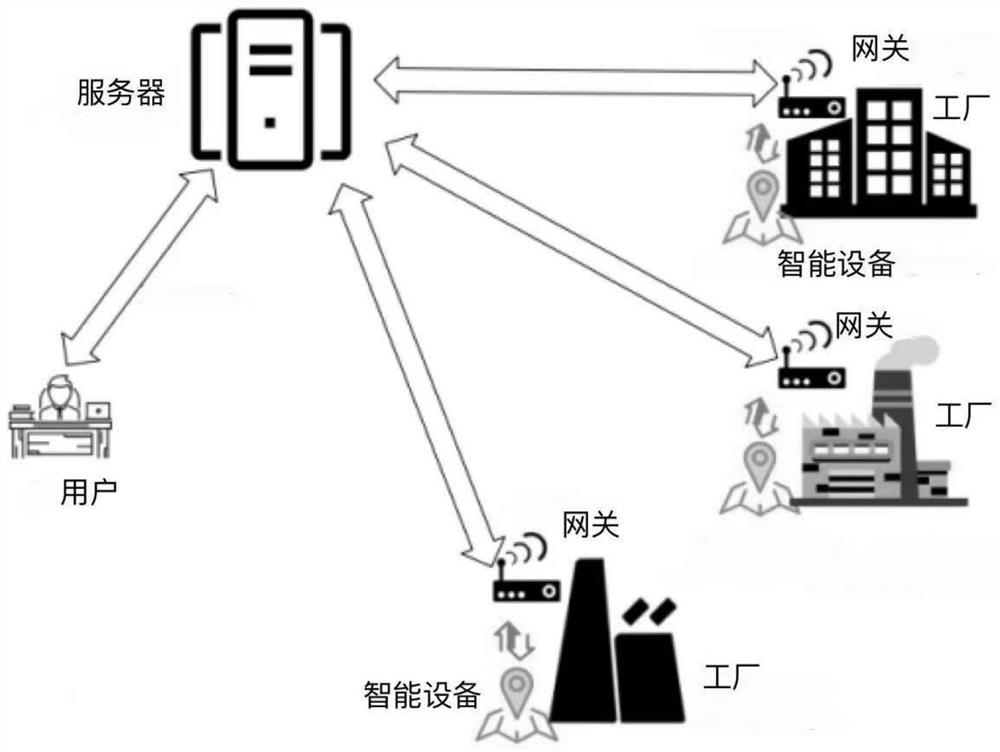
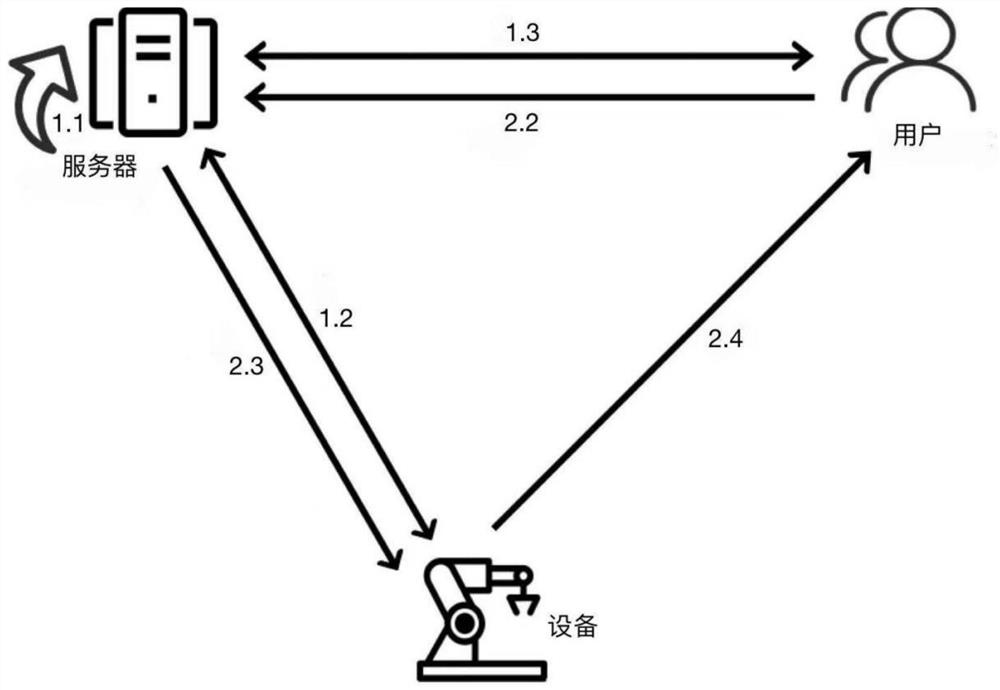
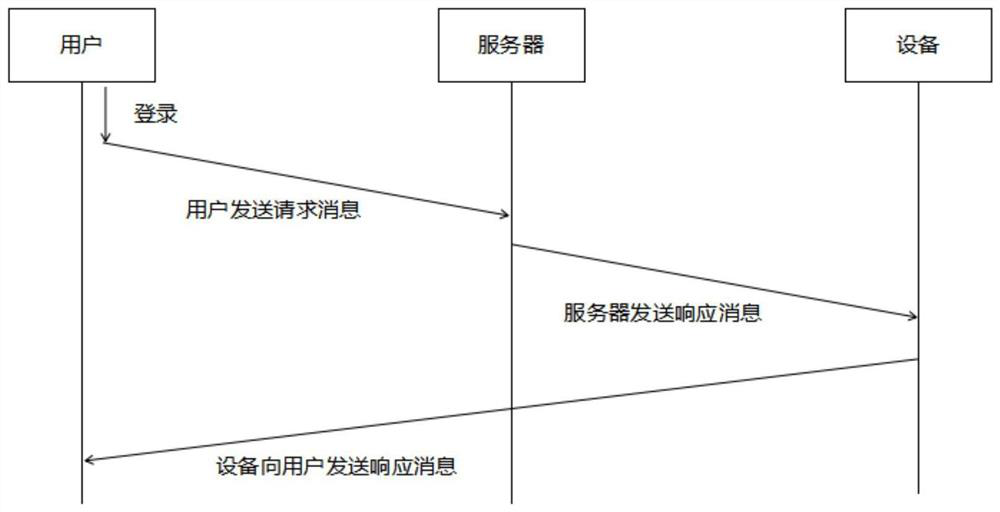
Multi-factor-based industrial Internet of Things session key negotiation method
An industrial Internet of Things and session key technology, which is applied in the field of multi-factor-based industrial Internet of Things session key negotiation, can solve problems such as unsatisfactory, unable to meet the security of the Internet of Things environment, and the key agreement process is not lightweight enough. To achieve the effect of ensuring anonymity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0132] The present invention uses hash function, bit operation and fuzzy extraction and recovery function, and the specific implementation calculation steps are as follows:
[0133] Define the execution time of some symbols as follows:
[0134] T h ≈0.0001ms: is the execution time of a one-way hash operation.
[0135] T f ≈0.442ms: is the execution time of a fuzzy extractor recovery function operation.
[0136] In the process of login, two-way authentication and completion of key agreement, the present invention has 3 communication messages: MQ1={RID i , M1, M2, M3, M4, T 1}, MQ2={Mu5, M6, M7, M8, Mu51, T 2}, MQ3={M10, M11, M12, M13, M13, T 3} need (160+160+160+160+160+160+160+32)=832 bits respectively, (160+160+160+160+160+160+32)=832 bits, (160+160+160+ 160+160+160+32)=832 bits.
[0137] Therefore, the total communication cost of this embodiment is 832+832+832=2496 bits.
[0138] After the above analysis, the communication overhead results shown in Table 2 can be ob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com