Cryptograph index supported database transparent encryption method
A transparent encryption and database technology, applied in the field of information security, can solve the problems of easy cracking, difficulty, weak strength, etc., and achieve the effect of efficient ciphertext index, efficient data structure and algorithm, and efficient conditional query
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
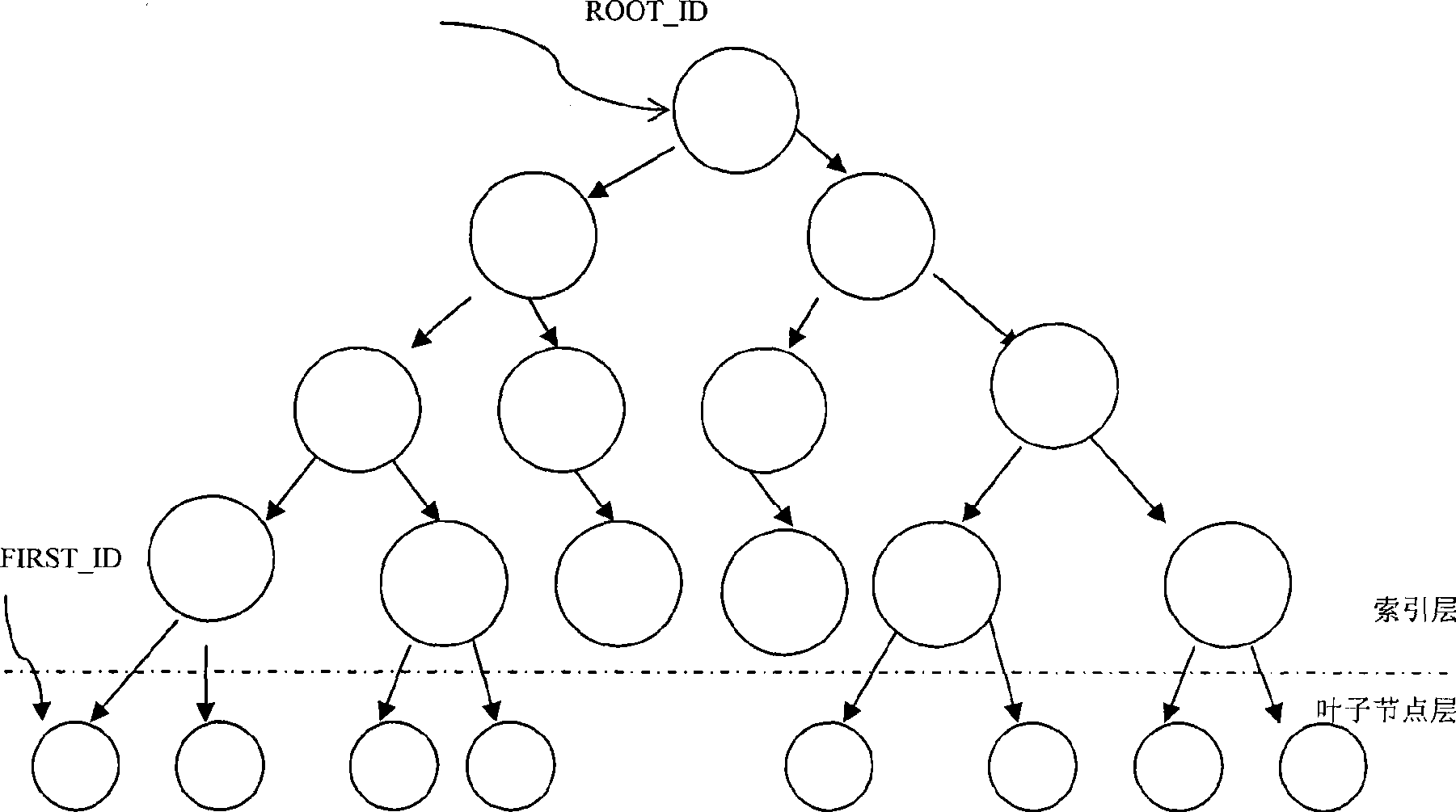
[0038] Assume there is a table T with fields: {F 1 , F 2 ,...,F i ,...,F n}. Field F in table T is required i Perform transparent encryption. f i The data type of is R, and this field has index I and constraint C, which needs to implement ciphertext index.
[0039] Step 1. Transform the original table T. The specific steps are as follows:
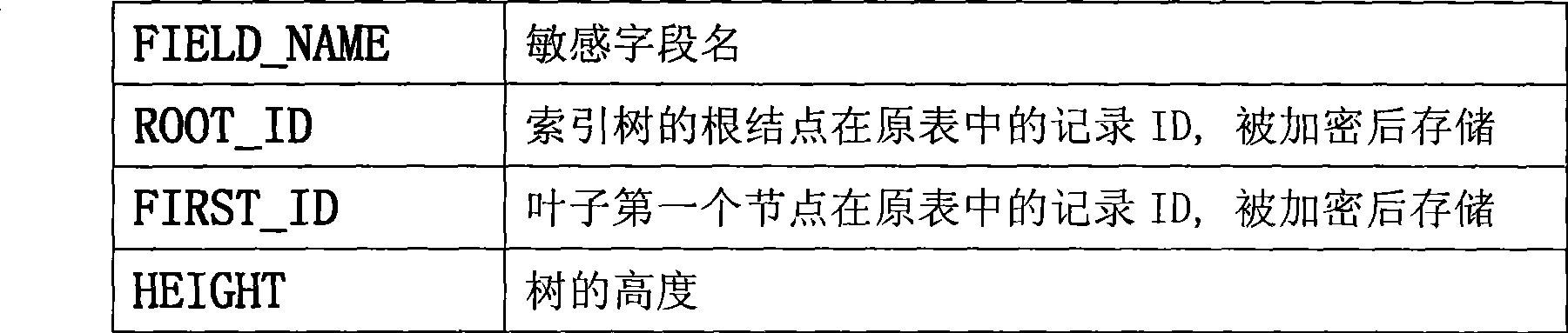
[0040] (1) Rename table T to T 1 , which contains fields: {F 1 , F 2 ,...,F i ,...,F n , F n+1}. Among them, F n+1 used to store field F i The ciphertext information, the type is RAW;
[0041] (2) delete F i Constraint C on
[0042] (3) delete F i index I on
[0043] (4) Call the encryption algorithm, and T 1 F in i Perform encryption transformation and store the ciphertext in F n+1 in, and set F i The value is set to NULL; it is the ciphertext field F n+1 Build an index data structure and insert the existing ciphertext into the structure.
[0044] The data structure and algorithm of the index use a balanced binary...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com