Key threshold algorithm based on level identity encryption
An identity encryption and level technology, applied in the field of identity encryption, can solve the problems of security dependence and achieve the effect of enhancing security and flexibility and broad application prospects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
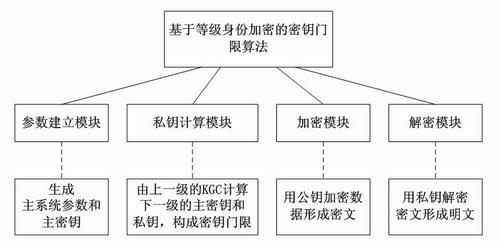
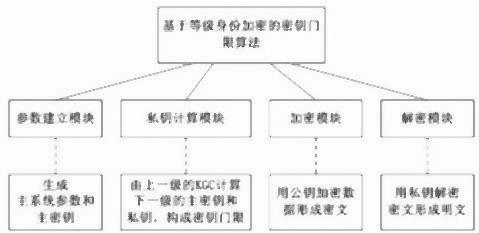
[0013] The present invention is based on the key threshold algorithm of hierarchical identity encryption, such as figure 1 As shown, the algorithm includes a parameter establishment module, a private key calculation module, an encryption module and a decryption module, assuming that the maximum level of encrypted identity is ,grade i Have private key generation center KGC, identity public key is ,in , each module is implemented as follows:
[0014] The parameter establishment module outputs the main system parameters and the master key according to a set of input security secret parameters, and the master key is managed by the highest-level KGC;
[0015] The private key calculation module is graded as i -1 n i-1 KGC calculation grade i The private key of the KGC constitutes ( m i-1, n i-1 ) threshold: input public parameters, identity public key ID , arbitrary m i-1 superior master key , output ID corresponding master key and user private key , the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com