Multi-user searchable encryption system and method with index validation and tracing
a searchable encryption and multi-user technology, applied in the field of multi-user searchable encryption technique, can solve the problems of inability to reliably store information using external database services, inability to efficiently manage such data, and increased costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
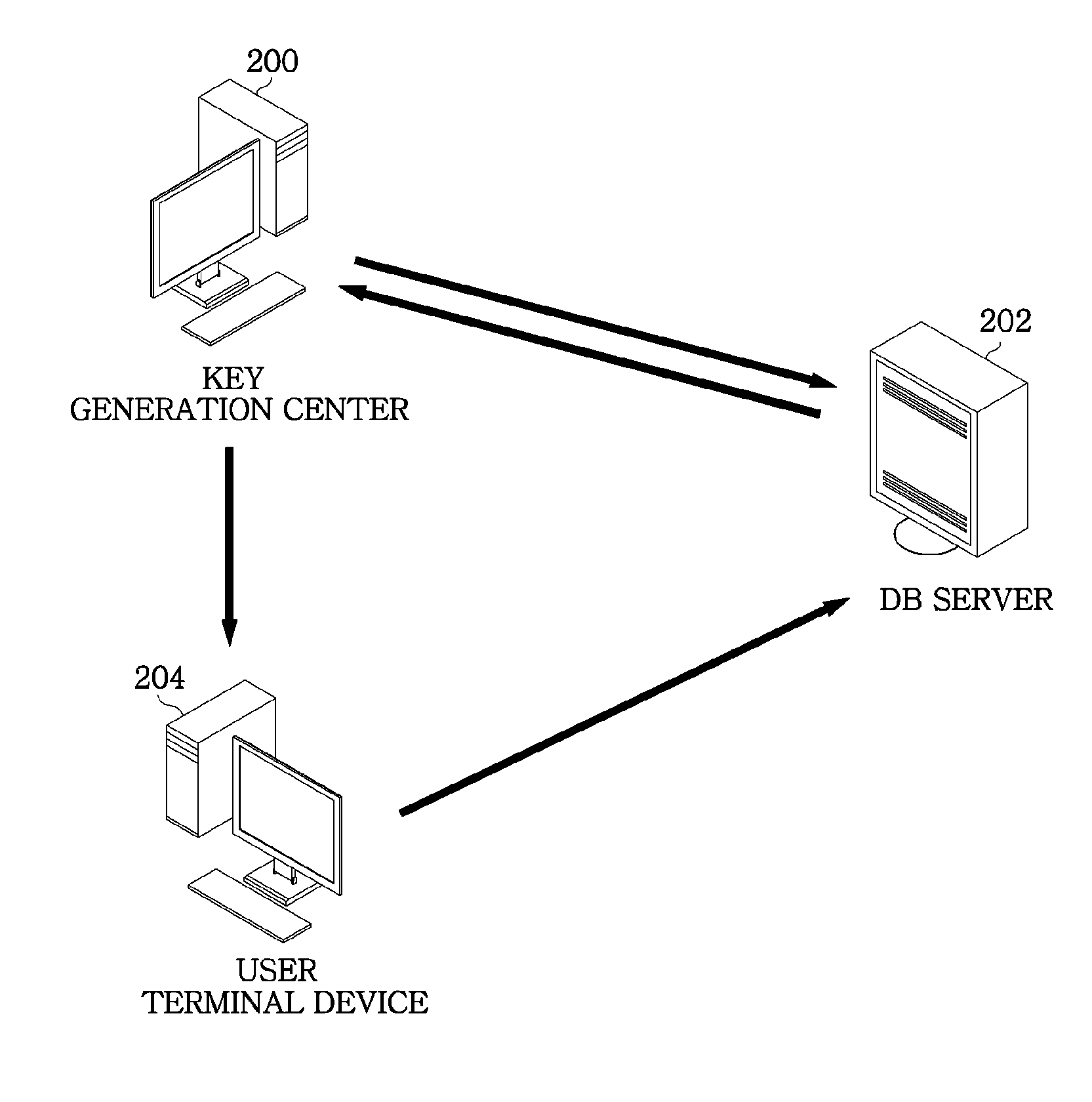
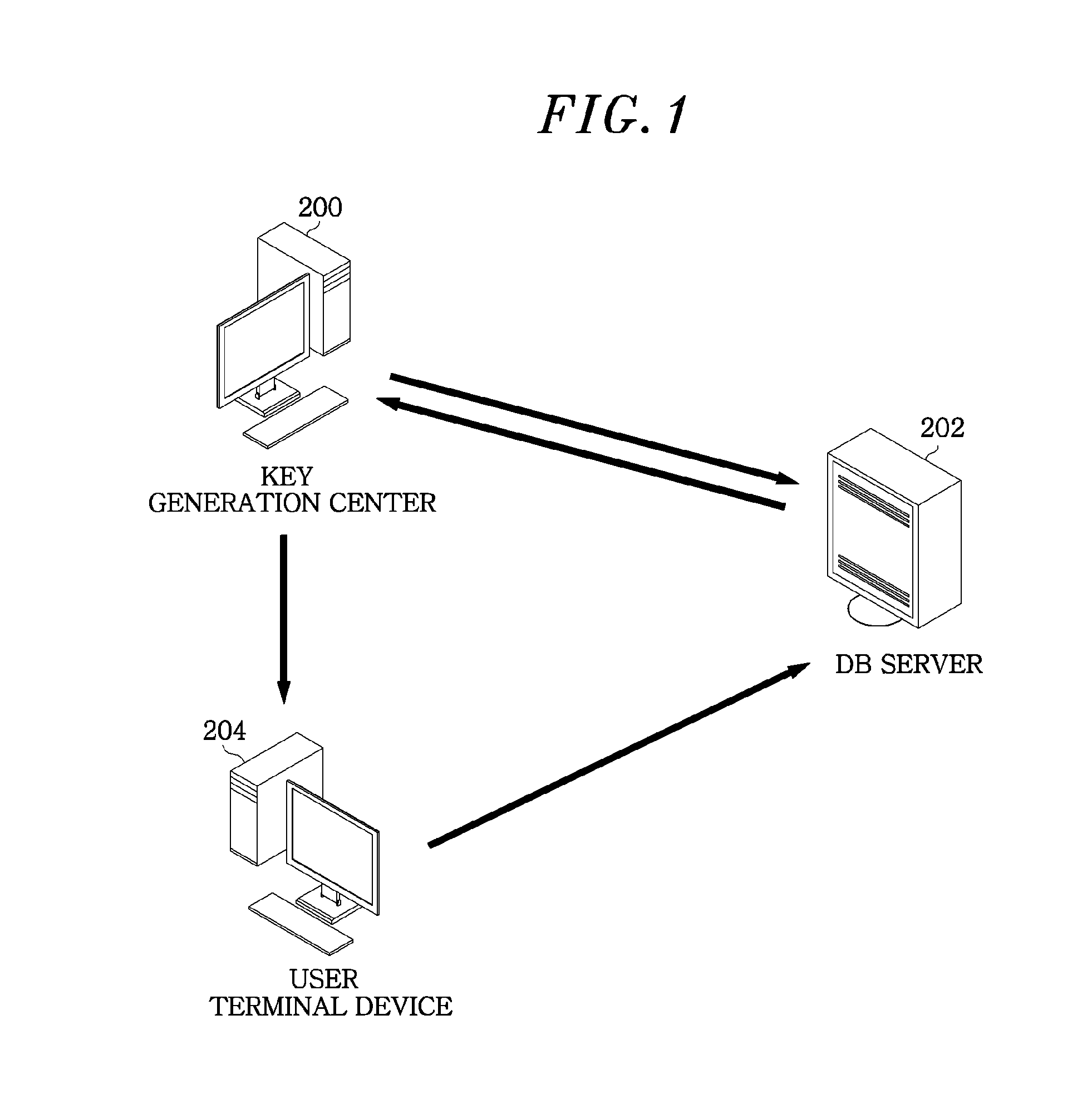
[0024]Hereinafter, embodiments of the present invention will be described in detail with the accompanying drawings. FIG. 1 is a view illustrating an operation flow in a multi-user searchable encryption system in accordance with an embodiment of the present invention.
[0025]Referring to FIG. 1, the multi-user searchable encryption system includes a key generation center (KGC) 200, a database (DB) server 202, and a user terminal device 204 used by multiple users u1, up2, . . . , un.
[0026]The key generation center 200 issues a private secret key to a user, and identifier regarding a user who has generated an index. When there is a problem with the index generated by the user terminal device 204, the key generation center 200 checks identifier of the user terminal device 204 by using the master secret key thereof to trace the user who has generated the index. Further, the key generation center 200 issues a system parameter and a public key for verifying an index before issuing the privat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com