Group signature method suitable for large groups
A group signature and group trustworthy technology, which is applied to the public key of secure communication, user identity/authority verification, electrical components, etc., can solve the problems of calculation amount, communication amount and efficiency that are not suitable for large groups, and achieve saving time and high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below in conjunction with accompanying drawing and embodiment:
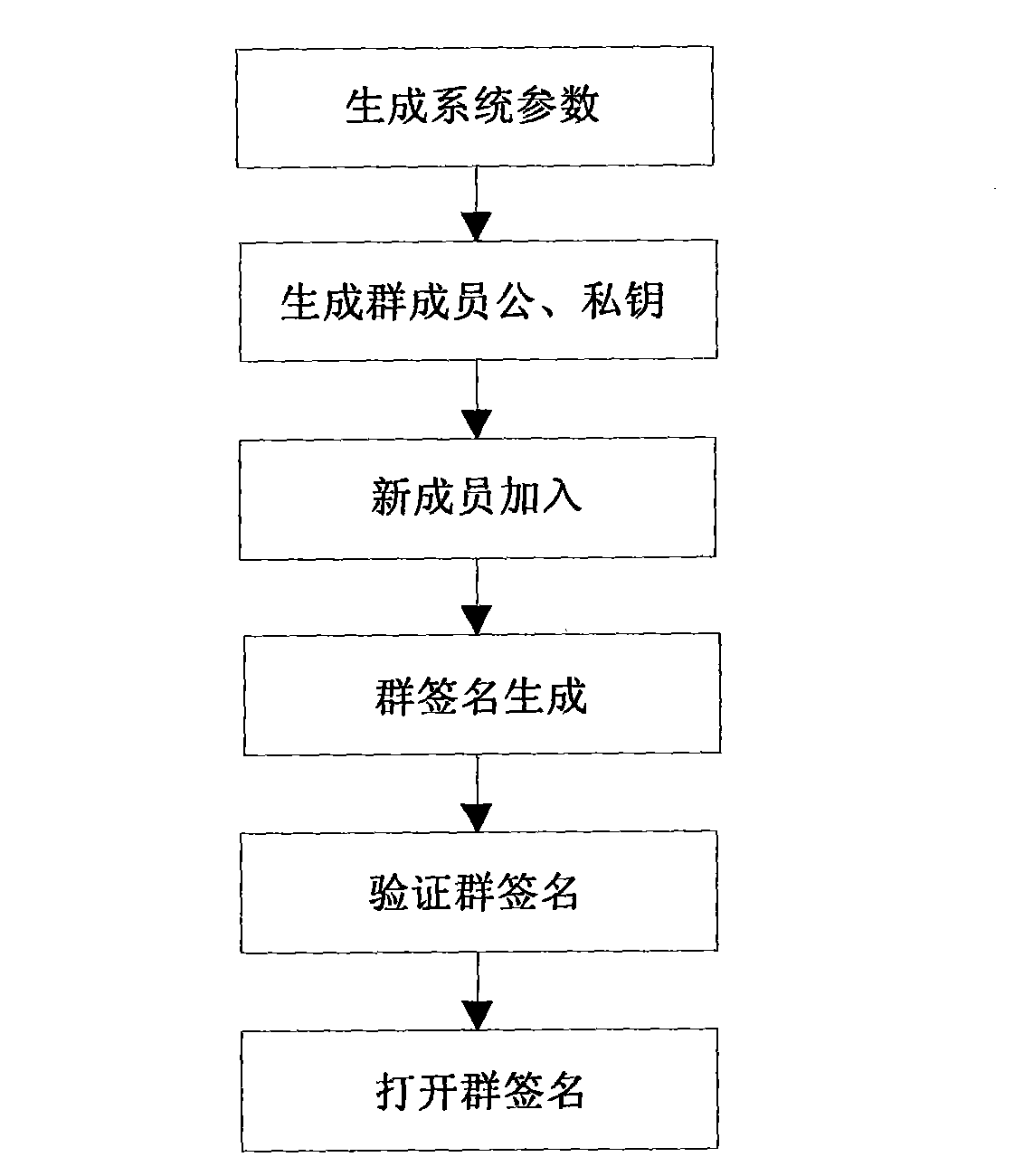
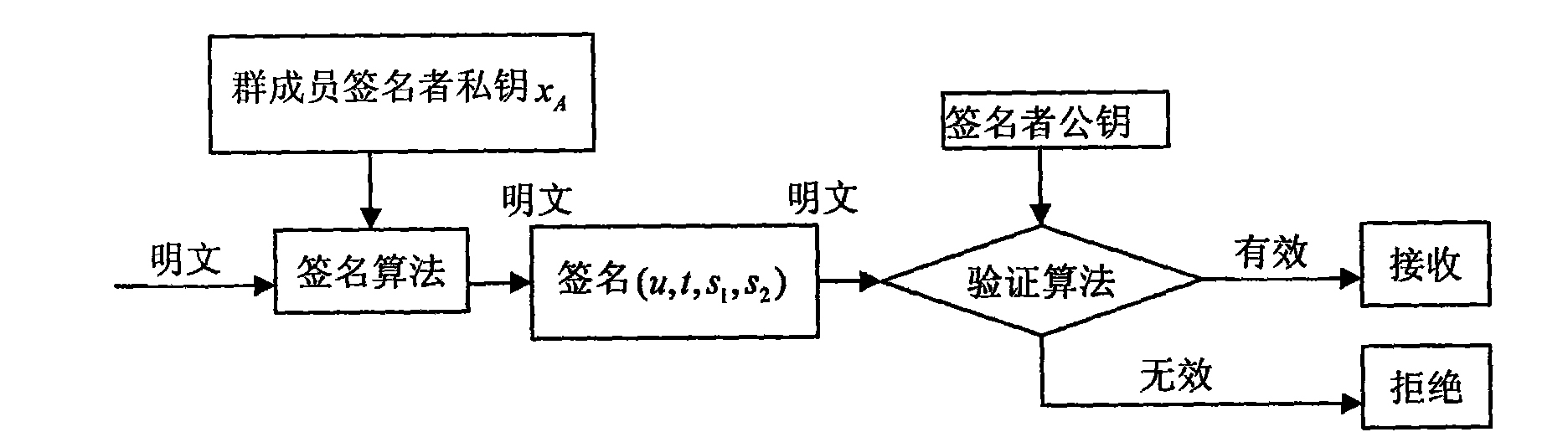
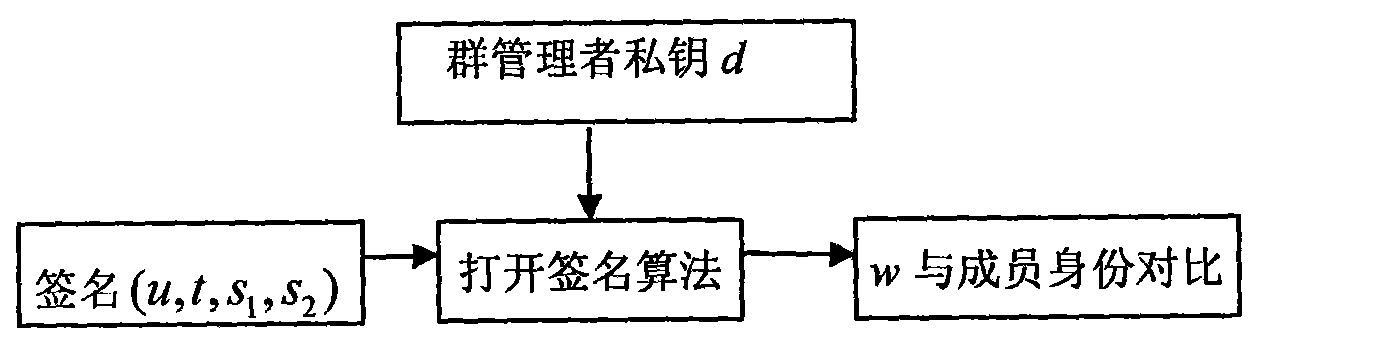
[0029] like figure 1 , figure 2 and image 3 As shown, this embodiment includes the following steps:
[0030] Step 1, the system is established, the trusted center (TC) generates system parameters, selects three prime numbers p, q, f and RSA modulus n=pq, and simultaneously selects e and d to satisfy Let g be Z n * An element of order f in , H( ) is a Hash function: , (k=160). Pick a random number Calculate y=g x(mod n).
[0031] The trusted center (TC) sends (d, x) to the group manager (GM) as the group private key, and then discloses (n, e, f, g, y) as the group public key. Trusted Center (TC), Group Manager (GM) and each group member are regarded as computers or nodes that process or jointly process specific operation steps.
[0032] Here is a further explanation of the selection method of the three prime numbers (p, q, f): select Z n * An...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com