Method for generating a secret or a key in a network
A network, secret technology, applied in the field of secret keys, to achieve the effect of low complexity, saving additional overhead, and small error probability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
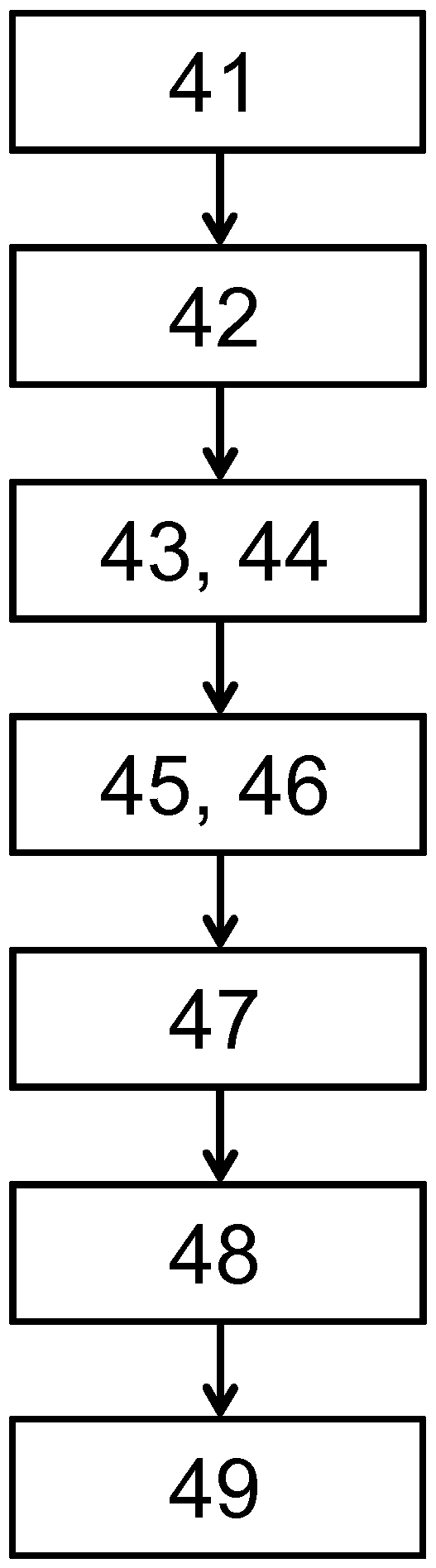
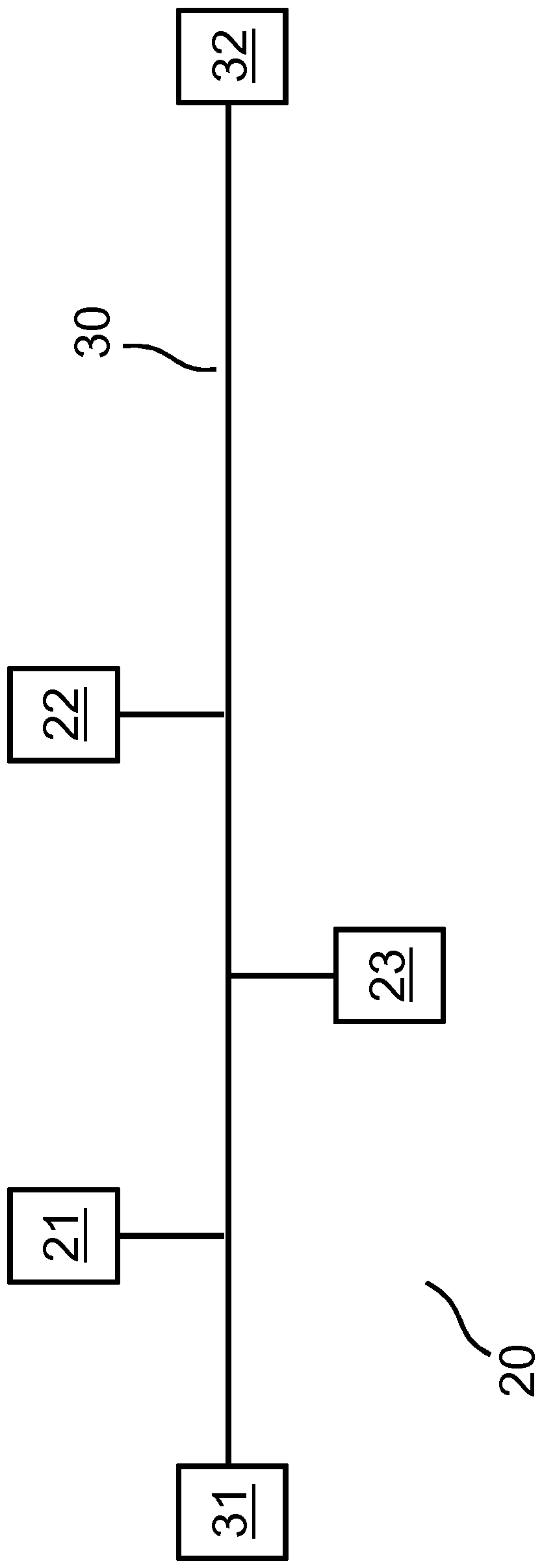
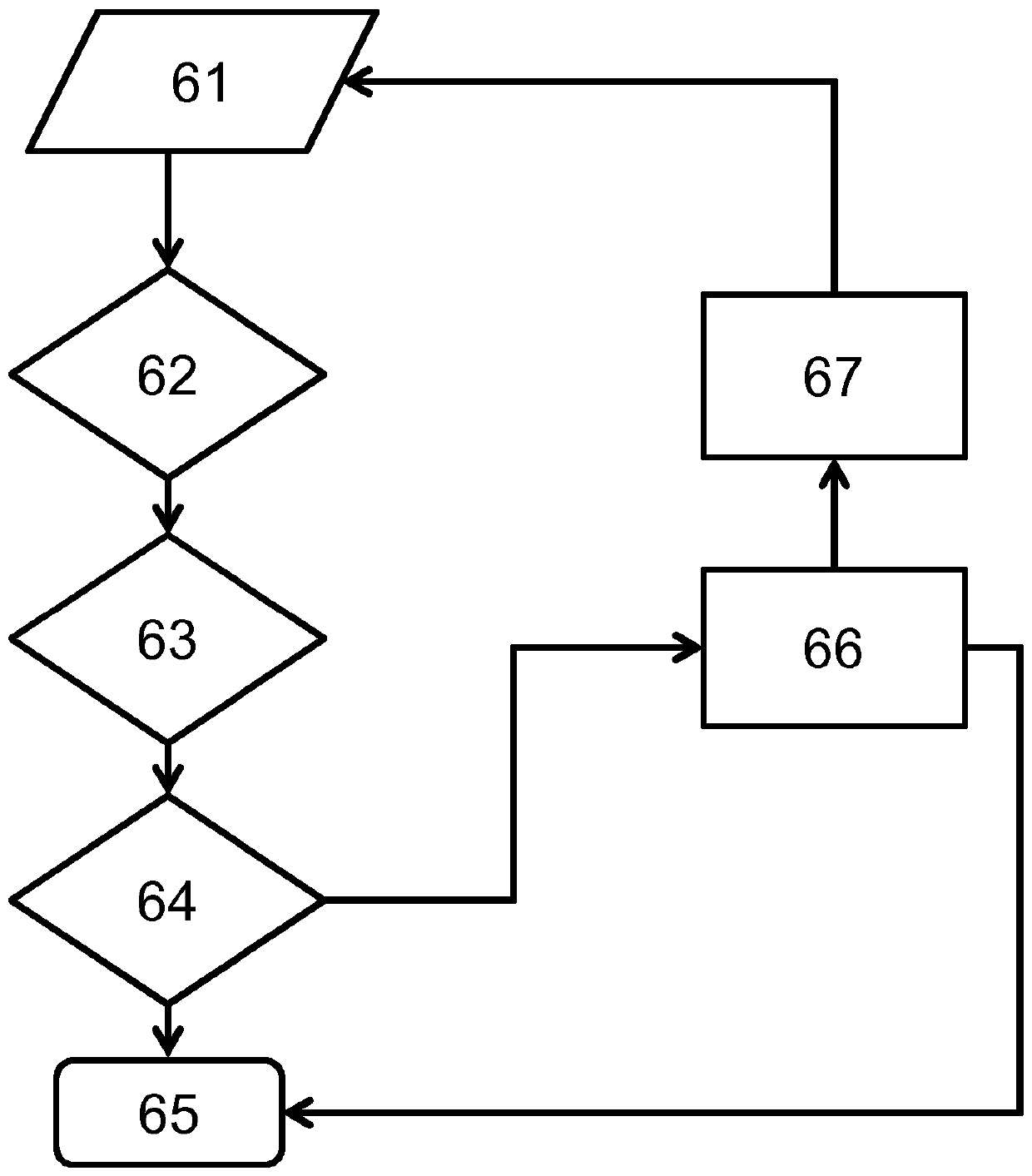
[0032] The invention relates to a method for generating a common secret or (secret) symmetric encryption key between two nodes (participants of a network) of a communication system, which nodes transmit via a commonly used medium (network) channel) to communicate with each other. In this case, the generation or negotiation of the encryption key is based on a public data exchange between the two participants, wherein a possible eavesdropping third party as an attacker is still not possible or only very difficult to achieve: inference The generated secret key. Thus, with the aid of the invention it is possible to fully automatically and securely set up corresponding symmetric encryption keys between two different participants in the network, in order to then implement certain security functions, such as data encryption, based thereon. As described in more detail, a common secret is first established for this, which can be used for key generation. But such a common secret can a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com