Digital signature quick generation method of SM2 public key cryptography
A technology of public key cryptography and digital signature, which is applied in the direction of digital transmission system, public key of secure communication, user identity/authority verification, etc. It can solve the problems of SM2 optimization acceleration, limited degree of optimization, and inconspicuous speed improvement, etc. Achieve the effect of improving calculation speed and speeding up
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
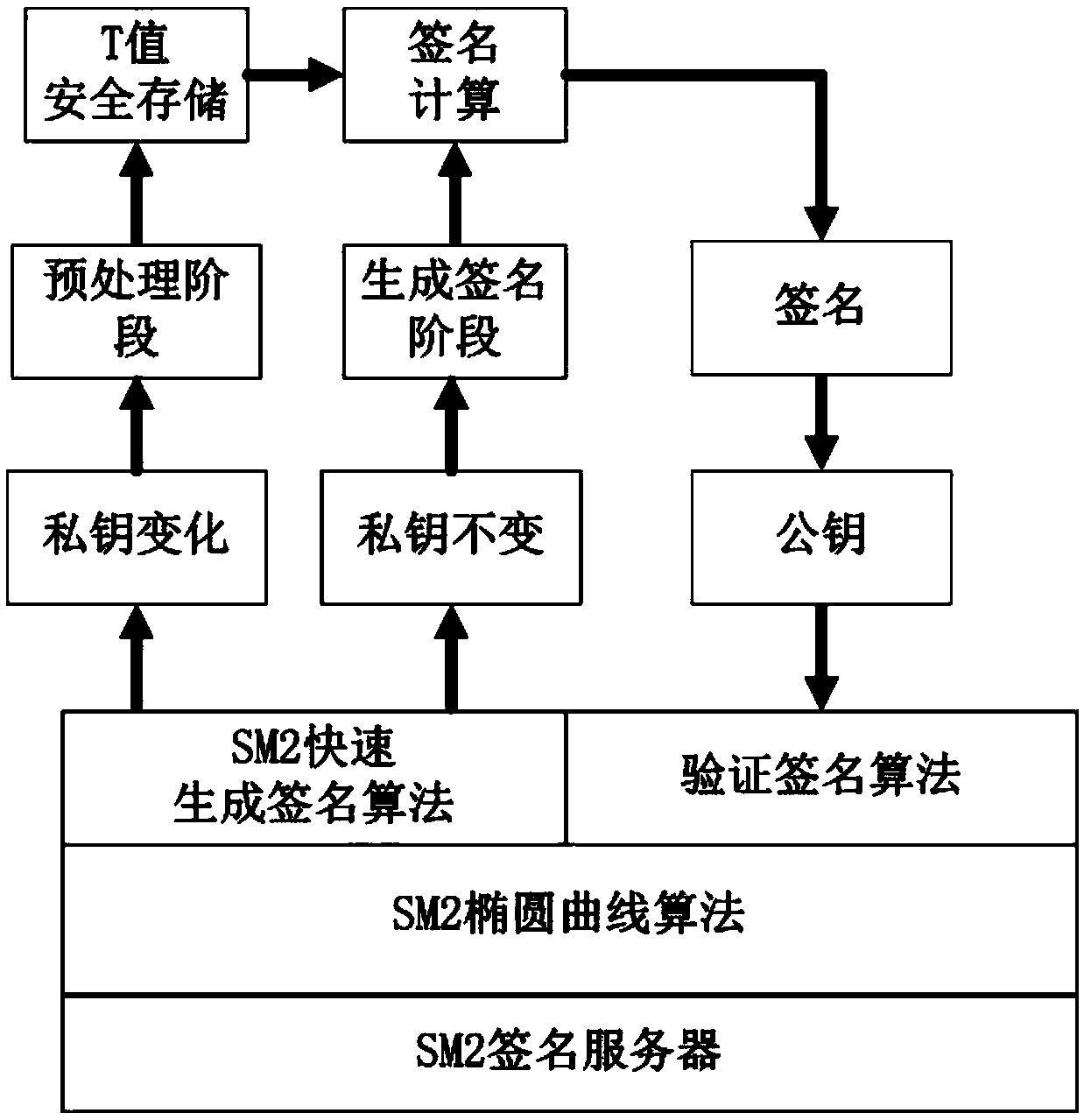
[0185] Example 1: Realize the two-stage SM2 algorithm on the SM2 signature server with a longer key life cycle
[0186] On a typical SM2 signature server platform (such as an SM2 signature server supporting ARM or X86 instruction set), if the signed private key has a long life cycle, such as several months or even years, then the two-stage SM2 algorithm can be used. Application frameworks such as figure 1 :
[0187] 1) When running for the first time or when the secret key expires, the server obtains or generates a secret key that needs to be used, and specifies the validity period of a secret key. The variable t is obtained in the preprocessing stage and stored safely (for example, a password is required to read USB shield).
[0188] 2) When the server needs to sign, if the secret key has expired, destroy the variable t, and run to step 1), otherwise, run to step 3
[0189] 3) In the signature calculation stage, the variable t in the preprocessing stage is used to complete...
Embodiment 2
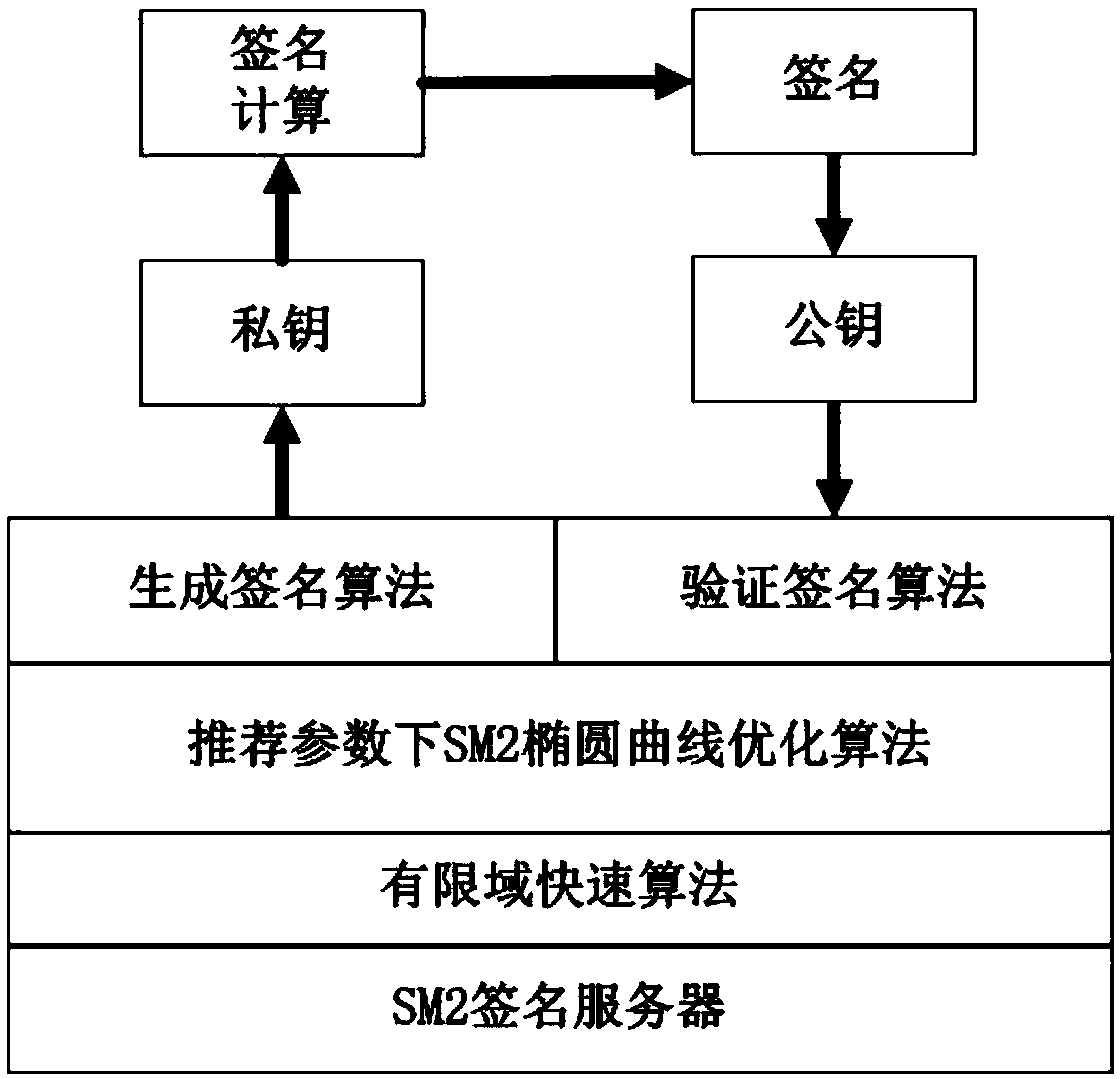
[0192] Embodiment 2: Optimizing the acceleration of elliptic curve calculations on the SM2 computing platform using recommended parameters
[0193] On a typical SM2 computing platform (such as an SM2 signature server that supports ARM or X86 instruction set), if the SM2 algorithm uses the recommended parameters, specifically, when SM2 performs elliptic curve calculations, the elliptic dotted line has a limited The domain is defined in F p (p=2 256 -2 224 -2 96 +2 64 -1), the multiplication and inversion on its finite field can be optimized and accelerated, thereby speeding up the operation on the elliptic curve. The application framework is as follows figure 2 Shown:
[0194] 1) When the server uses the recommended parameters, for the finite field F p (p=2 256 -2 224 -2 96 +2 64 -1), using the multiplication and inversion acceleration algorithm of the present invention.
[0195] 2) When performing operations such as addition and point multiplication on elliptic cur...
Embodiment 3
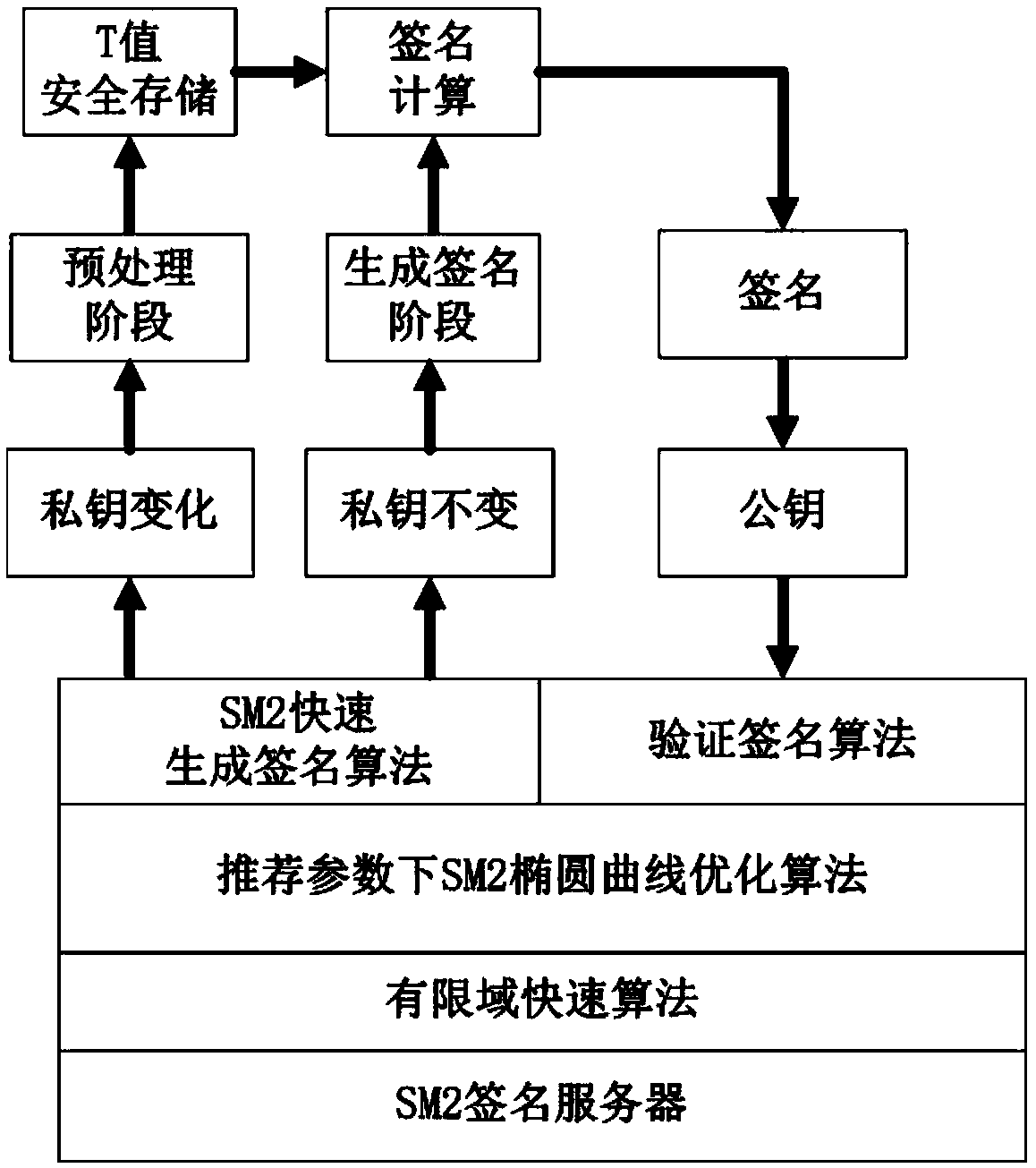
[0198] Example 3: SM2 signature server with recommended parameters and longer key period
[0199] On a typical SM2 signature server platform (such as an SM2 signature server that supports ARM or X86 instruction set), the signature private key has a long life cycle and uses standard recommended parameters. This is a very common situation and can be Integrate two-stage algorithm and finite field optimization algorithm to achieve higher speed, application framework such as image 3 :
[0200] 1) Use the two-stage SM2 algorithm to reduce the amount of computation. Specifically, in the case of no change in the key, this scheme reduces the one inversion and two multiplication calculations in the original scheme to one multiplication calculation.
[0201] 2) In the underlying finite field calculation, use the fast finite field multiplication and inversion calculation of this scheme to replace the original finite field multiplication and inversion calculation, thereby improving the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com