Data encryption/decryption checking method and system
A verification method and data technology, applied in the field of data processing, can solve problems such as errors or malicious tampering, increased computing overhead, and reduced transmission and storage performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0079] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
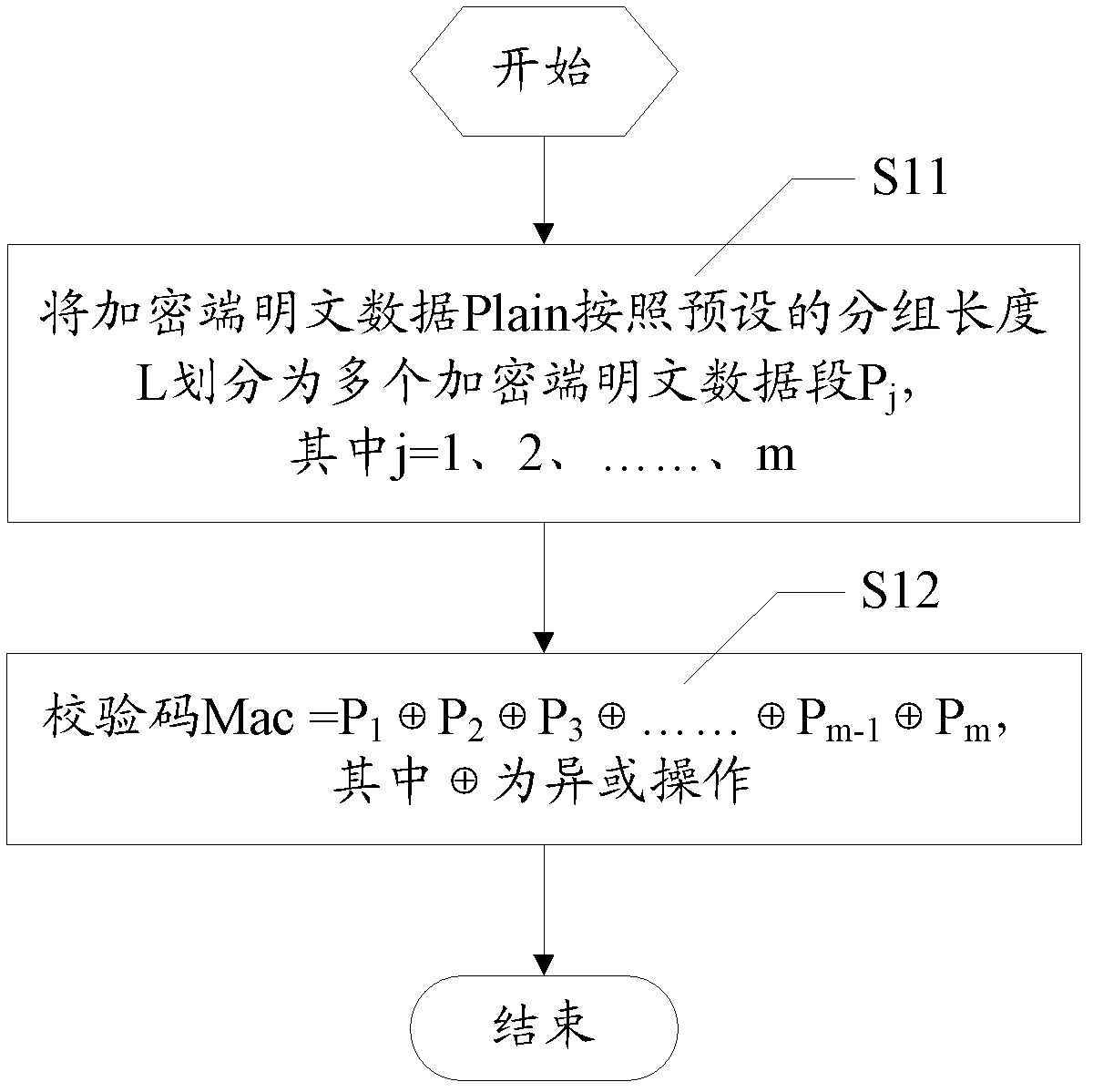
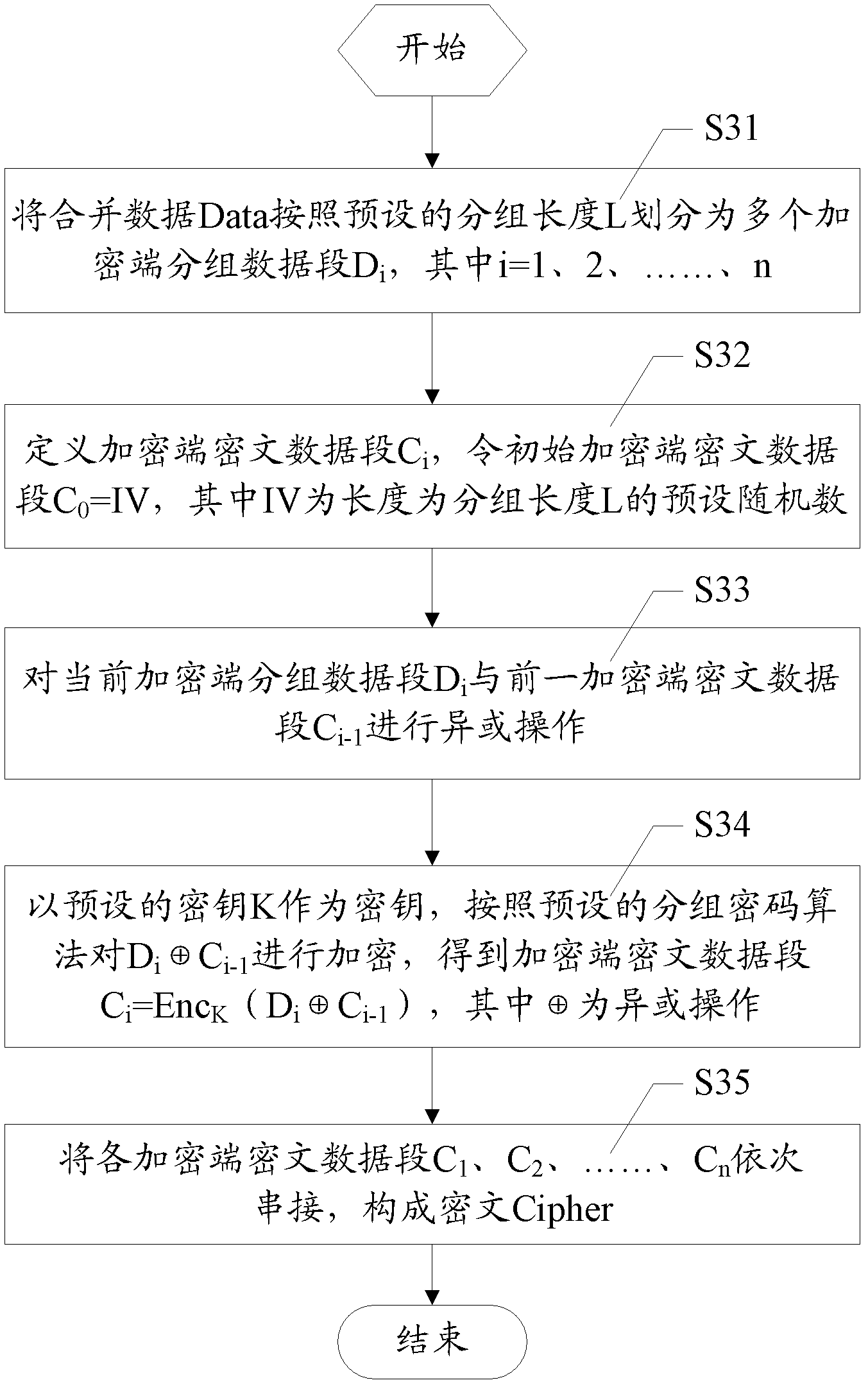
[0080] Such as figure 1 as shown, figure 1 It is a flowchart of a data encryption / decryption verification method in an embodiment of the present invention. The data encryption / decryption verification method mentioned in this embodiment of the invention includes steps:
[0081] In step S10, the encryption device performs an XOR operation on each data segment in the encrypted plaintext data Plain to obtain a check code Mac.
[0082] In this embodiment, the check code Mac is generated at the encryption end, and the encryption device installed in the encryption end computer PC executes the XOR operation to generate the check code Mac. Since the XOR operation is simple and the processing time is fast, the obtained check code The verification code Mac can also detect the correctness and integrity of the data, avoiding the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com