Privacy protection access control method in wireless sensor network supported by IP
A wireless sensor network and access control technology, applied in the field of Internet of Things security, can solve the problems of unusable security mechanism, privacy security threat of user data access, limited sensor resources, etc., to achieve flexible user revocation process and ensure unlinkability , the effect of ensuring anonymity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The specific implementation of the present invention will be further described below in conjunction with the accompanying drawings and examples, but the implementation and protection of the present invention are not limited thereto. It can be realized or understood with reference to the prior art.
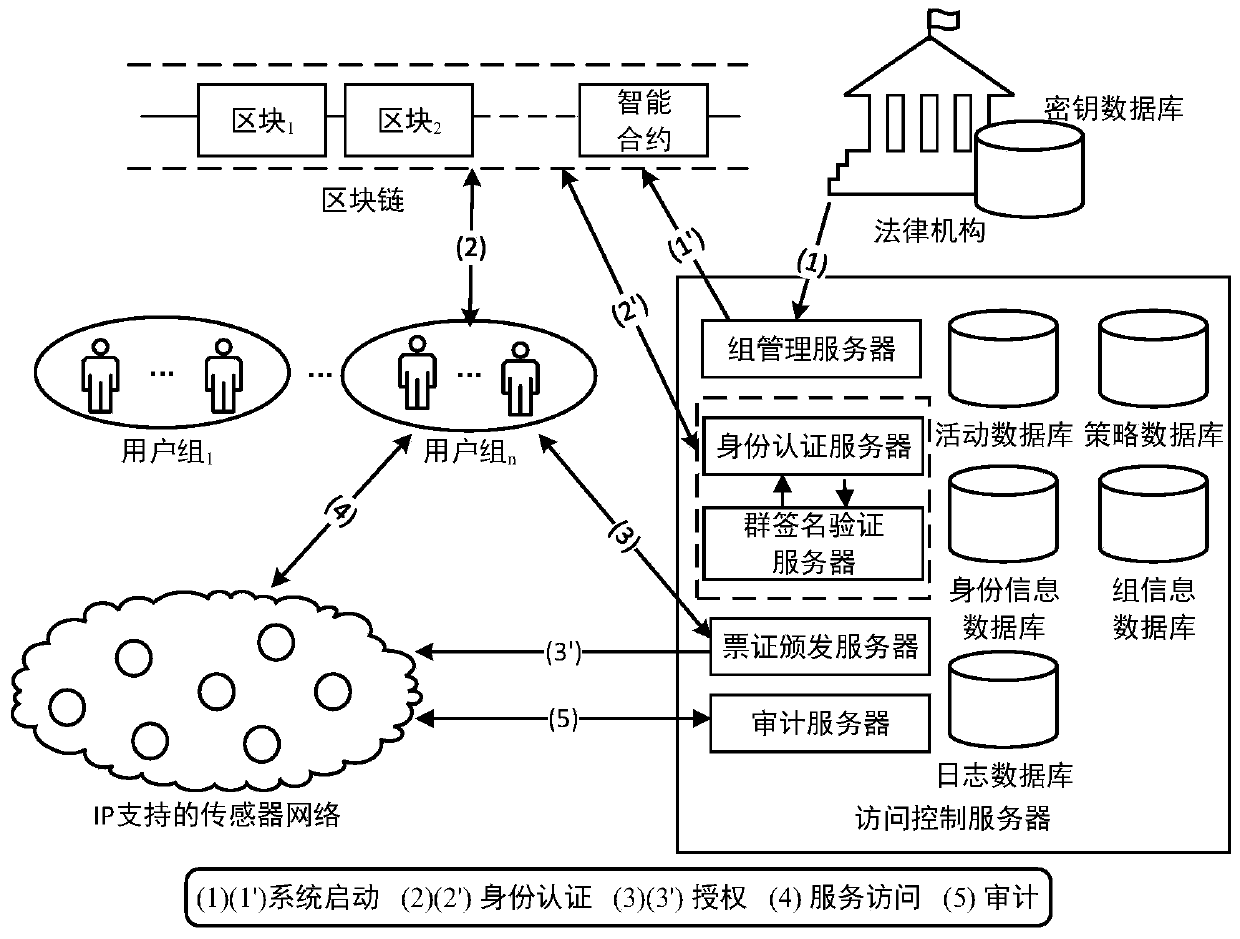
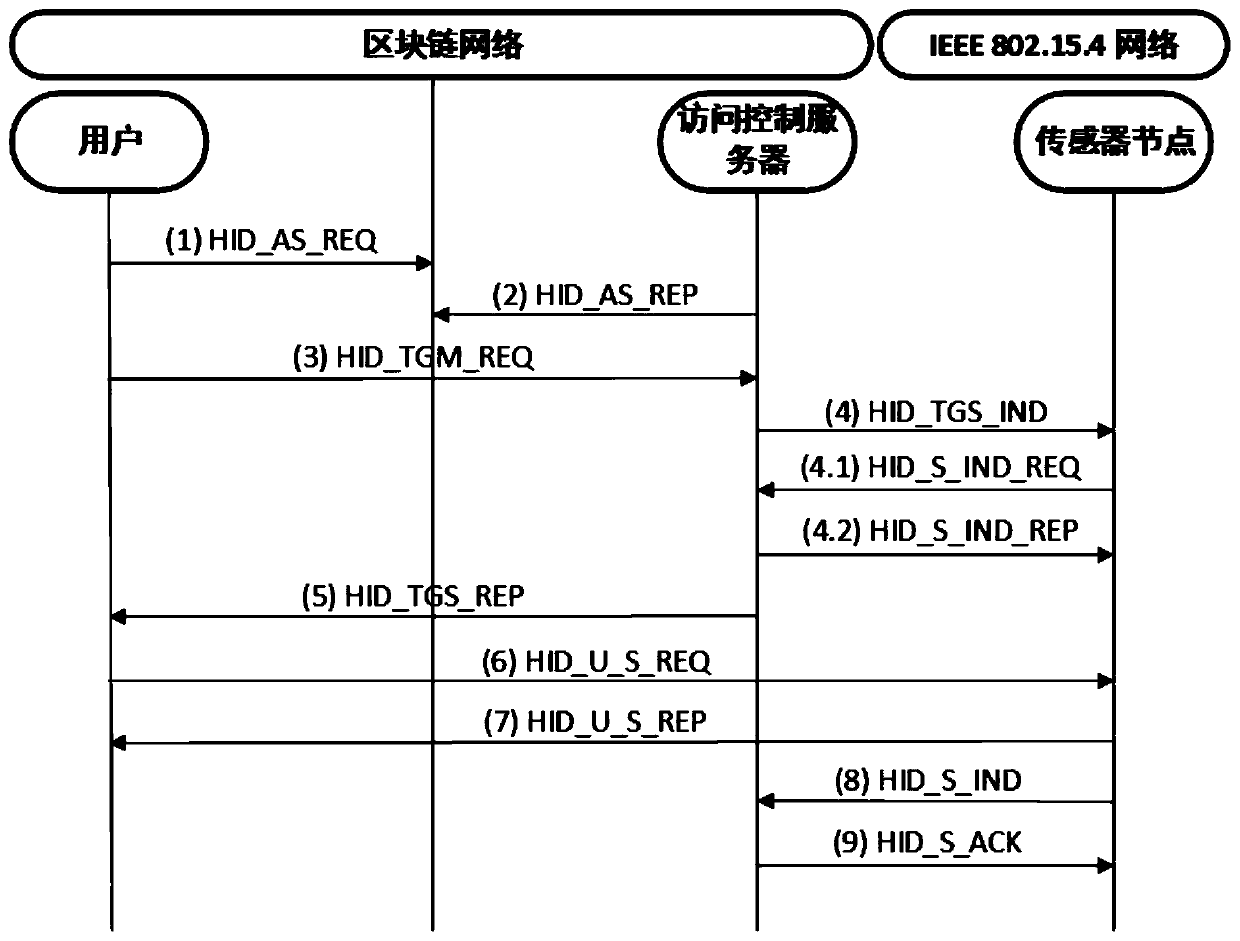
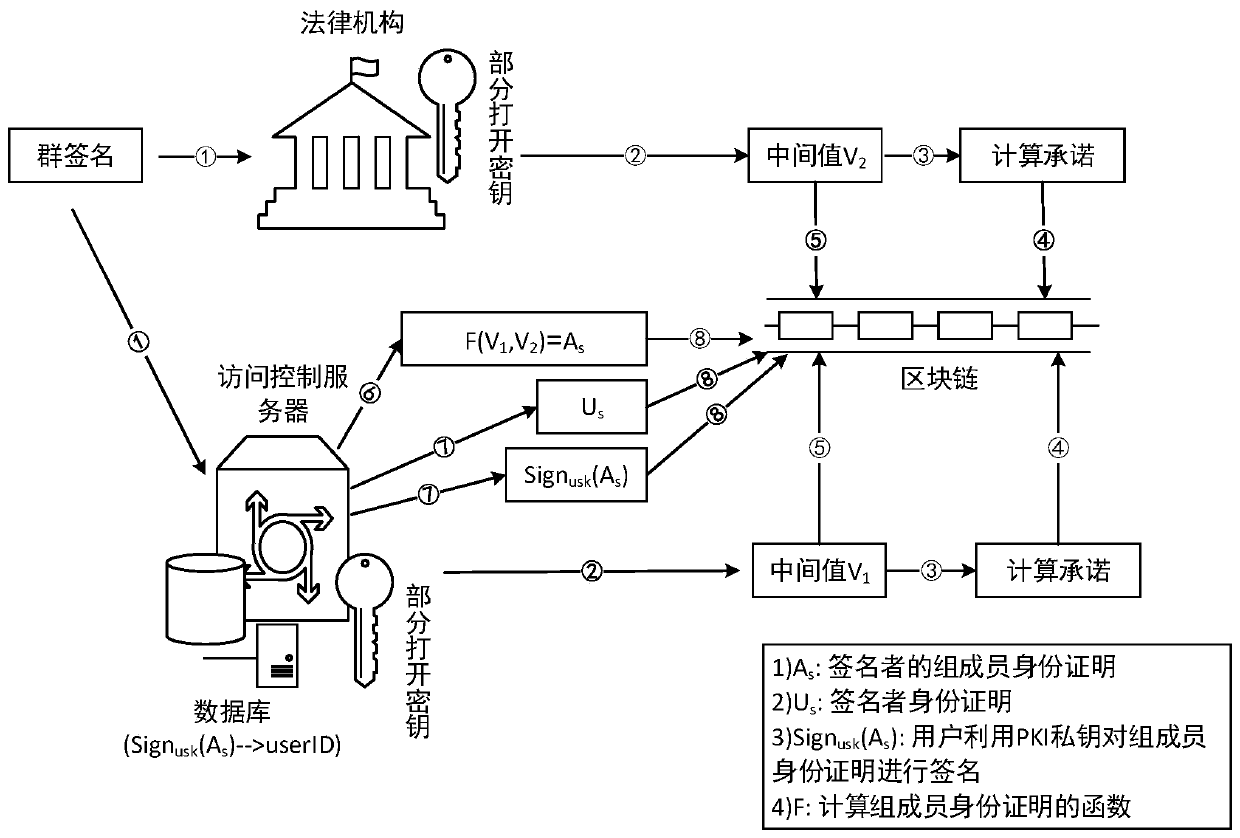
[0026] Such as figure 1 , a privacy-preserving access control method in an IP-supported wireless sensor network, and its specific implementation steps are as follows.
[0027] Symbol Description:
[0028] U: Registered user of the wireless sensor network, has the right to access specific sensor nodes in the network
[0029] IK: Issuing key, which is used by the access control server to issue group membership certificates to registered users
[0030] OK: Open the key, which consists of two parts {ξ 1 , ξ 2}, which are generated by the access control server and the legal authority, respectively.
[0031] e X : the elliptic curve Diffie-Hellman private key of entity X (a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com