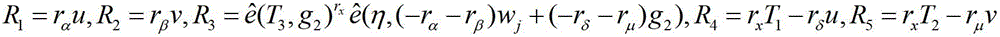Accountable and privacy-preserving wireless access network authentication method and authentication system
A wireless access network and authentication method technology, which is applied in the field of wireless access network authentication methods and authentication systems, can solve the problems such as the inability of the wireless access network to be accountable and ensure privacy, and avoid the problem of single point failure, Effectiveness to ensure efficiency and avoid escrow issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
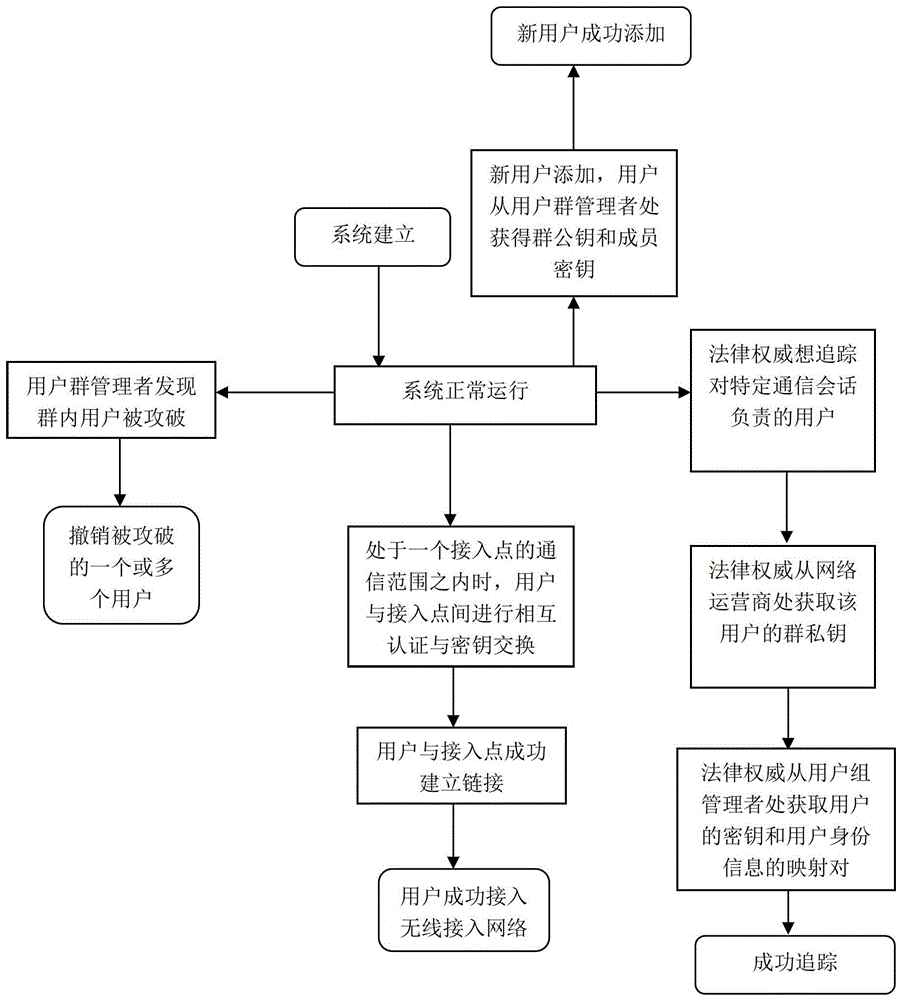
[0045] The existing wireless access authentication system involves three parties: a wireless roaming user U, an access point AP and a network operator NO. A certain number of APs are deployed at different locations in the service area to cover the entire area and provide network services to network users. Users can access the network from anywhere with their mobile devices.
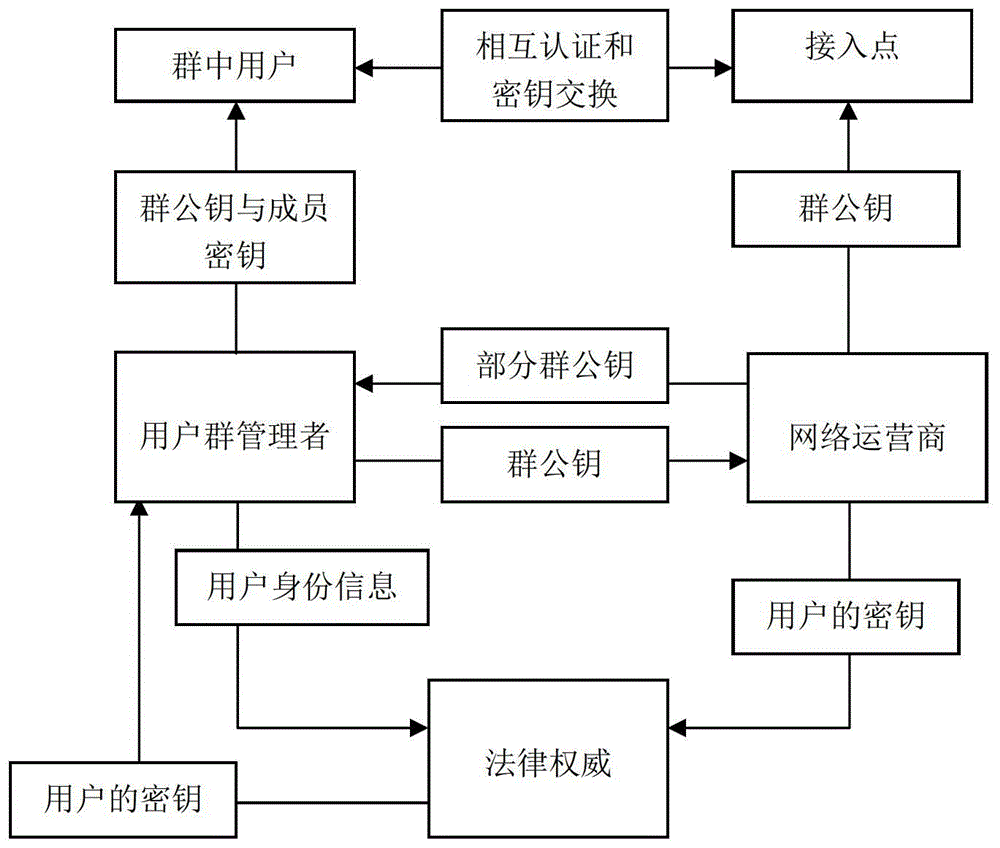
[0046] figure 2 For the wireless access network authentication system of the present invention, the key management model in the authentication system of the present invention involves four typical network entities: network operator, access point, user group manager and users in the group. In the present invention, the user does not directly register with the network operator, but the user group manager subscribes to the network operator for services on behalf of all users in the group. The network operator generates the group private key and part of the group public key, but keeps the group private key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com