Method and device for negotiating group cipher
A group and key technology, applied in the field of communication, can solve problems such as increasing time delay, increasing system traffic, increasing algorithm complexity, etc., to achieve the effect of improving real-time performance and reducing communication traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
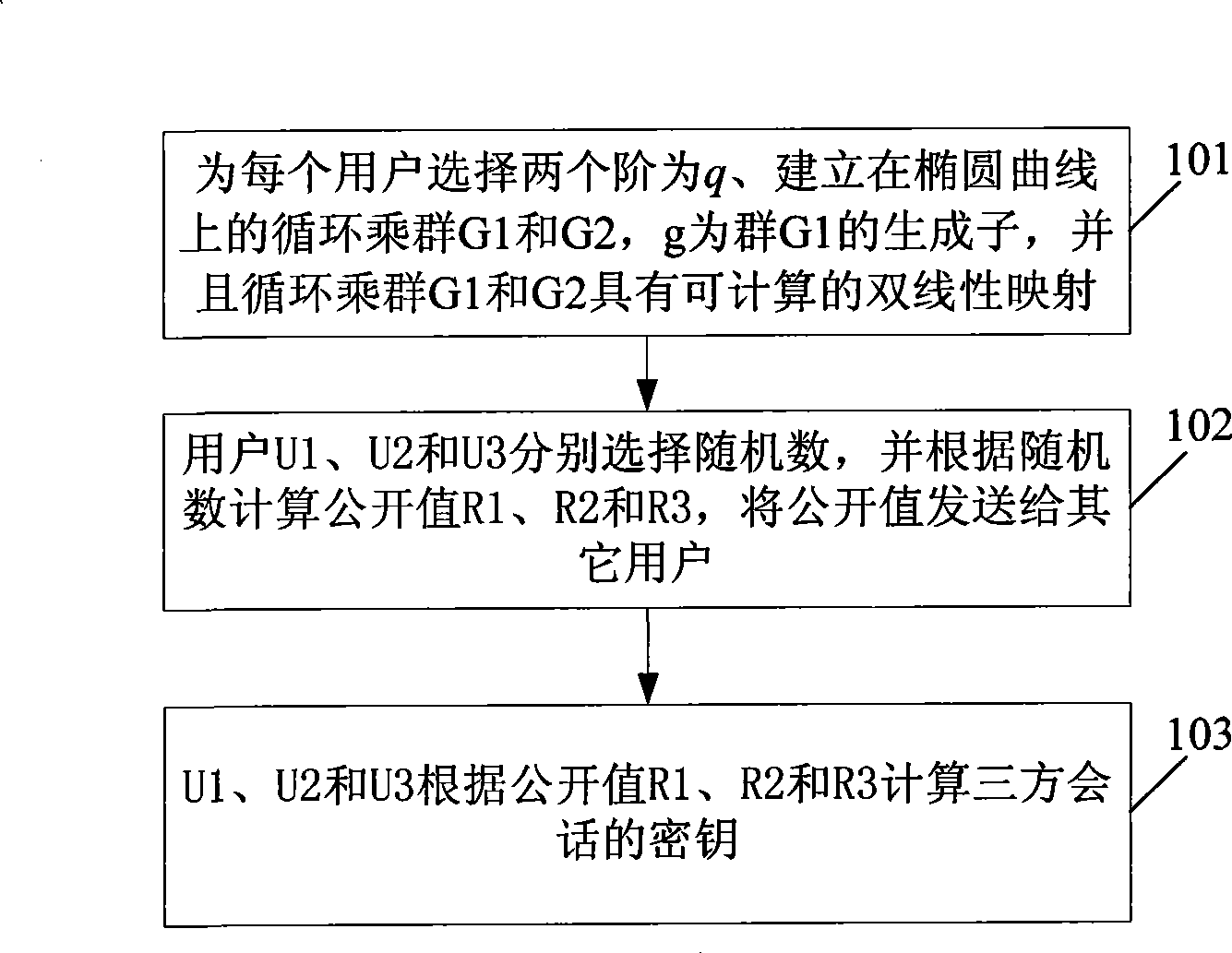
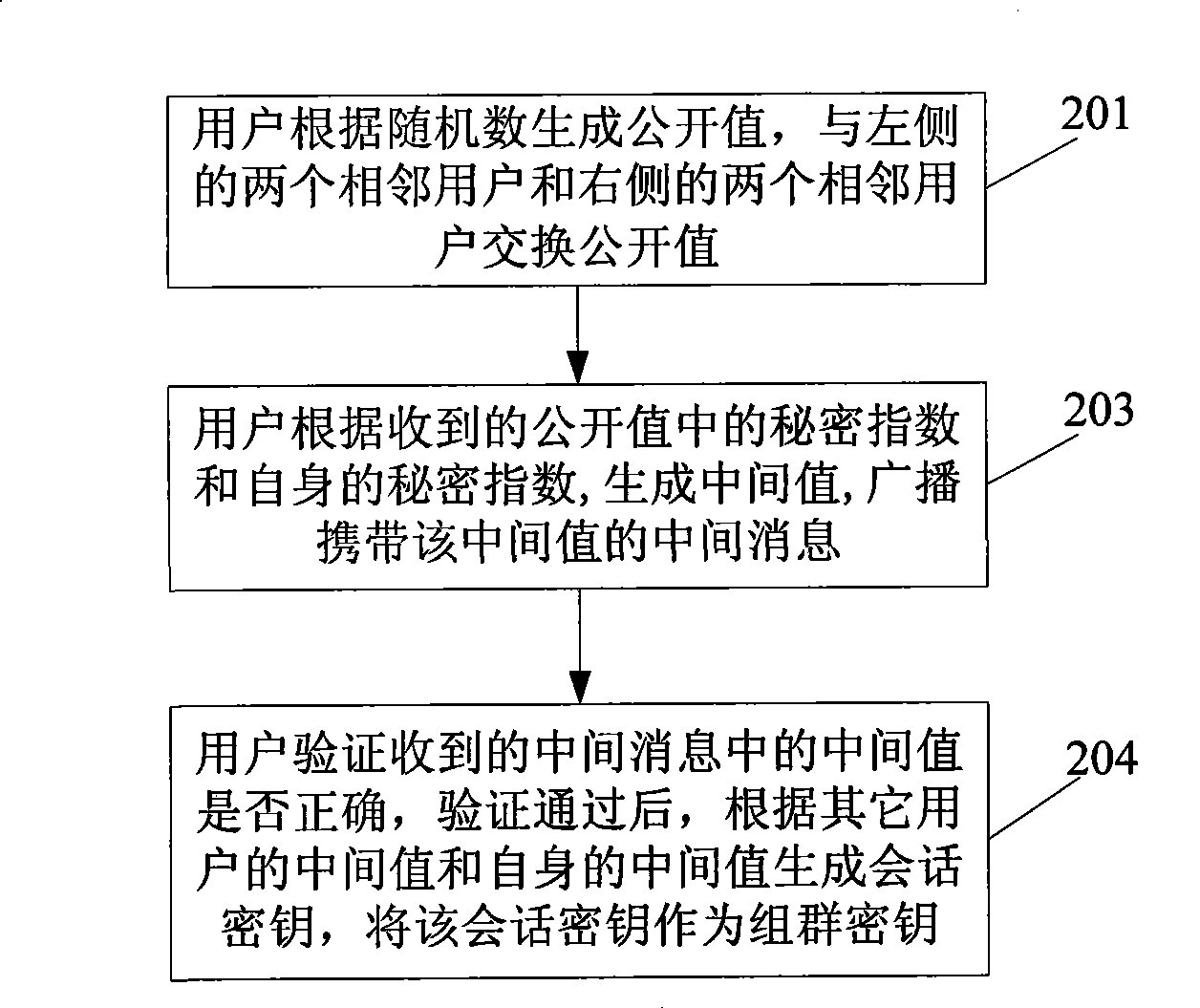
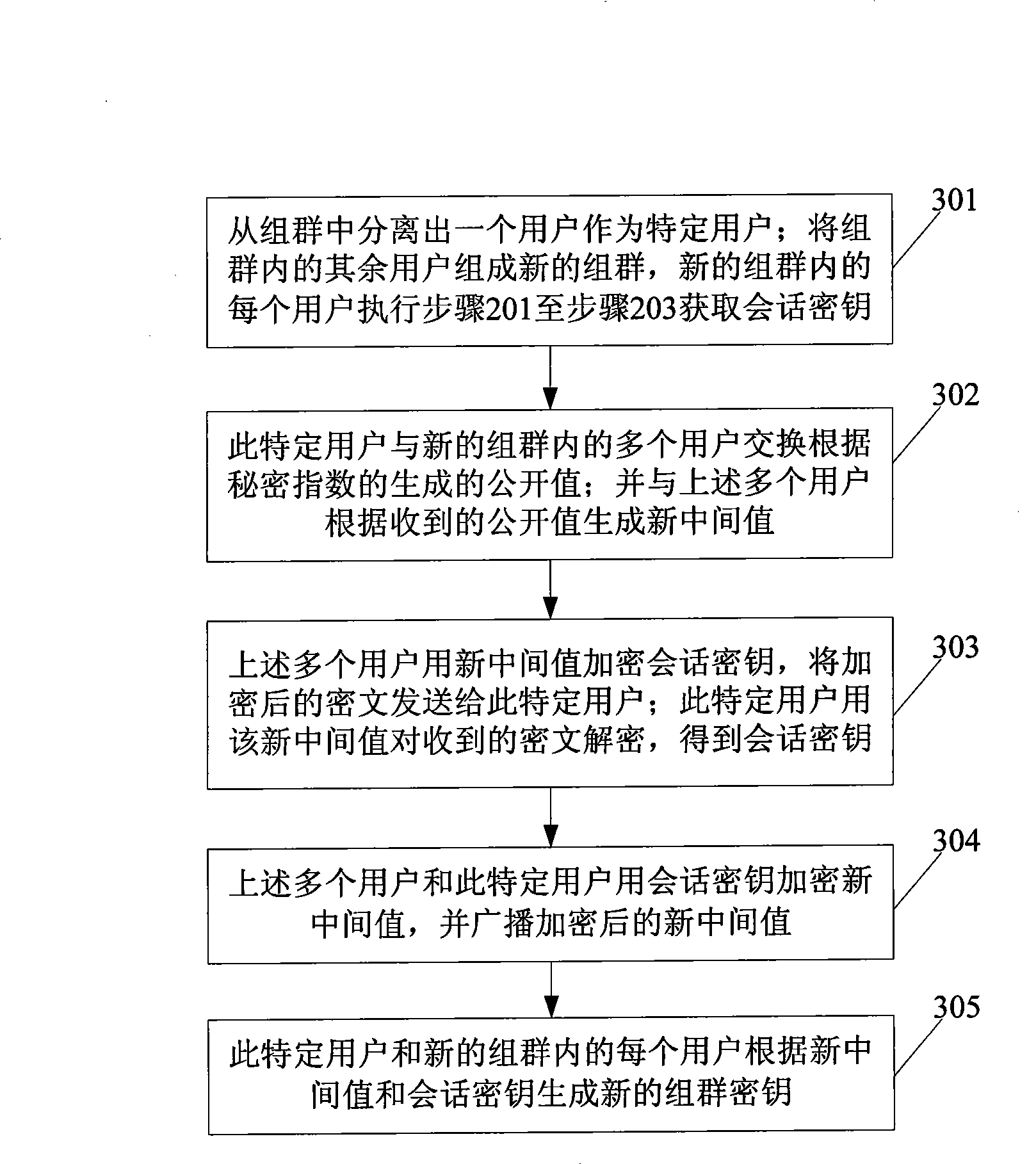
[0077] This embodiment provides a method for negotiating a group key. When the total number of users in the group is odd, see figure 2 , the method includes:
[0078] Step 201: The user generates a public value according to the secret index, and exchanges the public value with two adjacent users on the left and two adjacent users on the right;
[0079] Step 202: After receiving the public values sent by four adjacent users, the user generates an intermediate value according to the secret index in the received intermediate message and its own secret index, and broadcasts the intermediate message carrying the intermediate value;
[0080] Step 203: After receiving the intermediate message from other users, the user verifies whether the intermediate value in the received intermediate message is correct. After the verification is passed, generates a session key according to the intermediate value of other users and its own intermediate value, and uses the session key key as the...
Embodiment 2
[0135] see Figure 7 , this embodiment provides a device for negotiating a group key, including:
[0136] The information interaction module 701 is configured to generate a public value according to the secret index, exchange public values with two neighboring devices on the left and two neighboring devices on the right, and perform information interaction with other devices;
[0137] The intermediate value generation module 702 is used to extract the secret index in the public value received by the information interaction module 701, generate an intermediate value according to the secret index in the public value and the secret index of the device itself, and notify the information interaction module 701 to broadcast the intermediate value the intermediate message;
[0138] The group key generation module 703 is used to verify the intermediate value in the intermediate message received by the information interaction module 701. After the verification is passed, generate a ...
Embodiment 3
[0140] see Figure 8 , this embodiment provides a device for negotiating a group key, including:
[0141] The information interaction module 801 is configured to generate a public value according to the secret index, exchange public values with two neighboring devices on the left and two neighboring devices on the right, and perform information interaction with other devices;
[0142] The intermediate value generation module 802 is used to extract the secret index in the public value received by the information interaction module 801, generate an intermediate value according to the secret index in the public value and the secret index of the device itself, and broadcast the intermediate value through the information interaction module 801 the intermediate message;
[0143] The session key generation module 803 is used to verify the intermediate value in the intermediate message received by the information interaction module 801. After the verification is passed, generate a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com