Shared data cloud audit method with identity tracking function
A technology for sharing data and identities, applied in the field of cloud computing security, can solve the problem of not being able to determine which member uploads
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
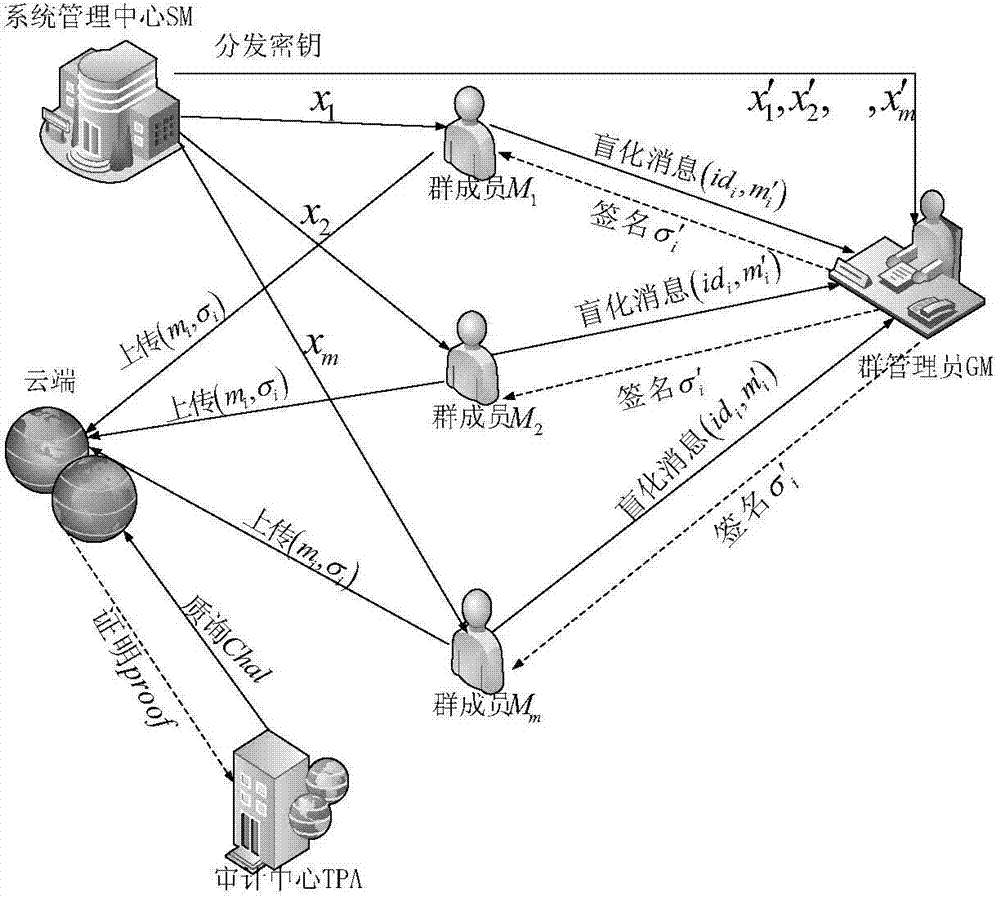
[0051] The present invention provides a shared data cloud audit system capable of tracking identities, which includes: a cloud module, a system management center module (SM for short), a group manager module (GM for short), a group member module, and an audit center module (TPA for short). ).
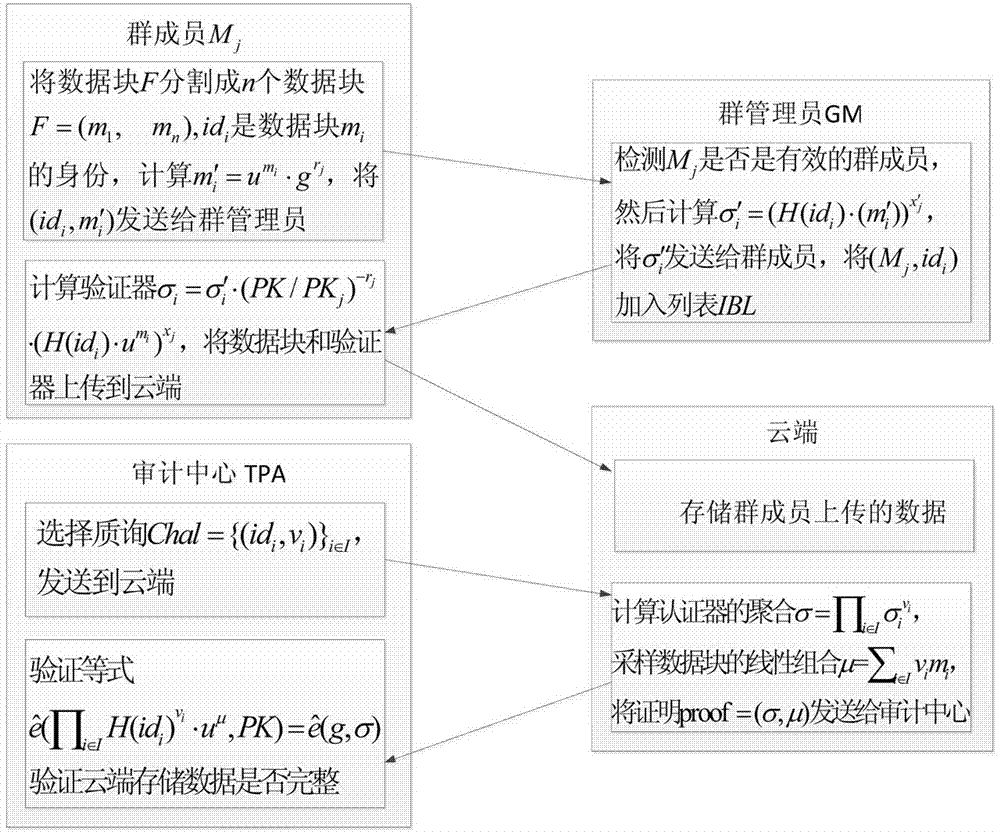
[0052] The cloud module provides storage resources for group member data, and the data is divided into n data blocks and stored in the cloud;
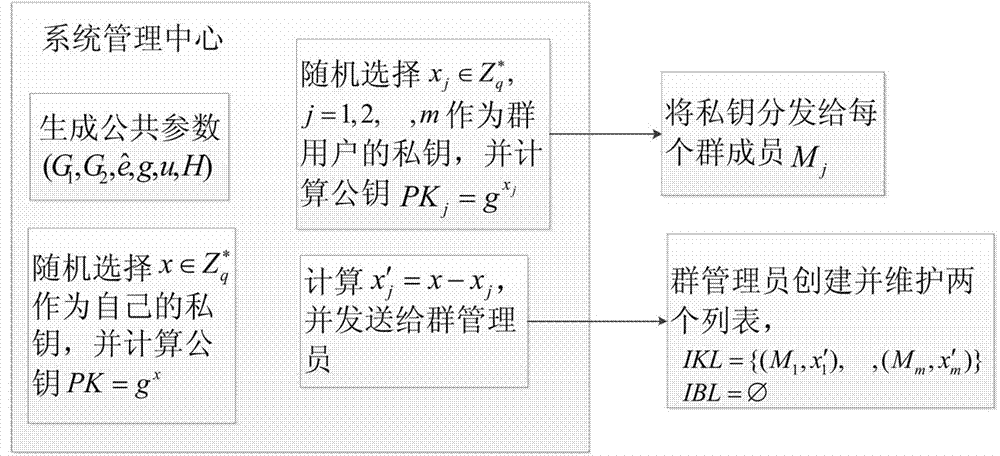
[0053] The system management center module generates various system parameters, the public and private keys of the user group, the private key of each group member and the key of the group administrator module;
[0054] The group administrator module maintains two lists, namely the identity-key list IKL and the identity-data block list IBL, which are used to track the identity of the data block owner when necessary, and the identity-key list saves the member identity and related keys, and the identity-data block list records the member's operat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com