Inter-satellite networking authentication system and method suitable for double-layer satellite network
A dual-layer satellite network and inter-satellite networking technology, applied in the field of information security, can solve the problems of incompatibility with satellite network networking scenarios, denial of service, difficulty in satellite independence, independent trust establishment, and secure communication.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0089] In order to make the object, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
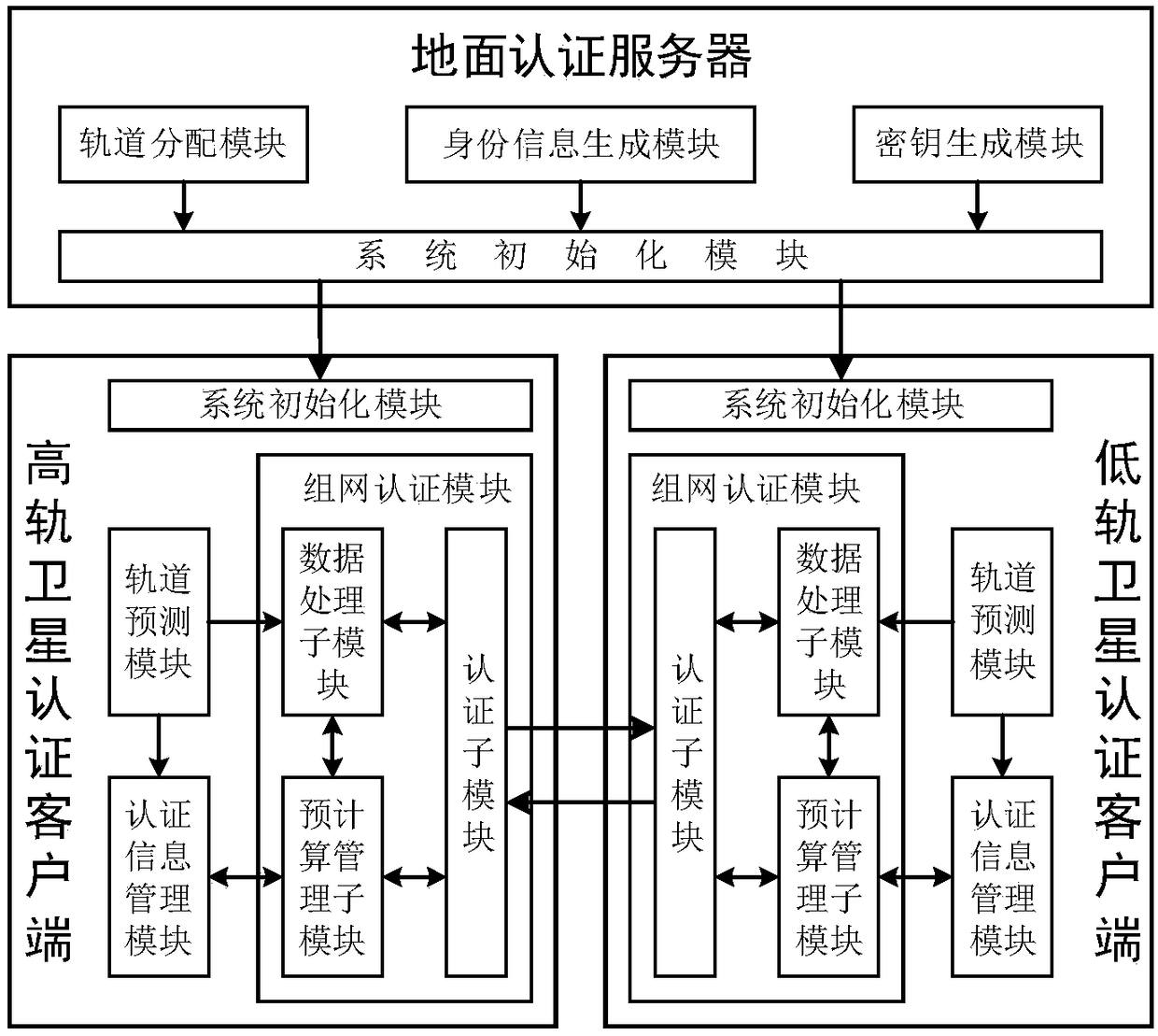
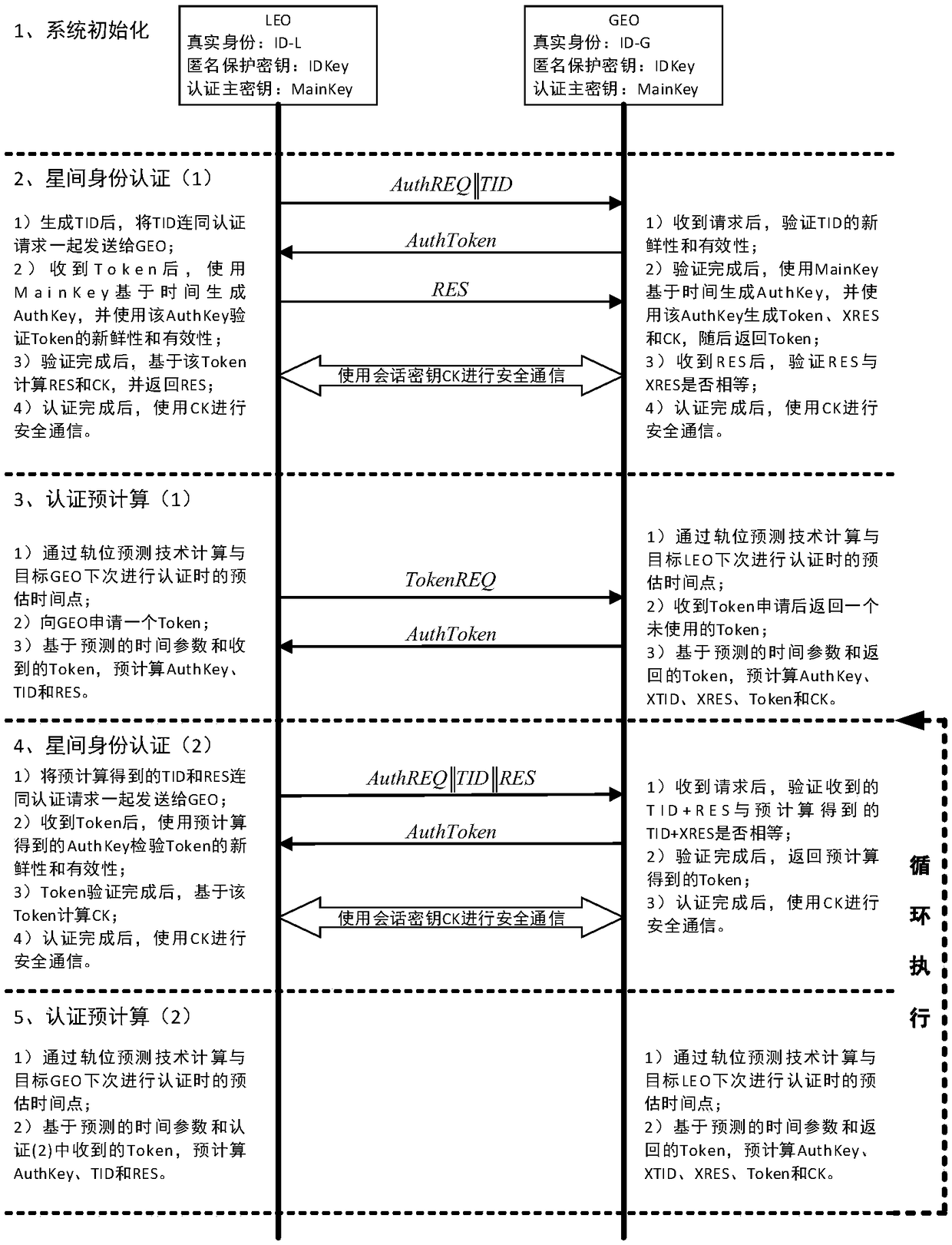
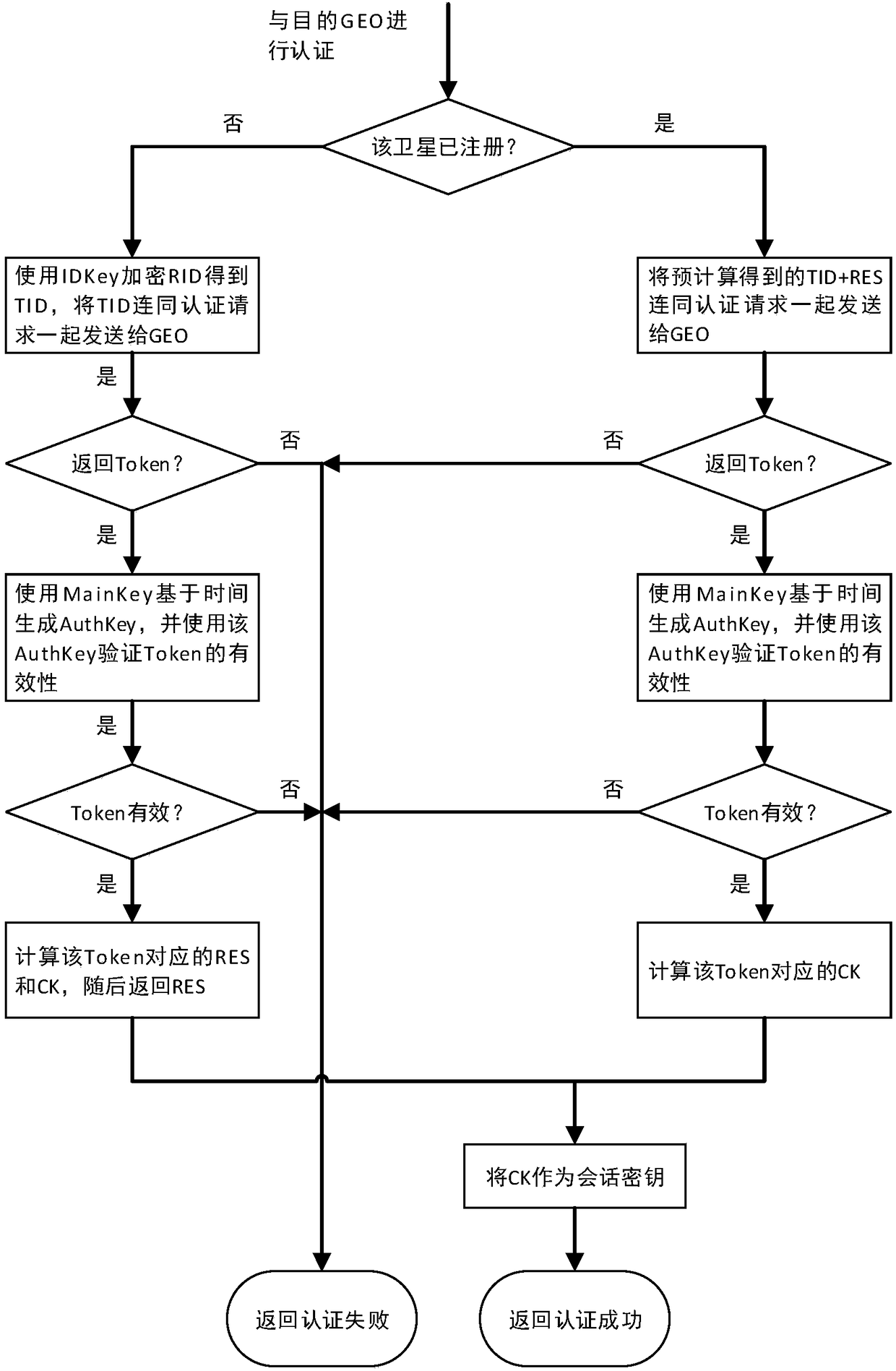
[0090] The existing technology cannot realize trust establishment and secure communication between satellites without the participation of a trusted third party. The present invention provides an inter-satellite networking authentication method applicable to a double-layer satellite network, comprising:
[0091] LEO completes the identity authentication of GEO by judging whether the locally calculated XMAC is equal to the MAC in Token; GEO completes the identity authentication of LEO by judging whether the locally stored XRES is equal to the returned RES; when performing identity authentication, GEO and The authentication ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com