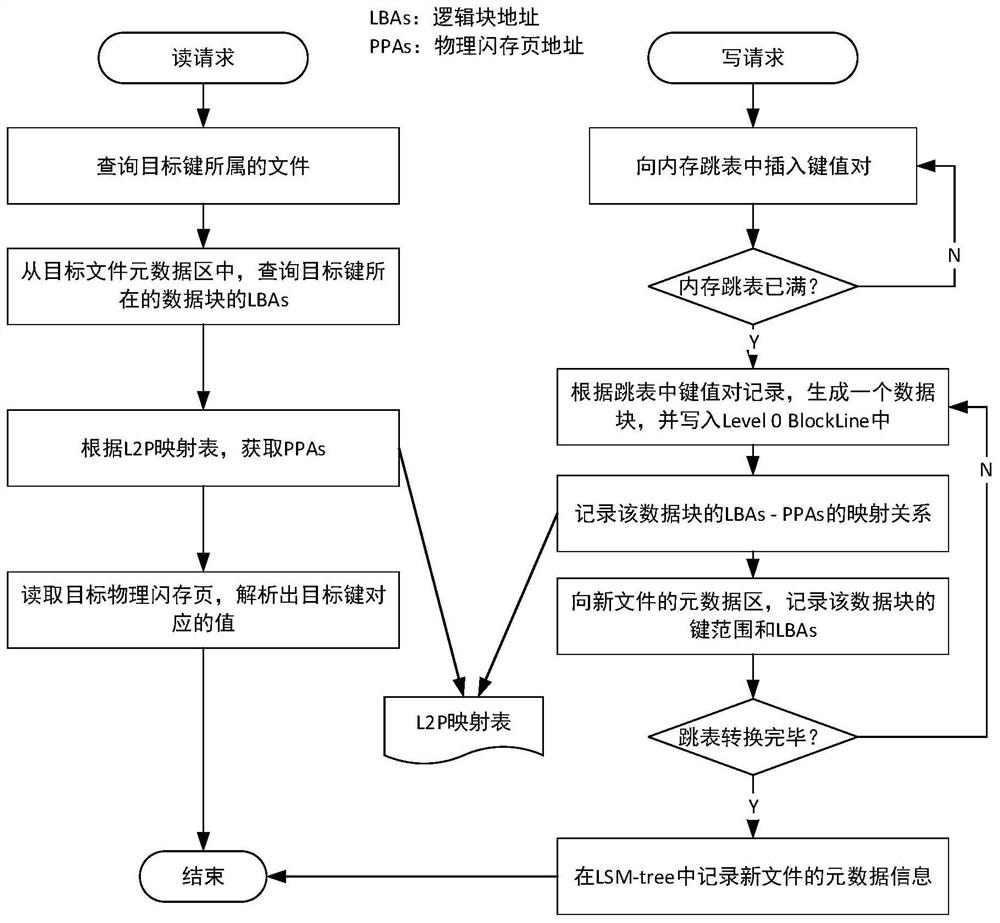
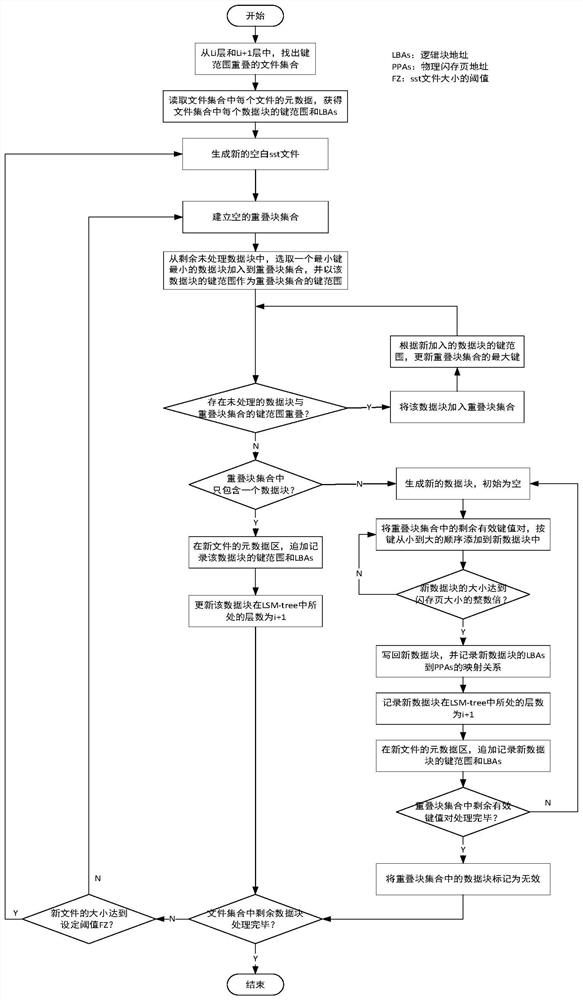
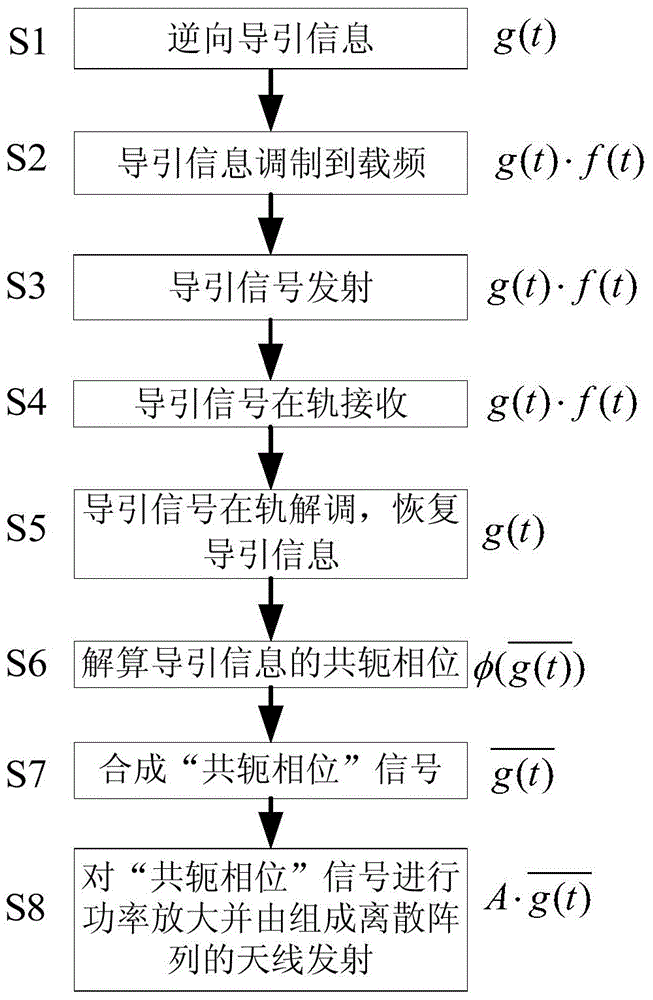
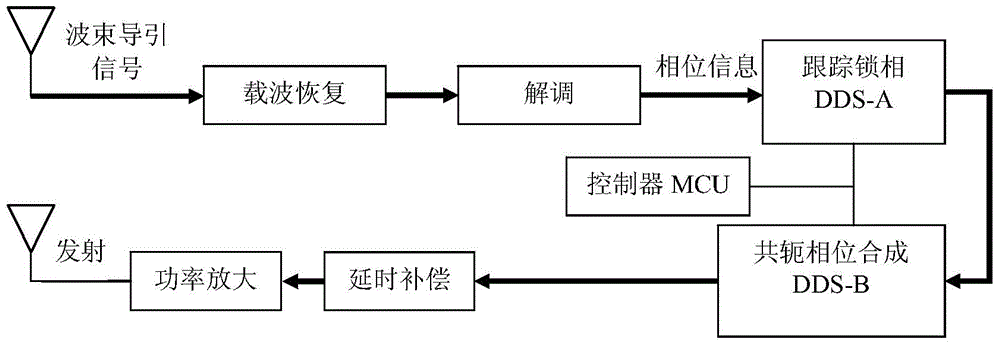
Patents
Literature
72results about How to "Increase computational overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
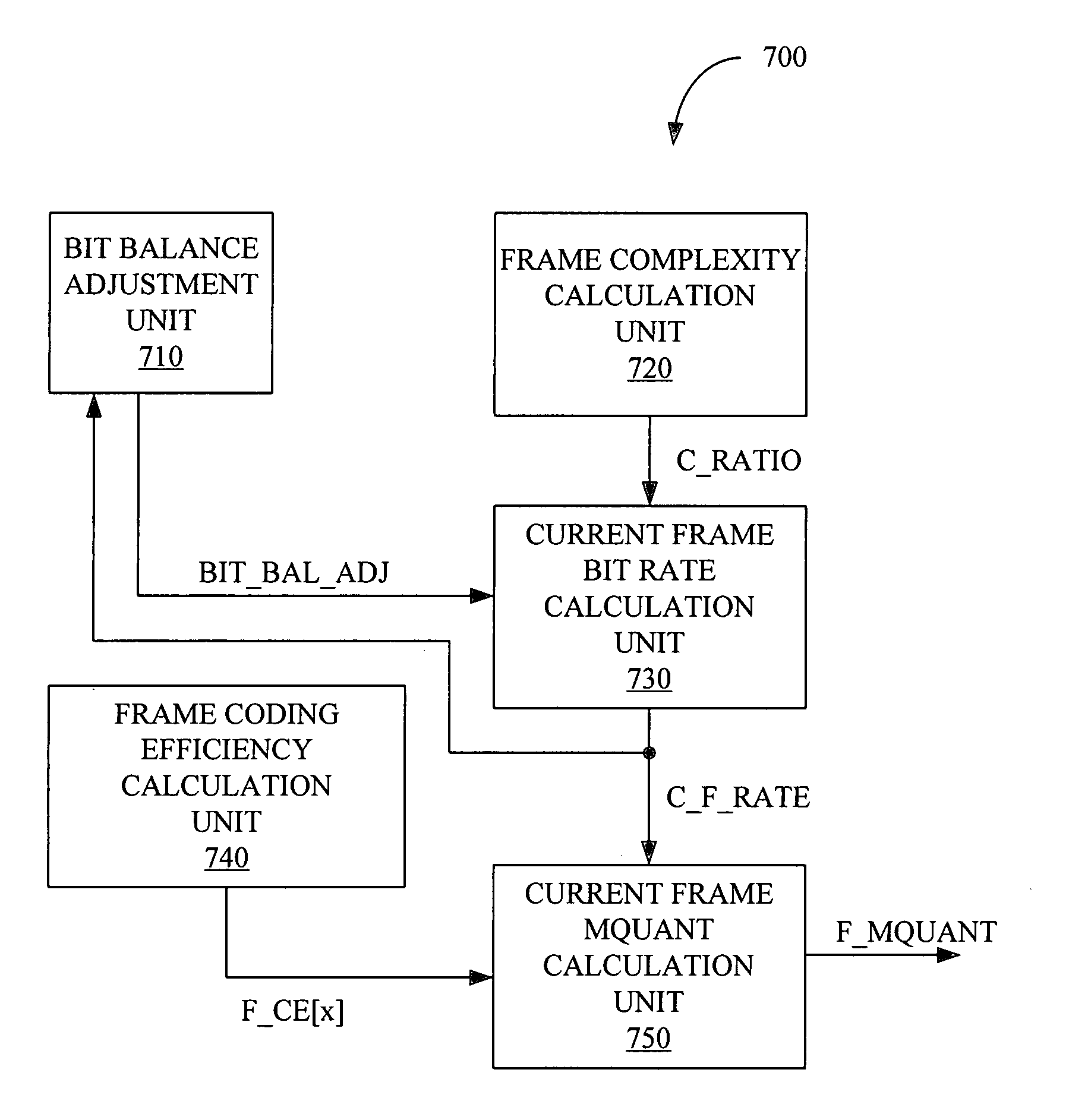
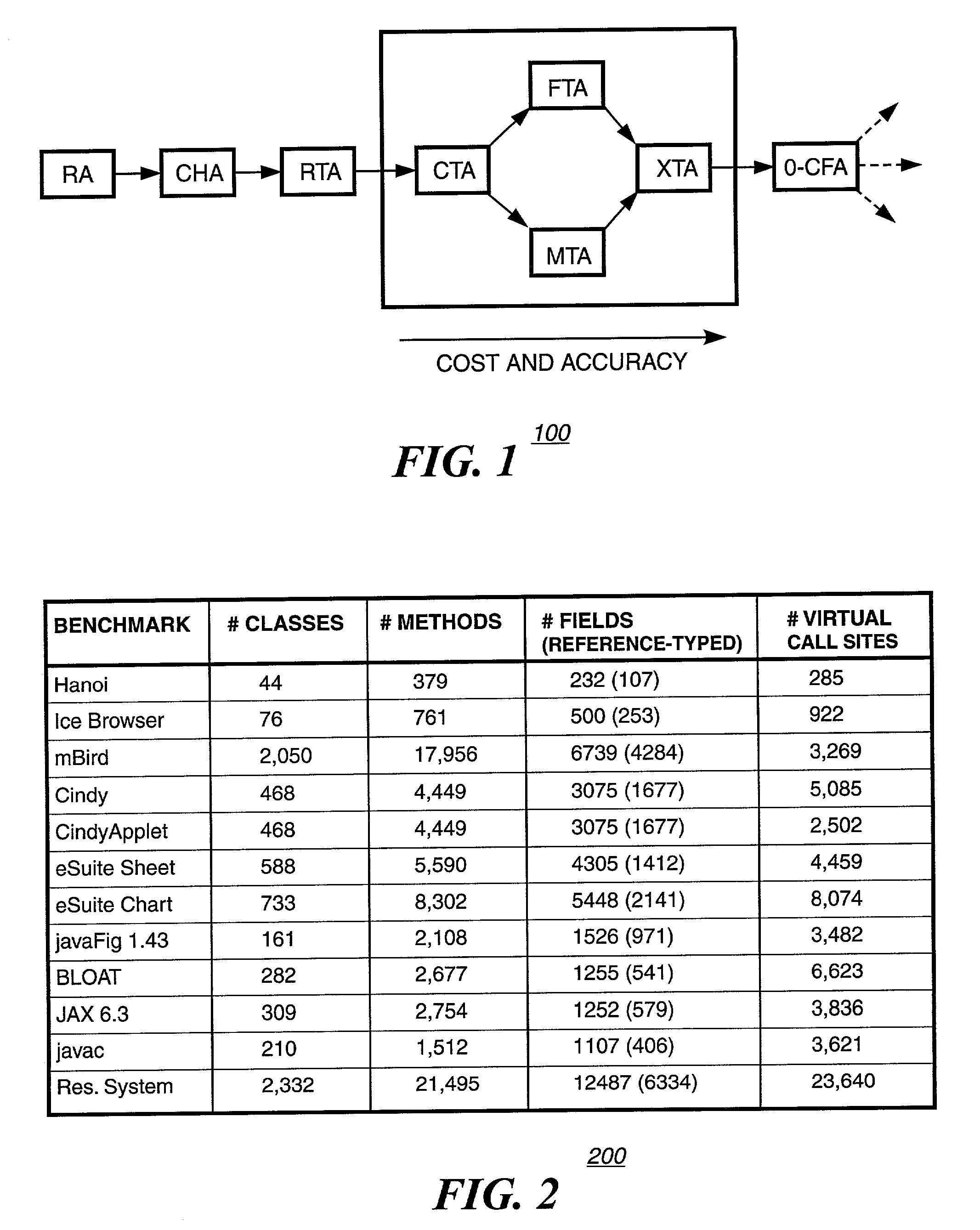
Video encoding using variable bit rates
InactiveUS20050105815A1Improve picture qualityIncrease computational overheadColor television with pulse code modulationColor television with bandwidth reductionVideo encodingTheoretical computer science
A system and method is provided for variable bit rate encoding using a complexity ratio. Quantization parameter is calculated using a complexity ratio, which is equal to a local complexity divided by a global complexity. Complex pictures are allocated a larger bit budget relative to simple pictures. With the larger bit budget the quality of complex pictures can be maintained while reducing the overall size of the encoded video stream.
Owner:CRP STEVENS CREEK L L C
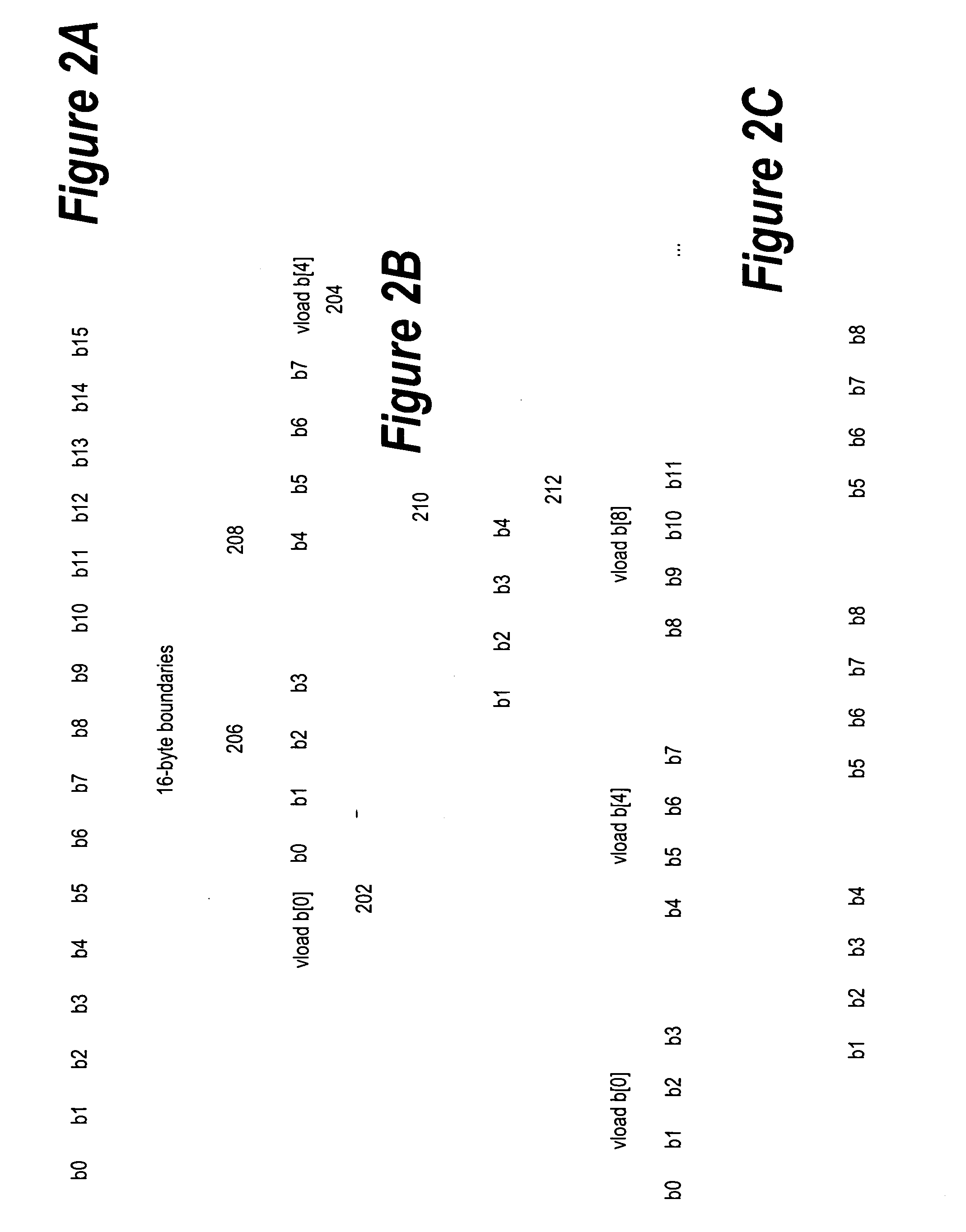
Framework for efficient code generation using loop peeling for SIMD loop code with multiple misaligned statements
InactiveUS20050283773A1Reduce computational overheadIncrease computational overheadSoftware engineeringGeneral purpose stored program computerData reorganizationSteady state
A system and method is provided for vectorizing misaligned references in compiled code for SIMD architectures that support only aligned loads and stores. In this framework, a loop is first simdized as if the memory unit imposes no alignment constraints. The compiler then inserts data reorganization operations to satisfy the actual alignment requirements of the hardware. Finally, the code generation algorithm generates SIMD codes based on the data reorganization graph, addressing realistic issues such as runtime alignments, unknown loop bounds, residual iteration counts, and multiple statements with arbitrary alignment combinations. Loop peeling is used to reduce the computational overhead associated with misaligned data. A loop prologue and epilogue are peeled from individual iterations in the simdized loop, and vector-splicing instructions are applied to the peeled iterations, while the steady-state loop body incurs no additional computational overhead.
Owner:IBM CORP
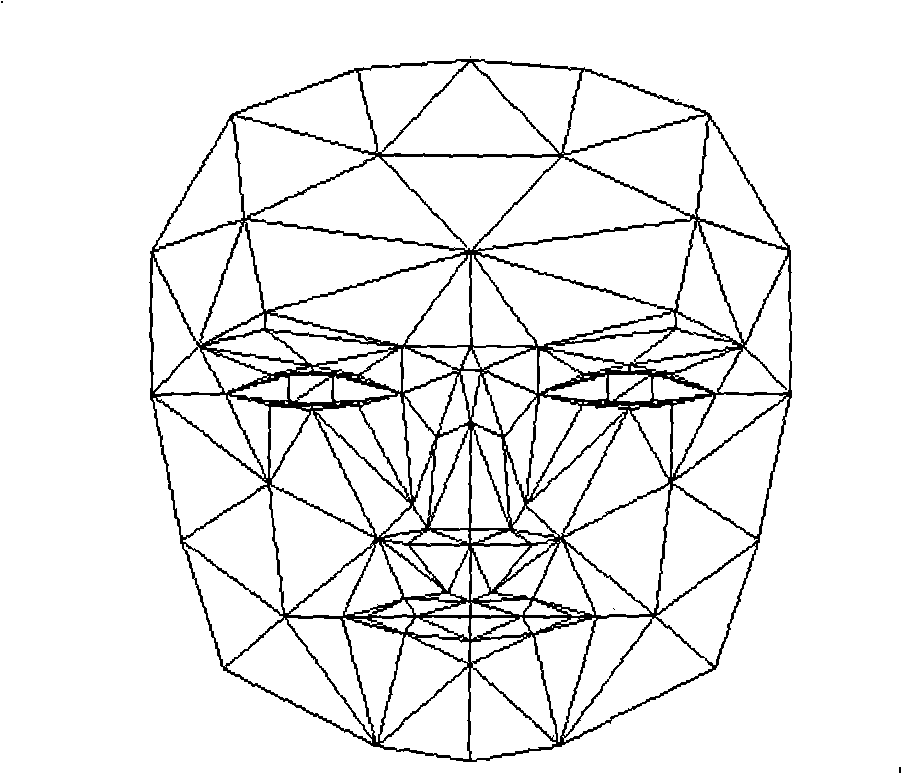
Three-dimensional human face modelling approach based on front side image
InactiveCN101339669AImprove efficiencyIncrease computational overhead3D-image rendering3D modellingHuman bodyPattern recognition
The invention relates to the technical field of computer graphics and image processing, in particular to a 3D human face modeling method based on front silhouette, which mainly models the 3D human face in a fully automatic manner. The method comprises the following steps: a general human face grid model is built by 113 feature points and 184 tri patch information arrays which are connected with the 113 feature points based on Candide parameterization; 2D position information and depth information of a specific human face are determined by virtue of human eyes location algorithm and side nose tip location algorithm by inputting two 2D images, the general face model is modified and transformed into a specific human face model; an interpolating is calculated for the human body patches by Delaunay Triangulation Technology and texture mapping is carried out by the Bilinear Interpolation Technology, thus causing the human face image to be appeared more delicate and accurate; and the method solves the problems such as low efficiency, high calculation expense, and the like, existing in the prior art.
Owner:SHANGHAI NORMAL UNIVERSITY
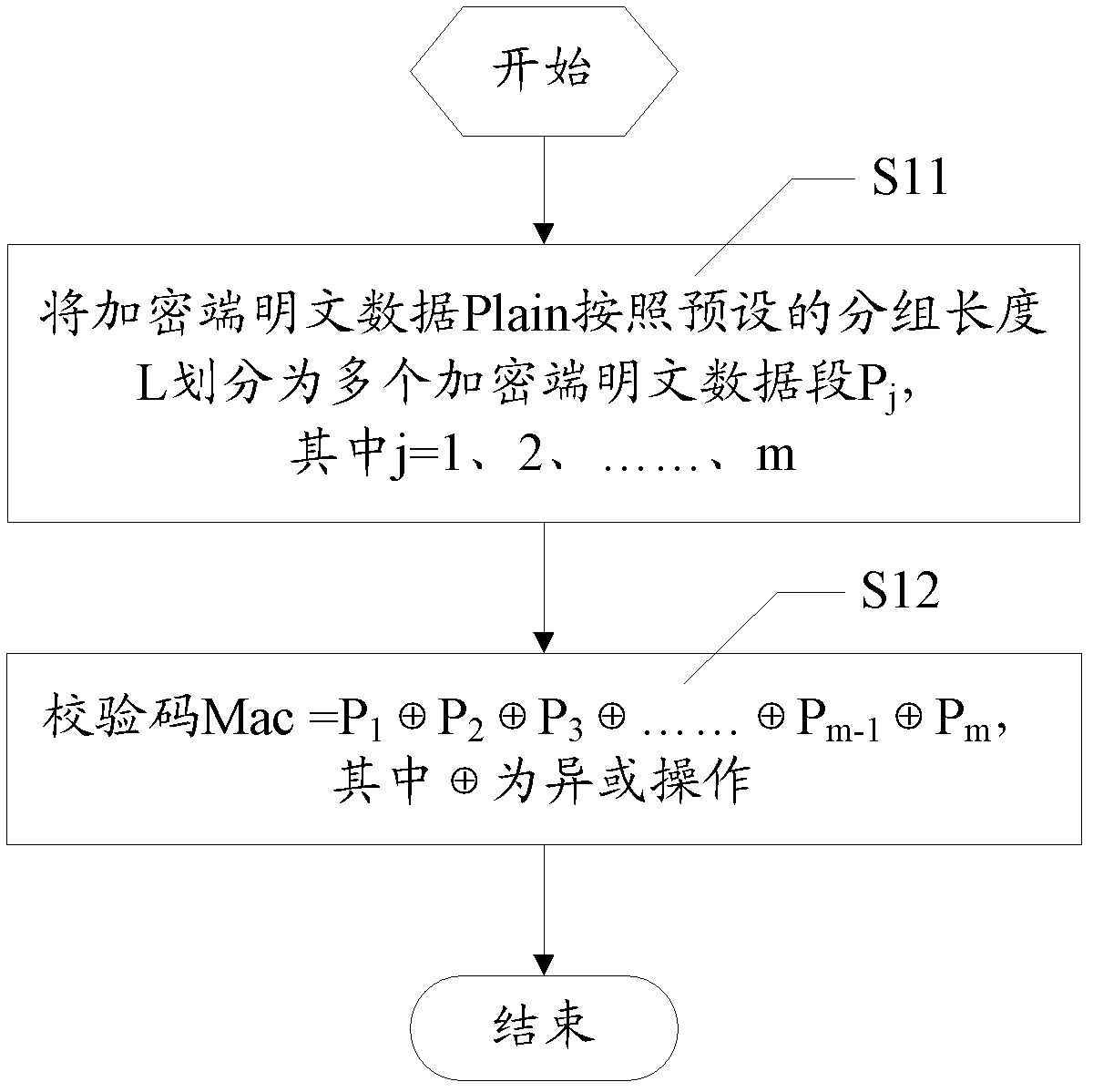
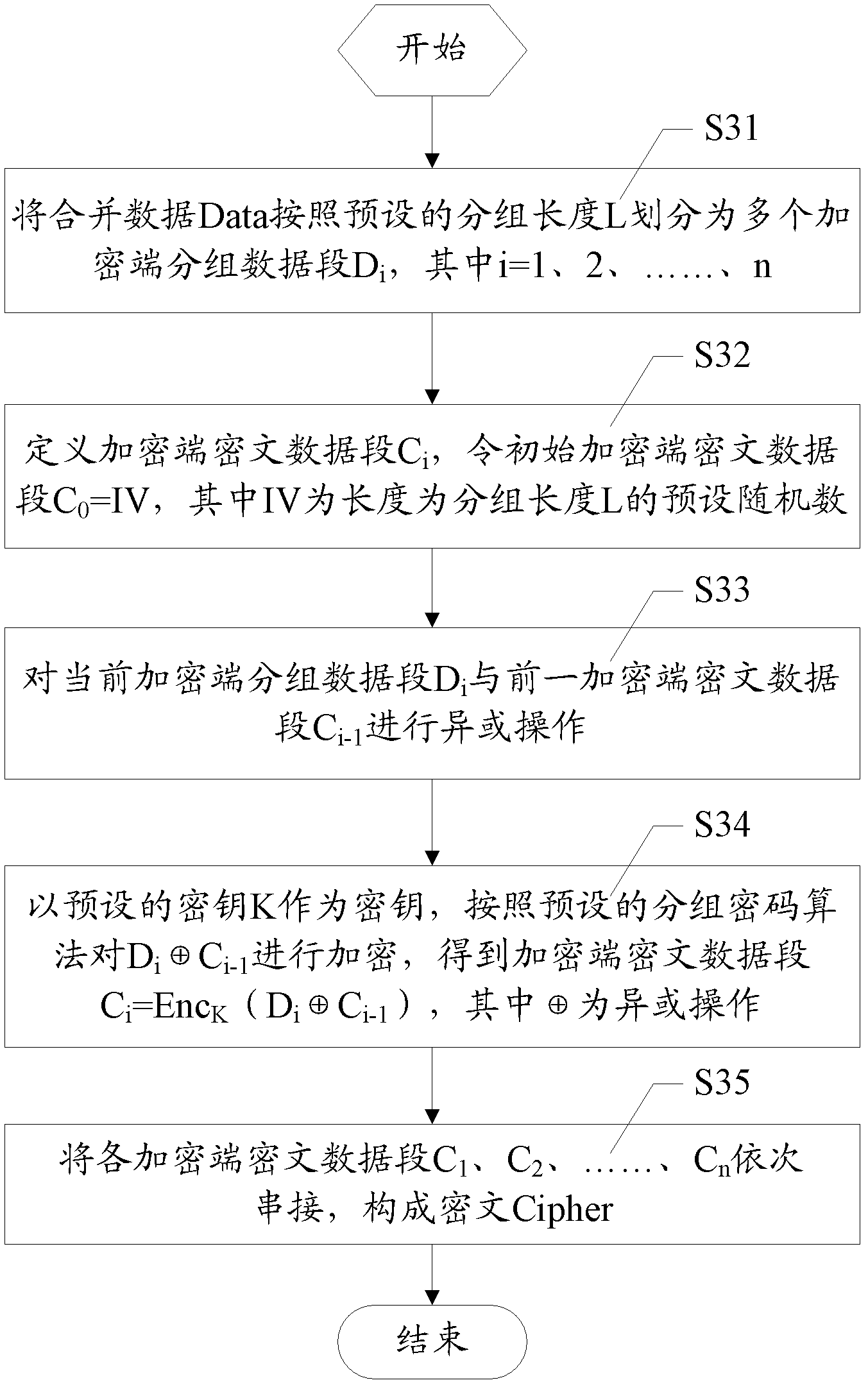
Data encryption/decryption checking method and system
InactiveCN102437910AGuaranteed correctnessGuaranteed privacyEncryption apparatus with shift registers/memoriesUser identity/authority verificationComputer hardwarePlaintext
The invention discloses a data encryption / decryption checking method and system. The method comprises the following steps that: an encryption device performs Xor operation on each data section in plaintext data at an encryption end to acquire a checking code, combines the plaintext data at the encryption end with the checking code to acquire combined data, encrypts the combined data to acquire a ciphertext and outputs the ciphertext to a decryption end; and a decryption device decrypts the received ciphertext to acquire decrypted data, separates out the plaintext data at the decryption end and the checking code from the decrypted data, and checks the checking code. According to the invention, the checking code is generated through the simple Xor operation, and the data is encrypted by adopting one-time encryption transformation, so that the encryption transformation frequency is reduced, the calculation overhead is prevented from being multiplied, and the encryption / decryption efficiency is improved effectively; and by checking the correctness of the checking code, whether the data is wrong or maliciously changed during encryption or decryption and transmission or storage can be detected; and the confidentiality and correctness of the data are guaranteed at the same time.
Owner:国家超级计算深圳中心(深圳云计算中心)
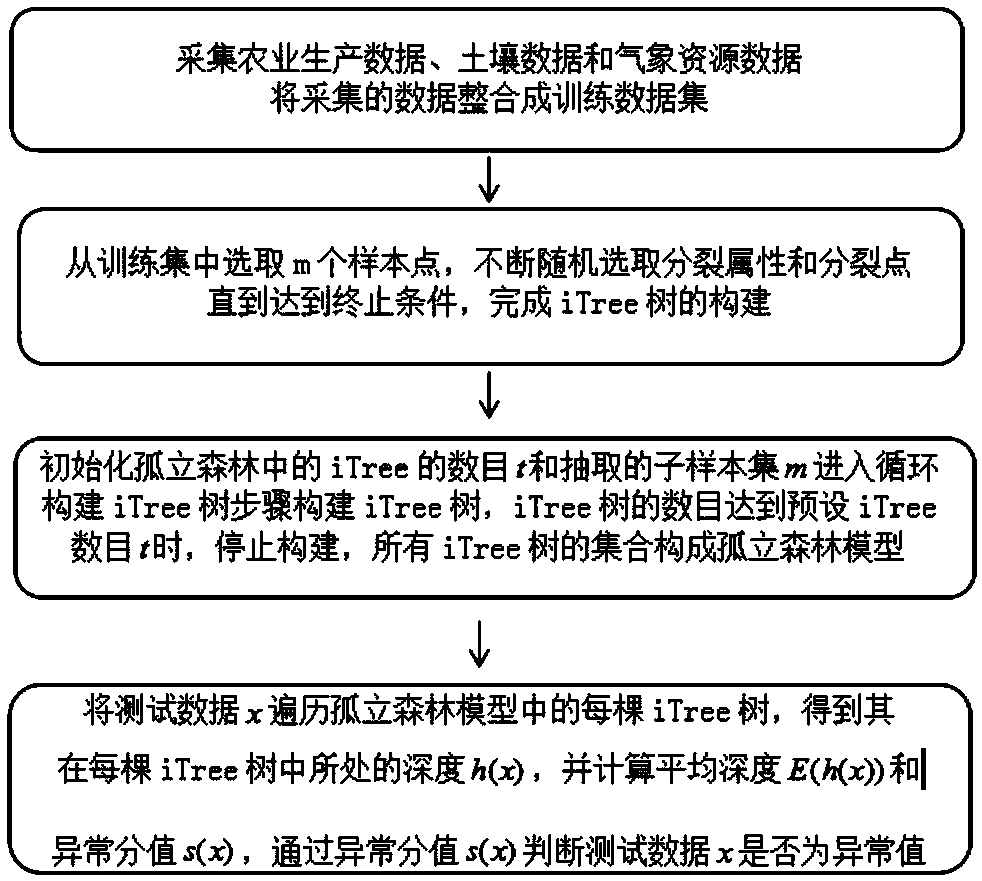
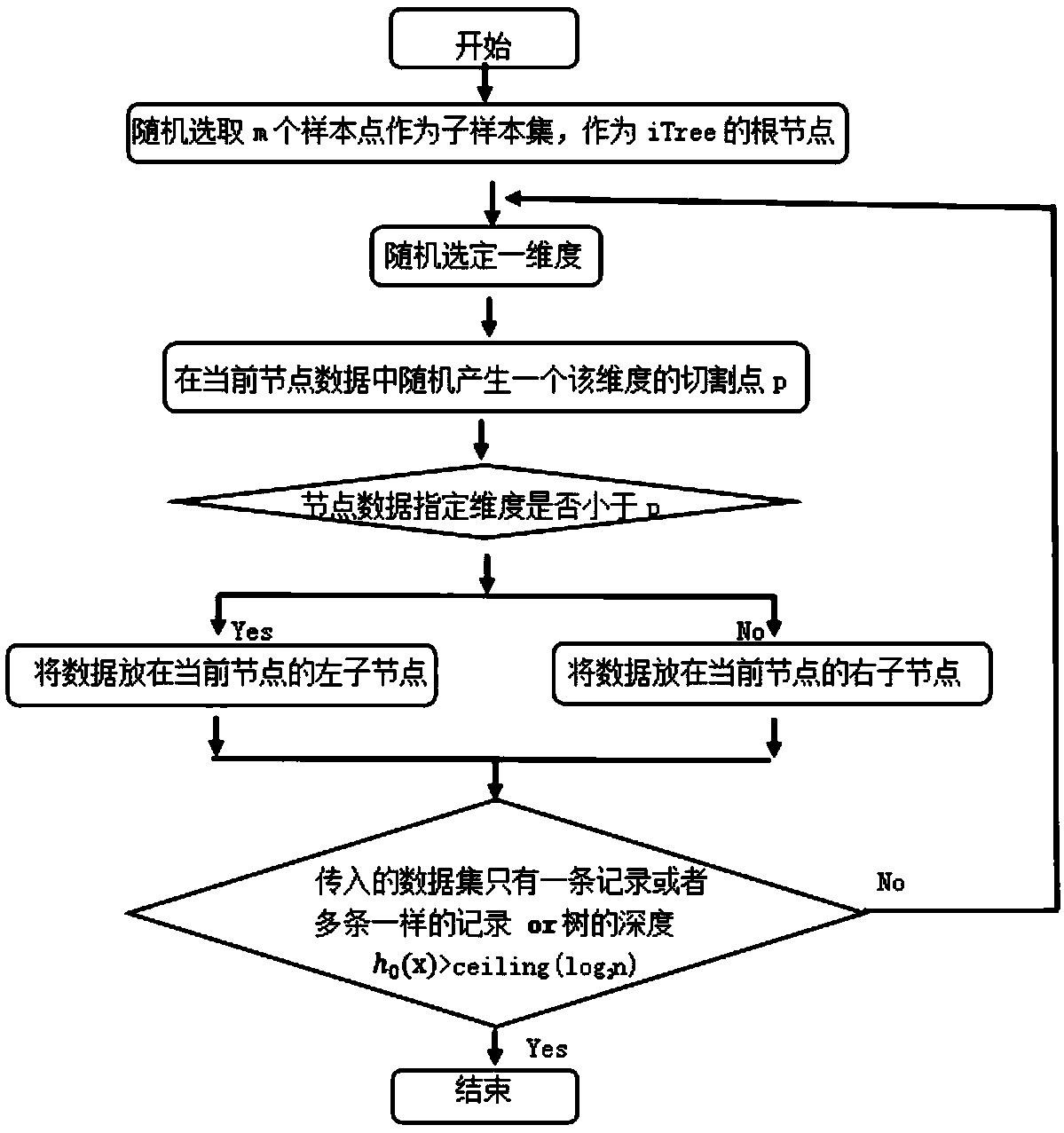
An outlier detection method based on agricultural big data
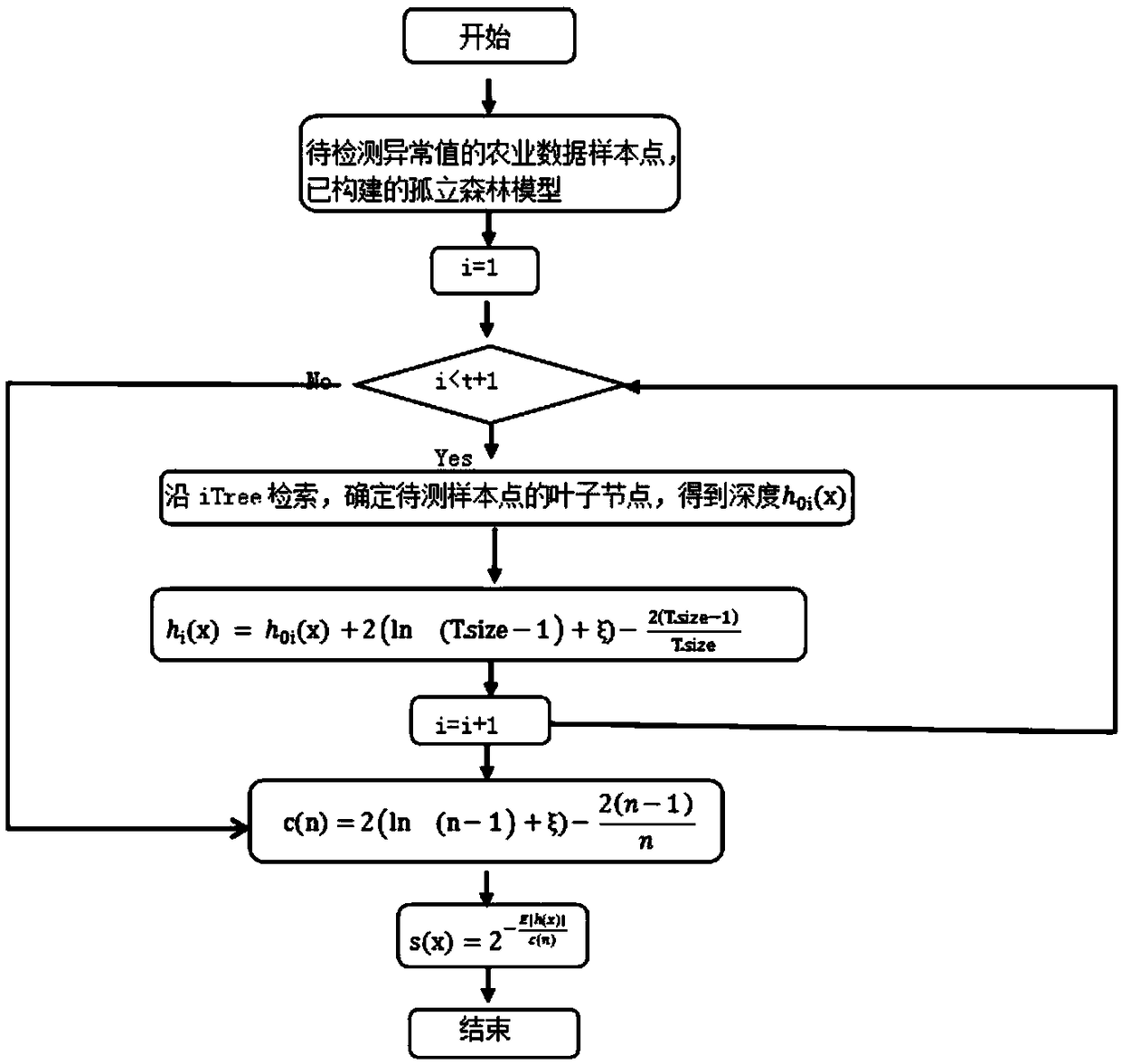
InactiveCN109345137AEasy to handleIncrease time complexityResourcesSpecial data processing applicationsData setData acquisition
The invention relates to the field of agricultural outlier detection, in particular to an outlier detection method based on agricultural big data. The method comprises the following steps: a data collection step of collecting agricultural production data, agricultural soil data and agrometeorological resource data, and integrating the data into a training data set; The step of constructing iTree tree is to select m sample points from the training dataset and continuously randomly select splitting attributes and splitting points until the termination condition is reached; the step of constructing iTree tree is to select m sample points from the training dataset. Constructing an isolated forest algorithm model, initializing the number t of iTree trees in the isolated forest and the set m ofsubsamples taken when constructing the iTree trees, entering the step of constructing the iTree trees in a loop, and constructing mutually independent iTree trees, wherein the set of all iTree trees constitutes the isolated forest algorithm model; An outlier judging step of calculating an outlier score s (x), and judging whether the test data x is an outlier by the outlier score s (x). The invention applies the isolated forest algorithm model to the outlier detection of the agricultural big data, and can effectively improve the detection effect of the outlier of the agricultural big data.
Owner:GUANGDONG KINGPOINT DATA SCI & TECH CO LTD
Method and apparatus for allocating memory for immutable data on a computing device
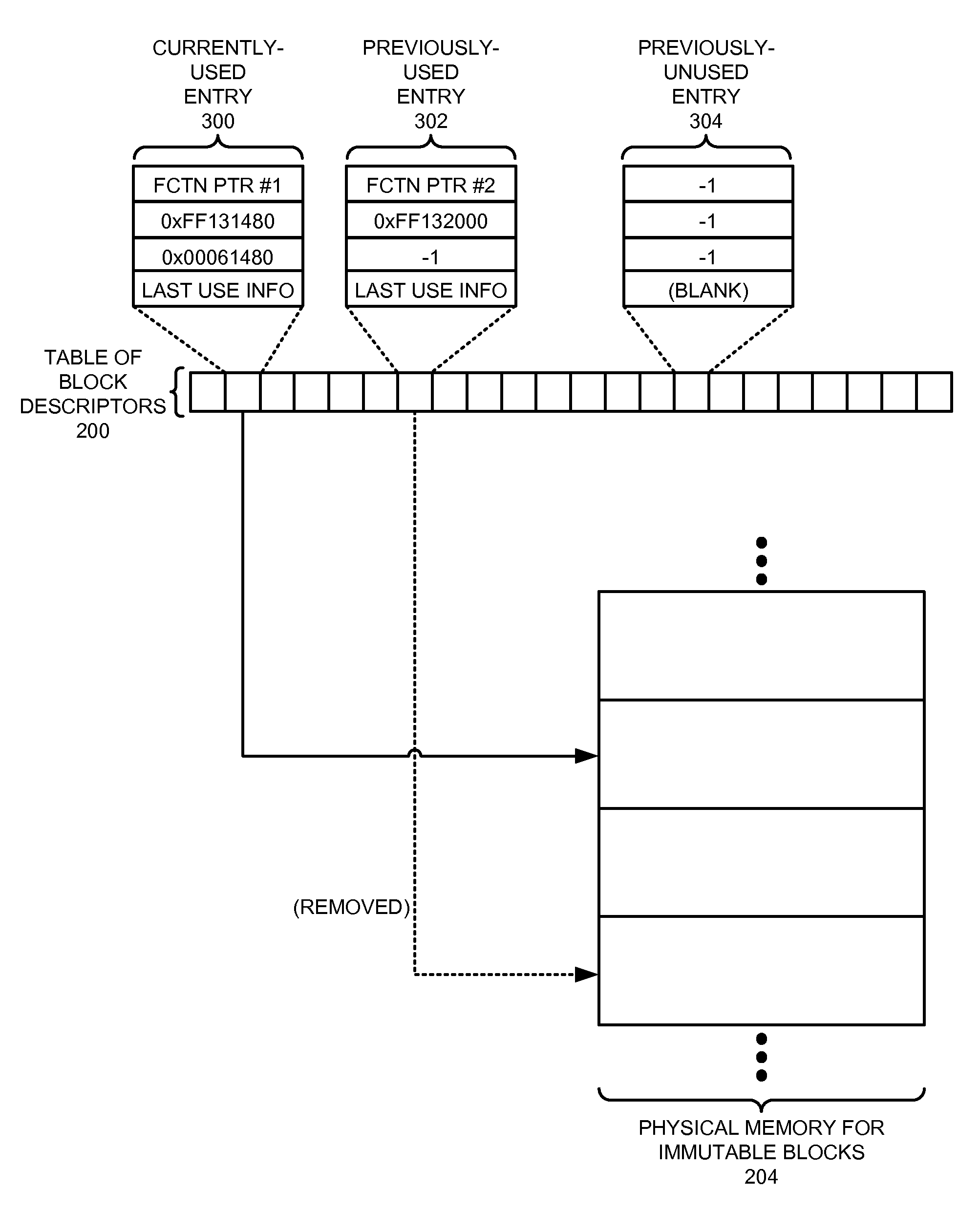
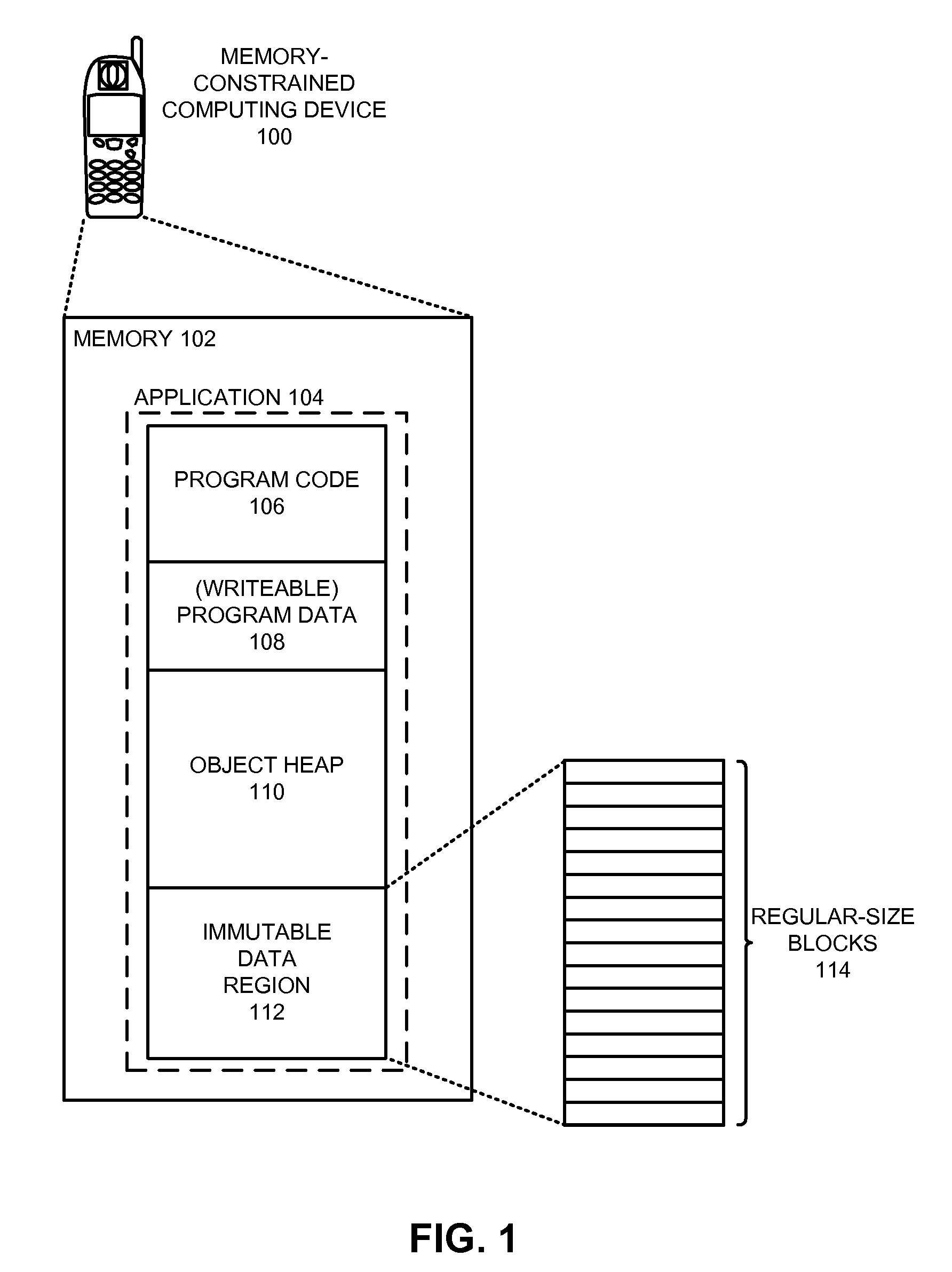
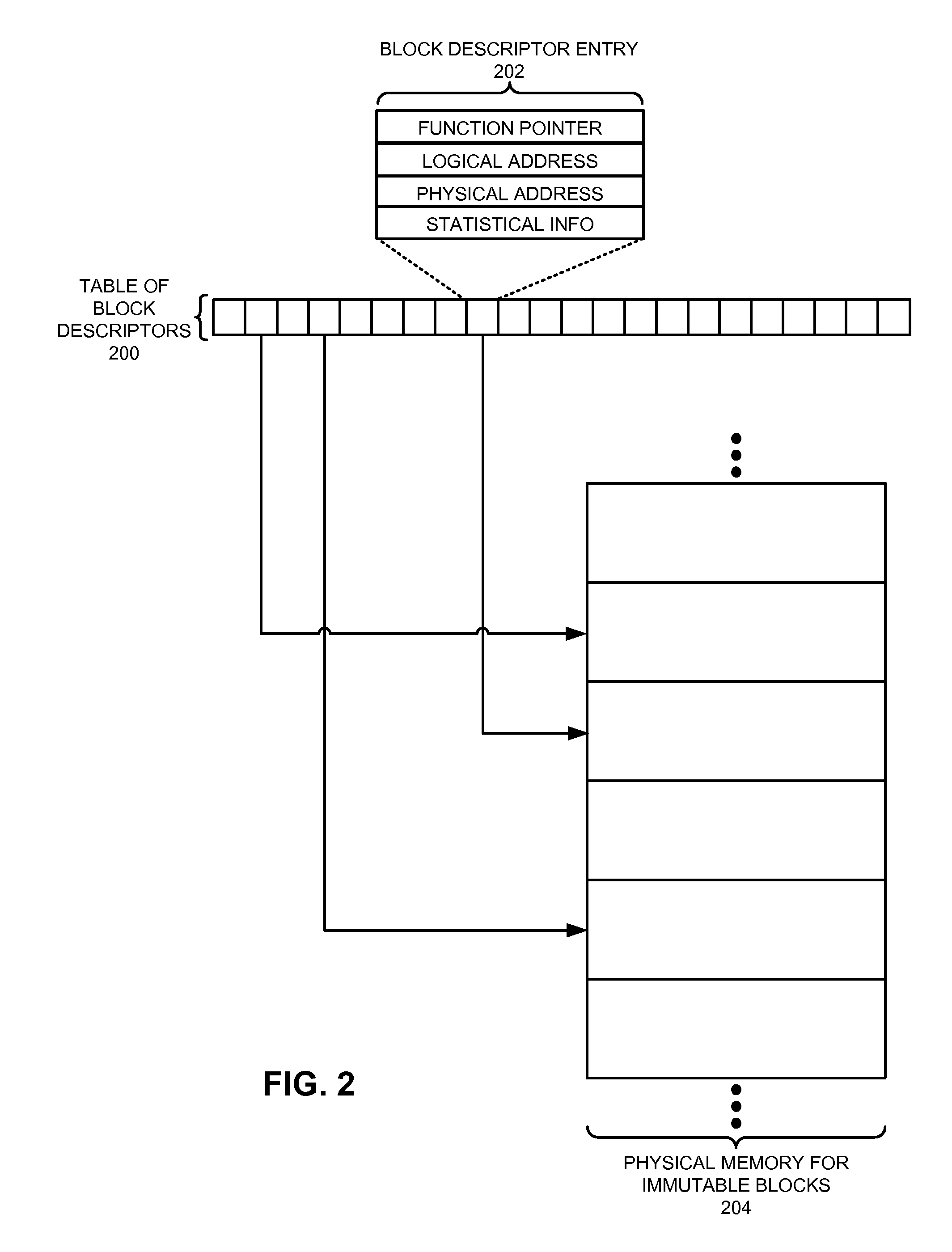
ActiveUS20090307455A1Reduce memory usageIncrease computational overheadMemory architecture accessing/allocationMemory adressing/allocation/relocationParallel computingTerm memory
One embodiment of the present invention provides a system that allocates memory for immutable data on a computing device. During operation, the system receives an application to be executed on the computing device. Next, the system allocates a memory region on the computing device to store immutable data for the application. Note that this memory region is smaller than the immutable data for the application. When the system subsequently receives a request to access a block of immutable data for the application, the system allocates space in this memory region for the block, and proceeds to load the block into the memory region. However, if at a later time the space occupied by this first block is needed for another block, the system unloads and discards the first block. If a subsequent operation needs to use information in the first block, the system regenerates the block by transforming raw data associated with the block into a form that can be directly accessed by the application, and then reloads the block into the memory region.
Owner:SUN MICROSYSTEMS INC
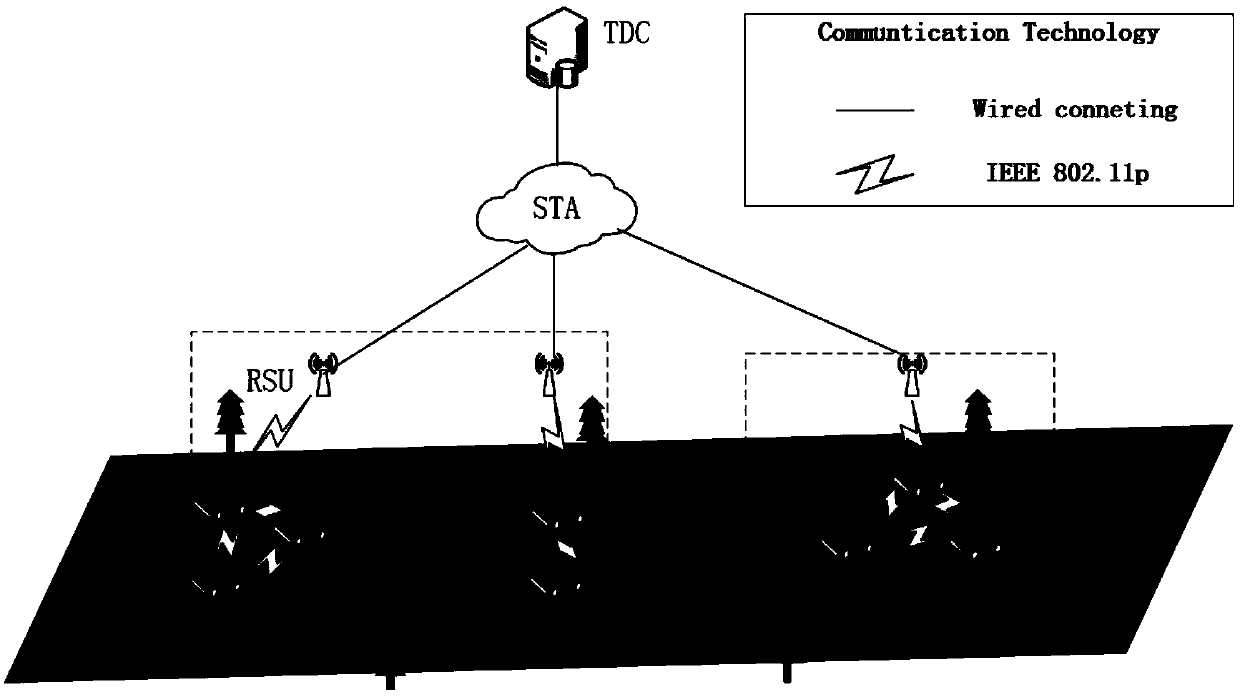
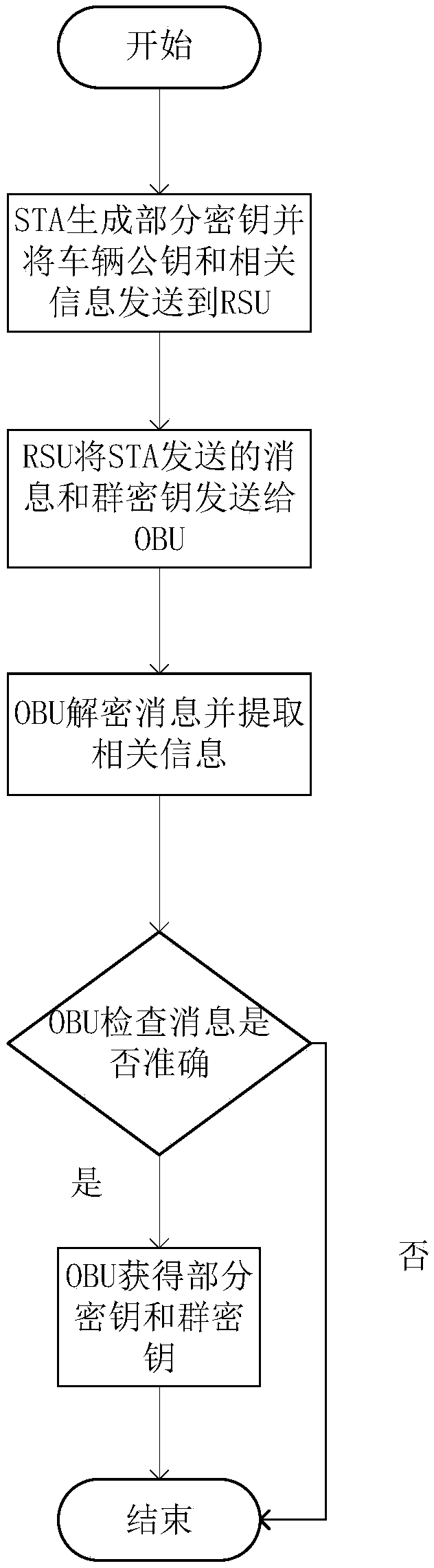
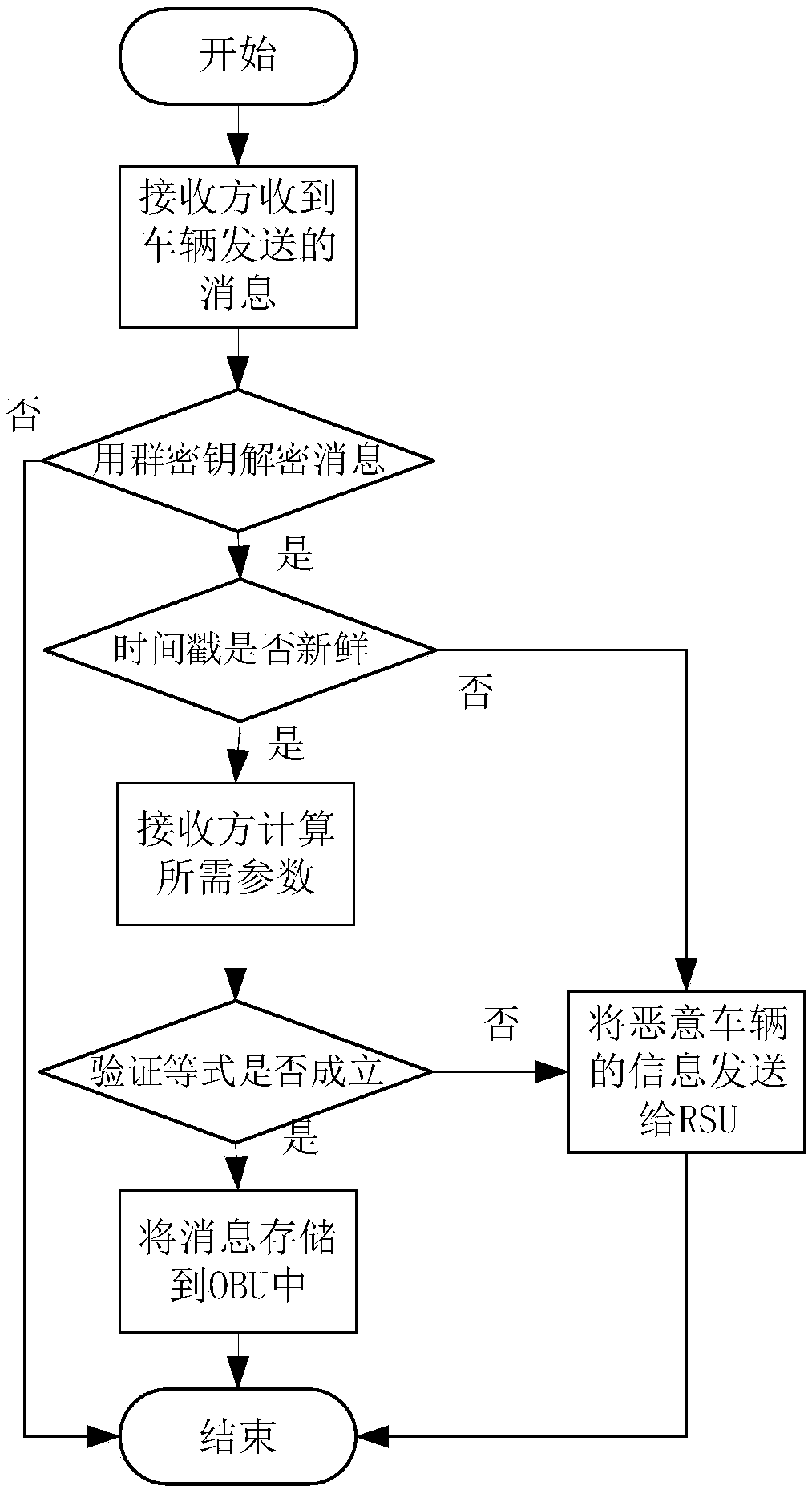
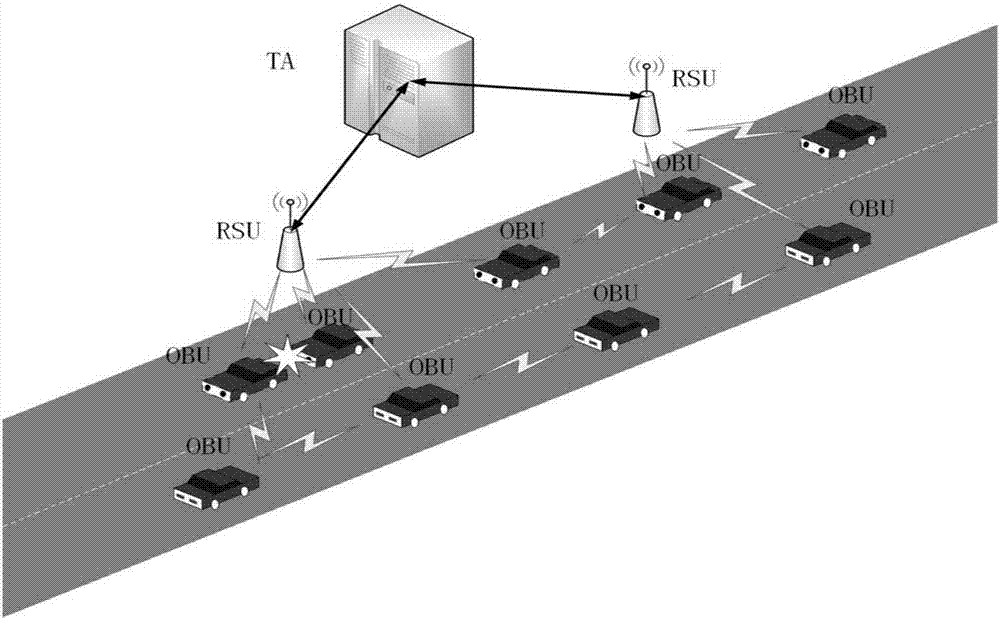
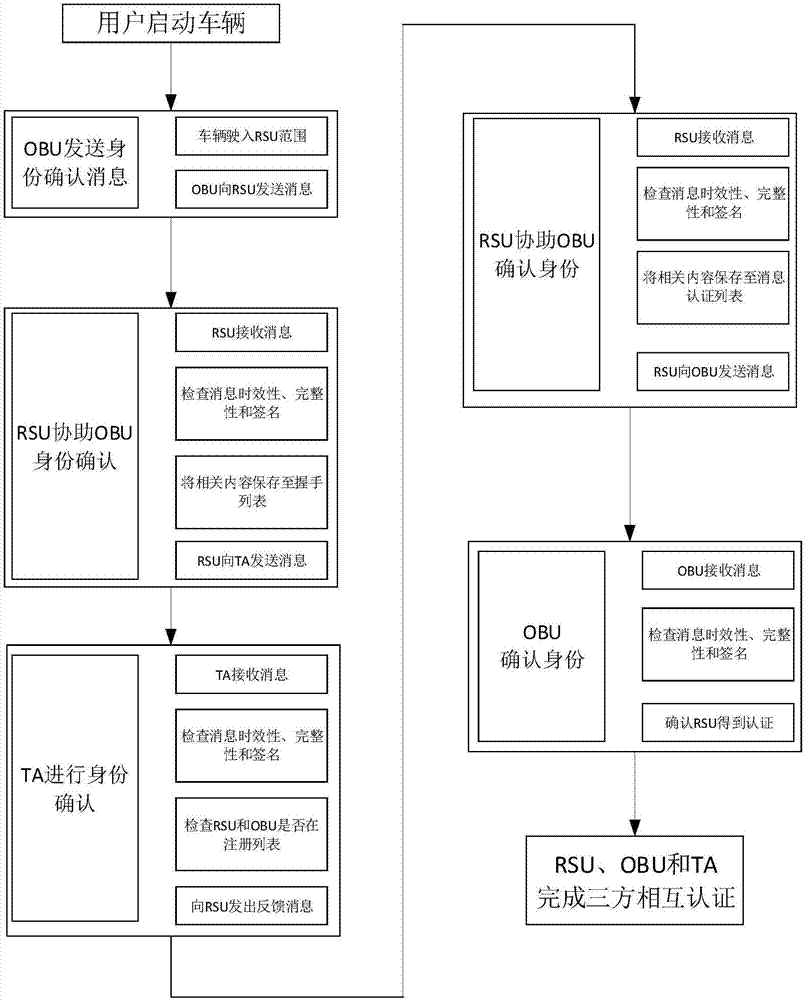
Message authentication method based on semi-trusted management center in vehicle networking
ActiveCN109067525AIdentity privacy leakIn line with realityKey distribution for secure communicationPublic key for secure communicationIn vehicleKey distribution
The invention discloses a message authentication method based on a semi-trusted management center in the vehicle networking. The user communicates with RSU and other vehicles arranged on both sides ofthe road through OBU, and extracts, analyzes and effectively utilizes the message, so that the vehicle runs more safely, and the user can obtain more efficient service at the same time. The inventionis based on the environment of a semi-trusted management center, more realistic, at the same time the vehicle's pseudonym is generated by the vehicle, RSU and STA together, RSU and STA trace the identity of the vehicle jointly, A single party cannot obtain the true identity of the vehicle, thus the safety is improved.The invention adopts the self-healing key distribution method to exclude the revoked vehicles from the group, so that the vehicles do not need to store and query the revoked list, the storage space, the resources are calculated and the searching time are reduced, and the efficiency of the message authentication is improved.
Owner:ANHUI UNIVERSITY
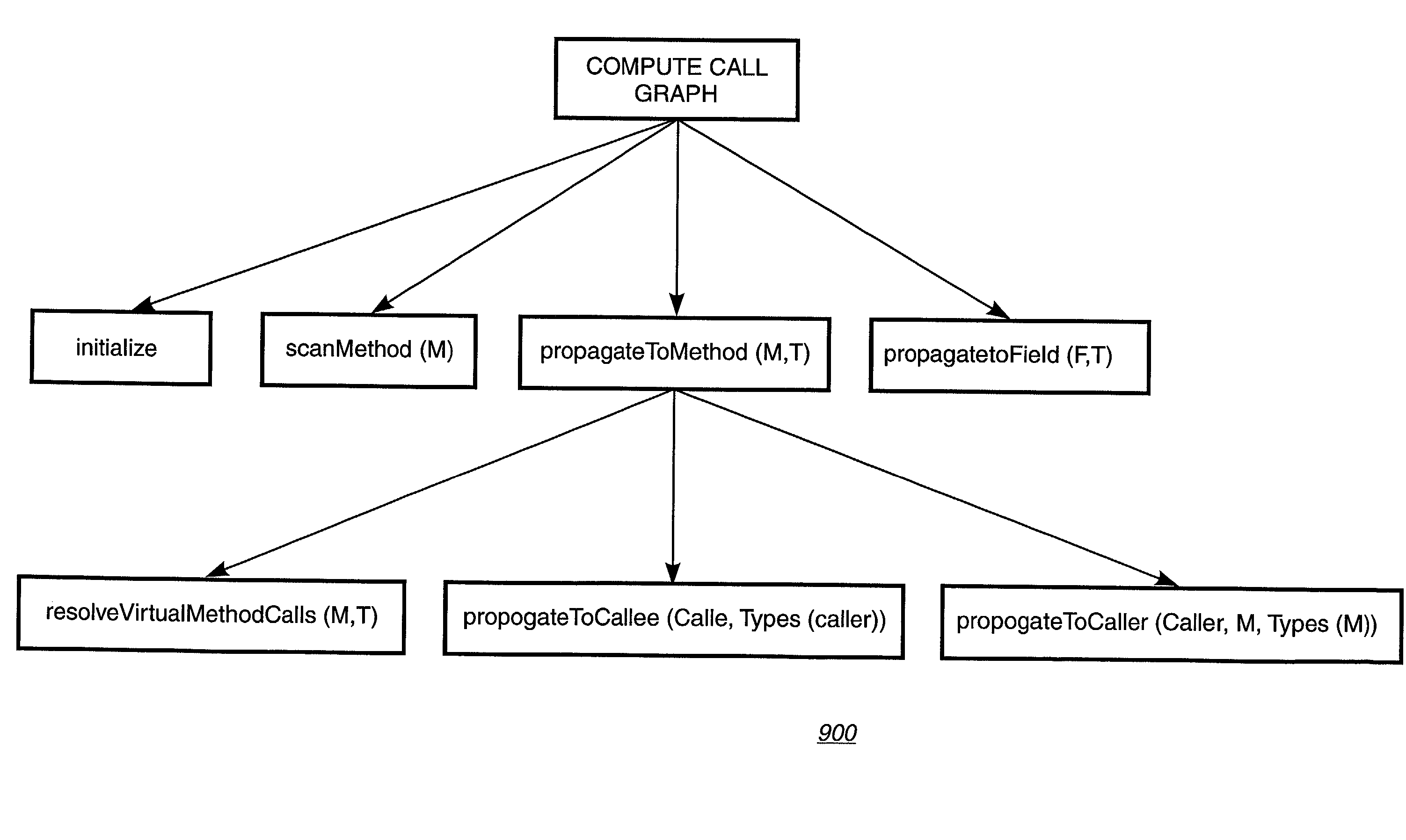
Scalable propagation-based methods for call graph construction
InactiveUS20030018603A1Cheap and less-preciseAvoid complicationsData processing applicationsDigital data processing detailsAlgorithmAllocation site
A program storage device, readably by a machine, tangibly embodying instructions to perform method steps for constructing a call graph whereby for each method M, a set of types SM of objects that may occur in method M is determined for each field F, a set of types SF of objects is determined that may be stored in field F, the method comprising: determining the allocation sites inside the body of method M; determining the set of directly called methods M' inside the body of method M; and determining the set of virtually called methods M'' inside the body of method M.
Owner:IBM CORP
Video encoding using variable bit rates
InactiveUS7409097B2Increase computational overheadImprove picture qualityPicture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningVideo encodingTheoretical computer science
A system and method is provided for variable bit rate encoding using a complexity ratio. Quantization parameter is calculated using a complexity ratio, which is equal to a local complexity divided by a global complexity. Complex pictures are allocated a larger bit budget relative to simple pictures. With the larger bit budget the quality of complex pictures can be maintained while reducing the overall size of the encoded video stream.
Owner:CRP STEVENS CREEK L L C
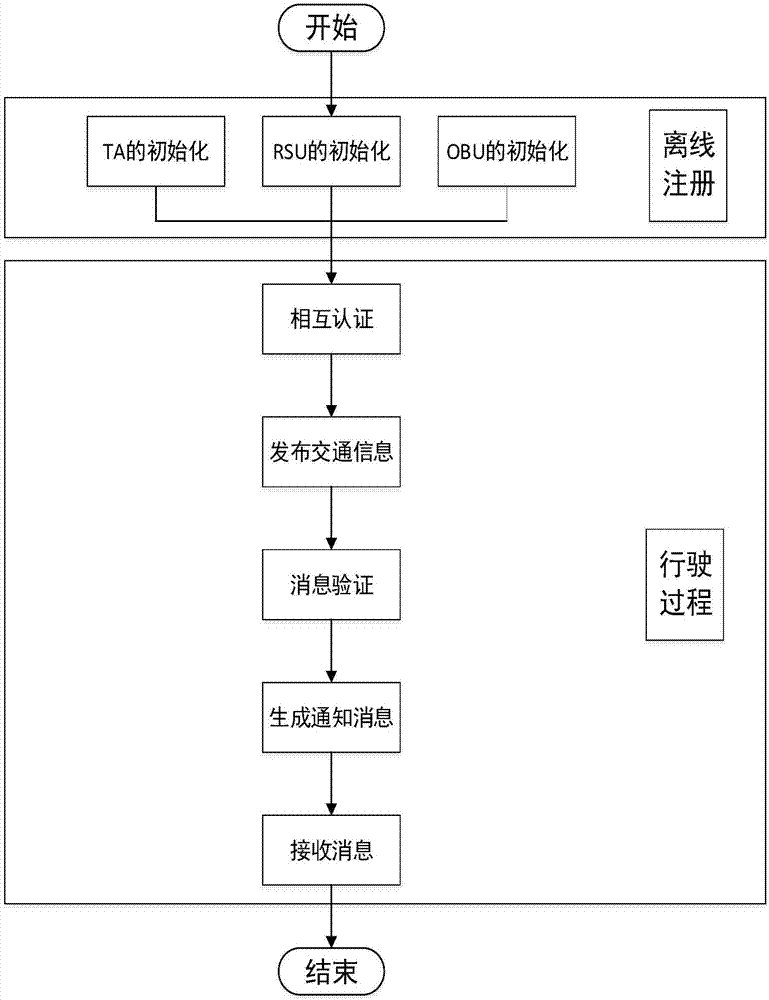
Method for protecting vehicular ad hoc network conditional privacy based on registration list
ActiveCN107580006AReduce time spentPrevent postingUser identity/authority verificationInternet privacyOn board
The invention discloses a method for protecting the vehicular ad hoc network conditional privacy based on a registration list. The method comprises the following steps: (1) offline registration, including trusted association TA initialization, road-side unit RSU initialization and on-board unit OBU initialization; and (2) driving process, including mutual authentication, traffic information release, message authentication, notice message generation and message receiving. According to the method, a vehicle user carries out cooperative communication with RSU which are deployed on two sides of aroad through the OBU, so that the driving safety can be effectively improved, and users can conveniently and quickly acquire related service.
Owner:ANHUI UNIVERSITY
Inter-satellite networking authentication system and method suitable for double-layer satellite network
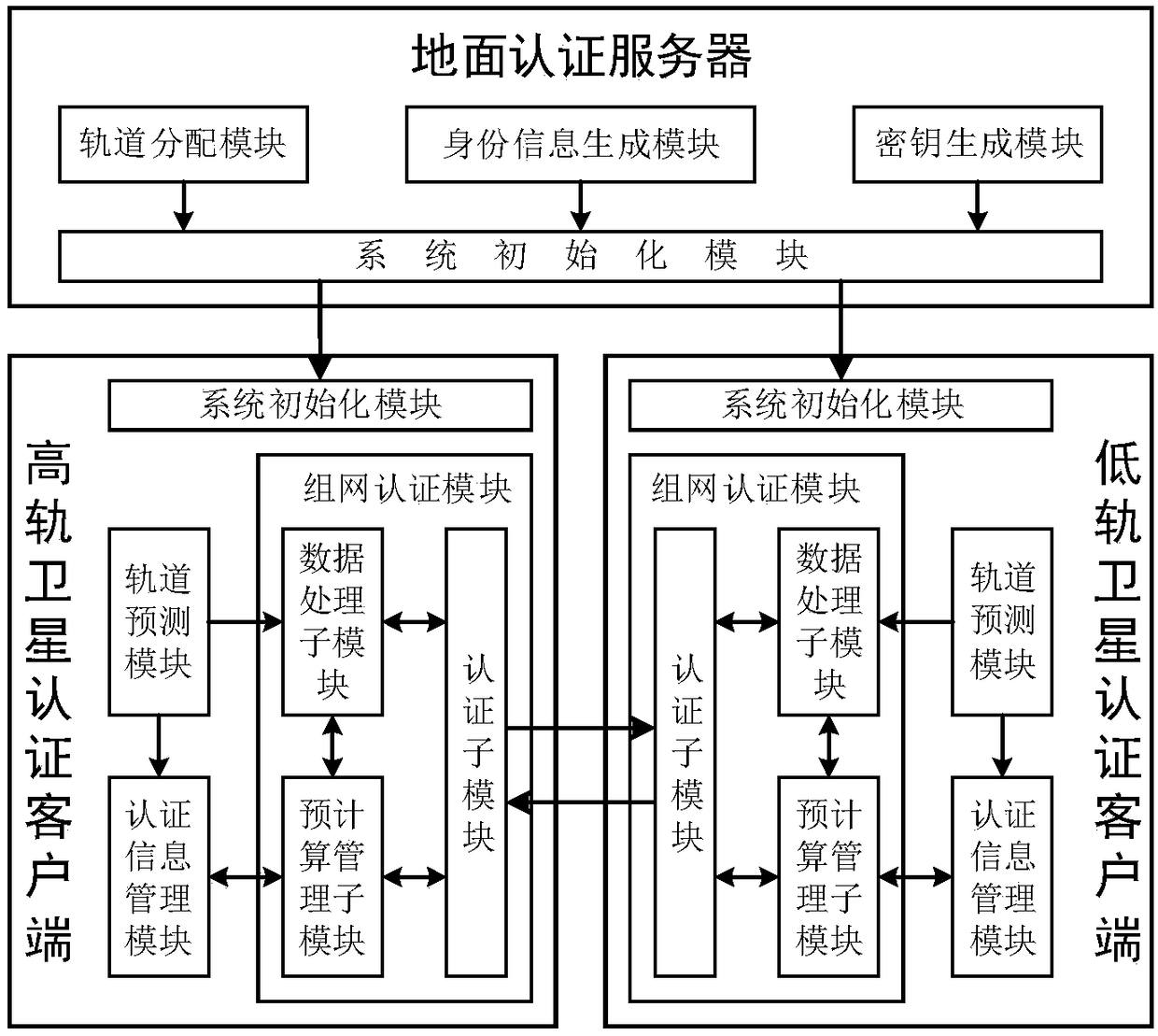
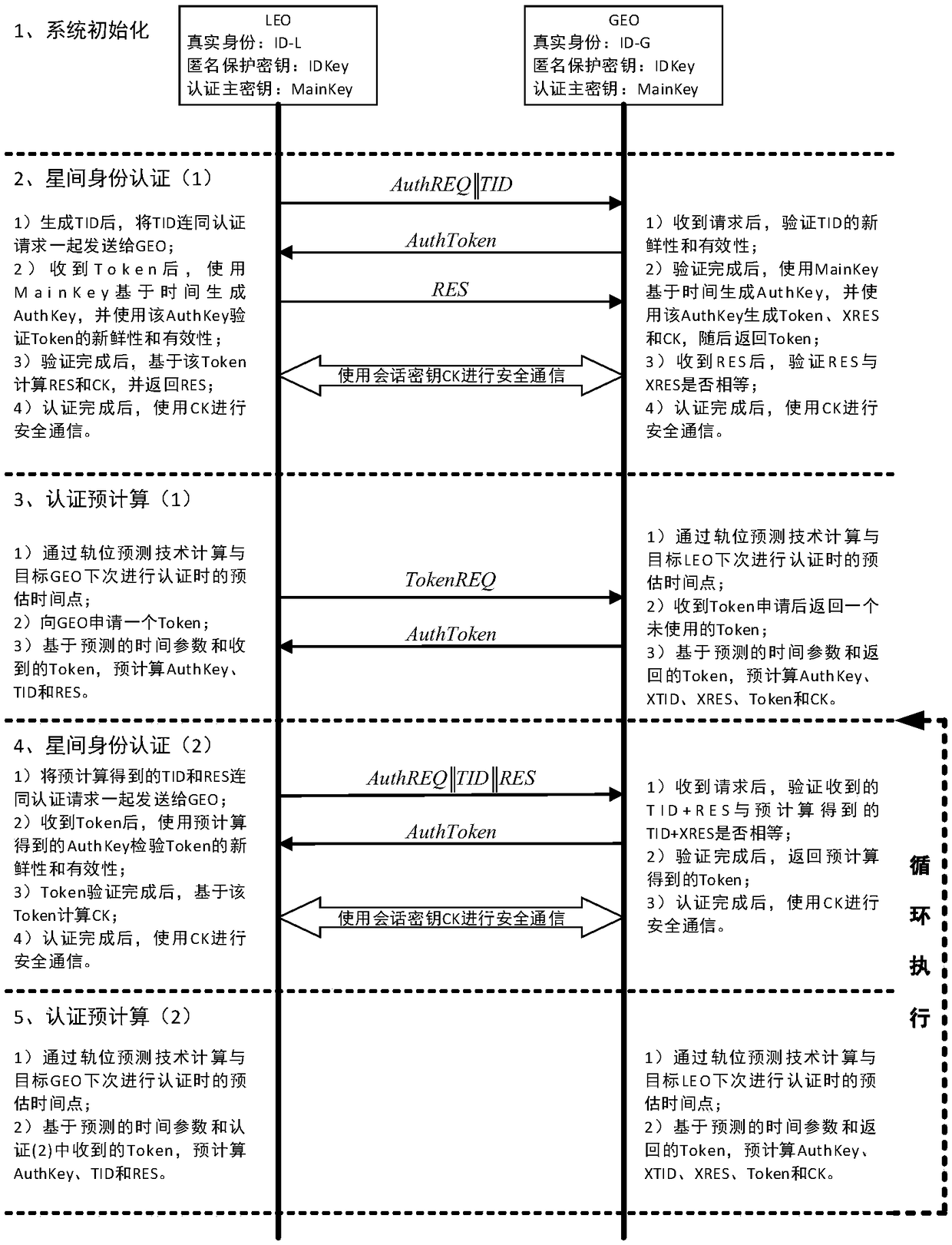
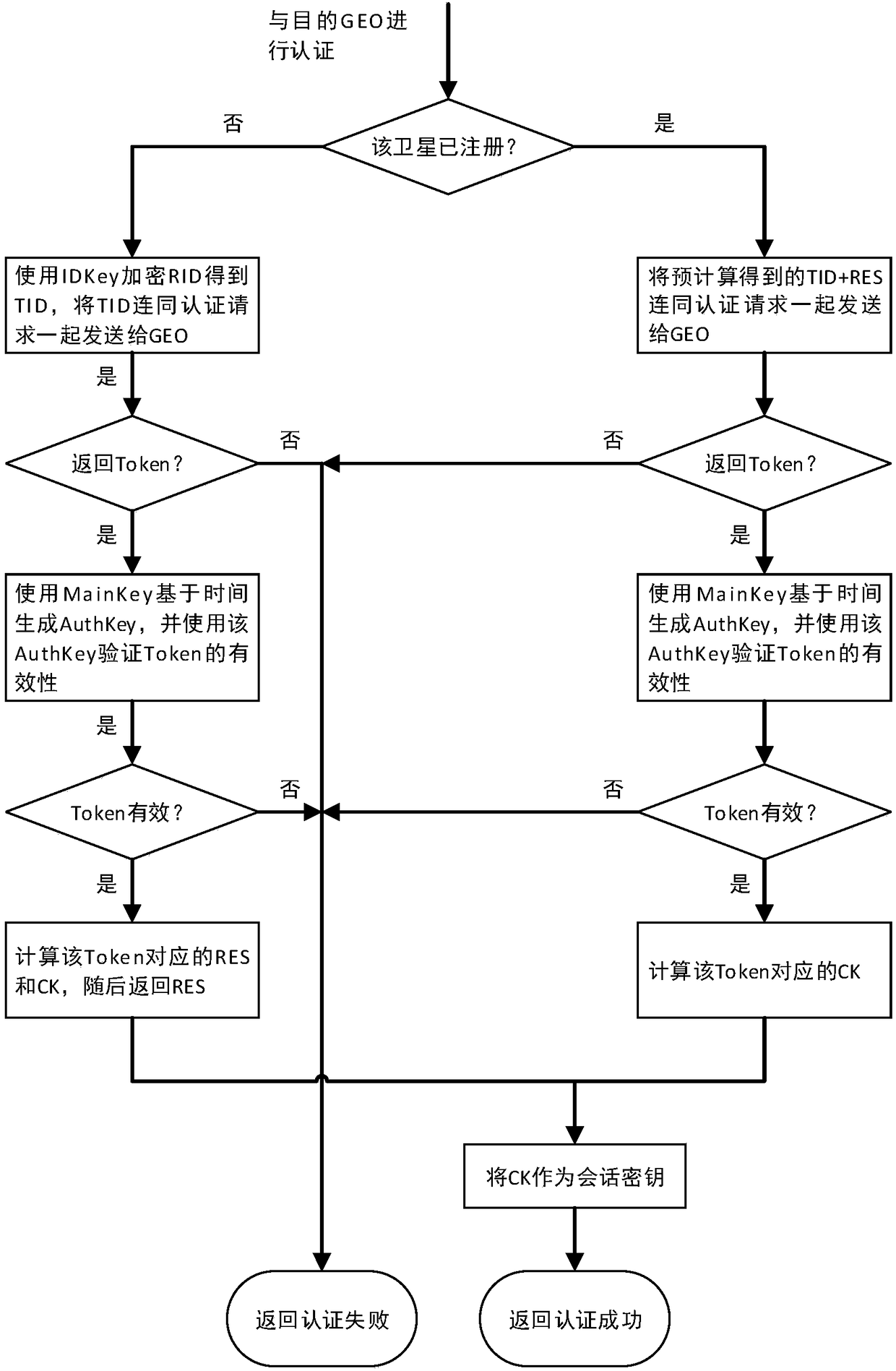
ActiveCN108566240AJudging freshnessImprove authentication efficiencyKey distribution for secure communicationUser identity/authority verificationPrecomputationAuthentication server
The invention belongs to the technical field of information safety, and discloses an inter-satellite networking authentication system and method suitable for a double-layer satellite network. The system comprises a ground authentication server, a high-orbit satellite authentication client and a low-orbit satellite authentication client, wherein the ground authentication server is used for completing initialization of a satellite authentication system, namely generating and distributing identity information, a secret key and track parameters which are needed for authentication between the satellites; the high-orbit satellite authentication client and the low-orbit satellite authentication client are main bodies of inter-satellite networking authentication, and the inter-satellite identity authentication and key negotiation are realized through the interaction of authentication parameters. An authentication precomputation mechanism is designed by utilizing the characteristics that a satellite network clock is highly synchronous and a node operation trajectory can be predicted, so that the authentication efficiency between the satellites is effectively improved. According to the system and the method, safe and efficient identity authentication and secret key negotiation of a high-orbit satellite and a low-orbit satellite in a networking stage can be realized, and the system and the method can be applied to networking authentication between the high-orbit satellite and the low-orbit satellite.
Owner:XIDIAN UNIV +1
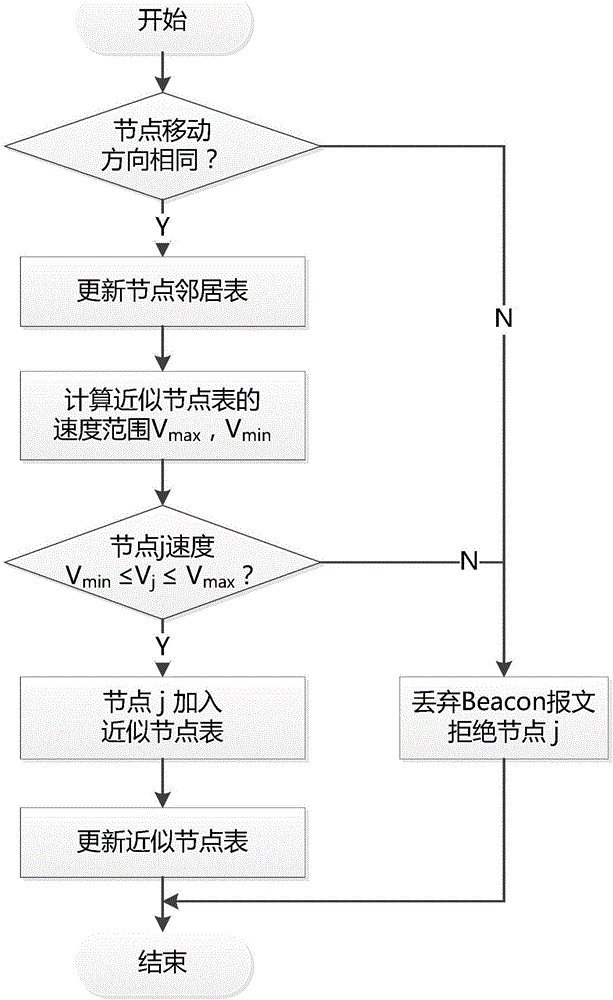
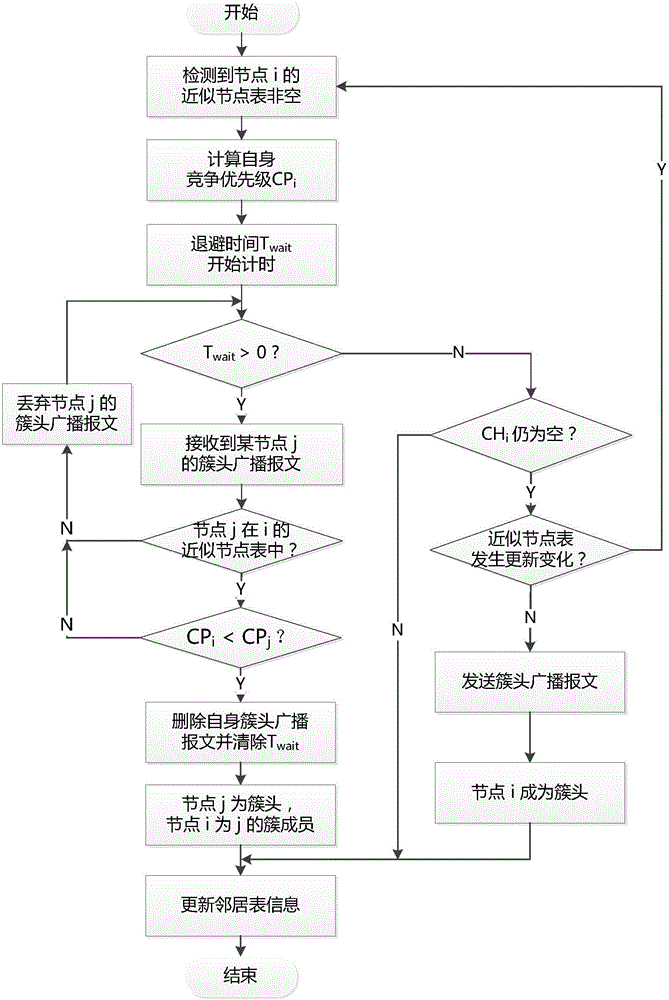
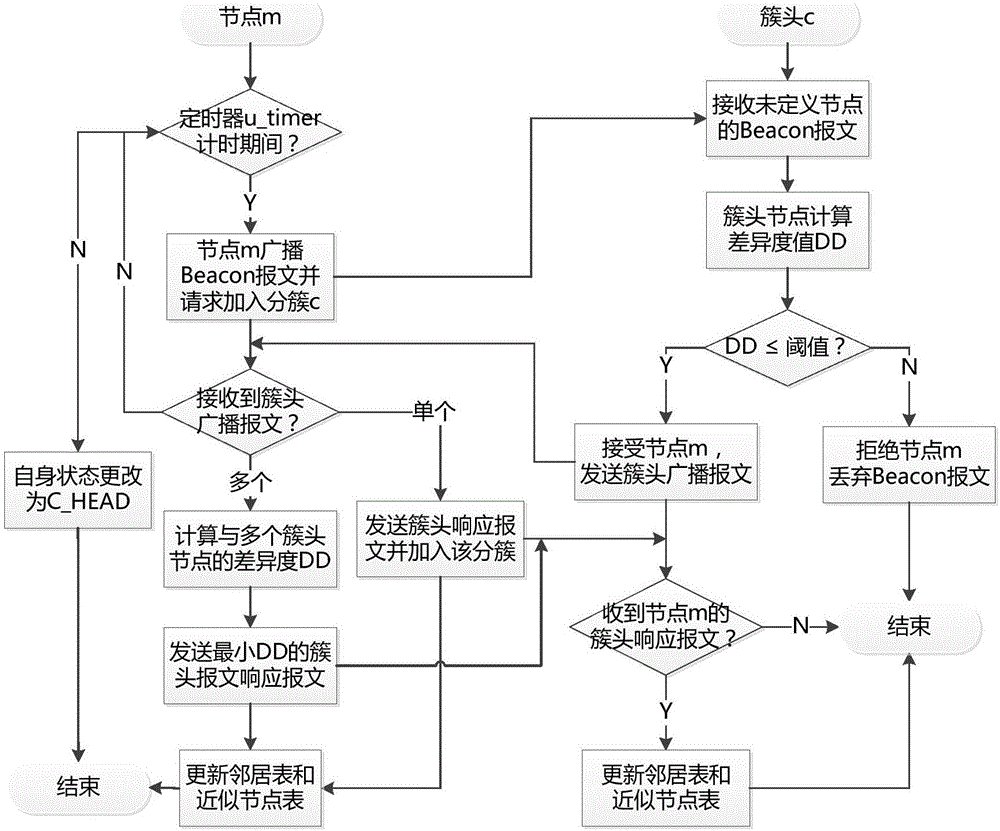
Vehicle routing protocol method with stability-based clustering in urban environment
The invention provides a vehicle routing protocol method with stability-based clustering in an urban environment. The method comprises approximate node clustering set formation, cluster head election and cluster maintenance. The approximate node clustering set formation means exchanging state information between adjacent nodes with the same moving direction through Beacon messages, modeling the randomly changing moving speed as a normal distribution model, forming an approximate node clustering set after excluding nodes which are greatly different from the whole in speed, and establishing and updating an approximate node table; the cluster head election means remodeling the speed, locations and adjacent node quantity of nodes in the approximate node table as a normal distribution model, and choosing the optimal cluster head node by calculating competing priorities; and the cluster maintenance means specifically processing joining / separation of nodes into / from clusters and combination of the clusters to guarantee the stability of the clusters. The cluster mechanism of the method owns a smaller cluster head change rate and a longer cluster head maintenance time; and the packet delivery ratio is effectively improved in the urban environment, and the delay is also effectively reduced in the urban environment.
Owner:SUN YAT SEN UNIV
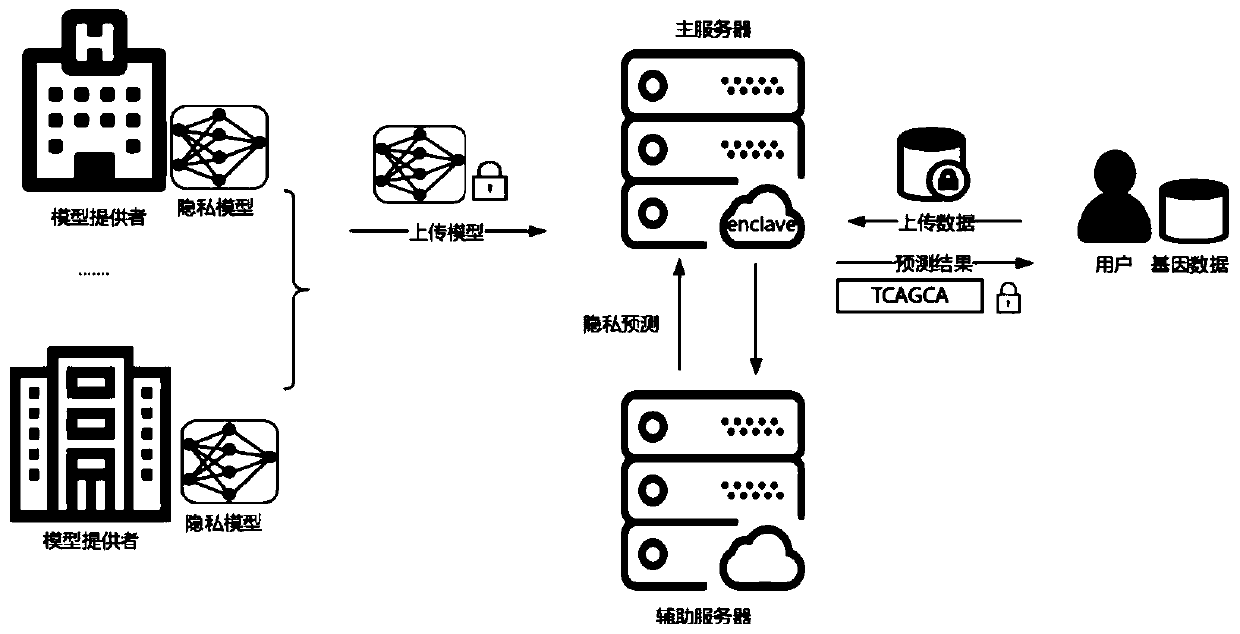
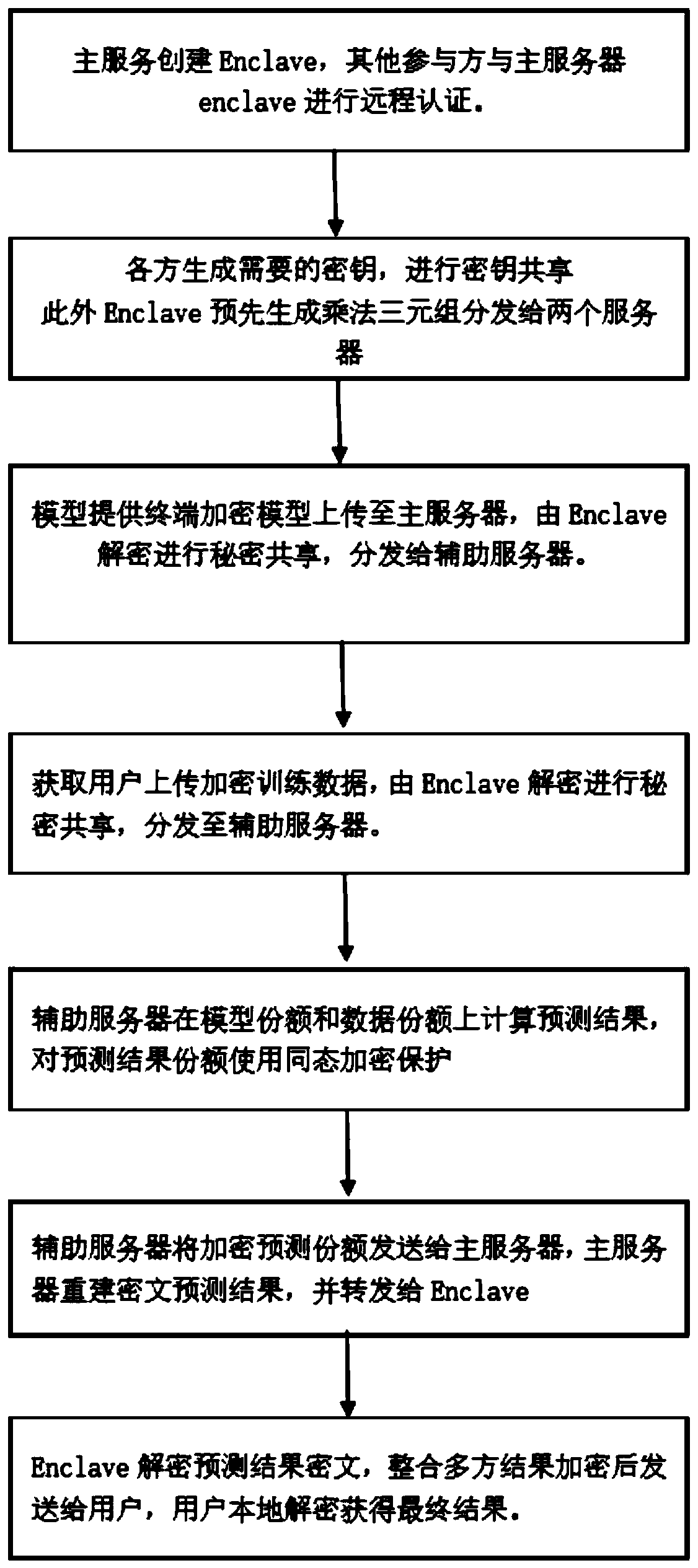
Data privacy protection-oriented machine learning prediction method and system
ActiveCN111275202APrevent theftReliable two-way securityDigital data protectionMachine learningData privacy protectionEngineering
The invention provides a data privacy protection-oriented machine learning prediction method and system. The method comprises the following steps of obtaining encrypted data; the main server creates acredible area, and decrypts the obtained to-be-predicted data and the prediction model in the credible area; the main server carries out secret sharing on the decrypted to-be-predicted data and the prediction model to obtain a data secret share and a model share respectively, and distributes the data secret share and the model share to an unconspired auxiliary server and the main server; the auxiliary server and the main server respectively perform prediction calculation to obtain a prediction result share; and the main server carries out secret reconstruction on all the prediction result shares, forwards the reconstructed prediction result shares to the trusted area for integration and encryption, and sends the reconstructed prediction result shares to the to-be-predicted data providingterminal, and the data providing terminal decrypts the reconstructed prediction result shares to obtain a prediction result predicted according to the model. Privacy security of the two parties is protected by combining secure multi-party computing and an SGX technology, and the security problem in the prediction service providing process is solved.
Owner:UNIV OF JINAN
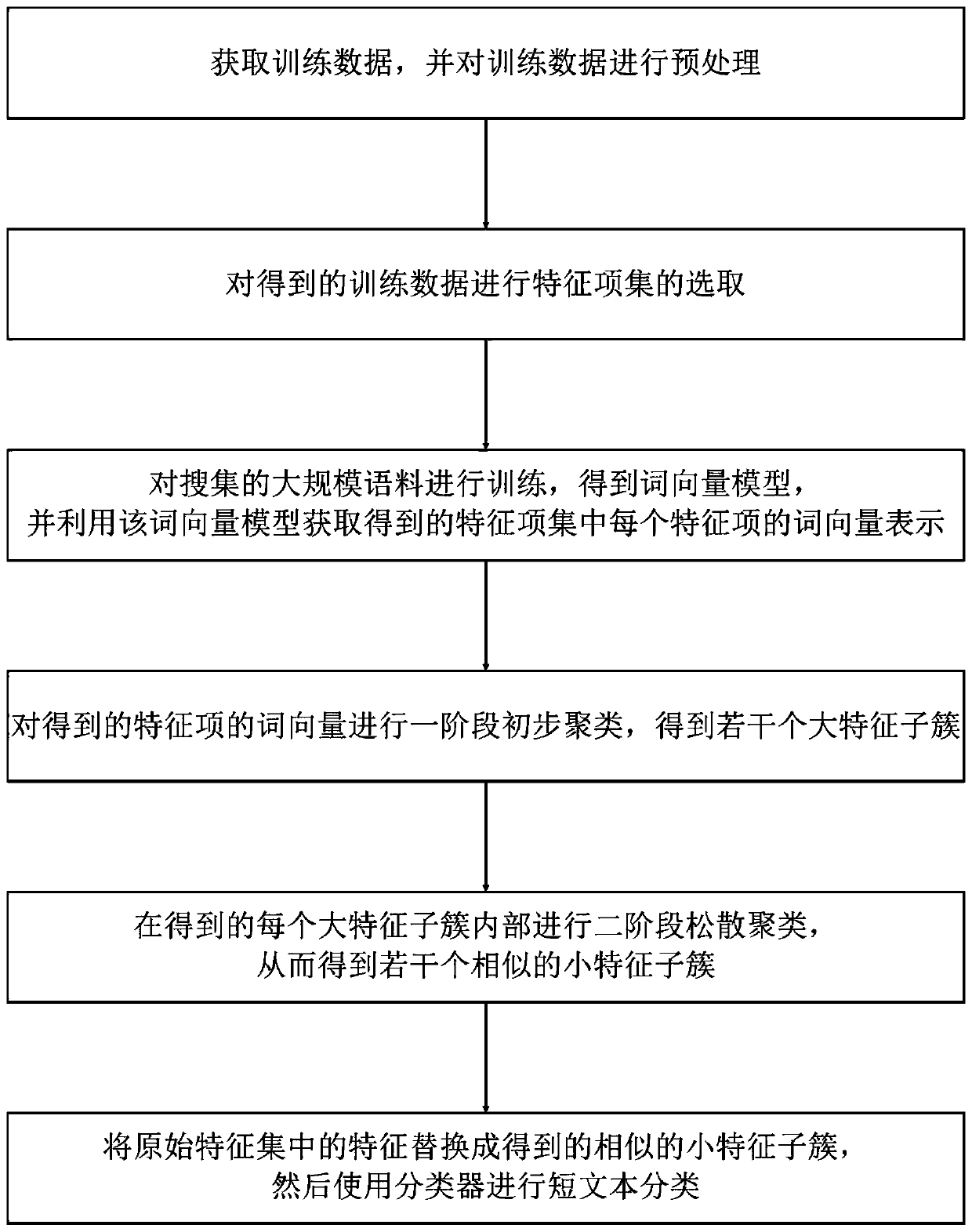
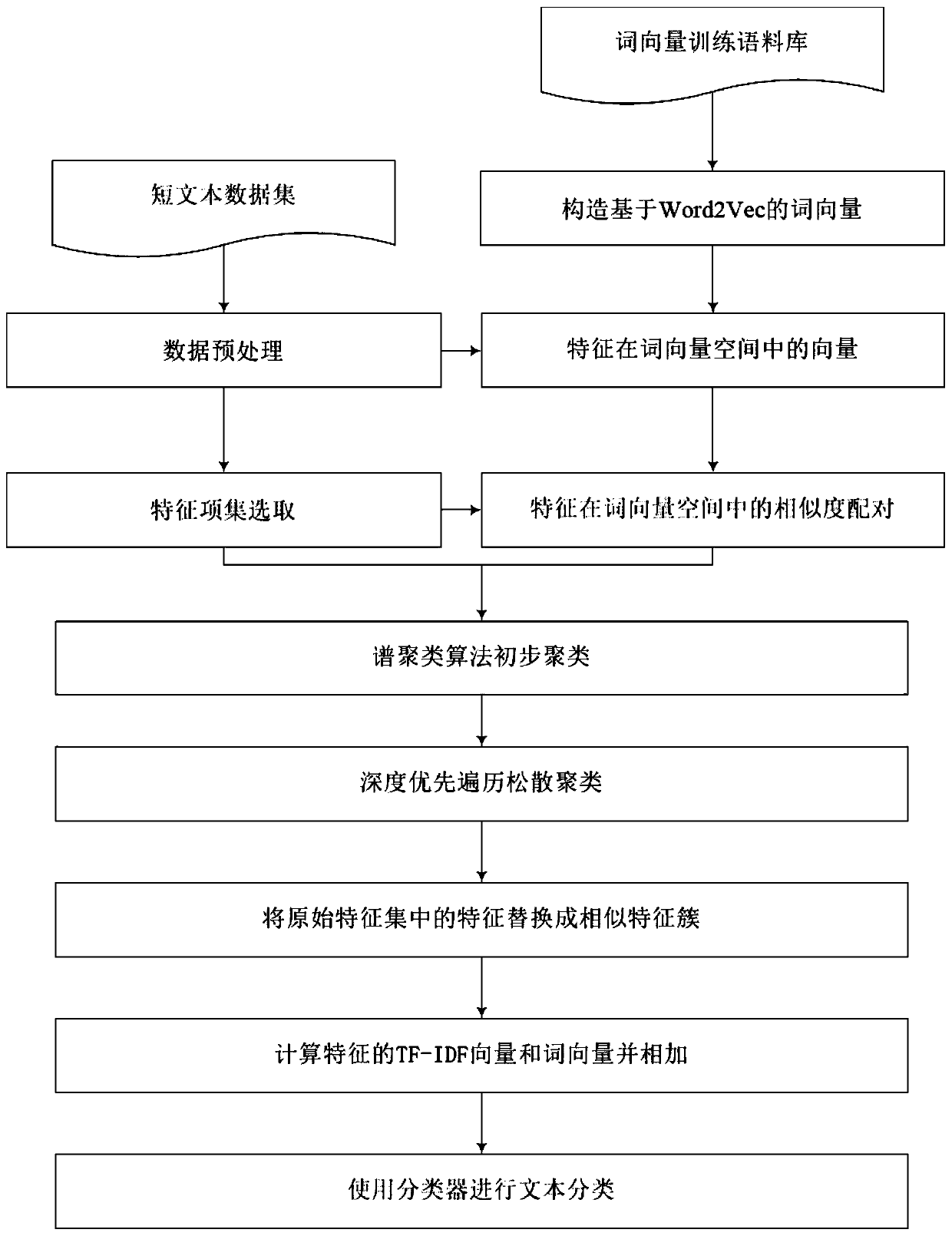
Short text-oriented optimization classification method
ActiveCN109960799AQuality improvementEnhanced Semantic Representation CapabilitiesSemantic analysisCharacter and pattern recognitionData setMicroblogging
The invention discloses a short text-oriented optimization classification method. The method comprises the following steps of: 1, obtaining an original data set and preprocessing the original data set; 2, selecting a feature item set from the preprocessed data set; 3, training the collected large-scale corpora by using a word vector tool to obtain a word vector model; 4, performing word vector representation on each feature item in the feature item set by using a word vector model, and performing primary clustering on the word vectors of the feature items to obtain a plurality of primary feature clusters; 5, performing two-stage loose clustering in each preliminary feature cluster to obtain a plurality of similar feature clusters; and 6, replacing the feature words obtained in the step 4 with the similar feature clusters obtained in the step 5, and then carrying out short text classification by using a classifier. Traditional short text classification mostly lacks semantic expression capability and is quite high in demnsion of the feature space; according to the invention, the semantic information of the short text can be expressed better, the dimension of the feature space is reduced, the precision and efficiency of short text classification are improved, and the short text classification method can be applied to short text classification tasks in various fields, such as spamshort message classification and microblog topic classification.
Owner:长沙市智为信息技术有限公司
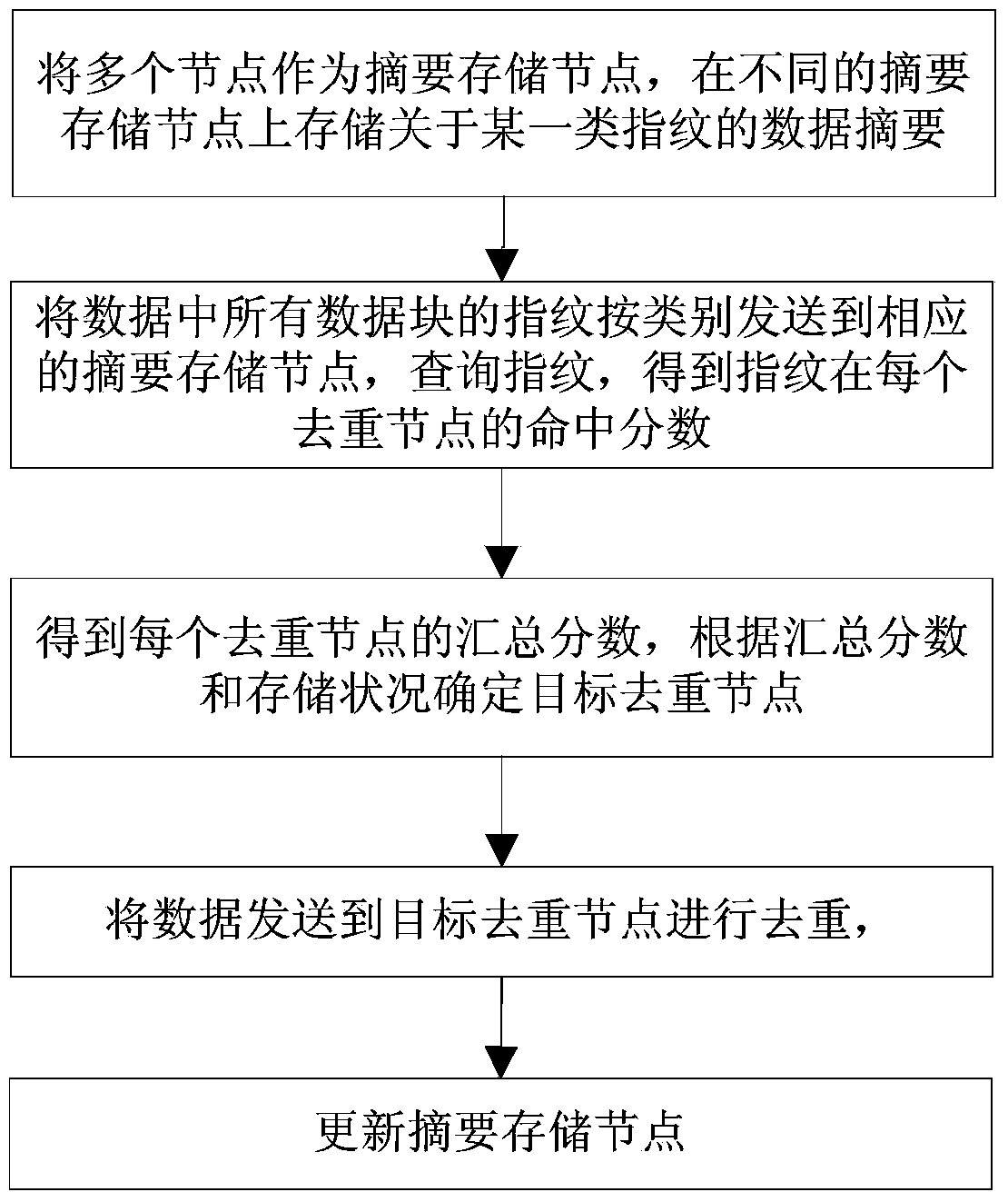
Distributed duplication elimination system-oriented data routing method
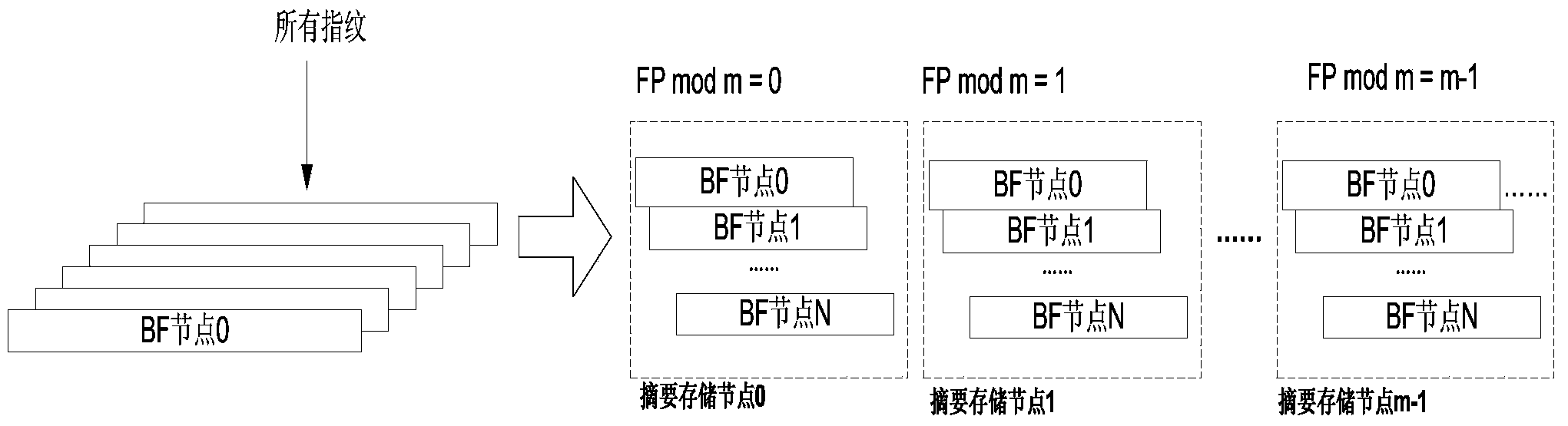
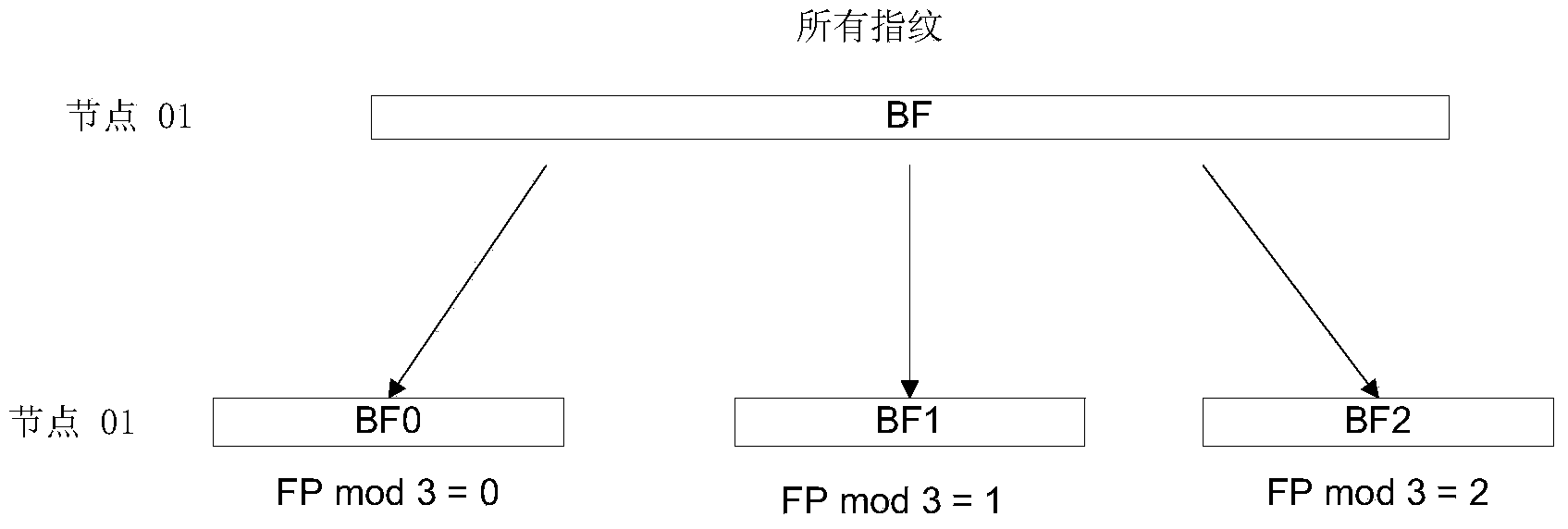
ActiveCN103631933AImprove scalabilityFix out of memory issuesTransmissionSpecial data processing applicationsDistributed computingFingerprint
The invention provides a distributed duplication elimination system-oriented data routing method, which comprises the following steps that a server categorizes fingerprints of all data blocks forming data, and transmits the fingerprints of different categories to different abstract storage nodes for storing data abstracts of the fingerprints of the corresponding categories respectively; the received fingerprints in the abstract storage nodes are queried to obtain hit scores of the fingerprints in each duplication elimination node; the hit scores are returned to the server; the server obtains a summery score of each duplication elimination node according to the hit scores of the fingerprints in each duplication elimination node, and determines a target duplication elimination node by combining the summery scores and the storage conditions of the duplication elimination nodes. According to the method, duplication elimination effect and the storage utilization rate are balanced, the communication and calculation overhead in a fingerprint query process is effectively inhibited, and the data routing expandability of a distributed duplication elimination system is improved.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Convolutional neural network structure simplification and image classification method based on evolutionary strategy
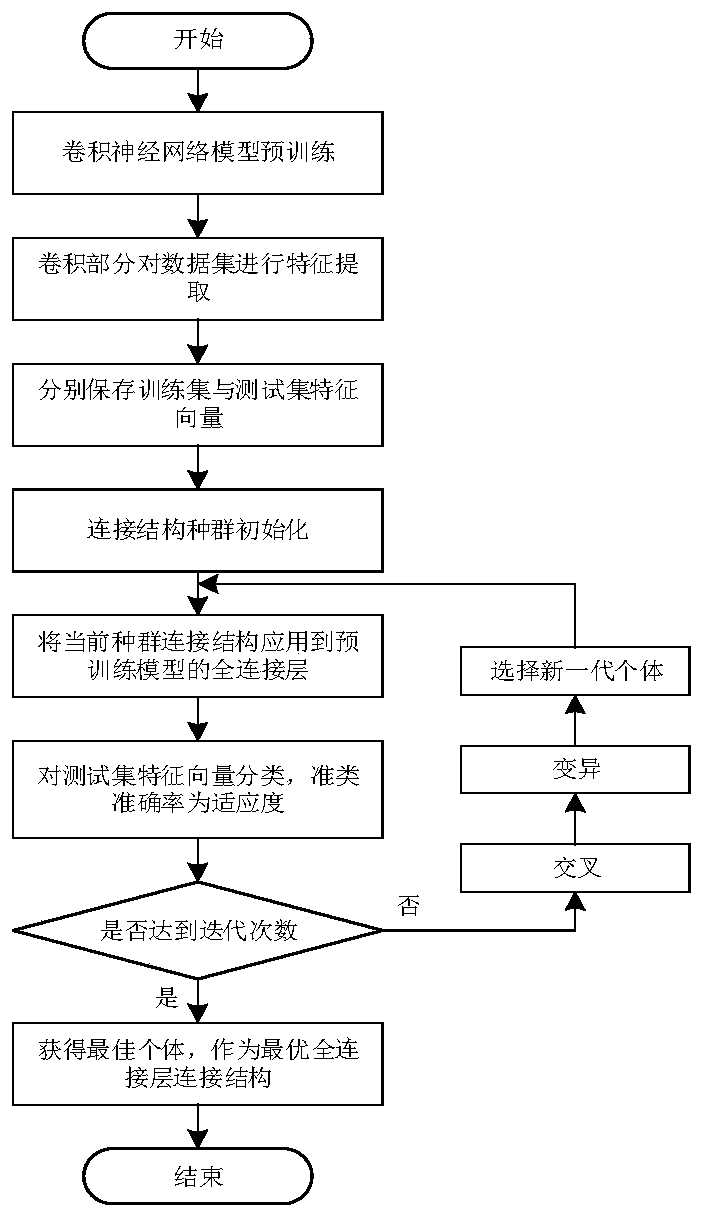
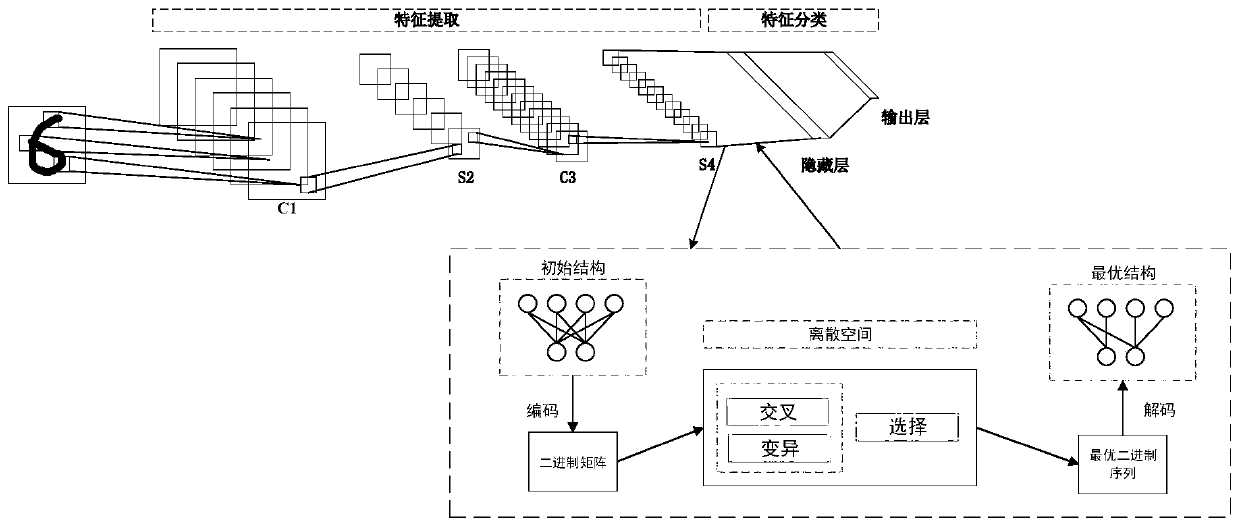
InactiveCN110427965AReduce computational overheadGuaranteed classification accuracyCharacter and pattern recognitionArtificial lifeData setTest set
The invention provides a convolutional neural network structure simplification and image classification method based on an evolutionary strategy. The structure between a convolution model feature extraction part and a full connection layer is simplified. The method comprises the following steps: firstly, pre-training a convolution model to fix a model weight, and performing feature extraction on an image data set by using a convolution part; then, randomly generating a plurality of binary sequences to serve as an initial population, wherein each binary sequence corresponds to a structure between a feature extraction part and a full connection layer; then, under each structure of the current population, using the pre-trained weight to classify the feature vectors of the test set, using theclassification accuracy as the fitness of the corresponding structure, obtaining a new-generation structure population through crossover, variation and selection operations, and continuously iteratingto be equal to the number of iterations; and finally, obtaining a structure between the simplified feature extraction part and the full connection layer, and performing fine adjustment on the pre-training weight by applying the structure.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
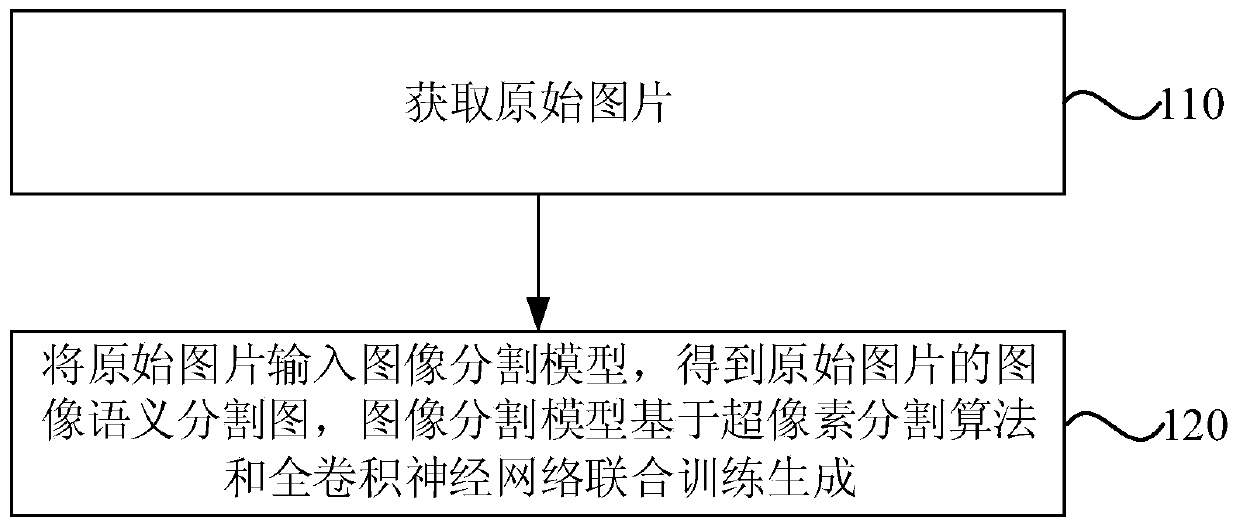
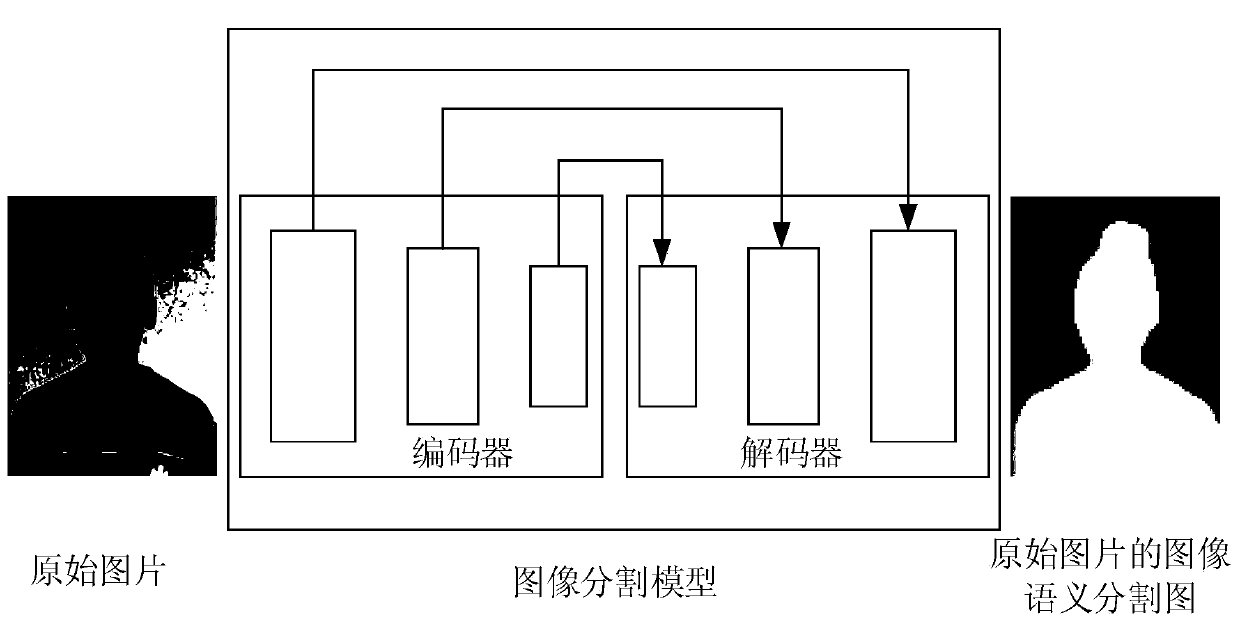
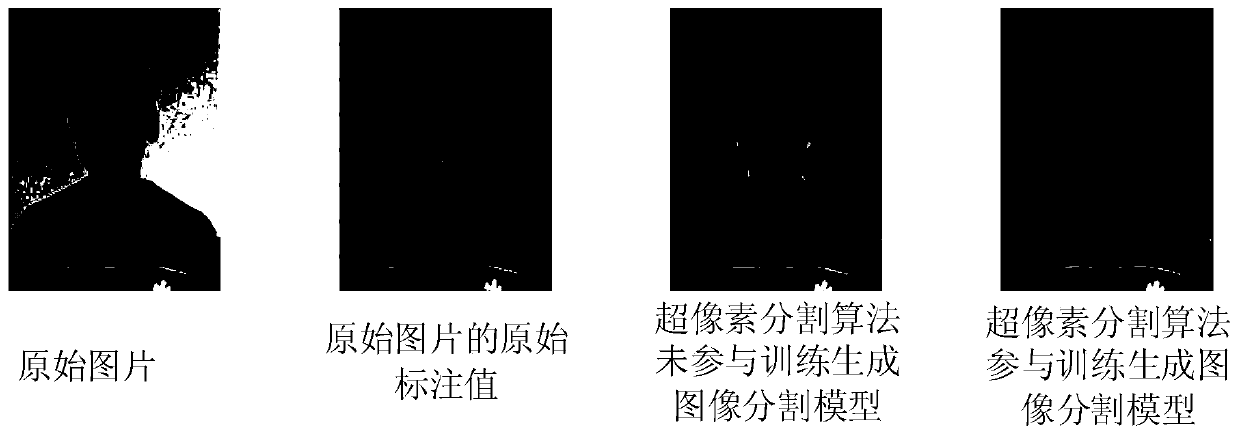
Image segmentation method, device and equipment and storage medium
PendingCN111489357AIncrease computational overheadImprove forecast accuracyImage analysisEngineeringSpatial consistency
The invention discloses an image segmentation method, device and equipment and a storage medium. The method comprises the steps of obtaining an original picture; and inputting the original picture into an image segmentation model to obtain an image semantic segmentation image of the original picture, and generating the image segmentation model based on joint training of a superpixel segmentation algorithm and a full convolutional neural network. According to the embodiment of the invention, when image semantic segmentation is carried out on an original image by using an image segmentation model generated by training a super-pixel segmentation algorithm and a full convolutional neural network, the low-level features of the original picture are identified; the generated image semantic segmentation image is accurate in edge positioning and good in space consistency; the super-pixel segmentation algorithm only participates in the training generation process of the image segmentation modelbut not participates in the process of generating the image semantic segmentation graph by adopting the image segmentation model, so that compared with the image segmentation model generated only based on full convolutional neural network training, the prediction precision of the model is improved on the basis of not increasing the calculation overhead.
Owner:GUANGZHOU BAIGUOYUAN INFORMATION TECH CO LTD
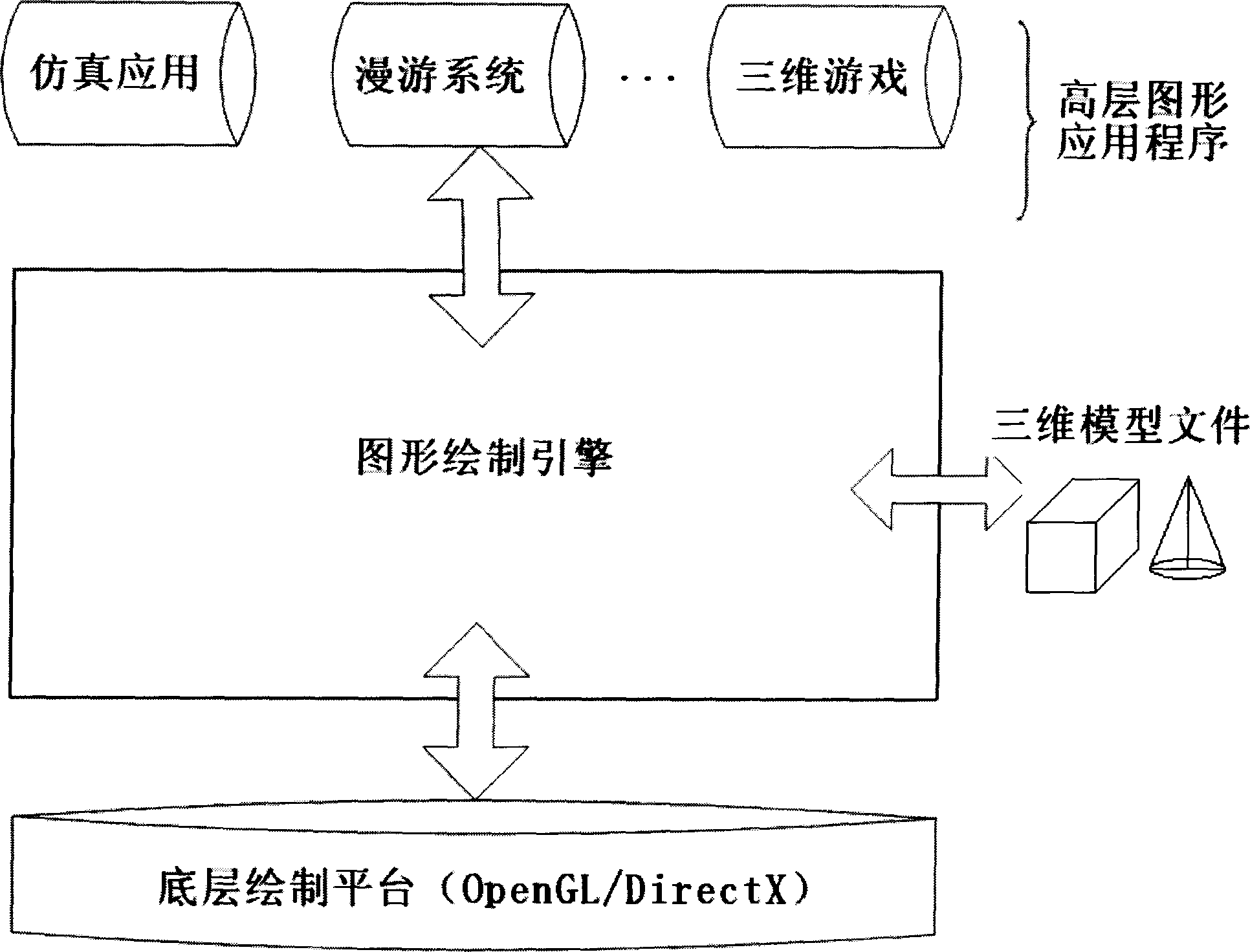
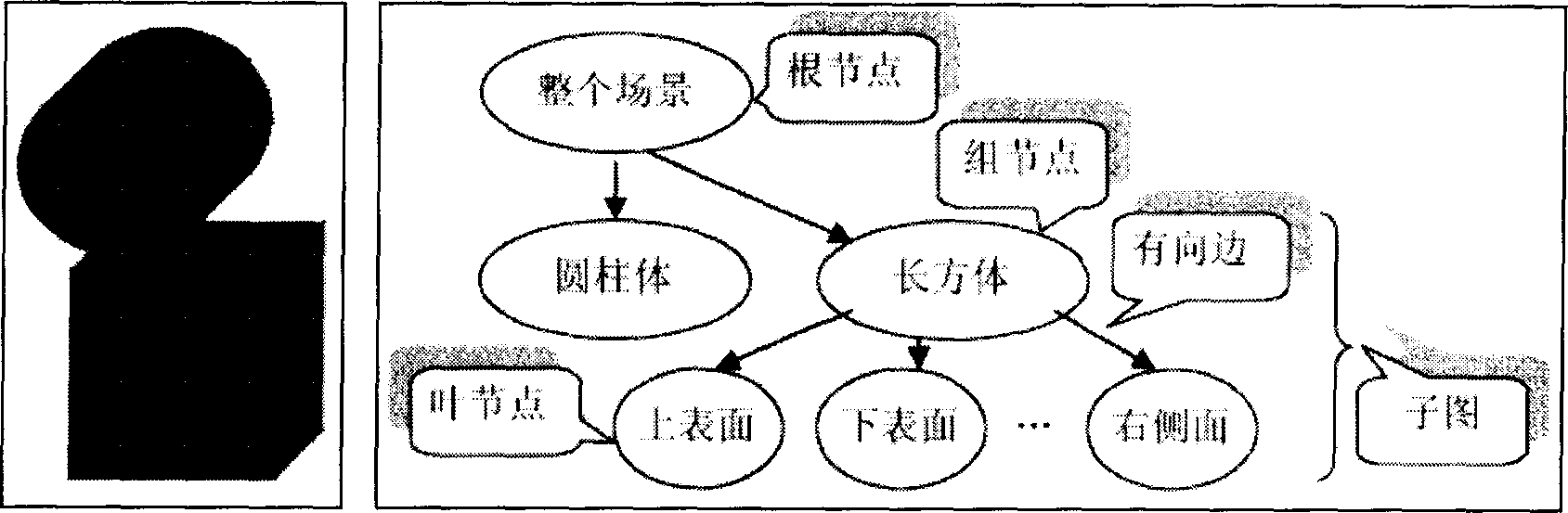
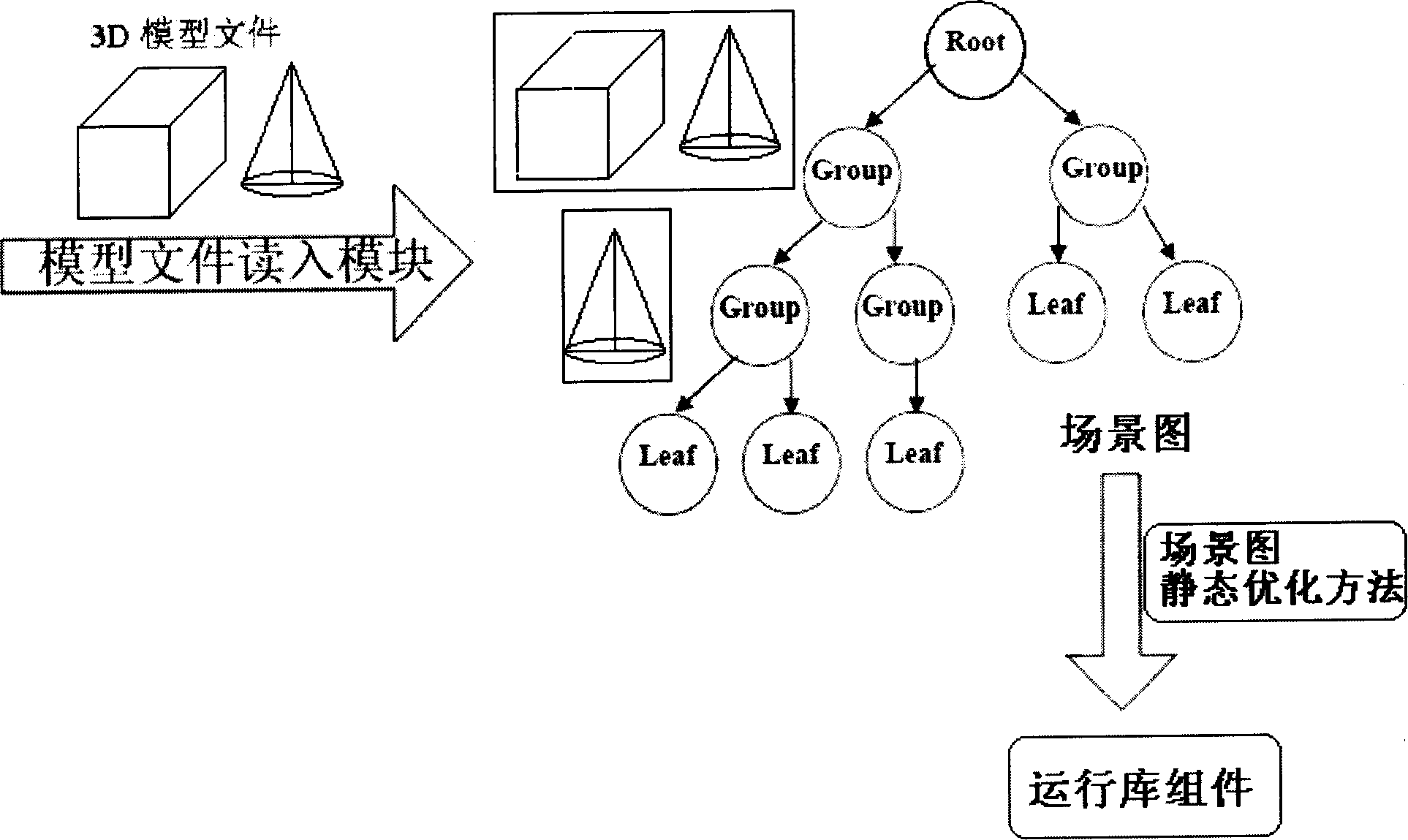
Pattern drawing platform-oriented scene graph optimizational designing method
InactiveCN1773494AOptimize structureReduce time overheadImage data processing detailsSpecial data processing applicationsScene graphDesign methods
A method for designing scene picture facing to picture drawing platform includes combining multiple Leaf nodes being brothers to each other with multiple Group nodes being brothers to each other if they have the same state control information and so on, combining LOD nodes being brothers to each other and being under Group node if they are near center, operating static Transform with its children and grandchildren nodes in advance and discard Transform node in scene picture, eliminating empty node and redundant node.
Owner:BEIHANG UNIV
Camera device and method for capturing a surrounding region of a vehicle in a situation-adapted manner
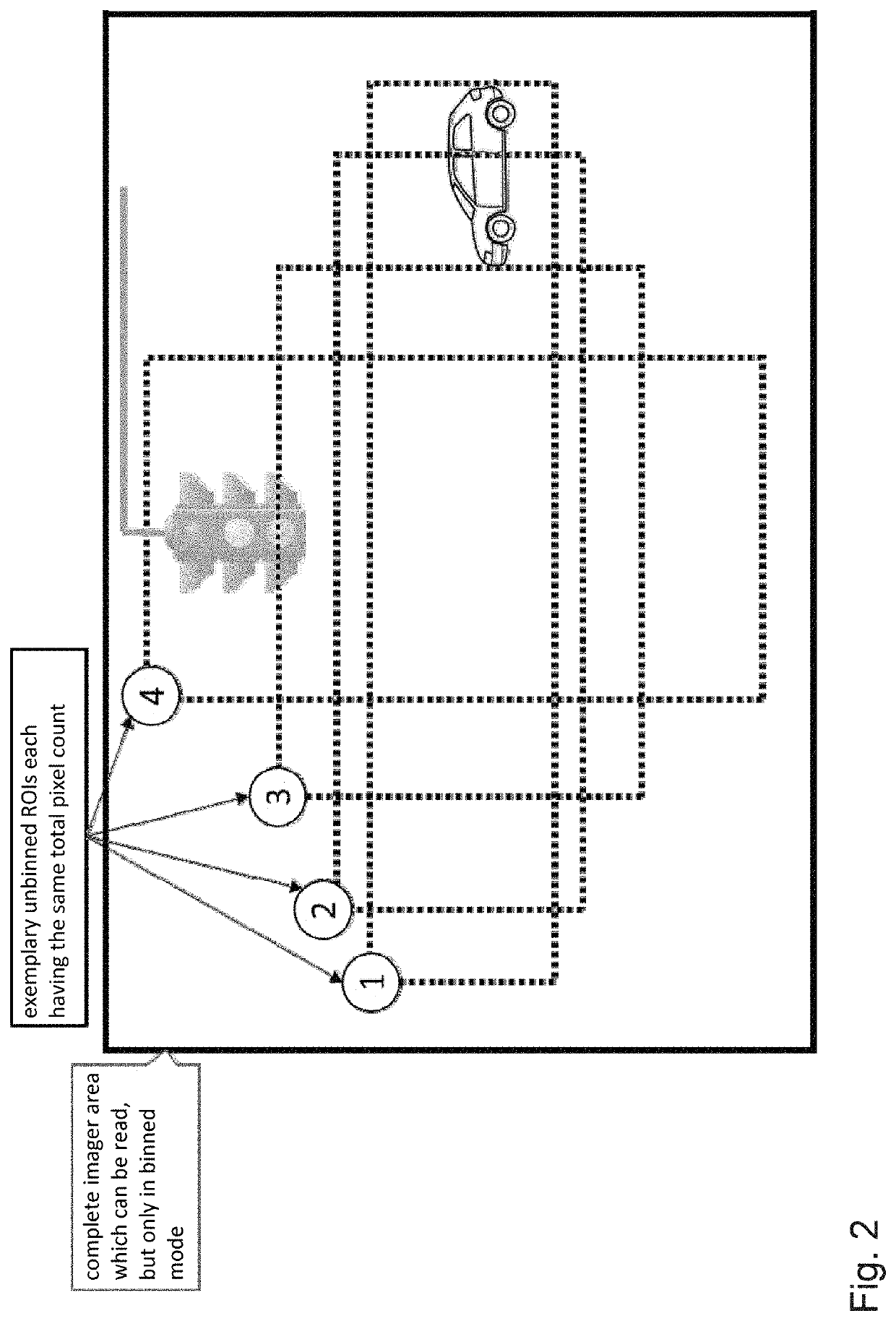
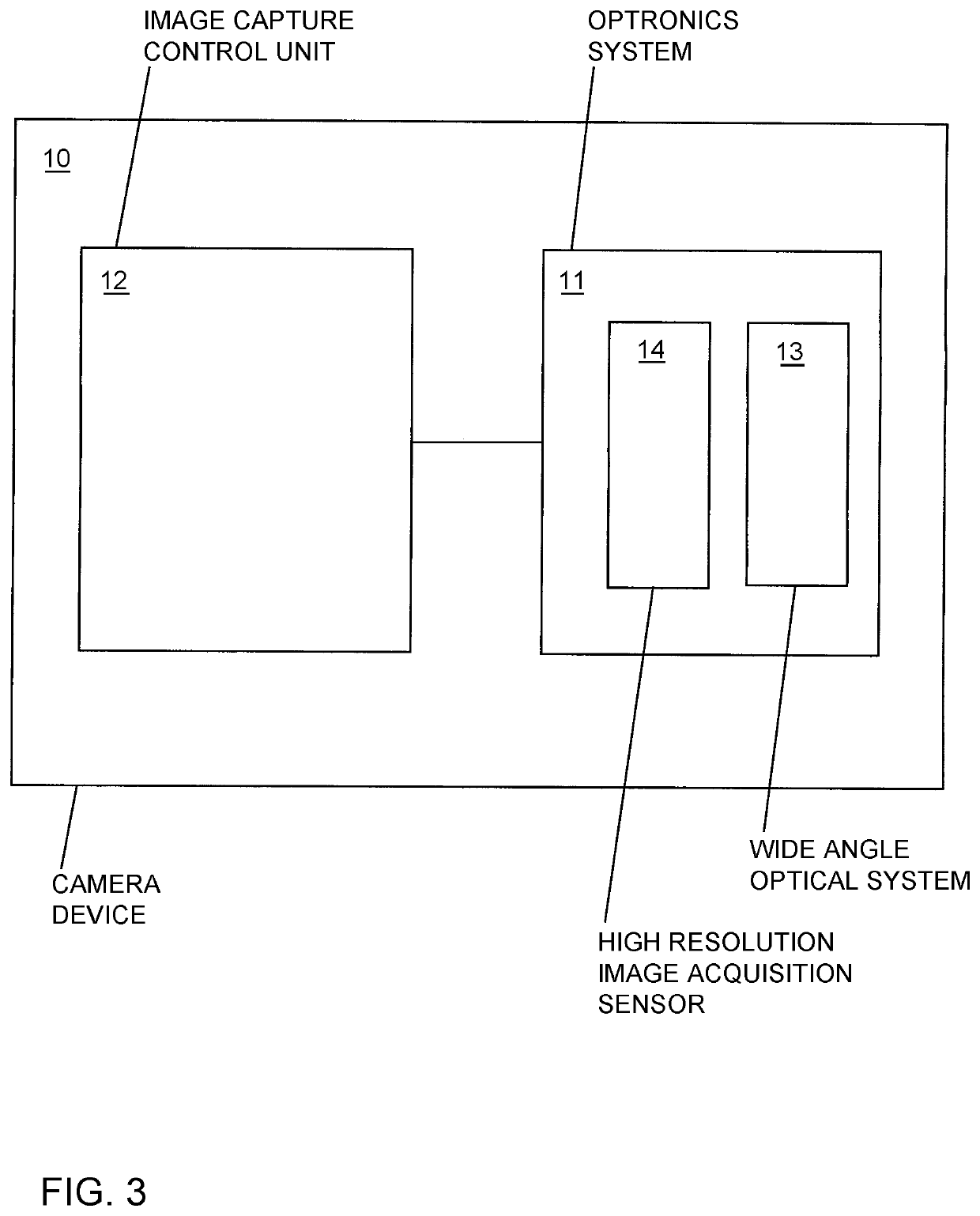
ActiveUS10798319B2Improve latencyNegative performanceTelevision system detailsCharacter and pattern recognitionComputer graphics (images)Image resolution
A camera device includes an optronics system and an image capture control unit, for acquiring a sequence of images of a surrounding region of a vehicle. The optronics system includes a wide-angle optical system and a high-resolution image acquisition sensor. The optronics system and the image capture control unit are configured to generate a reduced-resolution binned image of the entire capture region of the optronics system, or to capture an unbinned high-resolution image of a subregion of the capture region, respectively for each individual image of the sequence of images, depending on a current traffic and / or surrounding situation. A height and a width of the subregion are set depending on the current situation. A size of the subregion is set such that the pixel count of the high-resolution image of the subregion is no greater than the pixel count of the reduced-resolution image of the entire capture region.
Owner:CONTI TEMIC MICROELECTRONIC GMBH
Position information hiding method and position server
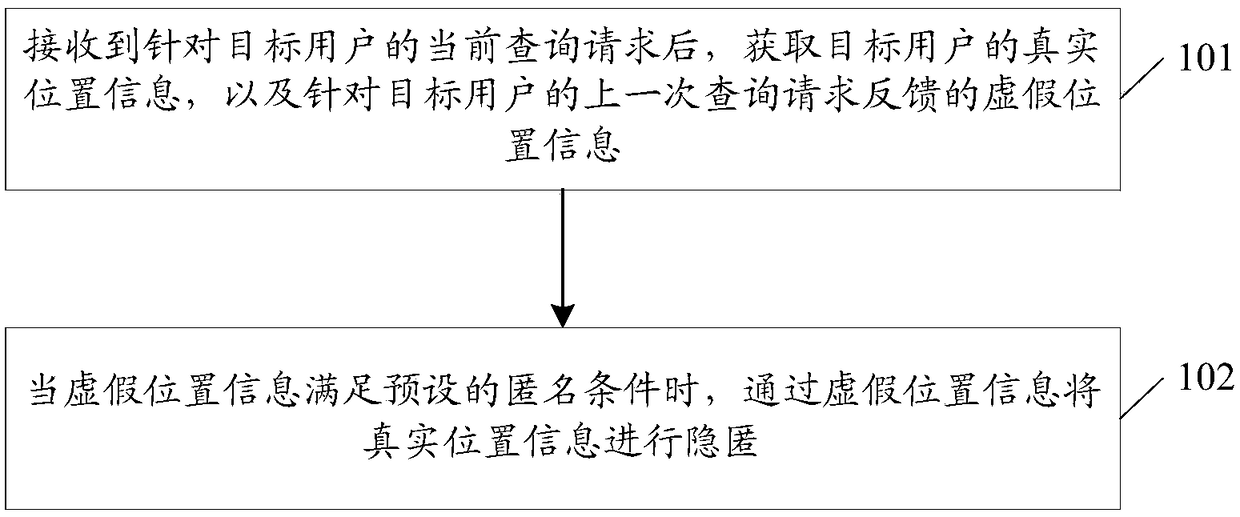
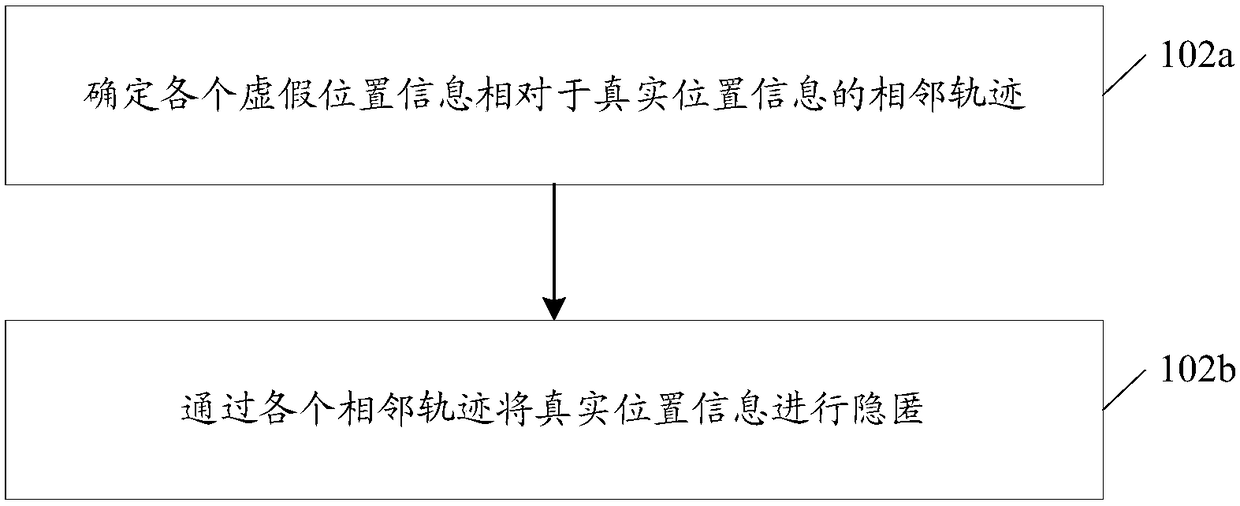
ActiveCN109327485AIncrease computational overheadGuaranteed availabilityTransmissionInformation hidingAnonymity
The embodiment of the invention discloses a position information hiding method and a position server. The method comprises the following steps: after receiving a current query request aiming at a target user, acquiring real position information of the target user, and false position information fed back aiming at last query request of the target user; and when the false position information satisfies a preset anonymity condition, hiding the real position information through the false position information.
Owner:CHINA MOBILE COMM GRP CO LTD +1
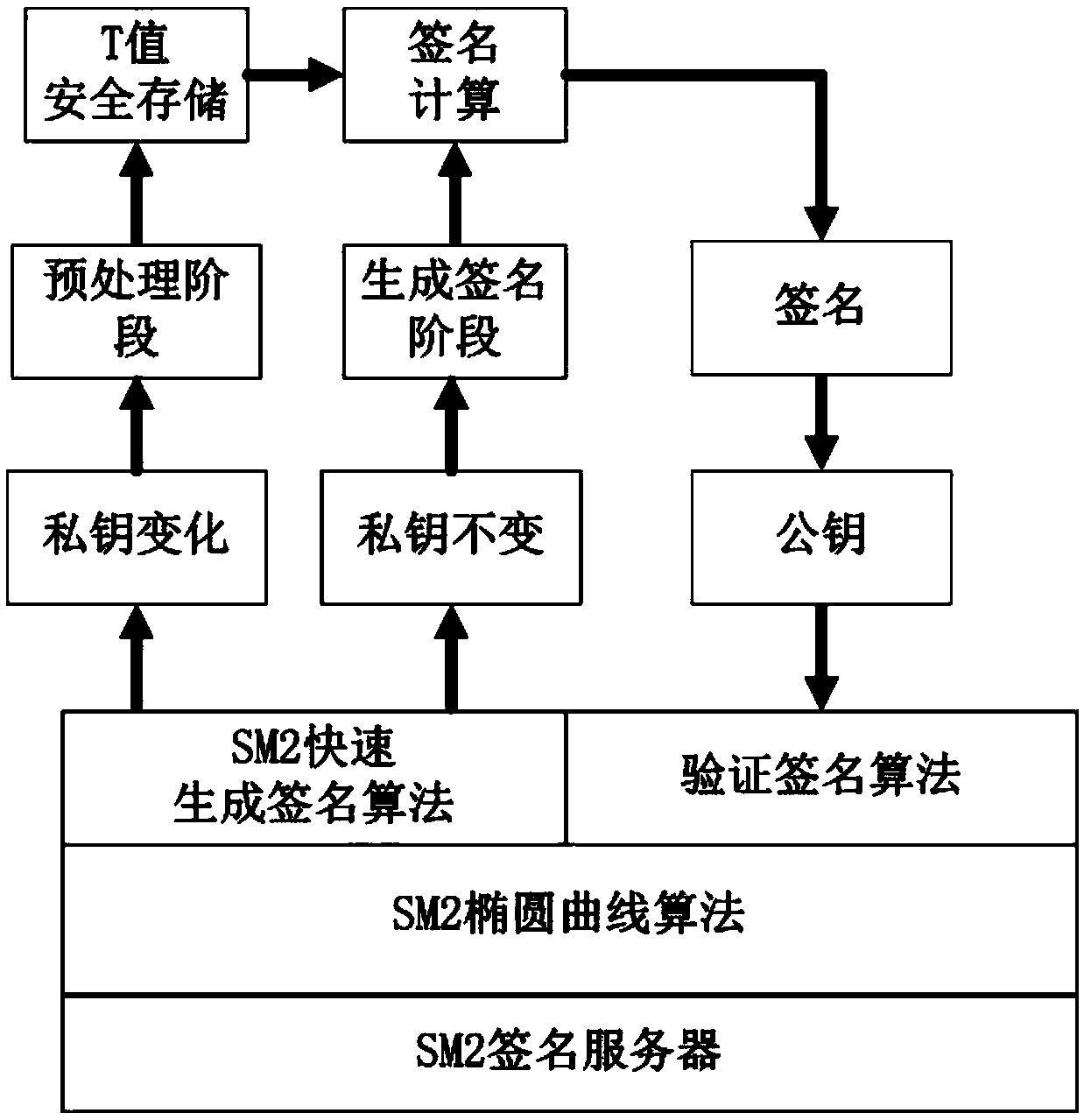
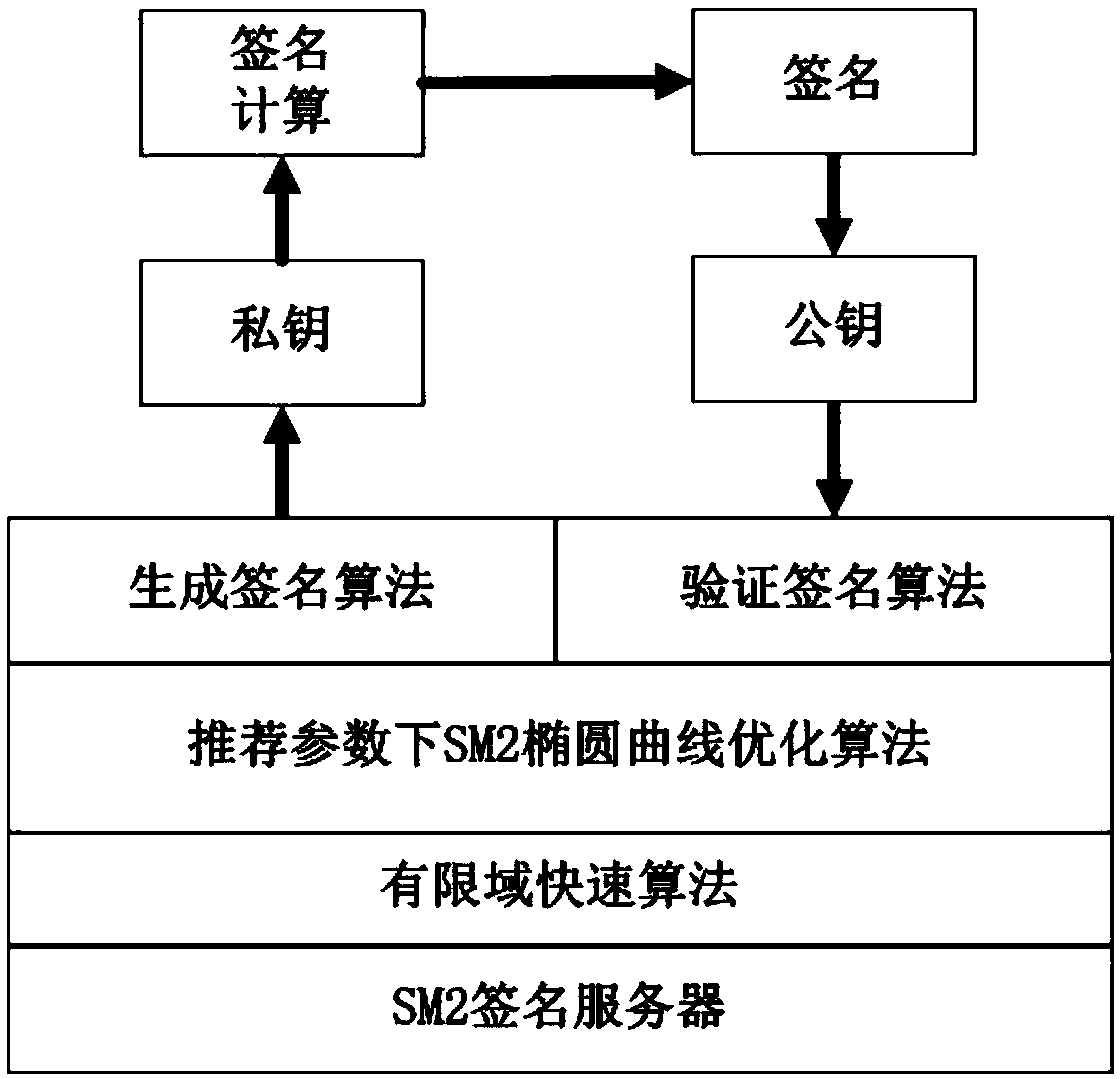
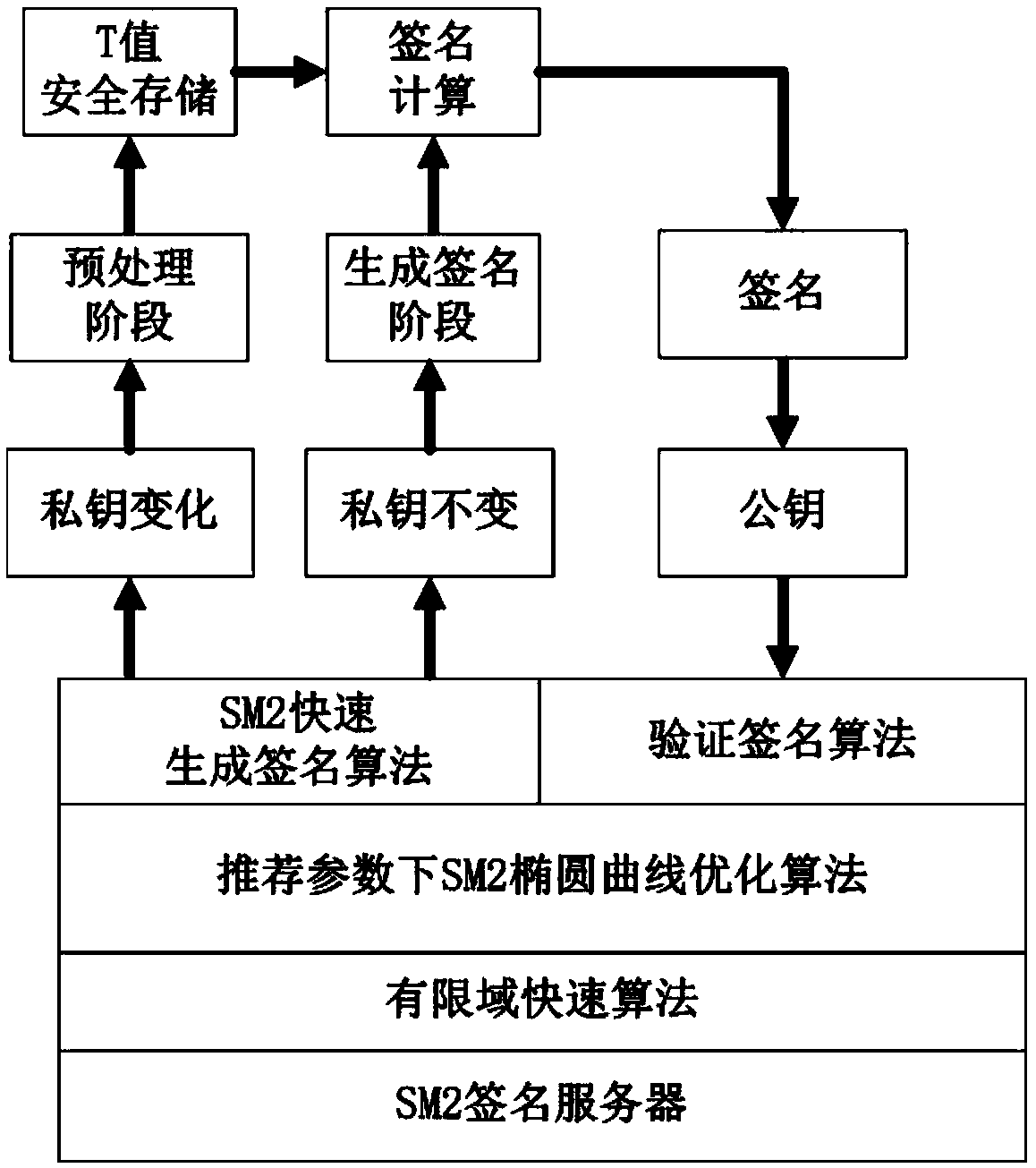
Digital signature quick generation method of SM2 public key cryptography
ActiveCN109660351AHigh speedCalculation speedPublic key for secure communicationUser identity/authority verificationDigital Signature Algorithm256-bit
The invention discloses a digital signature quick generation method of SM2 public key cryptography. The method comprises a step of performing optimization based on a SM2 signature generation algorithmin GM / T 0003.2-2012 SM2 elliptic curve public key cryptography standard on a SM2 signature server platform, and the method is a quick computation method of the SM2 signature generation algorithm, thesignature formation in the SM2 digital signature algorithm and the quick computation on the 256-bit prime number field in the SM2 recommendation parameter can be quickly realized. The optimization isperformed for the signature scheme and the finite field computation in the existing method, compared with the general optimization method on the elliptic curve, the method disclosed by the inventionbelongs to the specific optimization for the SM2 algorithm; on the SM2 signature server platform, especially a server platform using the recommended SM2 parameter and with long private key life cycle,the computation overhead is small, and the speed increasing can be effectively realized.
Owner:PEKING UNIV
Aerial image small target detection method based on feature fusion and up-sampling
ActiveCN111461217AEnhanced Representational CapabilitiesImprove featuresInternal combustion piston enginesCharacter and pattern recognitionFeature setImage resolution
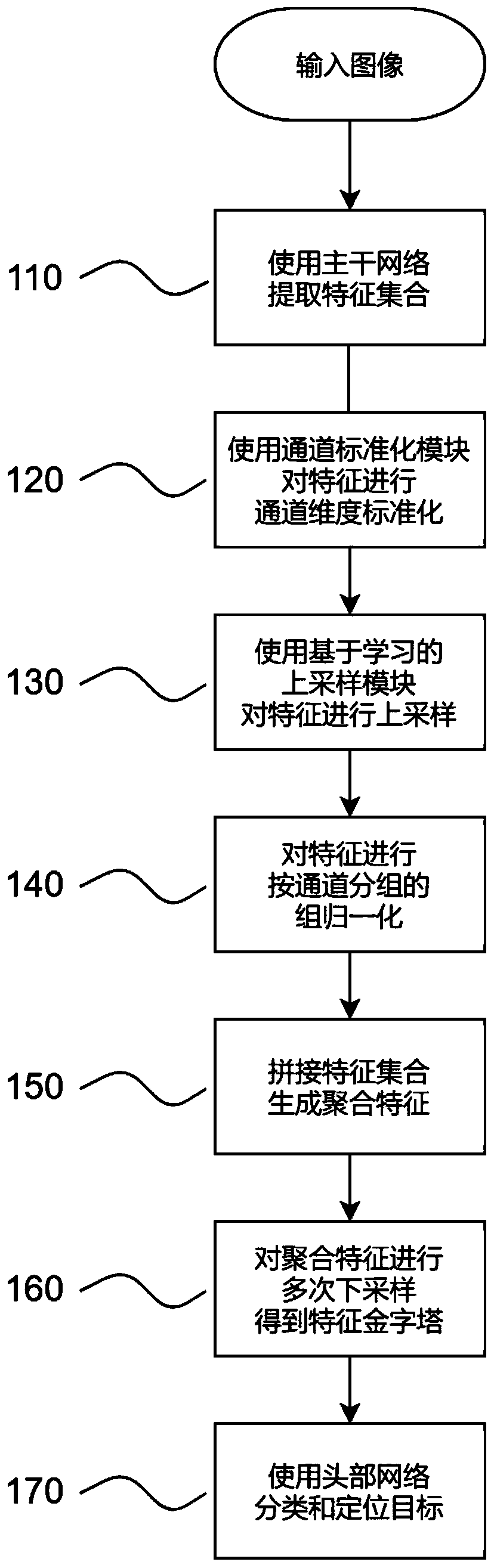
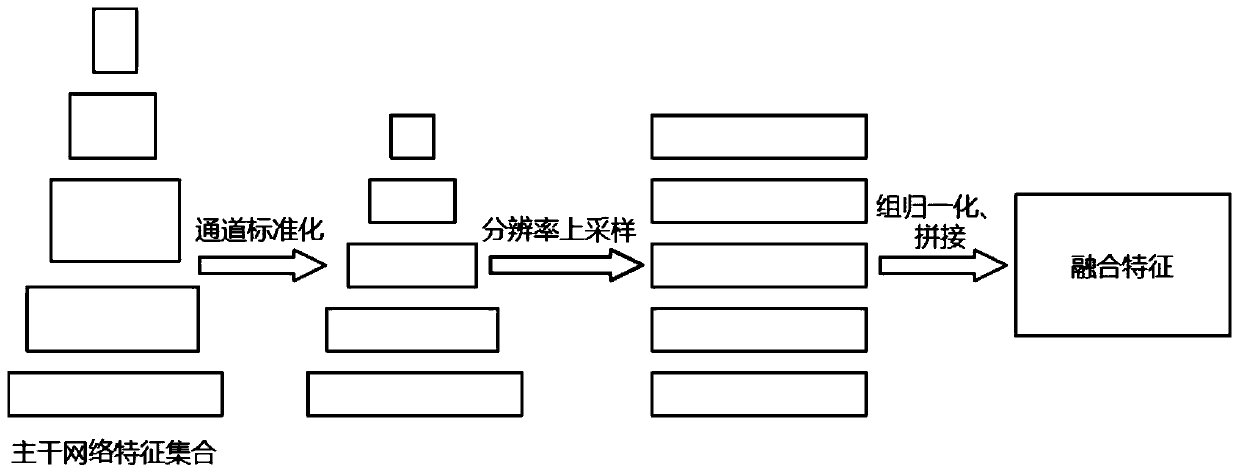
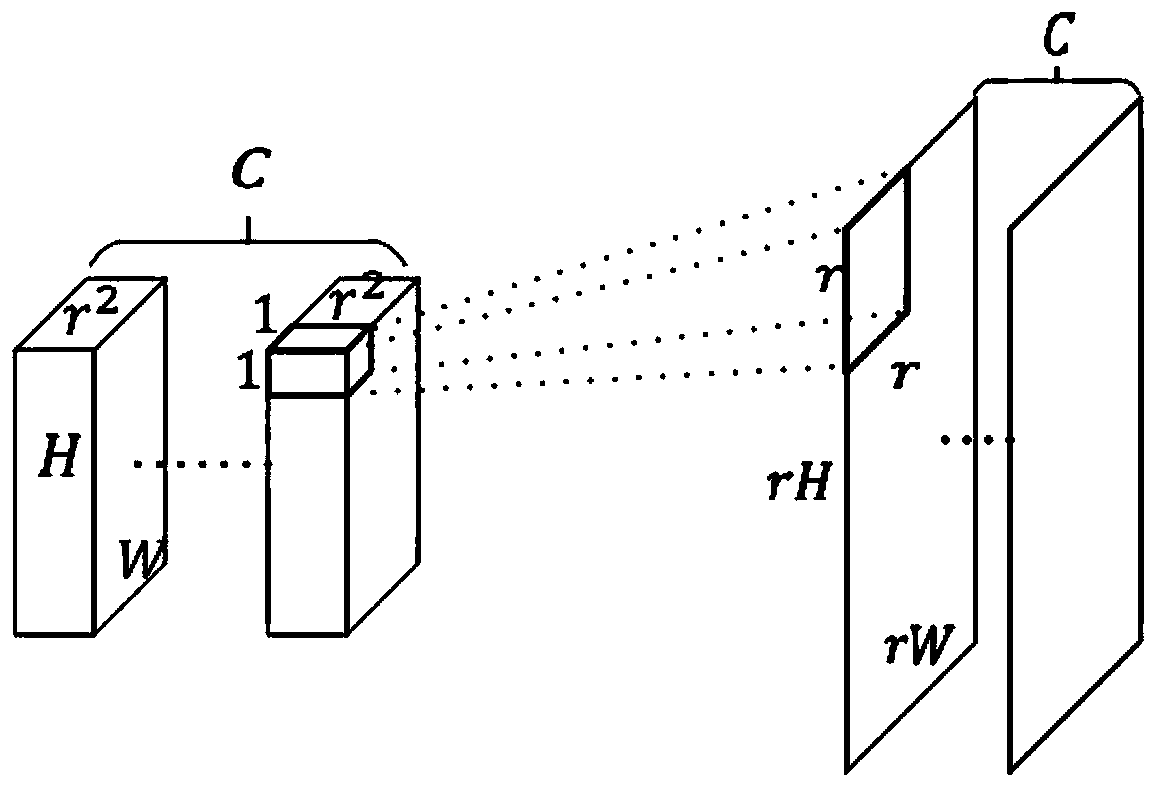
The invention discloses an aerial image small target detection method based on feature fusion and up-sampling. The method comprises the following steps: extracting a feature set of an input image by using a backbone network; constructing a channel standardization module, and standardizing the channel dimensions of the features; constructing an up-sampling layer based on learning, and performing resolution up-sampling on the features to obtain a feature set with uniform resolution; carrying out group normalization of grouping the features according to channels; splicing the feature sets to generate fusion features; performing down-sampling on the fusion features for multiple times, and constructing a feature pyramid for detection; classifying and locating targets using a head detection network. The invention relates to a feature fusion and feature up-sampling method for a target detection training and testing stage, which can significantly improve the detection precision of small targets in aerial images and only increase a small amount of calculation overhead.
Owner:SOUTH CHINA UNIV OF TECH
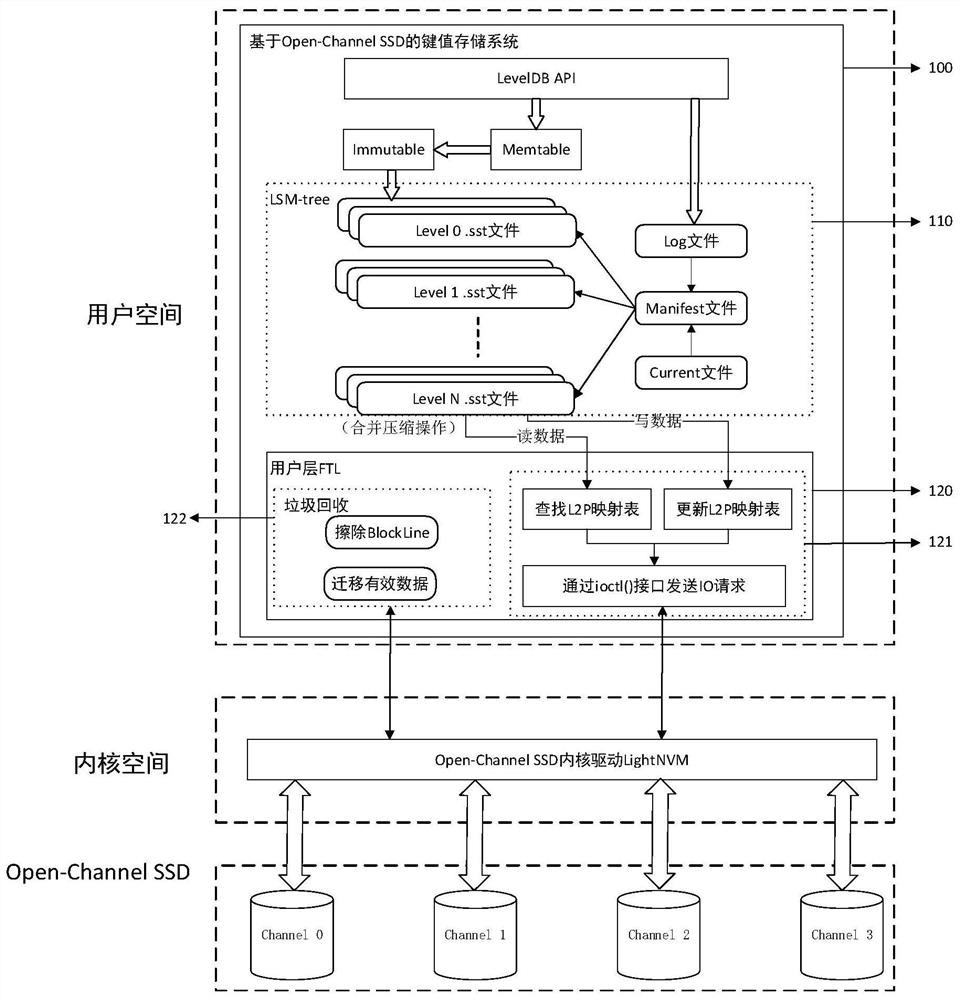
Writing and block granularity compressing and combining method and system of key value storage system based on OCSSD
ActiveCN112346666AReduce the proportionReduce the numberInput/output to record carriersWrite amplificationPERQ
The invention discloses a writing and block granularity compressing and combining method and system of a key value storage system based on an OCSSD, and belongs to the field of computer storage. Through selective compression and combination of data block granularity, read-in and write-back of non-overlapping data blocks are avoided, and the problem of read-write amplification in the LSM-tree compression and combination process can be reduced; the data blocks of the same file are uniformly distributed in all channels of the OCSSD, so that the multi-channel parallel characteristic of the OCSSD can be explicitly utilized, and the throughput of a key value storage system is improved; by directly managing a bottom storage medium at a user layer and bypassing intermediate software layers such asa file system, consumption of host resources is reduced, and semantic features of application software are conveniently transmitted. Generally speaking, the problem of read-write amplification of thekey value storage system based on the LSM-tree can be effectively reduced, semantic isolation between upper-layer application software and bottom-layer storage equipment is eliminated, and the throughput of the whole key value of the system to operation is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
Reverse wave beam control method for retrodirective discrete array
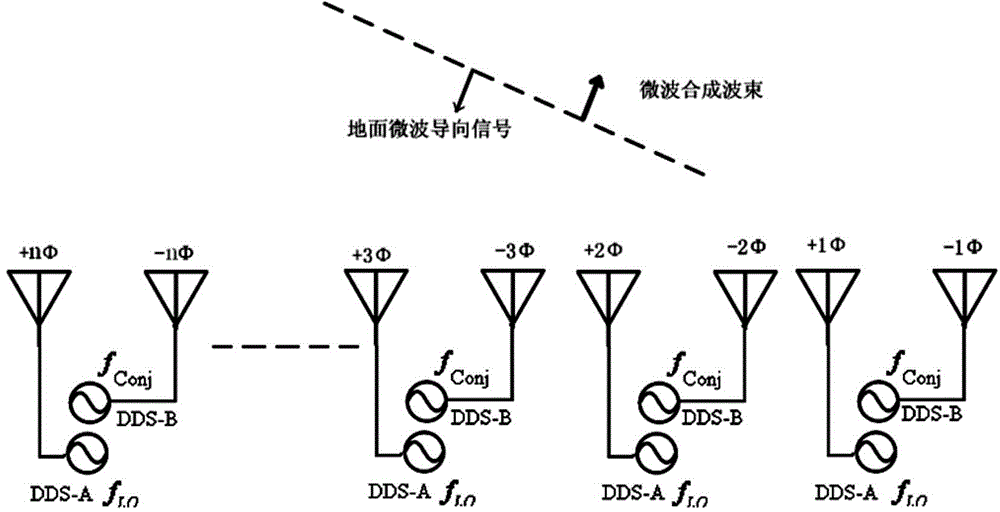
InactiveCN104485953ABeneficial technical effectImprove securityPulse automatic controlLocal oscillatorMicrowave signals
Provided is a reverse wave beam control method applied to a retrodirective discrete array. The method comprises the following steps: modulating guide information determined by a system to carrier frequency capable of real-time frequency adjusting to generate a reverse guide signal; sending the signal to the retrodirective array; carrying out demodulation on the received signal by the retrodirective array to obtain the guide information and calculating conjugate phase of the guide information; synthesizing a conjugate phase signal according to the conjugate phase obtained from calculation; and carrying out power amplification on the conjugate phase signal and emitting the signal through the retrodirective array. The method enables incoherent local oscillators which are independent mutually and are in a discrete state to generate the microwave signal which is coherent in phase and of which the phase is conjugate with that of the guide information, and realizes reverse wave beam control of the microwave beam backtracking along the incidence direction of the guide signal, thereby protecting system core frequency secret safety, avoiding malicious interference through frequency hopping and improving anti-interference capability of the system.
Owner:CHINA ACADEMY OF SPACE TECHNOLOGY
A multi-backup data holdings certification method in cloud storage environment
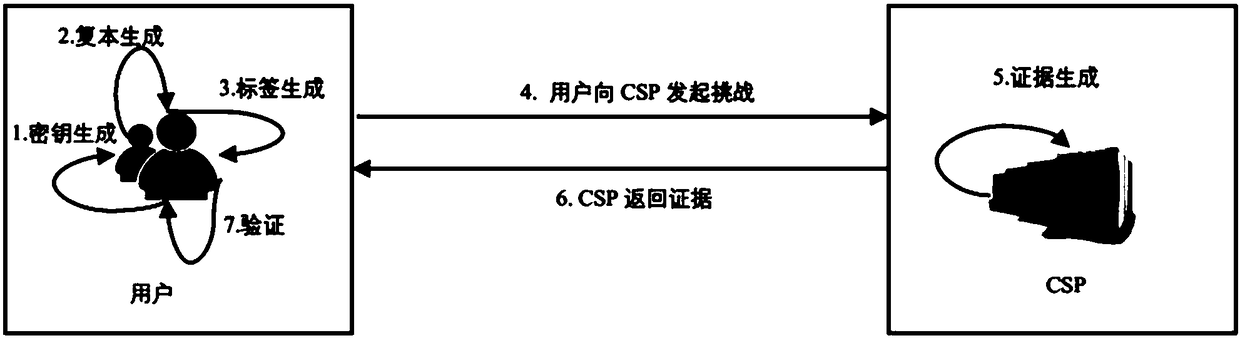
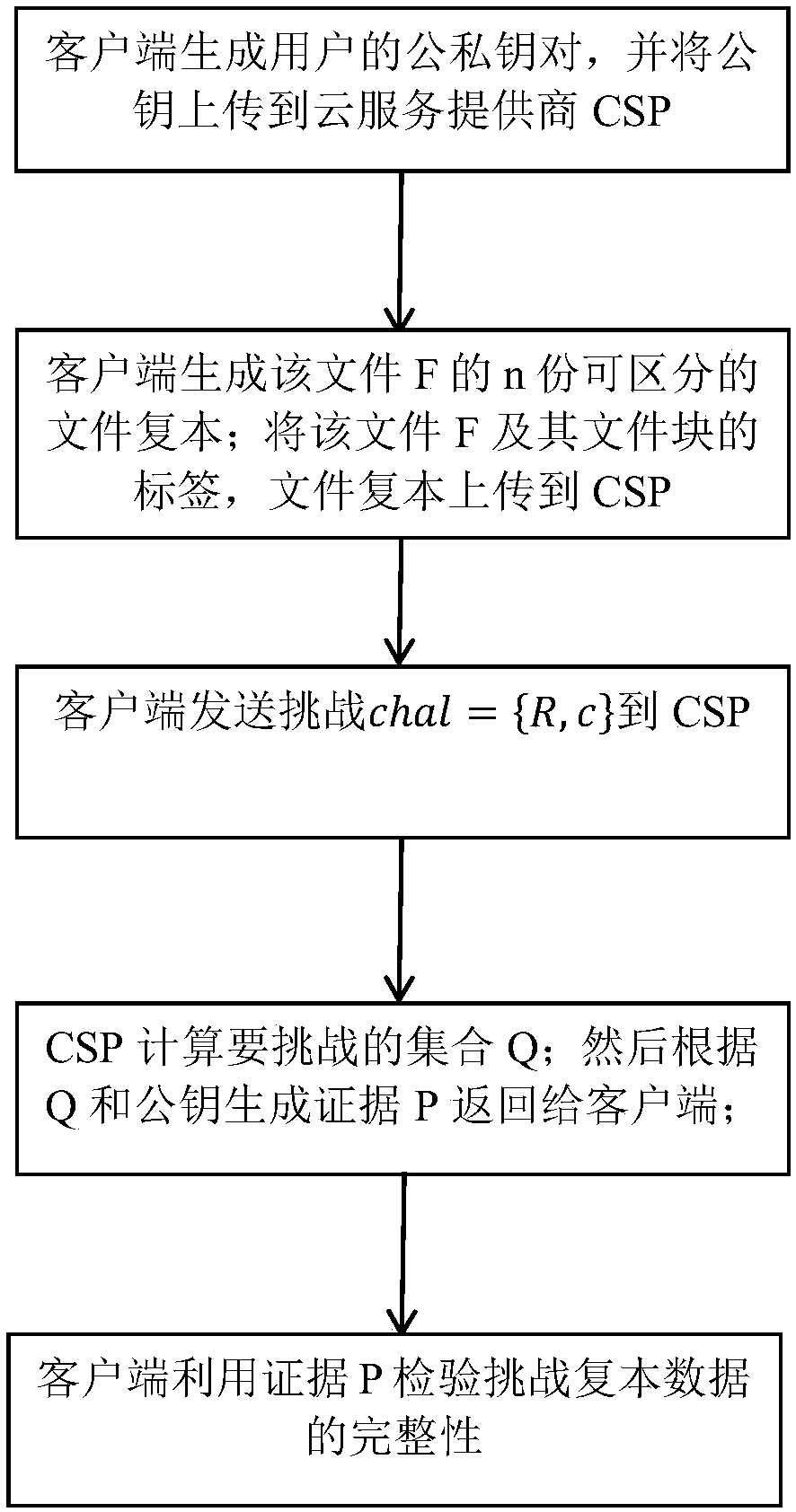
ActiveCN109104449AGet rid of heavy computing tasksReduce computational overheadTransmissionClient-sideCloud storage
The invention discloses a multi-backup data holding certification method under a cloud storage environment. The method comprises the following steps: 1) a client generates a public and private key pair of a user and uploads the public key pair to a cloud service provider CSP; 2) the client generates n distinguishable copies of the file F; then dividing the file F into m file blocks and generatinglabels of each file block, dividing each file copy into m file blocks, and uploading the labels of the file F and its m file blocks and the file copies to the CSP; 3) the client sends a challenge to the CSP; 4) according to the received challenge, CSP calculates the set Q to be challenged by the user through the public key; and then generating evidence P according to the set Q and the public key and returning the evidence P to the client; 5) the client end adopts the same way to generate the set Q, and then utilizes the evidence P to verify and challenge the integrity of the replica data. Theverification mode of the invention is flexible, and has positive significance to the replica positioning.
Owner:PEKING UNIV
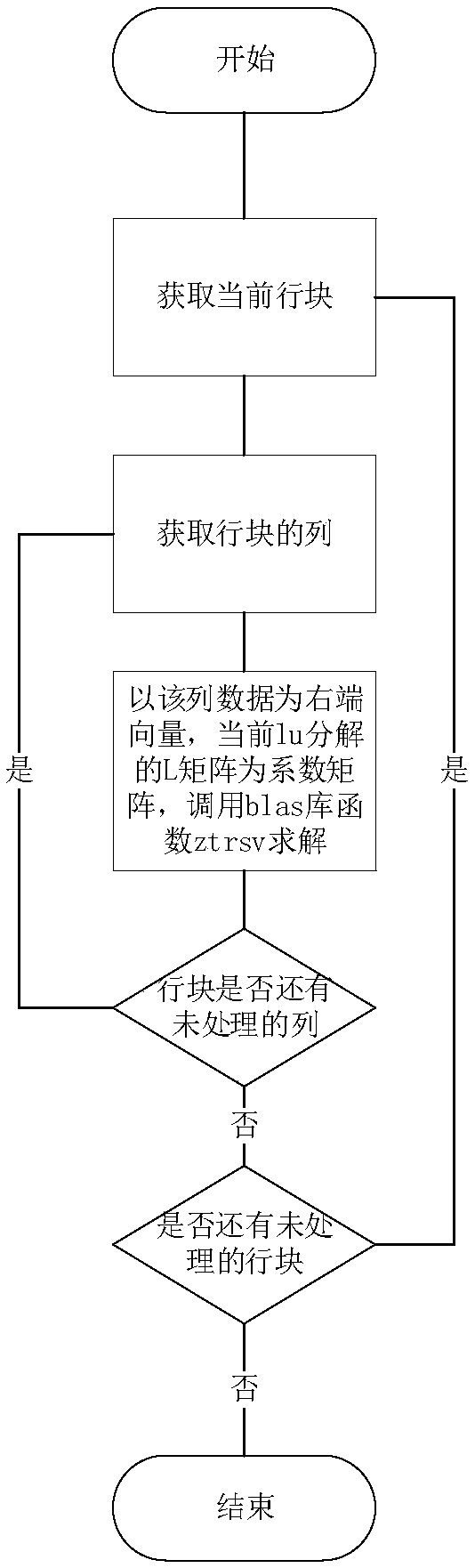
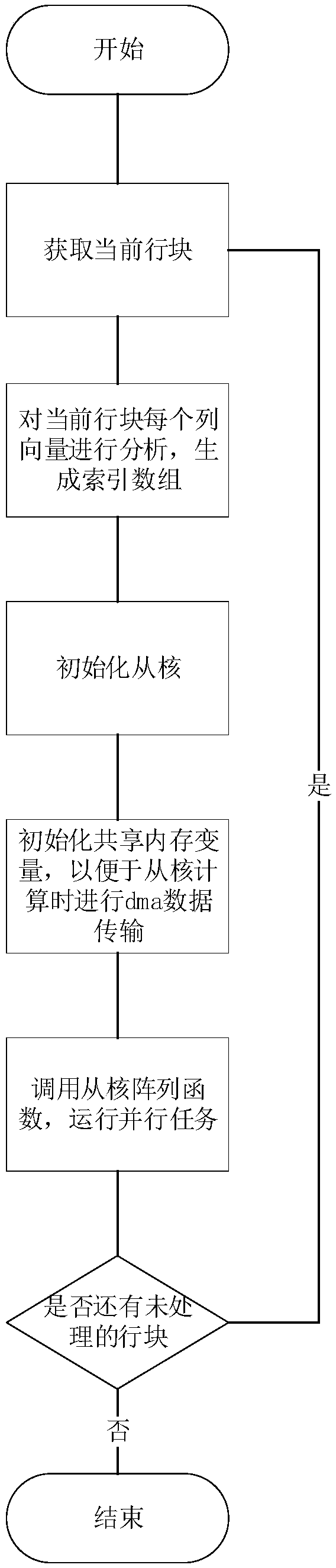
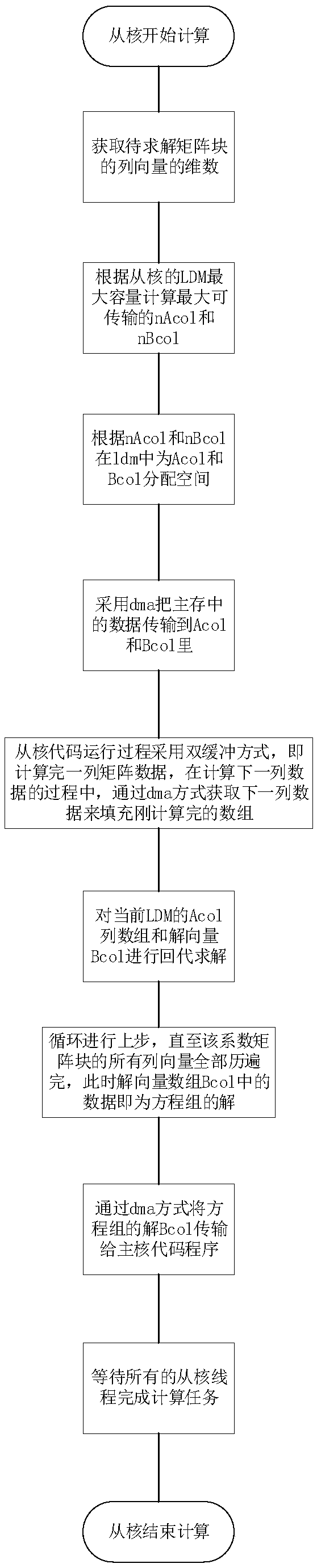
Heterogeneous parallel computing method for row updating of sparse matrix LU factorization
ActiveCN109145255AAvoid conflicts and dependenciesIncrease computational overheadComplex mathematical operationsIdentity matrixLU decomposition
The invention relates to a heterogeneous parallel computing method for updating sparse matrix LU decomposition rows. Based on the superlu algorithm, combined with the master-slave heterogeneity of Taihu Lake Light, the superlu solver transfers the large-scale computing task to the slave kernel in the process of matrix decomposition and row updating, and utilizes the efficient computing and data communication ability of the slave kernel to improve the computational ability of the super-large-scale sparse matrix and the overall performance of the solution. The invention divides tasks according to the data of the matrix, Firstly, a matrix space is created for each slave kernel, and each slave kernel is responsible for solving several matrix rows. In the process of solving the linear equationsof the lower triangular identity matrix type, each row of data is independent of each other, avoiding the conflict and dependence of the solution space, and smoothly realizing the solution of the equations.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Multi-factor-based industrial Internet of Things session key negotiation method
PendingCN114070559AGuaranteed anonymityGuaranteed unlinkabilityKey distribution for secure communicationPublic key for secure communicationHash functionEngineering
The invention discloses a multi-factor-based industrial Internet of Things session key negotiation method which comprises the following steps that: a user stores personal information by using a smart card, communicates with intelligent equipment deployed in the industrial Internet of Things and Internet of Things nodes by connecting a mobile phone or other intelligent terminal equipment, acquires equipment state information in real time, and performs remote management and monitoring on the equipment. The method is based on the environment of the semi-trusted management center and more accords with reality, meanwhile, the pseudonym of the user is generated by the user and the server together, and the pseudonym of the user can be updated in real time after each key negotiation process, so that it is ensured that identity information of the user cannot be leaked, anonymity of the user is ensured, the non-linkability and the non-traceability are ensured, and the safety is improved. A key pre-distribution method is adopted, and based on a multi-factor authentication mode, namely biological characteristics, passwords and intelligent cards, main encryption operation is bit operation and a hash function, so that the calculation overhead and the communication overhead of a key negotiation scheme are reduced.
Owner:ANHUI UNIVERSITY
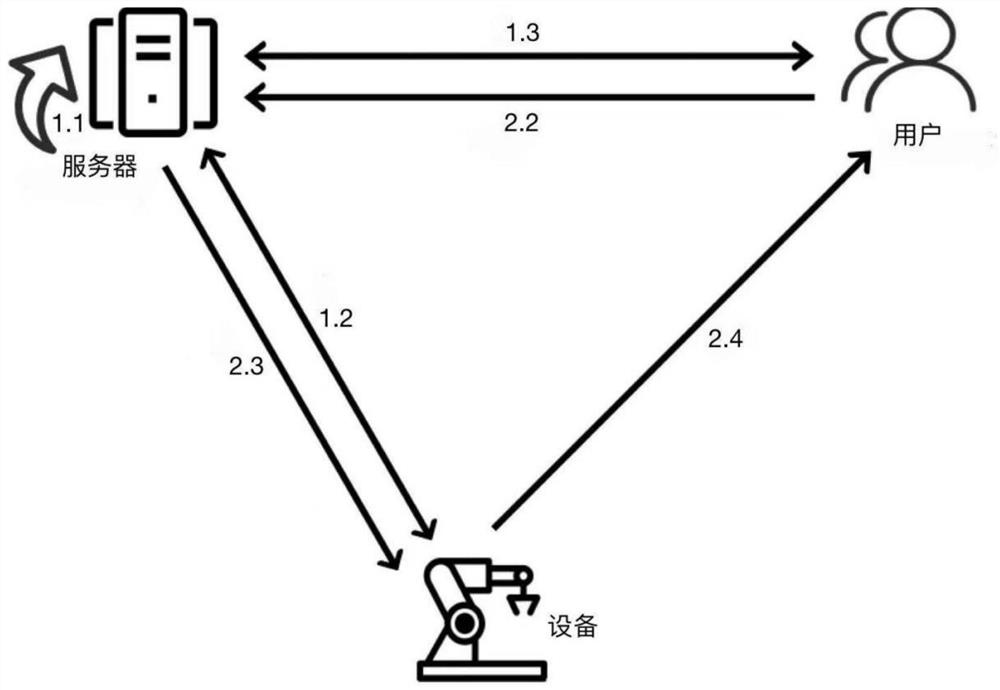
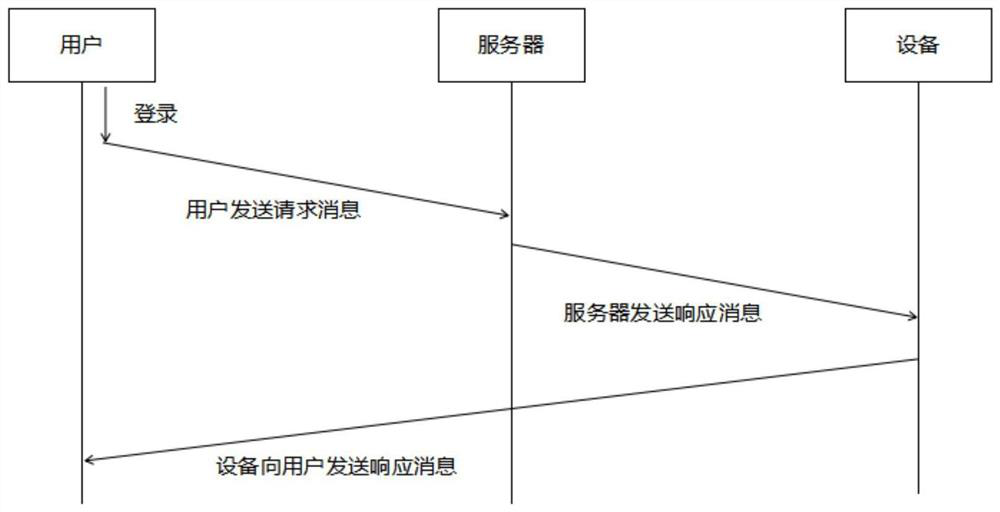
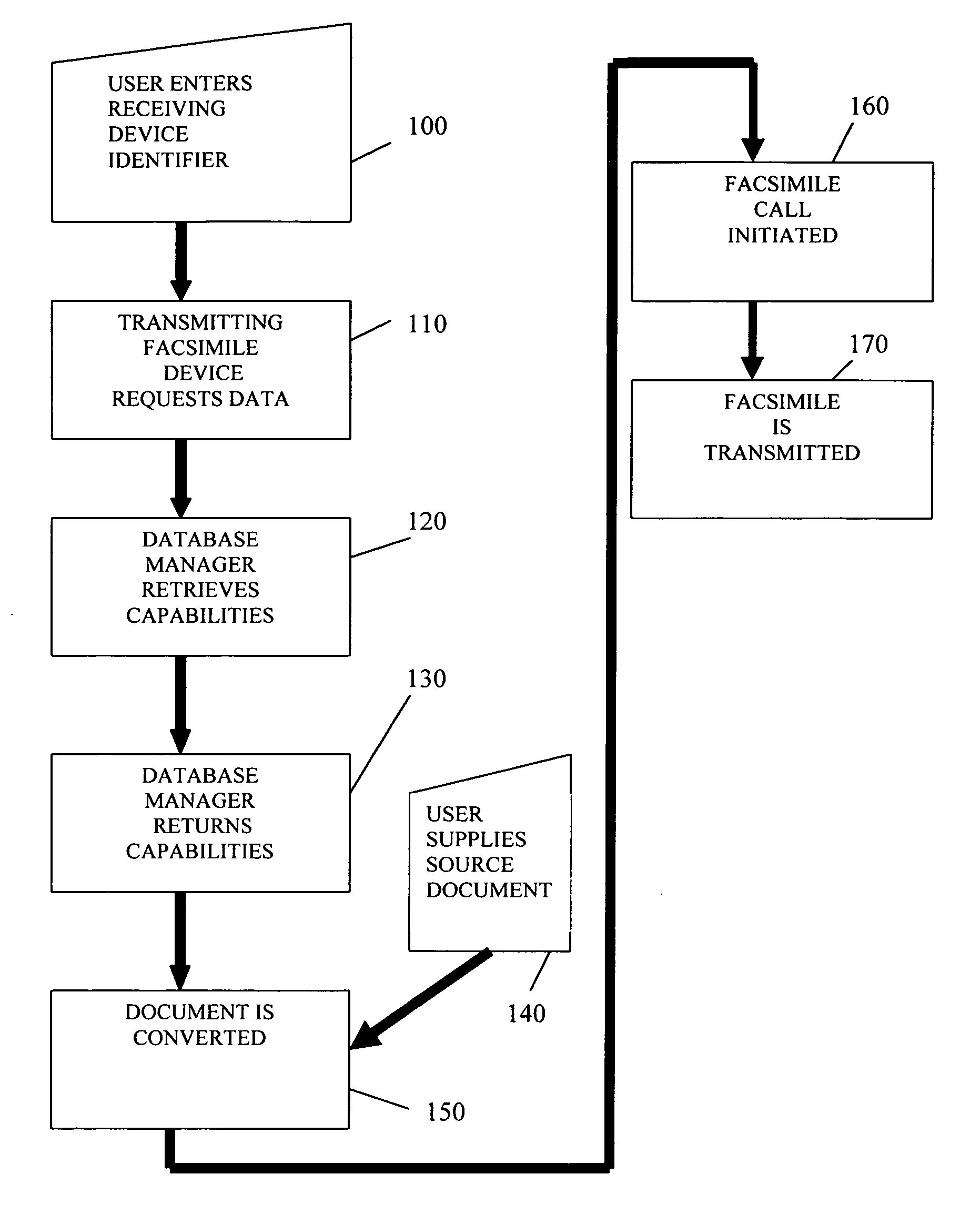
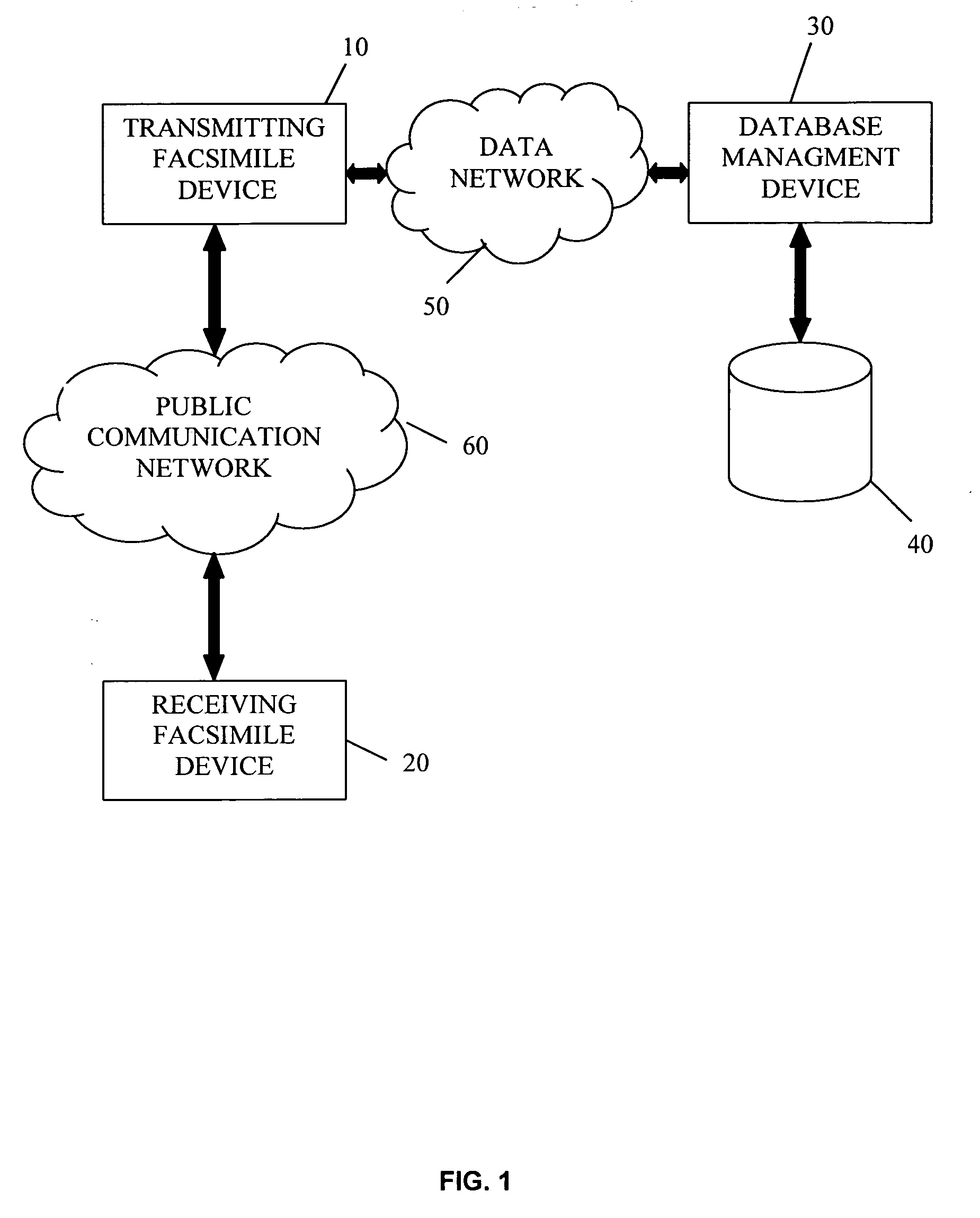
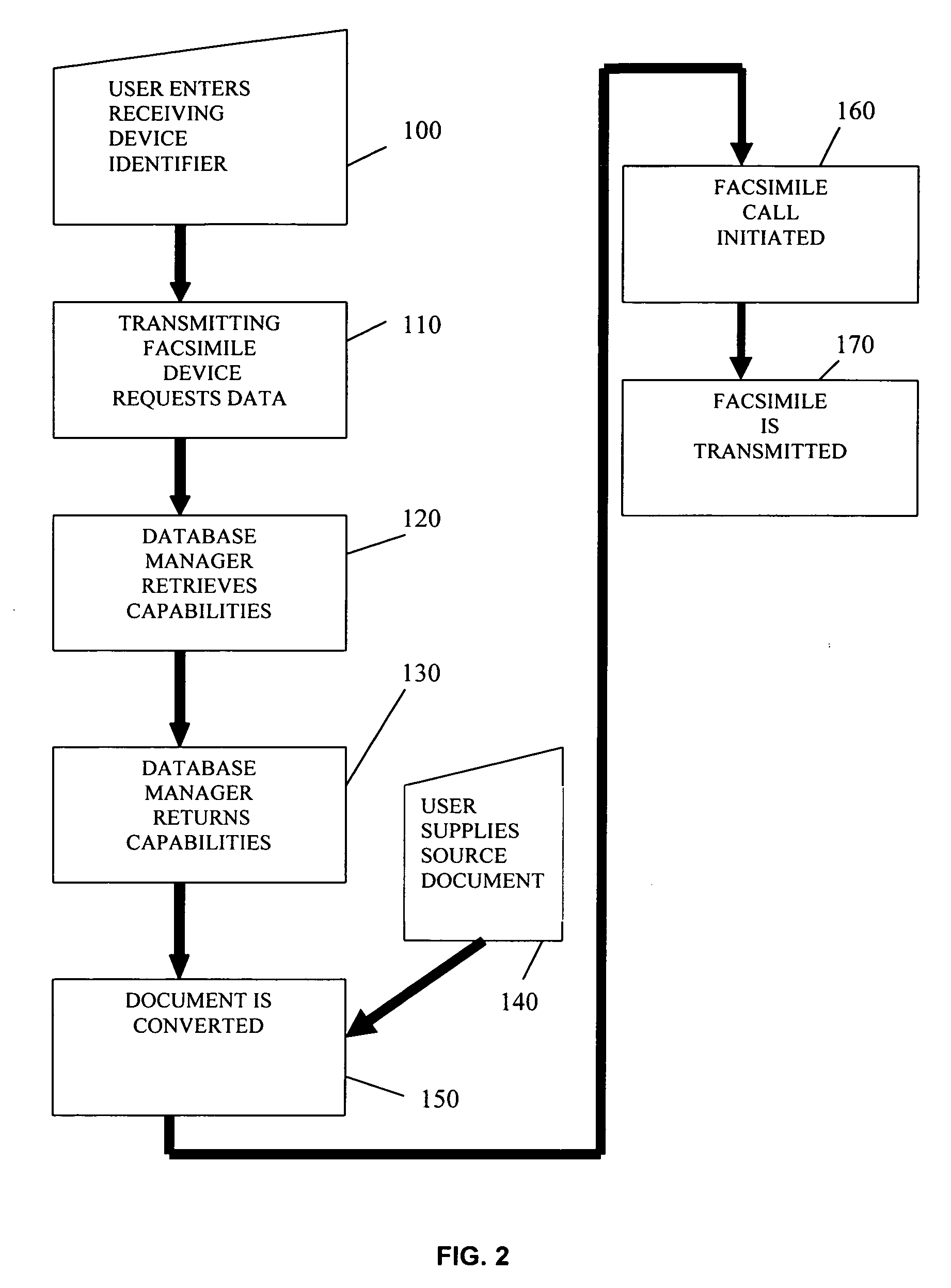
Systems and methods for determining user preferences and/or facsimile device capabilities before call initiation
InactiveUS20060268364A1Guaranteed normal transmissionIncrease computational overheadTransmissionPictoral communicationFacsimile transmissionDocumentation
Disclosed herein are systems and methods that can improve the quality and efficiency of document facsimile transmission. Quality can be improved by allowing a facsimile document sender to view the document as it will be transmitted to a receiving facsimile device. Efficiency of facsimile transmission is improved by providing systems and methods that allow the transmitting facsimile device to determine the capabilities and / or preferences associated with the receiving facsimile device and convert the facsimile document to match those capabilities and / or preferences before a call is placed.
Owner:OLISZEWSKI MICHAEL A +2
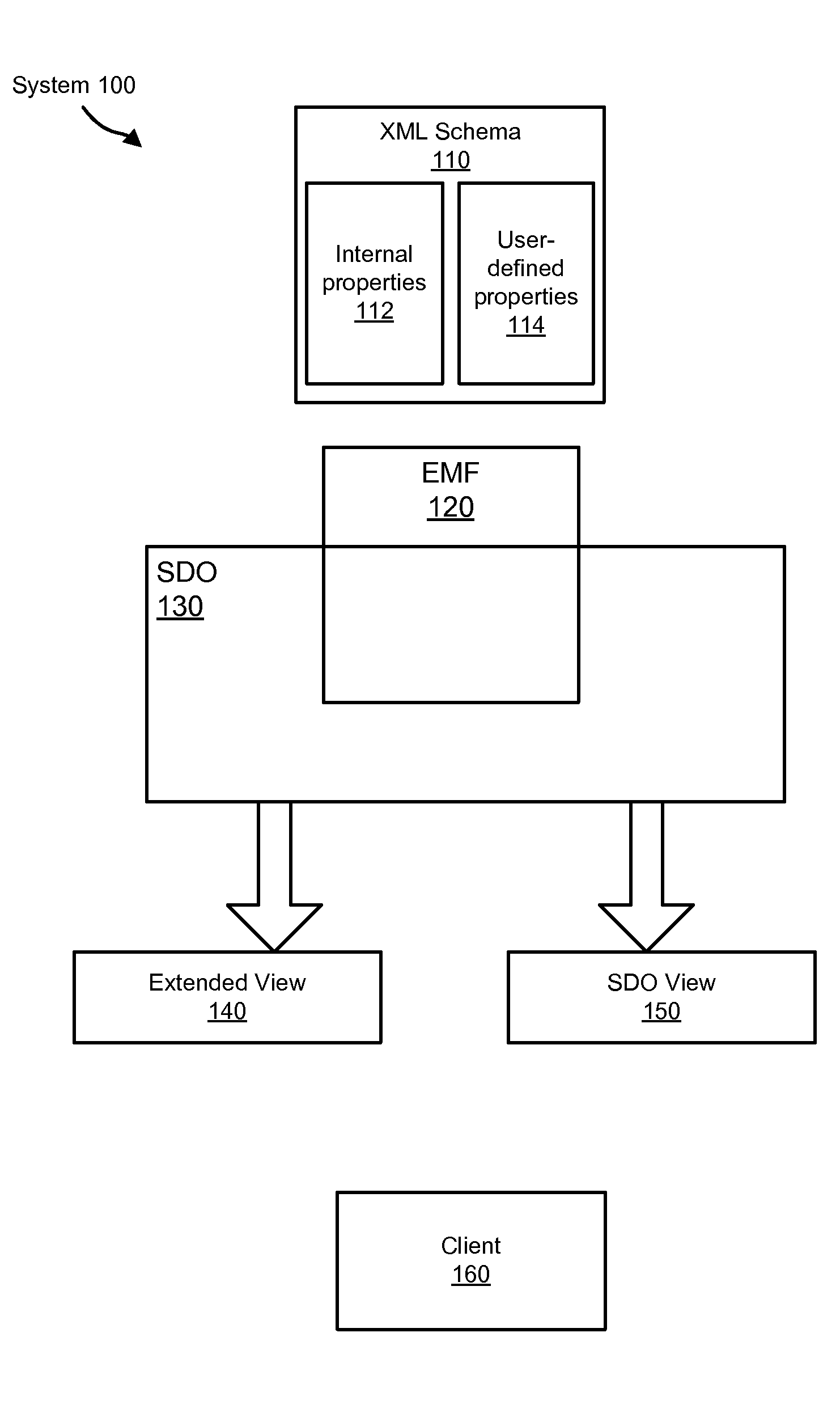
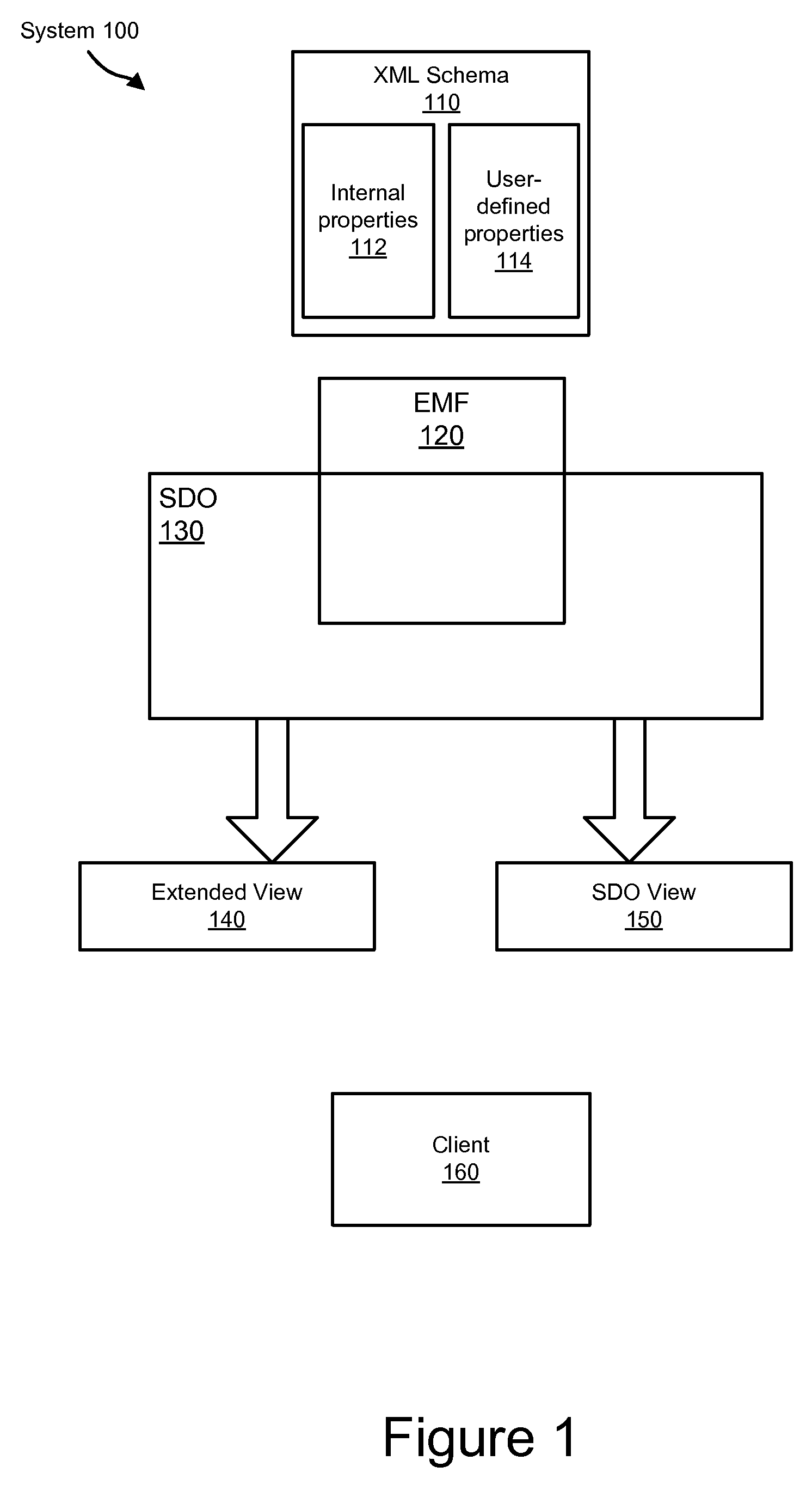
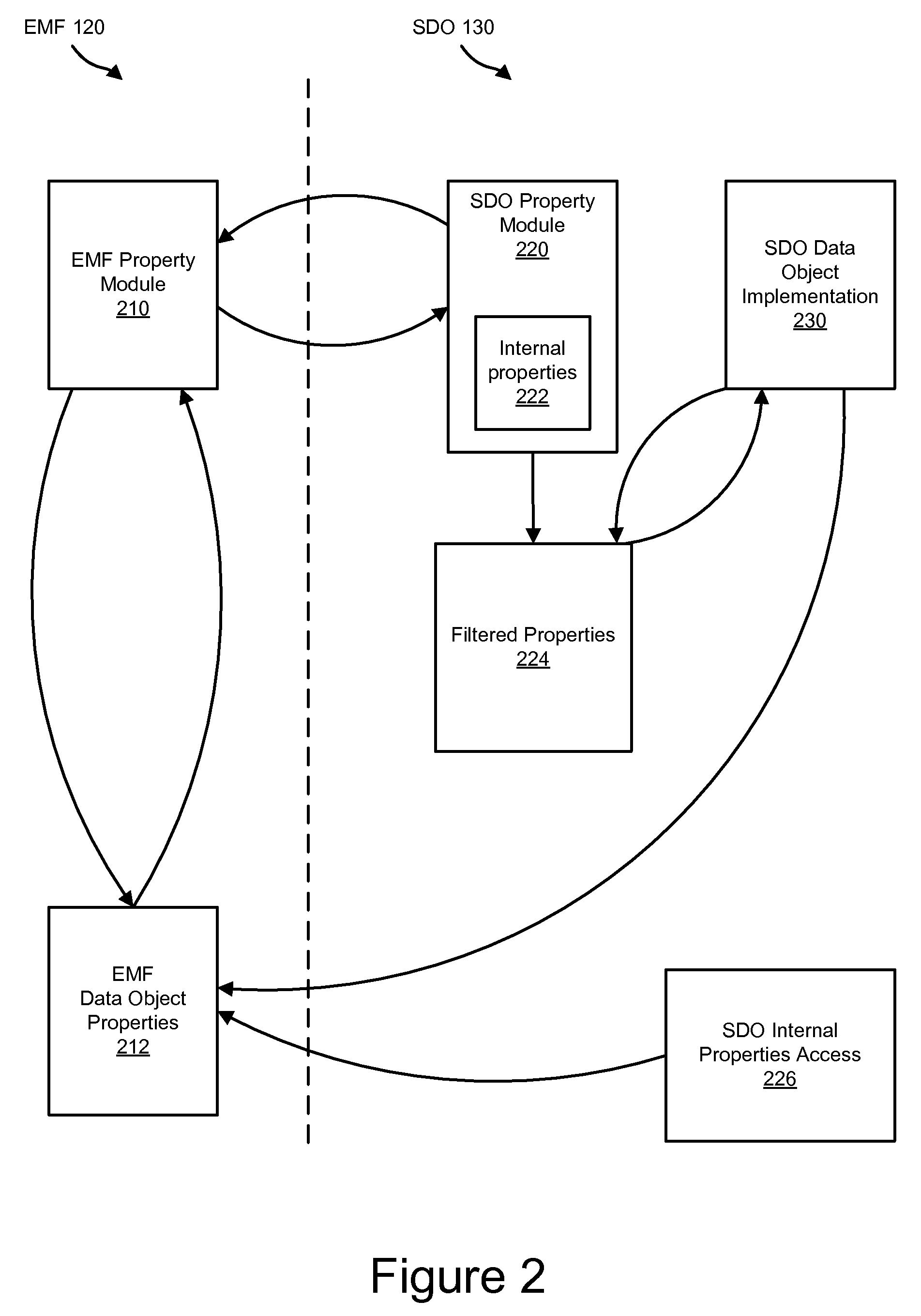
Apparatus, system, and method for hiding advanced XML schema properties in EMF objects
InactiveUS8434055B2Simplify the viewing processIncrease computational overheadSoftware designSpecific program execution arrangementsXML schemaClient-side
An apparatus, system, and method for hiding advanced XML schema properties in EMF objects. XML Schema may comprise both user-defined properties and internal properties related to the structural features of the schema. The present invention hides the internal properties from clients while still keeping them available such that a complete XML Schema model can be generated, but without exposing a client to the non-intuitive internal properties. An SDO implementation leverages EMF implementation artifacts to present a client with an SDO API exposing user-defined properties and metadata describing user-defined properties. The SDO implementation further provides an extended API through which a client may access internal properties and metadata describing the internal properties. The invention further accounts for both dynamic SDO objects and static SDO objects.
Owner:INT BUSINESS MASCH CORP
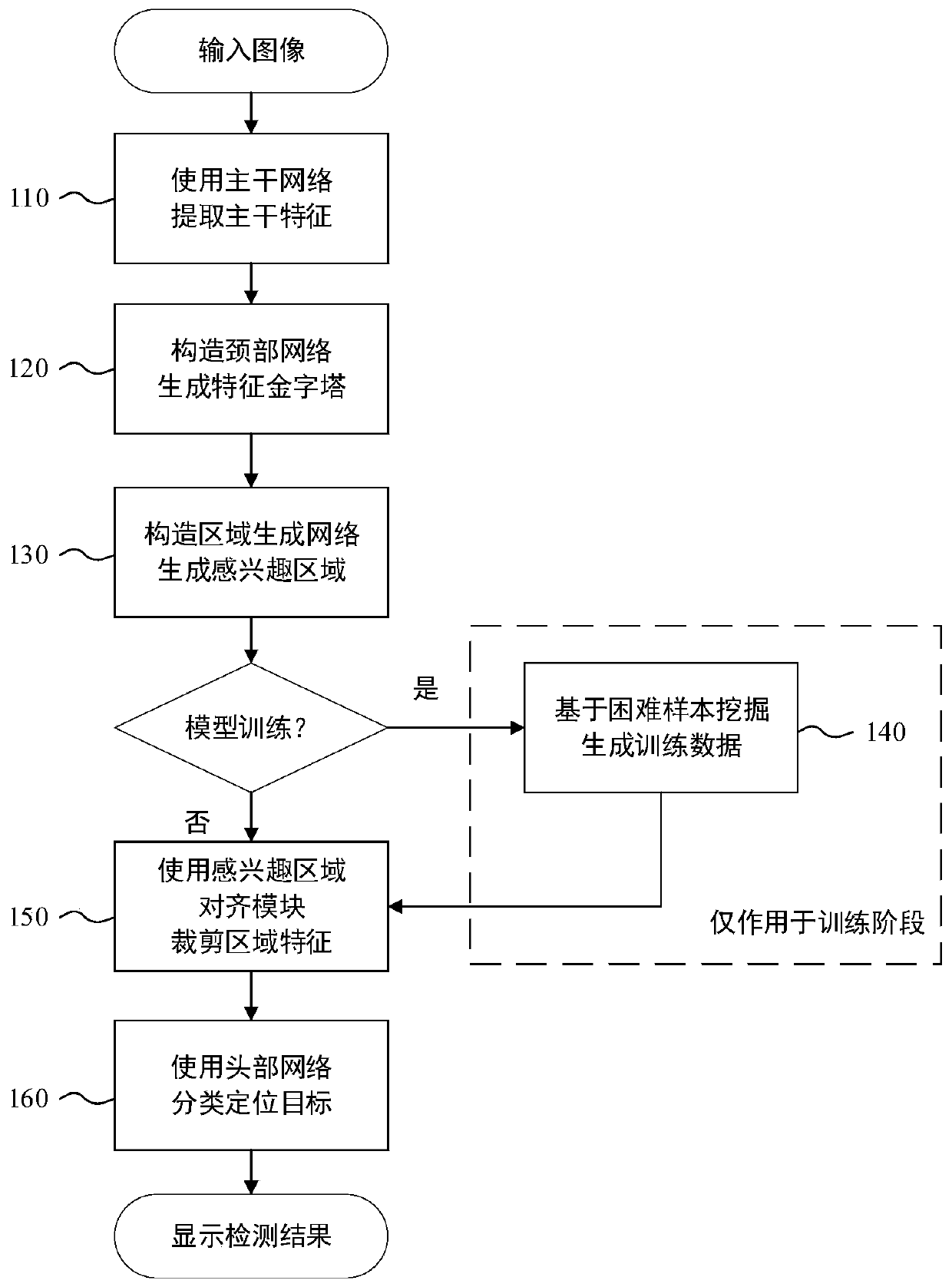
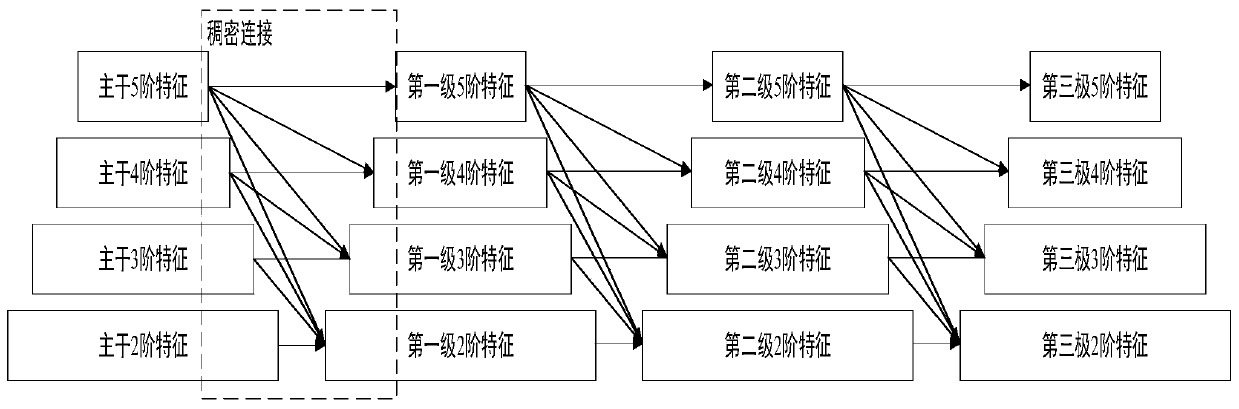
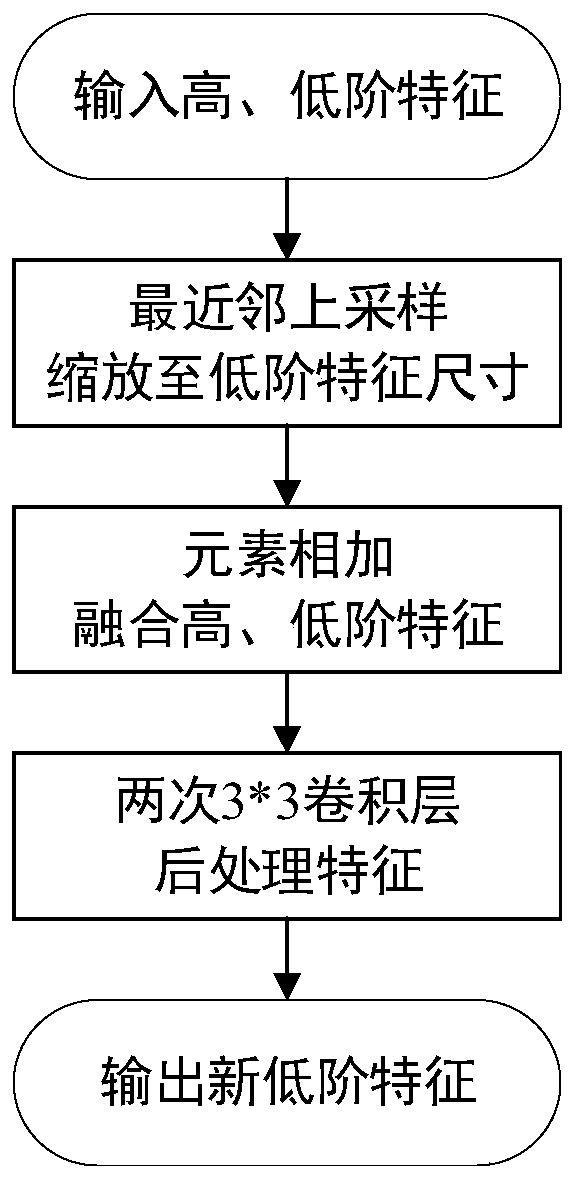
Small target detection-oriented network and difficult sample mining method
PendingCN110929649AImprove detection accuracyIncrease computational overheadScene recognitionNeural architecturesNetwork modelRegion of interest
The invention discloses a small target detection-oriented network and difficult sample mining method. The method comprises the following steps: step 1, extracting trunk features of a current image byusing a trunk network; 2, constructing a neck network, and generating a feature pyramid; 3, constructing a region generation network model, and generating a region of interest; 4, generating trainingdata based on difficult sample mining; 5, cutting the region features by using a region-of-interest alignment module; and step 6, classifying and positioning a target by using a head network. According to the method, the small target detection precision can be remarkably improved, and only little calculation overhead is increased.
Owner:SOUTH CHINA UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com