC
Method and device for searching based on mobile equipment
ActiveCN104504039AImprove acquisition efficiencyQuality improvementWeb data indexingEnergy efficient computingResource consumptionMobile device
The embodiment of the invention provides a method and a device for searching based on mobile equipment. The method comprises the following steps: transmitting a search request to a search engine in the mobile equipment; receiving a search result page returned by the search engine aiming at the search request, wherein the search result page comprises one or more data block objects, and each data block object has a characteristic region; displaying the one or more data block objects according to a screen size of the mobile equipment; acquiring one or more pieces of comment information corresponding to the data block objects to which the characteristic regions belong when the characteristic regions are triggered; displaying the one or more pieces of comment information. According to the embodiment of the invention, the user time and the energy consumption are reduced, the system resource consumption of the mobile equipment and other websites is also reduced, the occupation of network bandwidth is also reduced, and the efficiency, the quality and the capacity for acquiring the information are greatly improved.
Owner:BEIJING QIHOO TECH CO LTD
Sand casting production technology
InactiveCN108188346AAvoid parityAvoid hardnessFoundry mouldsFoundry coresProduction lineSand casting
The invention discloses a sand casting production technology. The sand casting production technology comprises the following specific steps: raw material inspection, core making, shaping, mold matching, melting and pouring, in-mold cooling, shake-out, heat treatment, cleaning and polishing, casting examination, machining, deburring, rough cleaning, pressure testing, final inspection, final cleaning and putting in storage. With adoption of the technology, multiple inspection procedures such as raw material inspection, mold matching, casting examination, pressure testing and final inspection areperformed respectively, so that manufacturing precision and quality can be monitored in the whole production process of castings, and production of defective products is prevented; meanwhile, the mold is manufactured through front procedures of core making and shaping, so that the mold is produced specially for batch products, and production efficiency of a production line is increased greatly.
Owner:鹰普机械(宜兴)有限公司
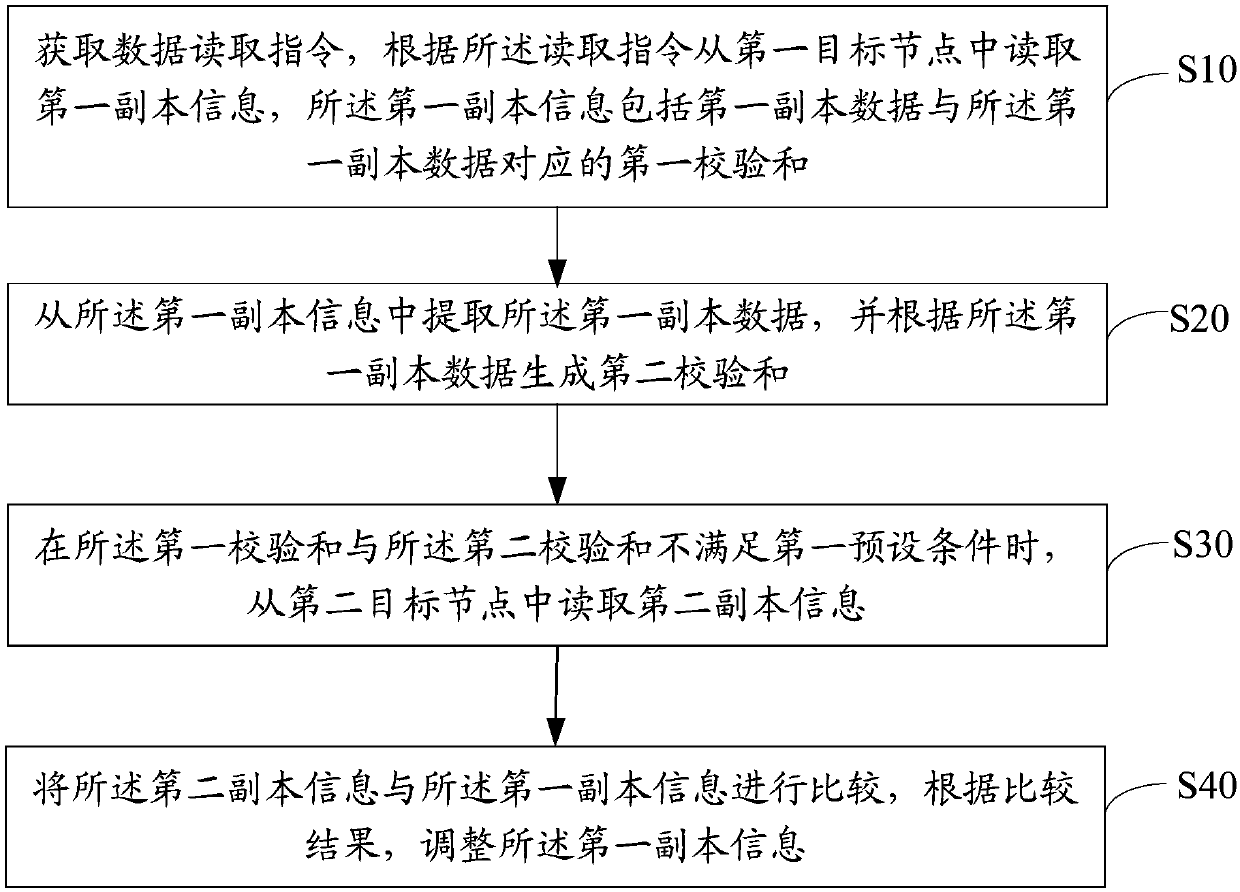
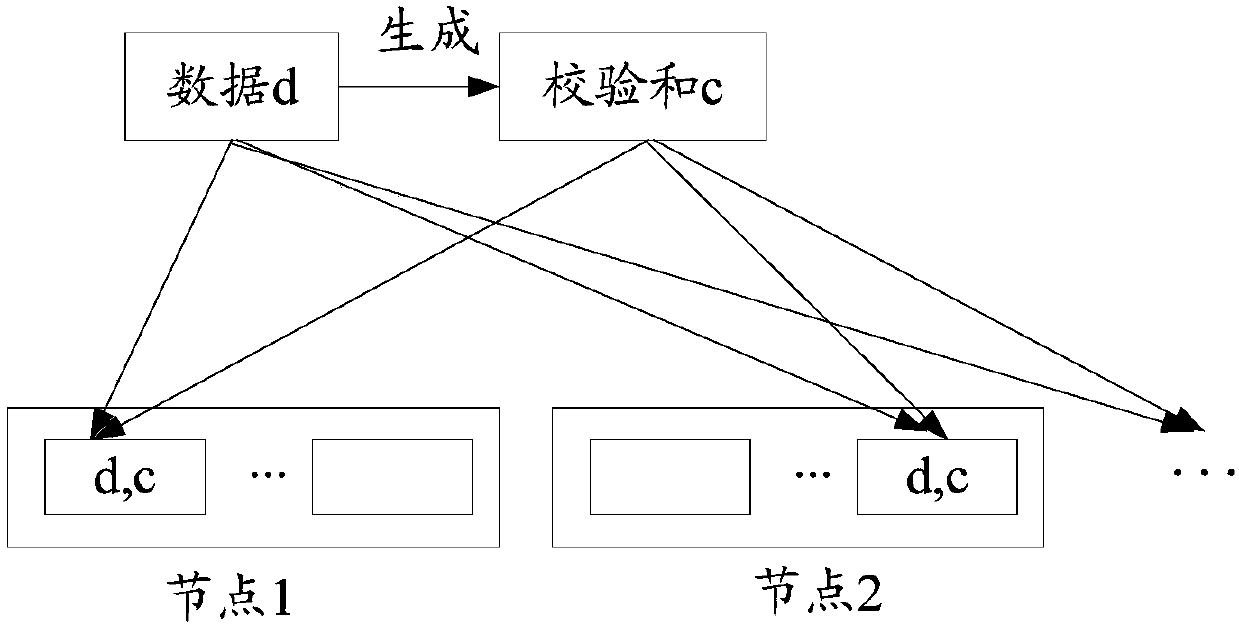
Data processing method and device based on multiple verification and storage medium
InactiveCN108052413AAvoid parityAvoid misjudgmentDigital data protectionRedundant data error correctionChecksumData error
The invention discloses a data processing method and device based on multiple verification and a storage medium. The method includes: acquiring a data reading instruction, and reading first copy information from a first target node according to the reading instruction, wherein the first copy information includes first copy data and a first checksum corresponding to the first copy data; extractingthe first copy data from the first copy information, and generating a second checksum according to the first copy data; reading second copy information from a second target node when the first checksum and the second checksum do not meet a first preset condition; and comparing the second copy information and the first copy information, and adjusting the first copy information according to a comparison result. According to the method, checksum misjudgment can be effectively detected and avoided through multiple verification on multiple copies, precision of using the checksums to detect data errors can be improved, and negative impacts on a system can be reduced.
Owner:SANGFOR TECH INC
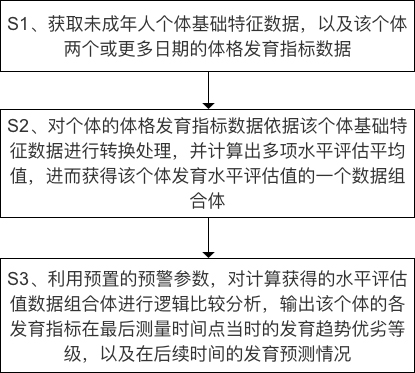
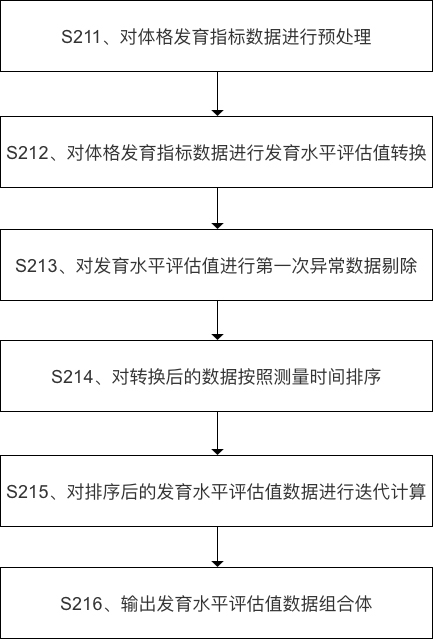
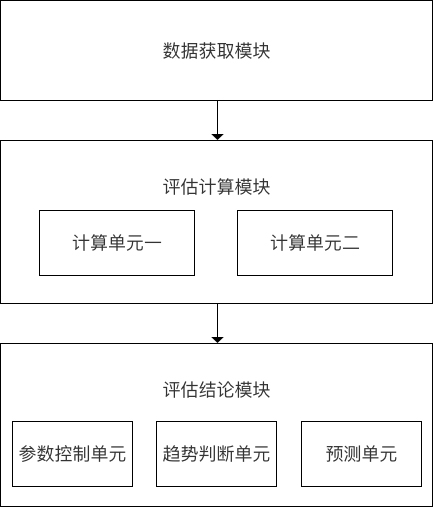
Juvenile physique development trend evaluation method and device
The invention discloses a juvenile physique development trend evaluation method and device. The method comprises the steps of obtaining juvenile individual basic feature data and physique developmentindex data of two or more dates of an individual; converting the physique development index data of the individual, and performing statistical calculation to obtain a data combination of the individual development level evaluation value; and performing logic analysis according to the data combination body, and outputting the development trend quality grade of each development index of the individual at the last measurement time point and the development prediction condition at the subsequent time. Compared with the prior art and scheme, the standardization method and device can replace experiential manual judgment of professionals to a certain extent, and a user does not have professional knowledge bases, so that the cost can be effectively saved, the efficiency can be effectively improved, and the method and device can be further applied to businesses such as real-time evaluation and interpretation of growth and development conditions of juveniles, health state early warning and the like.
Owner:北京菁医林国际医院管理有限公司
Website content data display method and device, equipment and storage medium
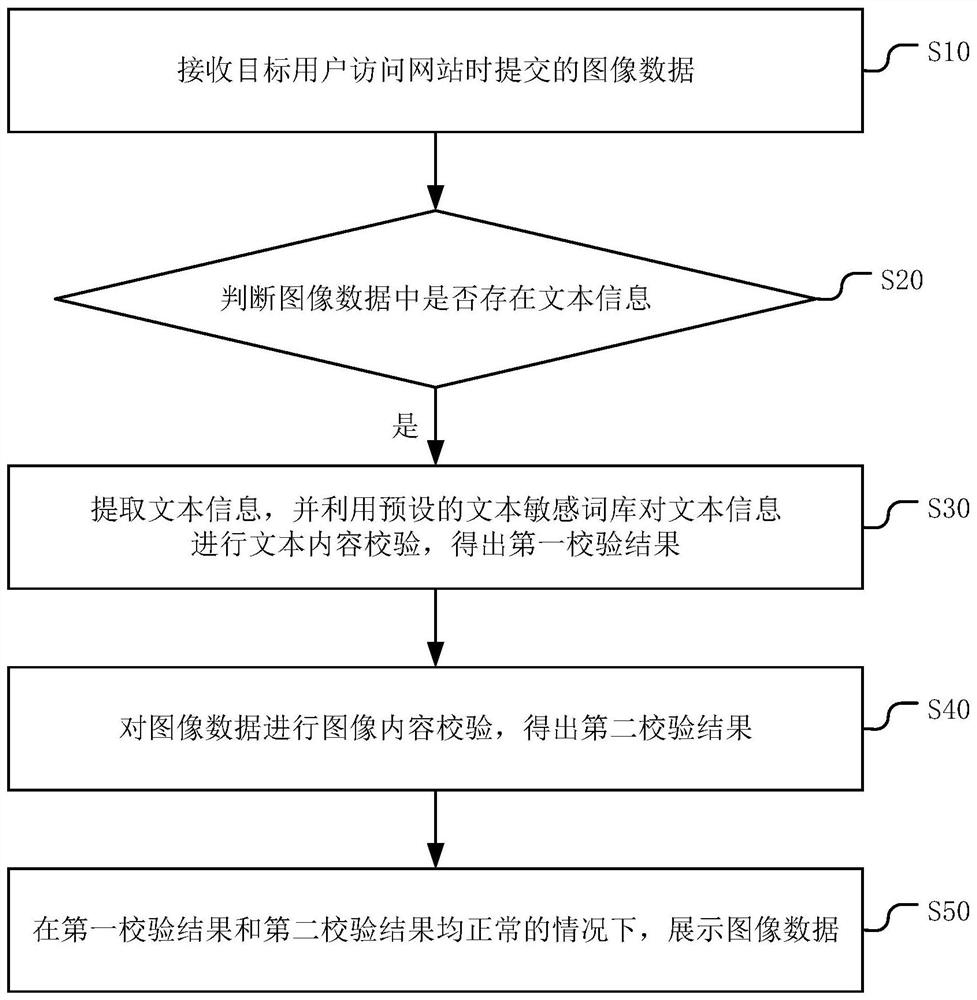
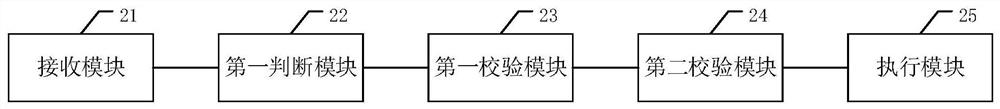
PendingCN111767493ASensitive verification is complete and accurateAvoid showingNatural language data processingImage data processing detailsData displayWeb site
The invention discloses a website content data display method. The method comprises the following steps of receiving image data submitted when a target user accesses the website, judging whether textinformation exists in the image data or not, if yes, extracting the text information, and performing text content verification on the text information by utilizing a preset text sensitive word bank toobtain a first verification result, performing image content verification on the image data to obtain a second verification result, and under the condition that both the first verification result andthe second verification result are normal, displaying the image data. According to the method, the mode of determining whether the text information in the image data contains the sensitive information or not according to the text sensitive word bank is more accurate; and two modes are used for verification and are combined to obtain a verification result, so that sensitive verification of the image data is more complete and accurate, and sensitive information can be further prevented from being displayed on a website. The invention furthermore discloses a website content data display device and equipment, and a computer readable storage medium, which all have the above beneficial effects.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
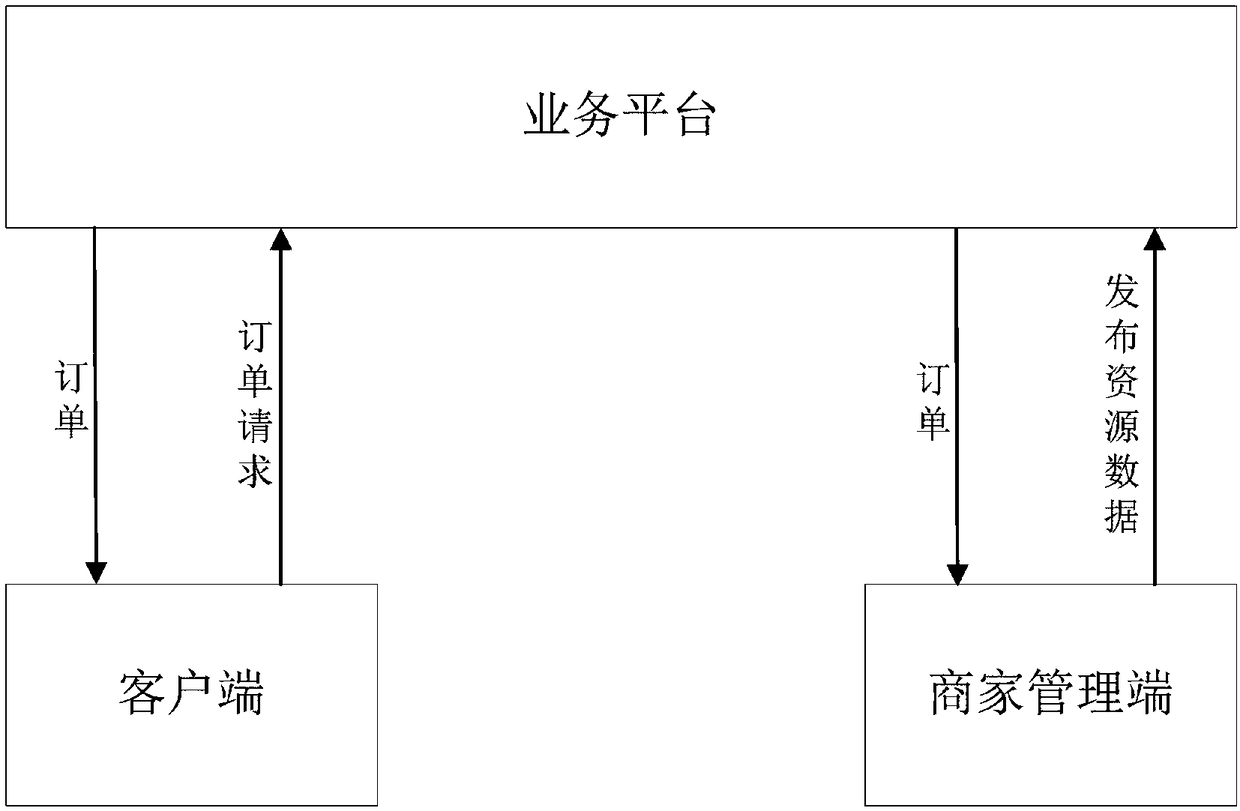
Business object information sending method, publishing method, server and client
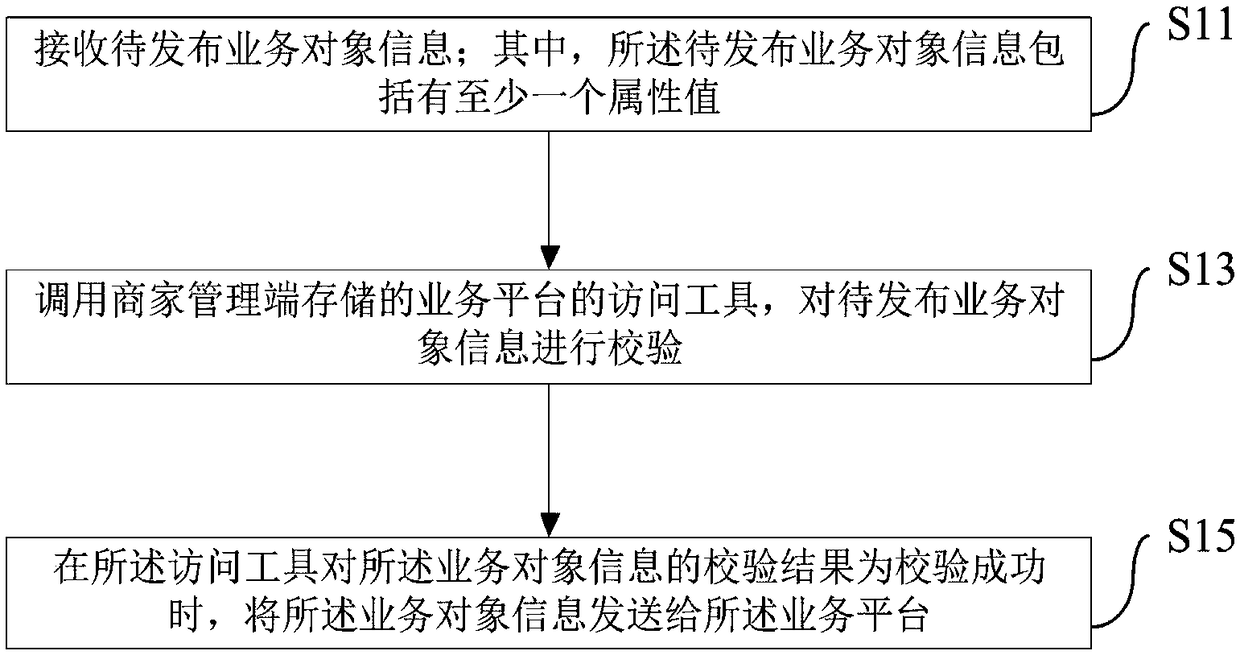
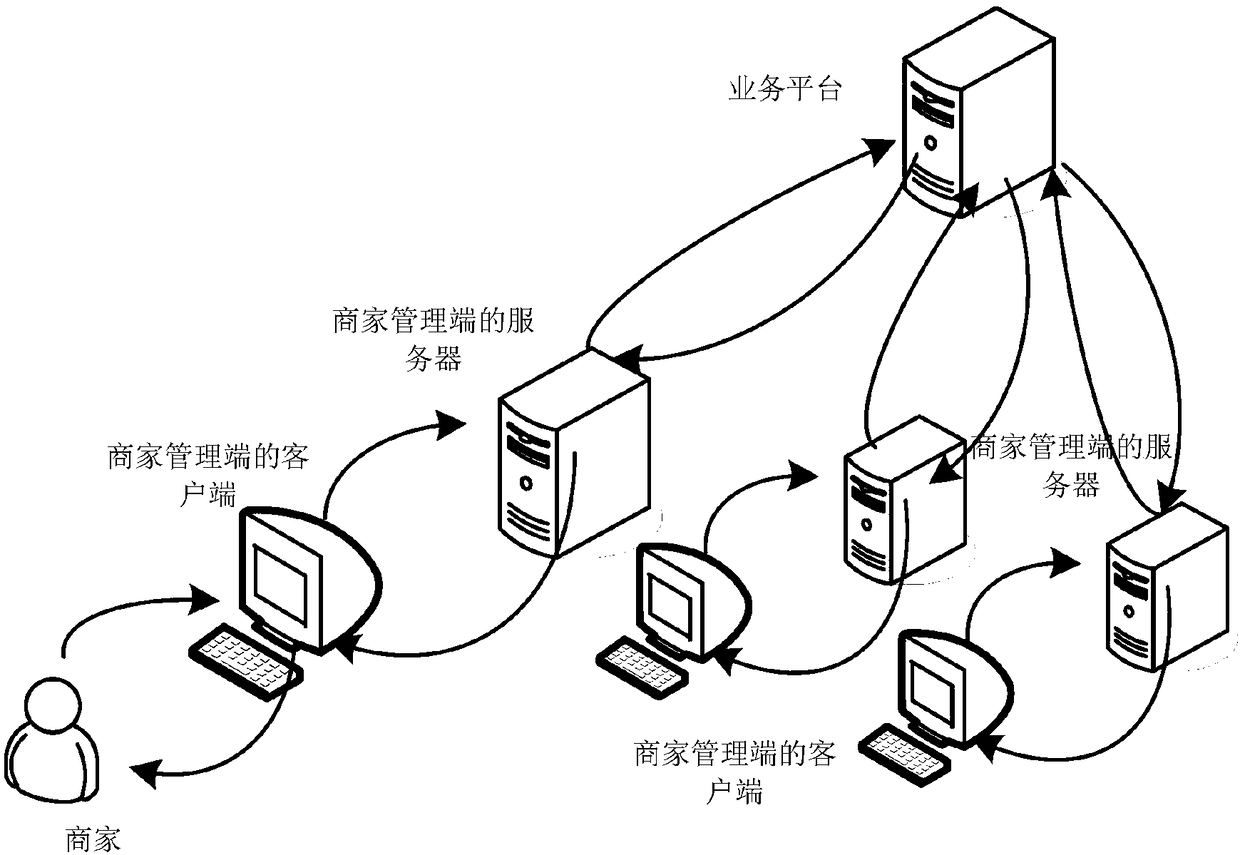
The embodiments of the present invention provides a business object information sending method, a business object information publishing method, a server and a client. The business object informationsending method includes the following steps that: business object information to be published is received, wherein the business object information to be published contains at least one attribute value; and the access tool of a business platform stored by a management terminal is called, so that the business object information to be published can be provided to the access tool, wherein the access tool contains a verification rule set, wherein the verification rule set comprises at least one verification rule, wherein the verification rule is used to verify the attribute values; when the resultof the verification of the business object information to be published by the access tool indicates successful verification, the business object information to be published is sent to the business platform, so that the business platform can publish the business object information to be published. With the business object information sending method of the invention adopted, the publishing efficiency of business object information can be improved.
Owner:ALIBABA GRP HLDG LTD
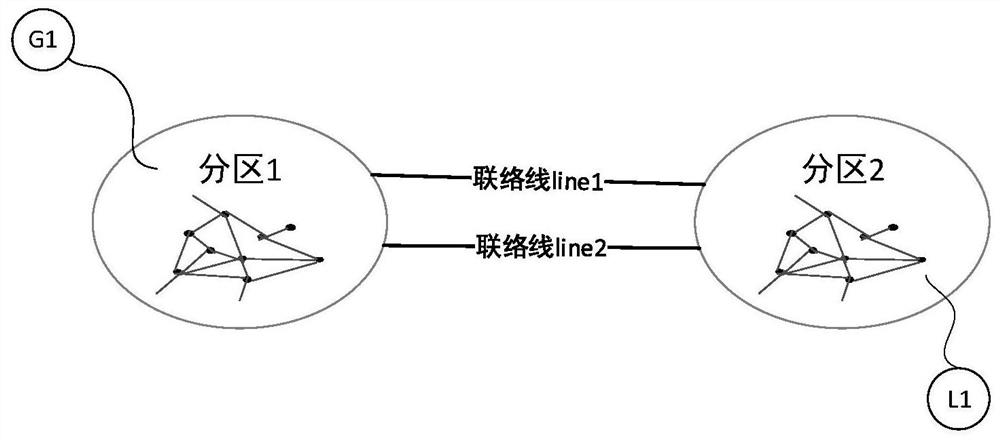
Method and system for simplifying point-to-point transaction network of partitioned power market
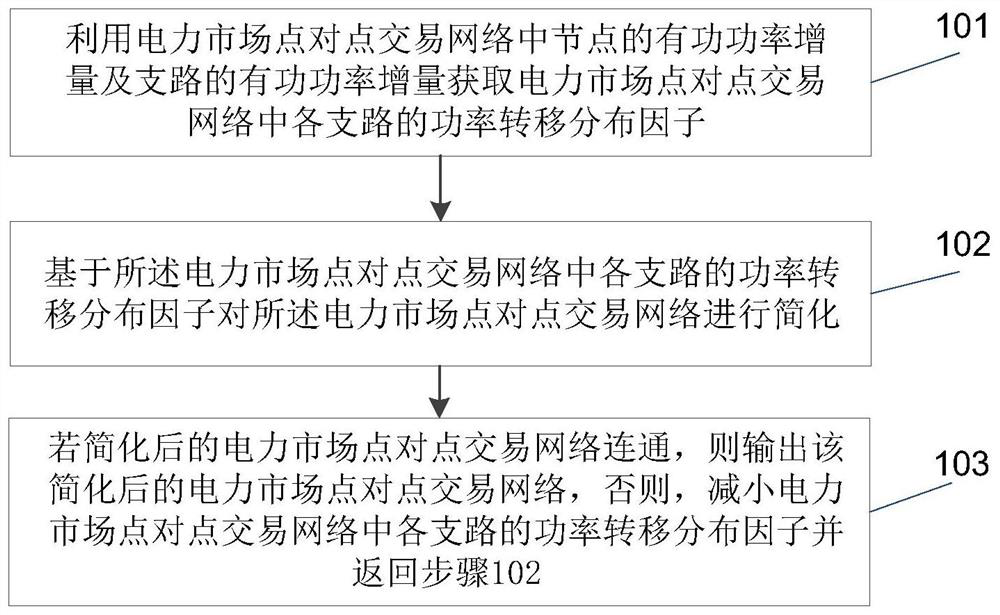
PendingCN111724011AIntuitive cullingAvoid adjustmentBuying/selling/leasing transactionsResourcesSecurity checkReal-time computing
The invention relates to a method and a system for simplifying a point-to-point transaction network of a partitioned power market. The method comprises the following steps of: 101, acquiring a power transfer distribution factor of each branch in the point-to-point transaction network of the power market by utilizing an active power increment of a node and an active power increment of each branch in the point-to-point transaction network of the power market; 102, simplifying the point-to-point transaction network of the power market based on the power transfer distribution factor of each branchin the point-to-point transaction network of the power market; and 103, if the simplified point-to-point transaction network of the power market is connected, outputting the simplified point-to-pointtransaction network of the power market, otherwise, reducing the power transfer distribution factor of each branch in the point-to-point transaction network of the power market and returning to the step 102. According to the technical scheme provided by the invention, various power transactions can be quicker and more intuitive, the purpose of effective analysis can be achieved, meanwhile, transaction information can be completely reserved, and the high efficiency and accuracy of security check load flow calculation are ensured.
Owner:CHINA ELECTRIC POWER RES INST +2
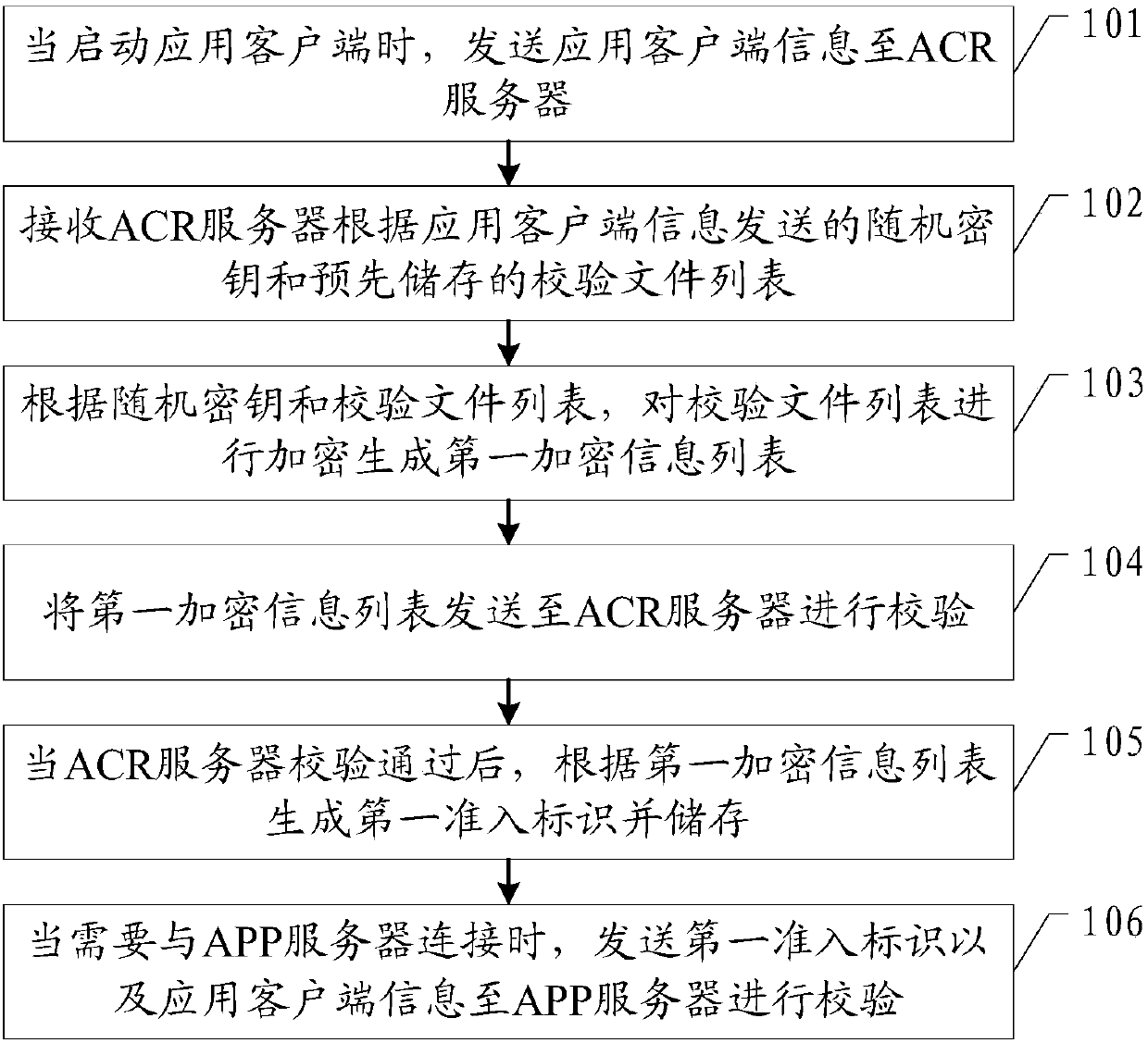
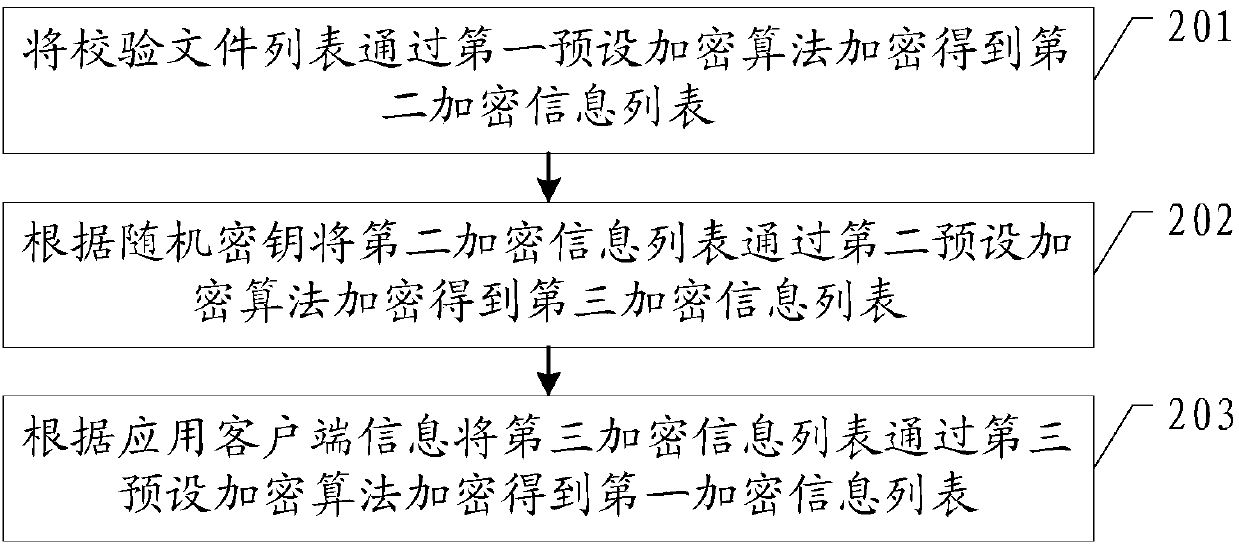
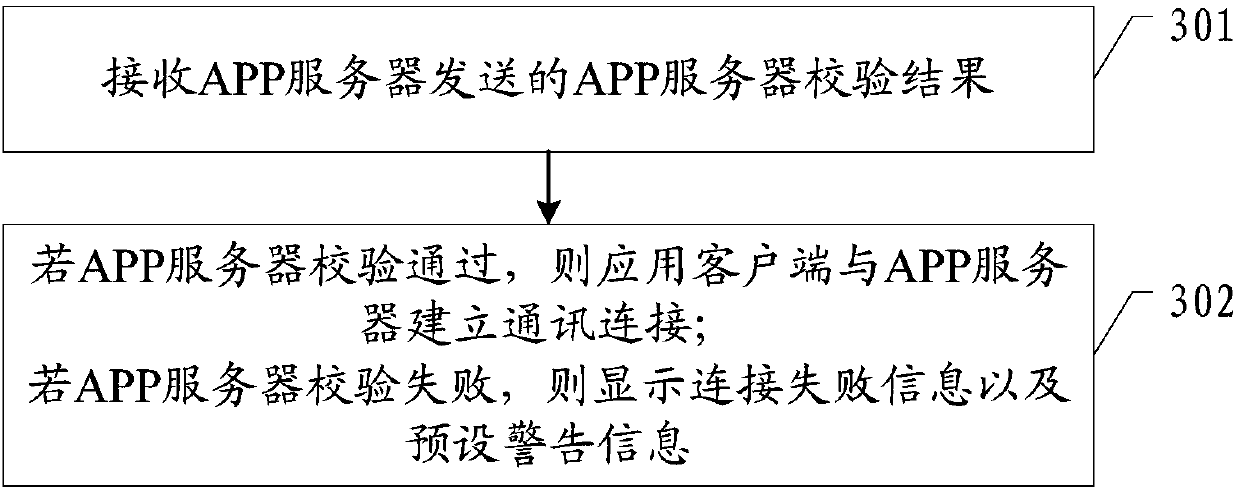
Safety protection method of application program, application client and ACR server
ActiveCN109995700AAvoid parityPrevent intrusionComputer security arrangementsTransmissionFirst admissionApplication software
The invention provides an application security protection method, an application client and an ACR server, and the application security protection method comprises the steps: sending application client information to the ACR server; receiving a random key sent by the ACR server and a pre-stored check file list; according to the random key and the check file list, encrypting the check file list togenerate a first encrypted information list; sending the first encrypted information list to an ACR server for verification; after the ACR server passes the verification, generating a first admissionidentifier according to the first encryption information list and storing the first admission identifier; and when needing to be connected with the APP server, sending the first admission identifier and the application client information to the APP server for verification. According to the embodiment of the invention, through a dual-verification mode, a hacker is prevented from obtaining sensitiveinformation of a user or disseminating illegal information by cracking an application client, so that the information security of the user is protected.
Owner:北京易安睿龙科技有限公司
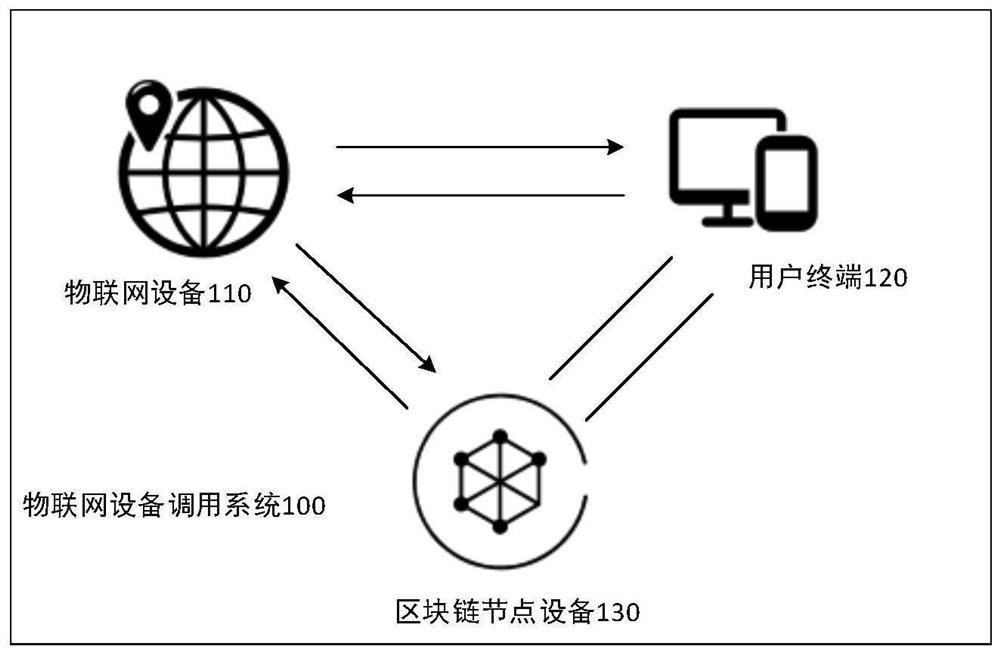
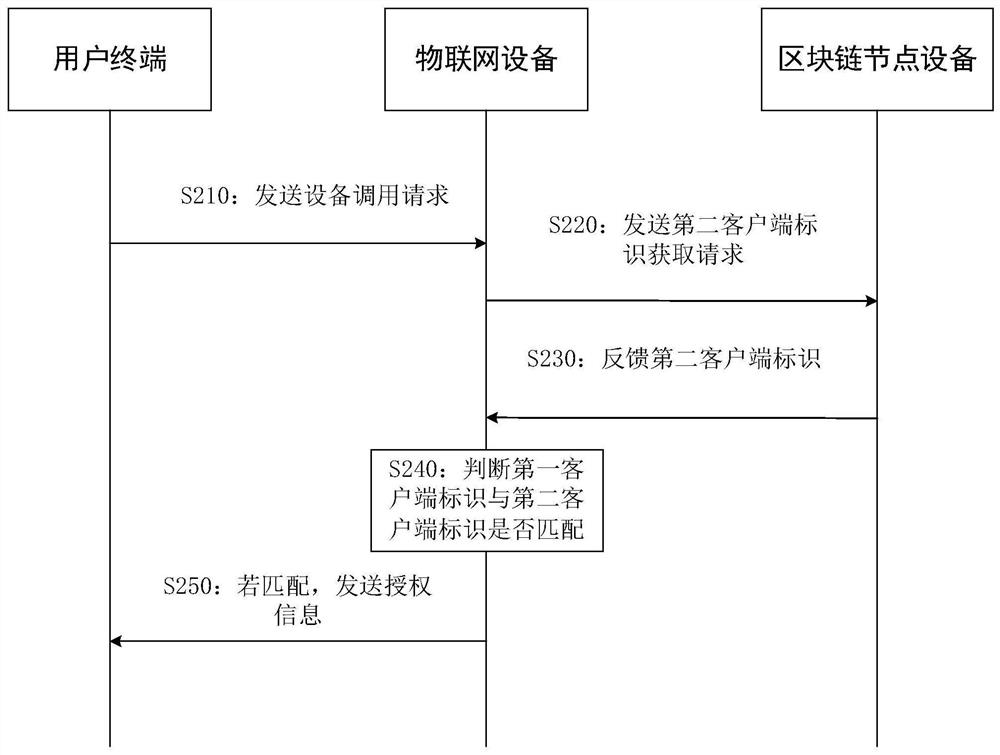
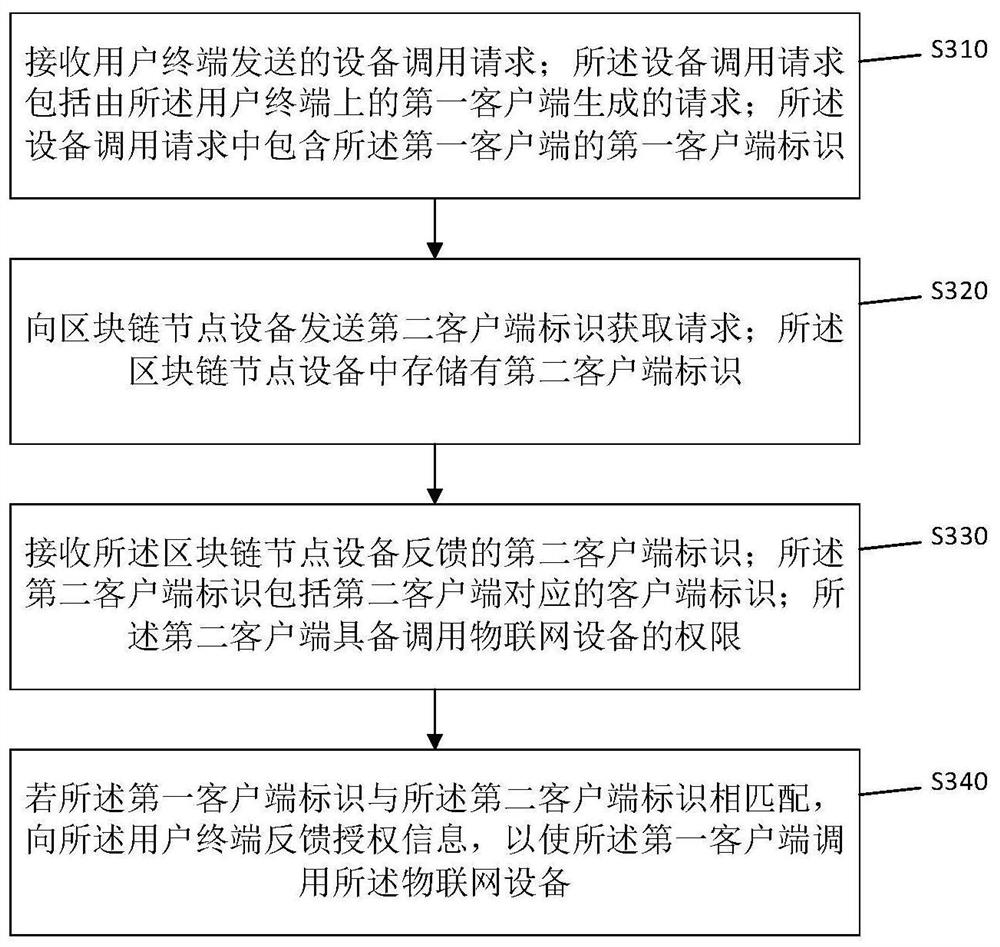
Internet-of-Things equipment safety calling method, device and equipment based on block chain
InactiveCN111835775AAvoid parityEnsure safetyKey distribution for secure communicationUser identity/authority verificationThe InternetEngineering
The embodiment of the invention provides an Internet-of-Things equipment safety calling method, device and equipment based on a block chain. The method comprises the following steps: receiving an equipment calling request sent by a user terminal, wherein the equipment calling request comprises a request generated by a first client on the user terminal, and the equipment calling request comprises afirst client identifier of the first client; sending a second client identifier acquisition request to the block chain node device, wherein a second client identifier is stored in the block chain node device, the second client identifier comprises an identifier corresponding to the second client, the second client has the authority of calling the Internet-of-Things equipment; and receiving a second client identifier fed back by the block chain node device; and if the first client identifier is matched with the second client identifier, feeding back authorization information to the user terminal, so that the first client calls the Internet-of-Things equipment. According to the method, the identity of the first client is verified, so that the calling security is ensured.
Owner:NORTH CHINA ELECTRICAL POWER RES INST +2
A verification method for data destruction of storage media
Owner:深圳青柠存储技术有限公司
Counterfeit product tracking method based on big data
ActiveCN109461010BAvoid copy forgeryCounterfeiting is easy to be exposedCo-operative working arrangementsCommerceData scienceReliability engineering
The present invention provides a method for tracking counterfeit products based on big data. The system includes a server, a mobile terminal, a webpage two-dimensional code set on the product, a two-dimensional code generator and a two-dimensional code display screen. Count the number of sold products, and determine whether the counterfeit products are mainly sold online or offline according to the difference between the two, so that counterfeit products can be tracked based on different situations, and the accuracy of counterfeit product tracking can be improved .
Owner:CHONGQING TECH & BUSINESS INST
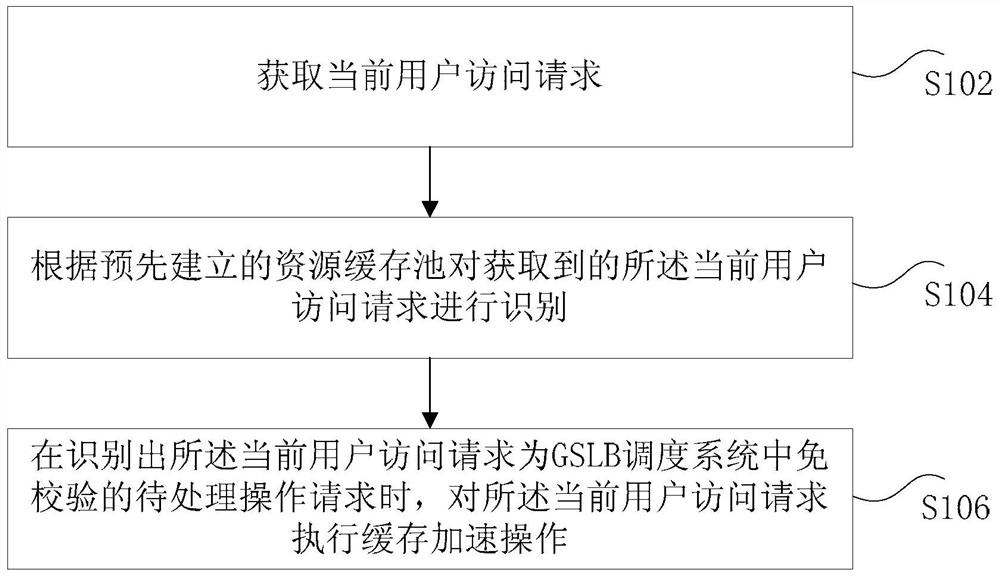
Data processing method and device of gslb dispatching system
ActiveCN106657201BThe effect of improving data processing efficiencyOvercoming the problem of low processing efficiencyTransmissionPoolReal-time computing
The invention provides a data processing method and device of a GSLB scheduling system. Wherein, the method includes: obtaining the current user access request; identifying the obtained current user access request according to the pre-established resource cache pool; identifying that the current user access request is a pending operation request exempt from verification in the GSLB scheduling system , the cache acceleration operation is performed on the current user access request. Through the present invention, the problem of low processing efficiency caused by adopting the existing traversal verification processing method is solved, and the effect of improving data processing efficiency and further ensuring the success rate of data processing is achieved.
Owner:ZTE CORP
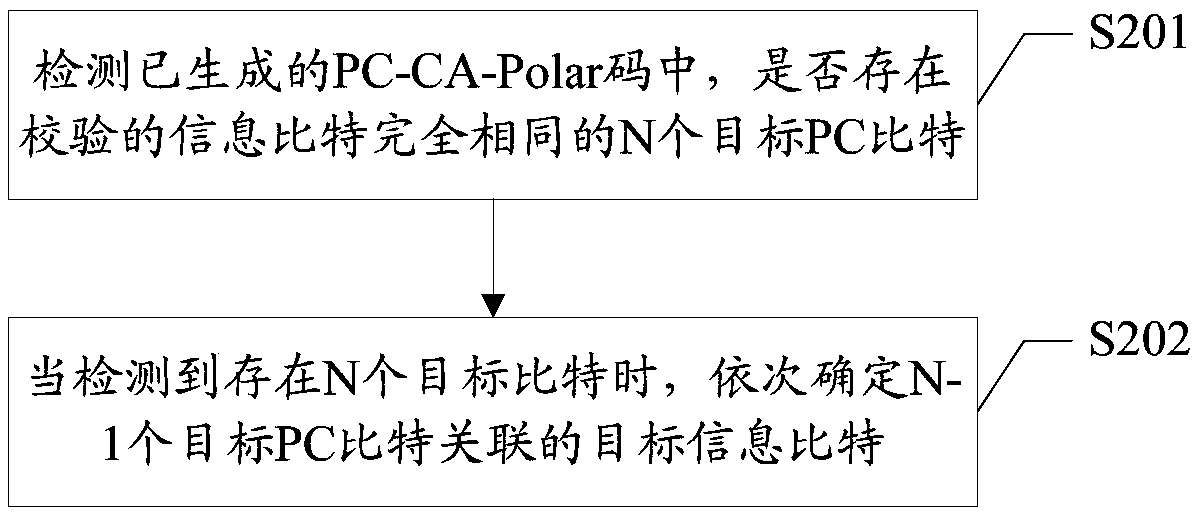
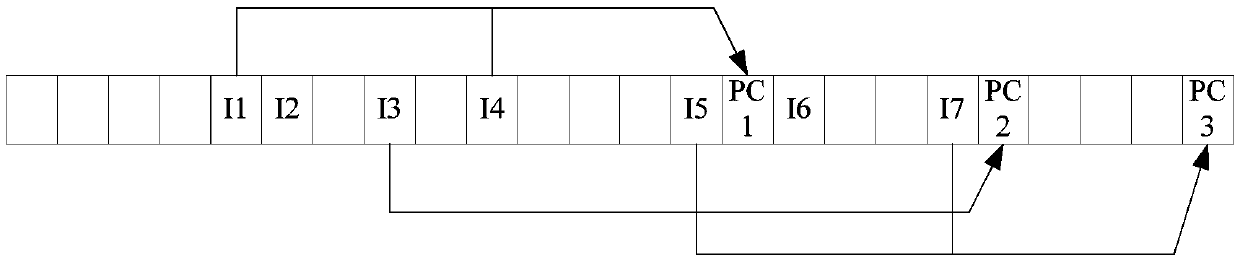
Parity check bit generation method and device of Polar code and readable storage medium
ActiveCN111384977AAvoid parityError correction/detection using linear codesError detection onlyComputer hardwareEngineering
The invention discloses a parity check bit generation method and device of a Polar code and a readable storage medium. The method comprises: detecting whether there are N target PC bits with the samecheck information bits or not in a generated PC-CA-Polar code; when it is detected that N target PC bits exist, determining target information bits associated with N-1 target PC bits in sequence, comprising: adjusting the information bit associated with the ith target PC bit, the adjusted information bit associated with the ith target PC bit not overlapping with the information bit associated withthe PC bit before the ith target PC bit; and selecting X information bits satisfying a preset condition from the adjusted information bits associated with the ith target PC bit as target informationbits associated with the ith target PC bit. According to the scheme, the situation that different PC bits in the PC-CA-Polar code verify the same information bit can be effectively avoided.
Owner:BEIJING SPREADTRUM HI TECH COMM TECH CO LTD
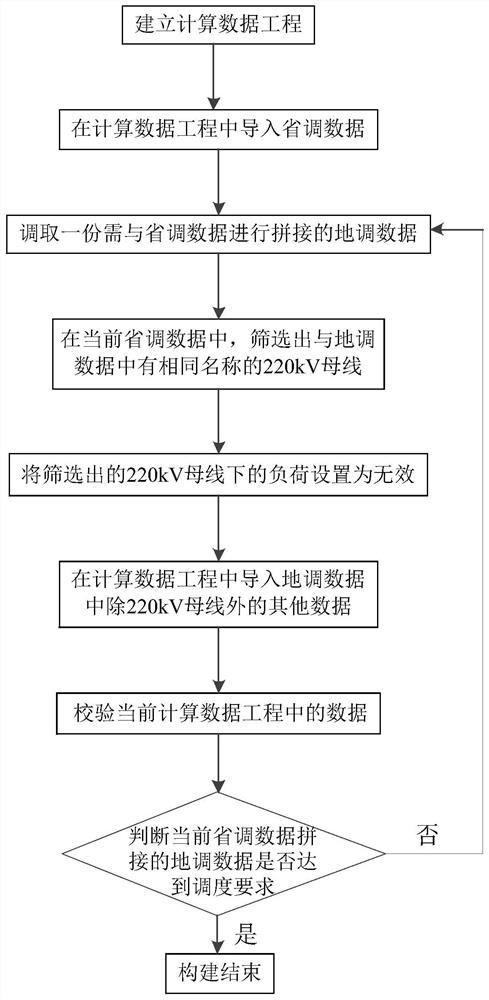
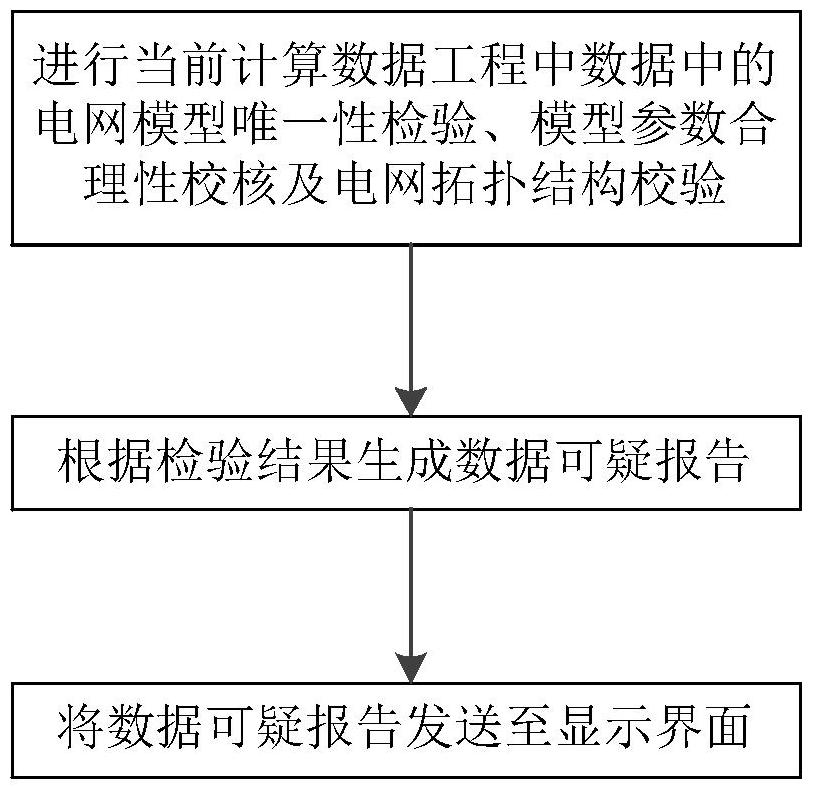
A data construction method and system suitable for power grid dispatch calculation
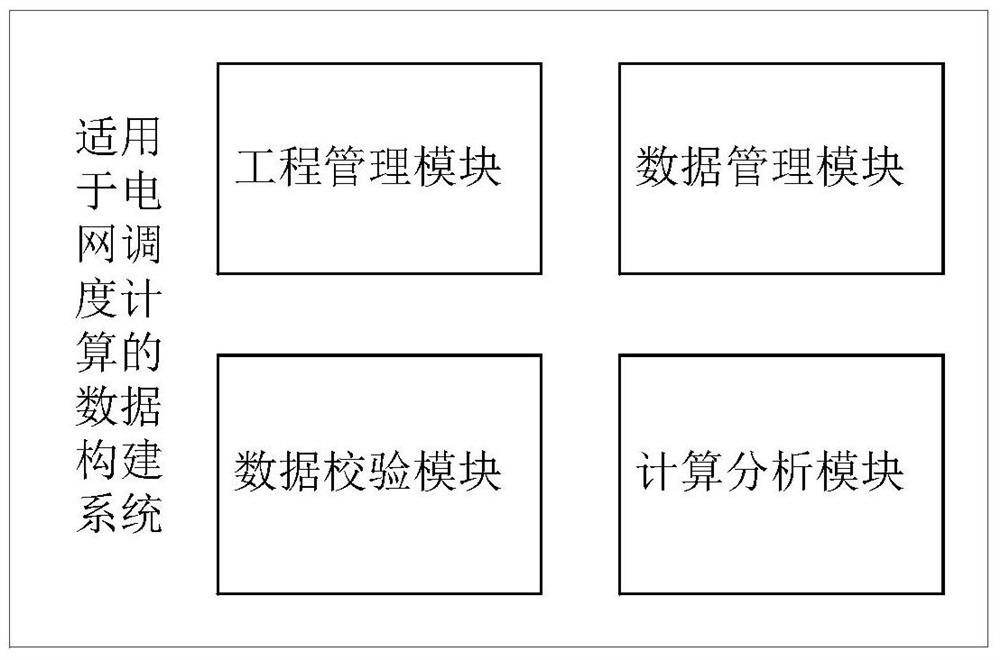
ActiveCN105678635BGuaranteed accuracyGuaranteed reasonablenessData processing applicationsSource Data VerificationData source
The invention provides a data construction method and system suitable for power network dispatching calculation. By use of the method, data for power network dispatching calculation is constructed through establishing a calculating data project, importing provincial dispatching data, and splicing dispatching data. The system comprises a project management module, a data management module, a data verification module, and a calculation analysis module. By use of the method and system, power network dispatching calculation with provincial dispatching data and local dispatching data is realized, wherein the provincial dispatching data and local dispatching data can be managed uniformly, maintained separately, and spliced for use as required; the system is flexible and effective; data source end maintenance and global sharing are realized; mutual influence of data modification is effectively prevented to help data analysis and verification of each area; By use of the method and system, calculating data can be flexibly constructed as calculation required, the uniqueness and accuracy of power network dispatching are guaranteed.
Owner:CHINA ELECTRIC POWER RES INST +3
A log-based structured data synchronization method
ActiveCN103455557BAvoid parityAvoid Synchronous ExceptionsSpecial data processing applicationsData synchronizationData format
The invention discloses a log based structured data synchronization method. The log based structured data synchronization method includes the steps of a), establishing a middle table for storing major keys and doubt fields of a doubt table; b), modifying database synchronization settings and adding the doubt table to a synchronization strategy of the middle table; c), modifying a database synchronization setting strategy and adding filter conditions and store procedures during doubt table synchronization of the doubt table; d), establishing a trigger on the doubt table and setting trigger date for clearing of the middle table and entering of illegal data format data. By the log based structured data synchronization method, data synchronization can be realized by avoiding the verification mechanism of a database, data consistency of corresponding records between a source library and an object library can be kept, and synchronous exception caused by data type report errors can be avoided.
Owner:上海新炬网络技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com