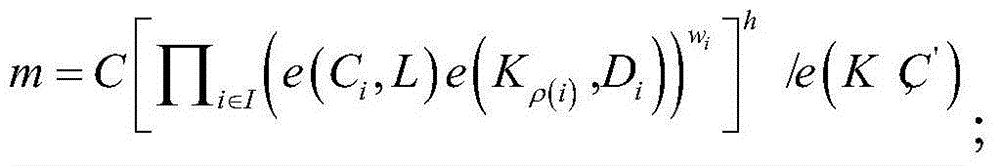Identity-based encryption method with certificates and attributes
An identity encryption and certificate technology, applied in the field of electronic information security, can solve the problems of low key escrow security, complex solution implementation, and undisclosed certificates.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
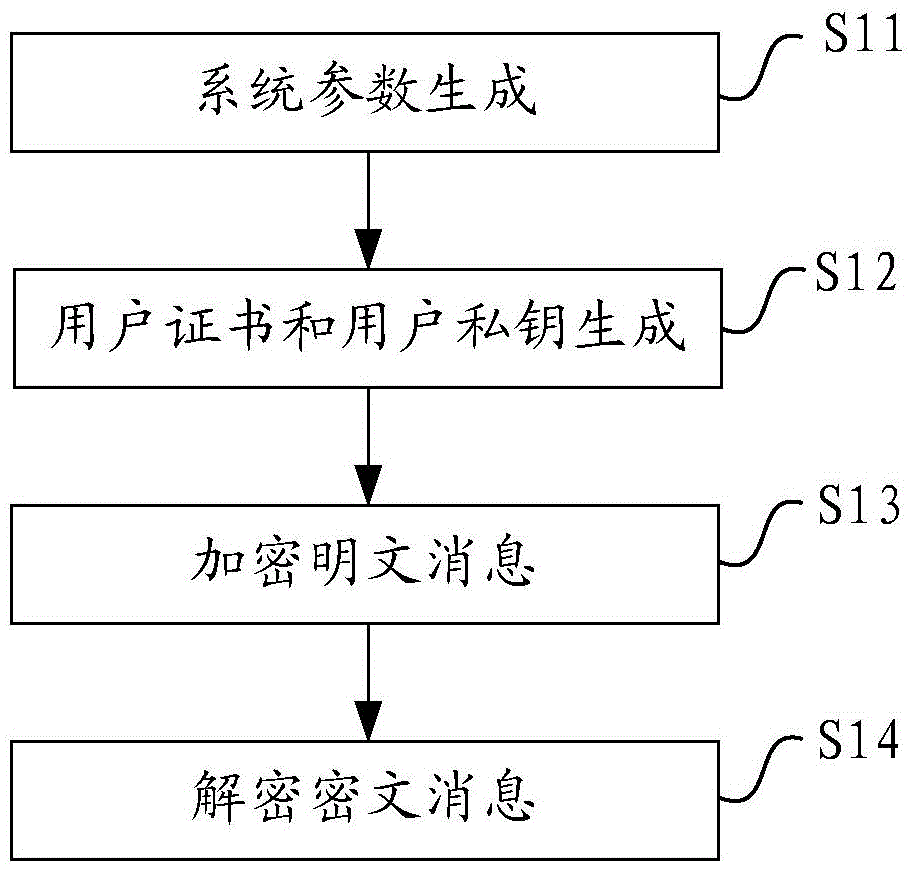
[0057] This embodiment provides a method for identity-based encryption with certificates and attributes, the flow chart of which is as follows figure 1 As shown, the following processing steps are included:
[0058] Step 11: The certificate authority CA generates and publishes system parameters by selecting the elliptic curve and the set of all attributes, and selecting the master key and security parameters.
[0059] The above CA is based on the security parameter k, selects the finite field and the constant elliptic curve on the finite field, and then selects the efficient asymmetric bilinear pairing e:G on the elliptic curve 1 ×G 2 →G T , select the generator in the pairing group, where G 1 and G 2 is the additive group of prime numbers of order p on the elliptic curve, G T is the group of p-factorial methods in finite fields;
[0060] Take G respectively 1 and G 2 Generators P and Q; denote U as the set of all attributes;
[0061] Randomly pick a non-zero element ...
Embodiment 2
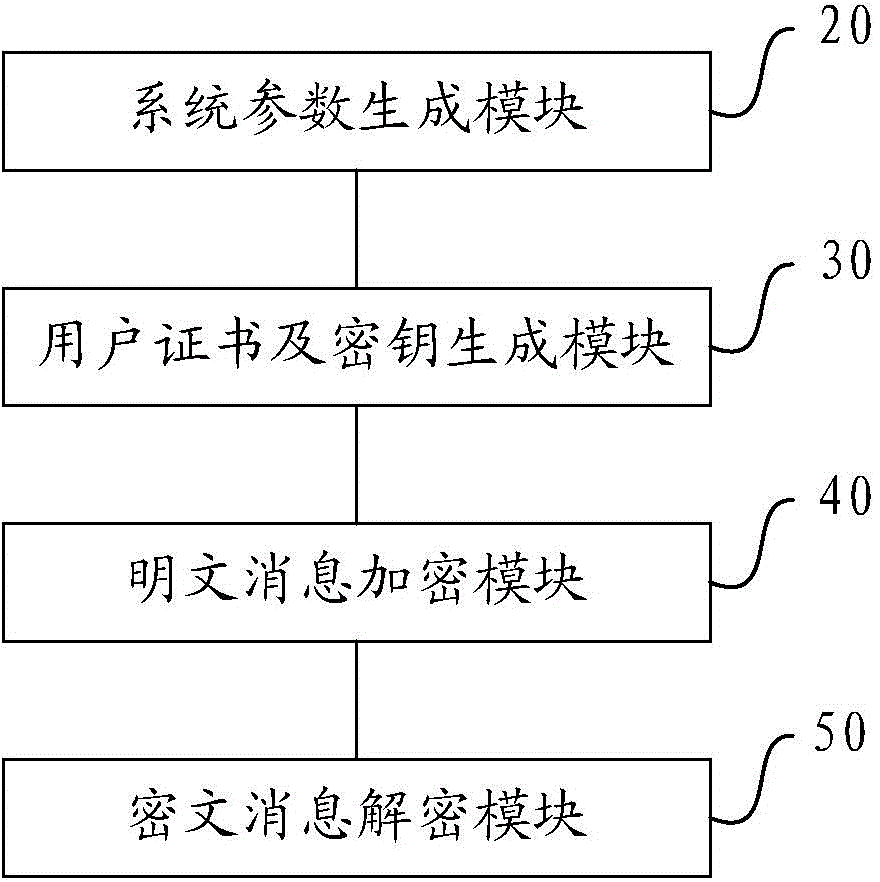
[0082] This embodiment provides an identity-based encryption device with certificates and attributes, and its specific implementation structure is as follows: figure 2 As shown, it can specifically include the following modules:
[0083] The system parameter generation module 20 is used for the certificate authority CA to generate and issue system parameters by selecting the elliptic curve and the set of all attributes, and selecting the master key and security parameters;
[0084] The user certificate and key generation module 30 is used for the user to provide information to the above-mentioned CA, obtain the certificate issued by the CA to the above-mentioned user, verify the certificate, and use the above-mentioned certificate and the above-mentioned system parameters to generate the private key of the above-mentioned user, and disclose the above-mentioned the public key of the user, said user including the sender and receiver;
[0085] The plaintext message encryption m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com