Position information hiding method and position server
A location information and server technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of sparse users, inability to guarantee the availability and accuracy of location services, and increase the calculation overhead of location services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
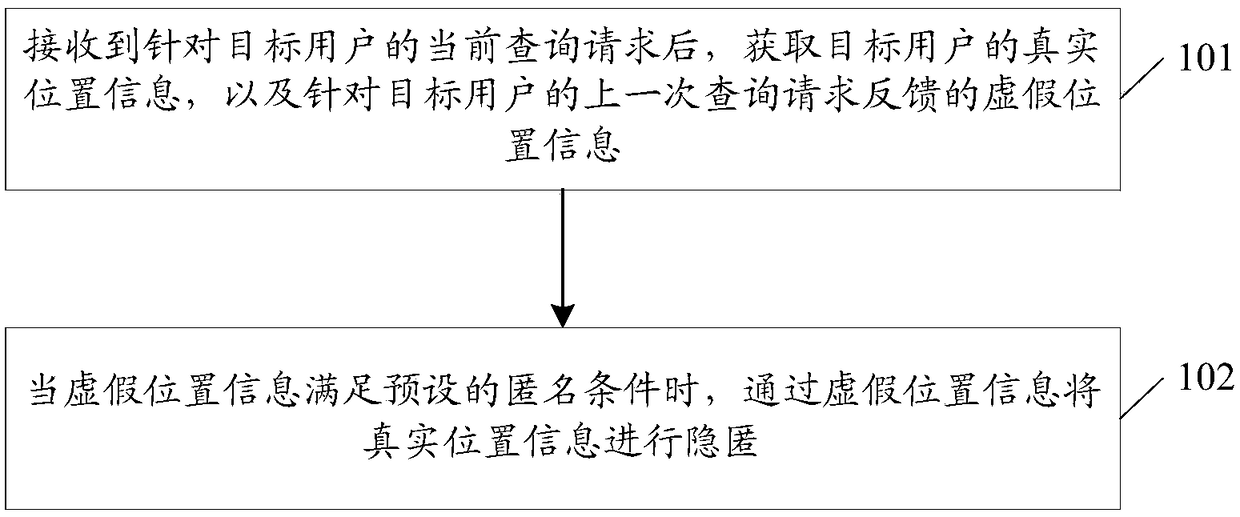
[0057] In a specific embodiment of the invention, figure 1 It is a schematic flowchart of the first realization of the location information concealment method in the embodiment of the present invention. Such as figure 1 As shown, the concealment method of location information may include the following steps:
[0058] Step 101. After receiving the current query request for the target user, obtain the real location information of the target user and the false location information fed back by the last query request for the target user.
[0059] In the specific implementation of the present invention, the location server first receives the current query request for the target user; wherein, the current query request may carry the location identifier of the target user. In a specific embodiment of the present invention, the location server may store the false location information of the target user corresponding to each query. Therefore, after receiving the current query request...
Embodiment 2
[0087] Image 6 It is a schematic flowchart of the second implementation of the location information concealment method in the embodiment of the present invention. Such as Image 6 As shown, the concealment method of location information may include the following steps:
[0088] Step 601. After receiving the current query request for the target user, obtain the real location information of the target user and the false location information fed back by the last query request for the target user.
[0089] In the specific implementation of the present invention, the location server receives the current location request sent by the inquiring user; wherein, the current inquiring request may carry the location identifier of the target user. In a specific embodiment of the present invention, the query user and the target user may be the same user or different users.
[0090] Step 602. Record the current query time when the current query request is received.
[0091] In a specific...
Embodiment 3
[0121] Figure 11 It is a schematic structural diagram of the first component of the location server in the embodiment of the present invention. Such as Figure 11 As shown, the location server includes: an acquisition unit 1101 and a concealment unit 1102; wherein,
[0122] The obtaining unit 1101 is configured to obtain the real location information of the target user after receiving the current query request for the target user, and the false location information fed back by the last query request for the target user;
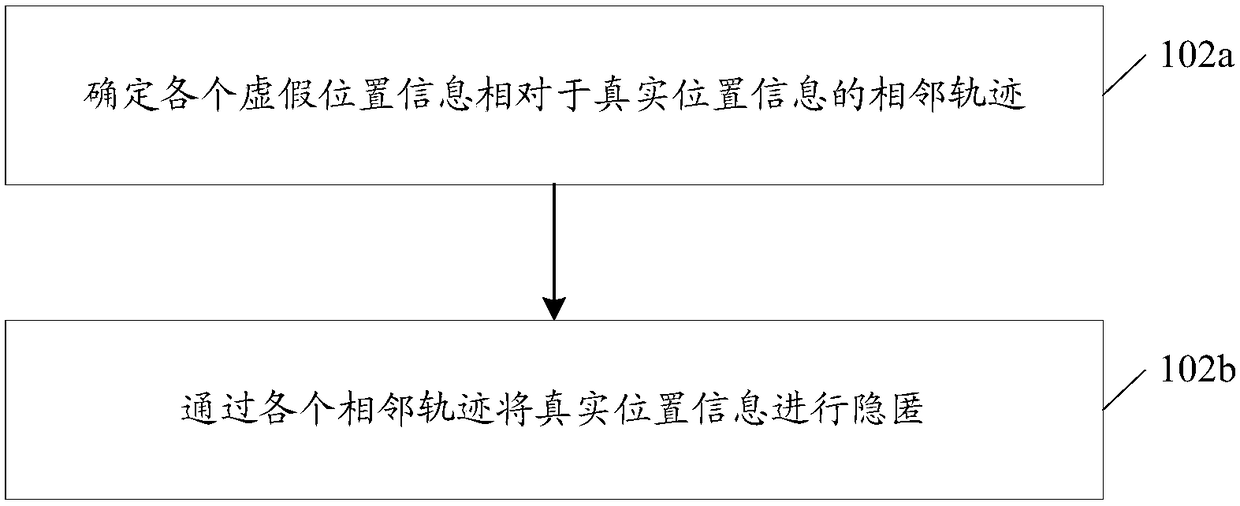
[0123] The concealment unit 1102 is configured to conceal the real location information through the false location information when the false location information satisfies a preset anonymity condition.
[0124] Figure 12 It is a schematic diagram of the second component structure of the location server in the embodiment of the present invention. Such as Figure 12 As shown, the concealment unit 1102 includes: a determination subunit 11021 and a concea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com