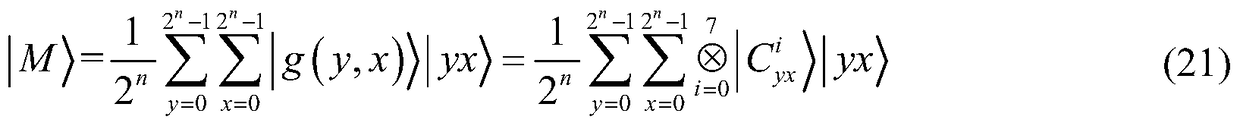A Quantum Image Encryption Method Based on Hyperchaotic System
A technology of quantum images and encryption methods, applied in the field of information security, can solve problems such as speed and cost constraints, and achieve the effects of enhancing anti-attack and security, resisting brute force attacks, and being easy to distribute
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The present invention will be further described below in conjunction with the embodiments and drawings, but the protection scope of the present invention should not be limited thereby.
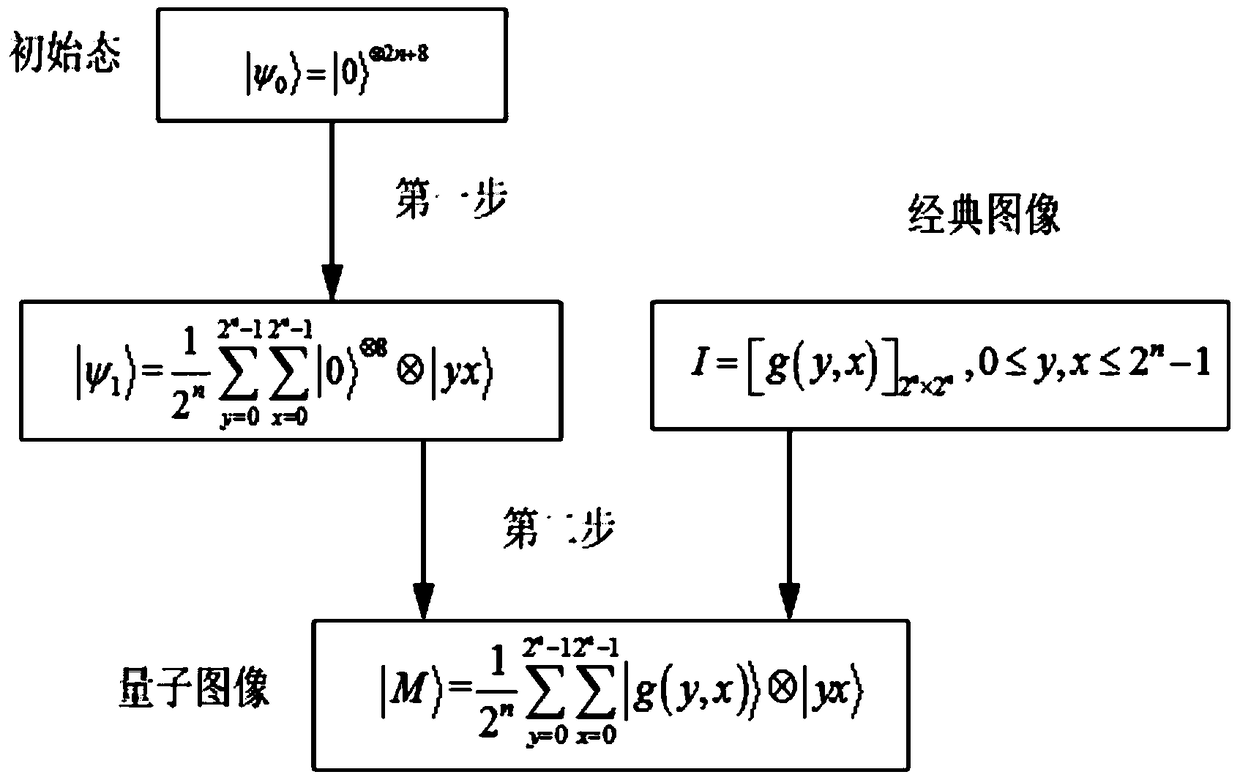
[0028] The encryption object of this implementation is the grayscale image stored in the quantum state, assuming that the plaintext quantum image is in g(y,x)∈[0,2 8 -1], the encryption algorithm steps are as follows:
[0029] Step 1: Choose the initial condition x 0 ,y 0 ,z 0 , h 0 , using the Runge-Kutta method with a step size of 0.001 to iterate the Chen hyperchaotic system n 0 = 2 2n times, four hyperchaotic sequences {x i}, {y i},{z i},{h i}(1≤i≤n 0 ).
[0030] Step 2: Put the four hyperchaotic sequences {x i}, {y i},{z i} and {h i} into the corresponding integer sequence {x i *}, {y i *},{z i *} and {h i *}.
[0031]
[0032] Where fix(x) represents the largest integer not greater than x.
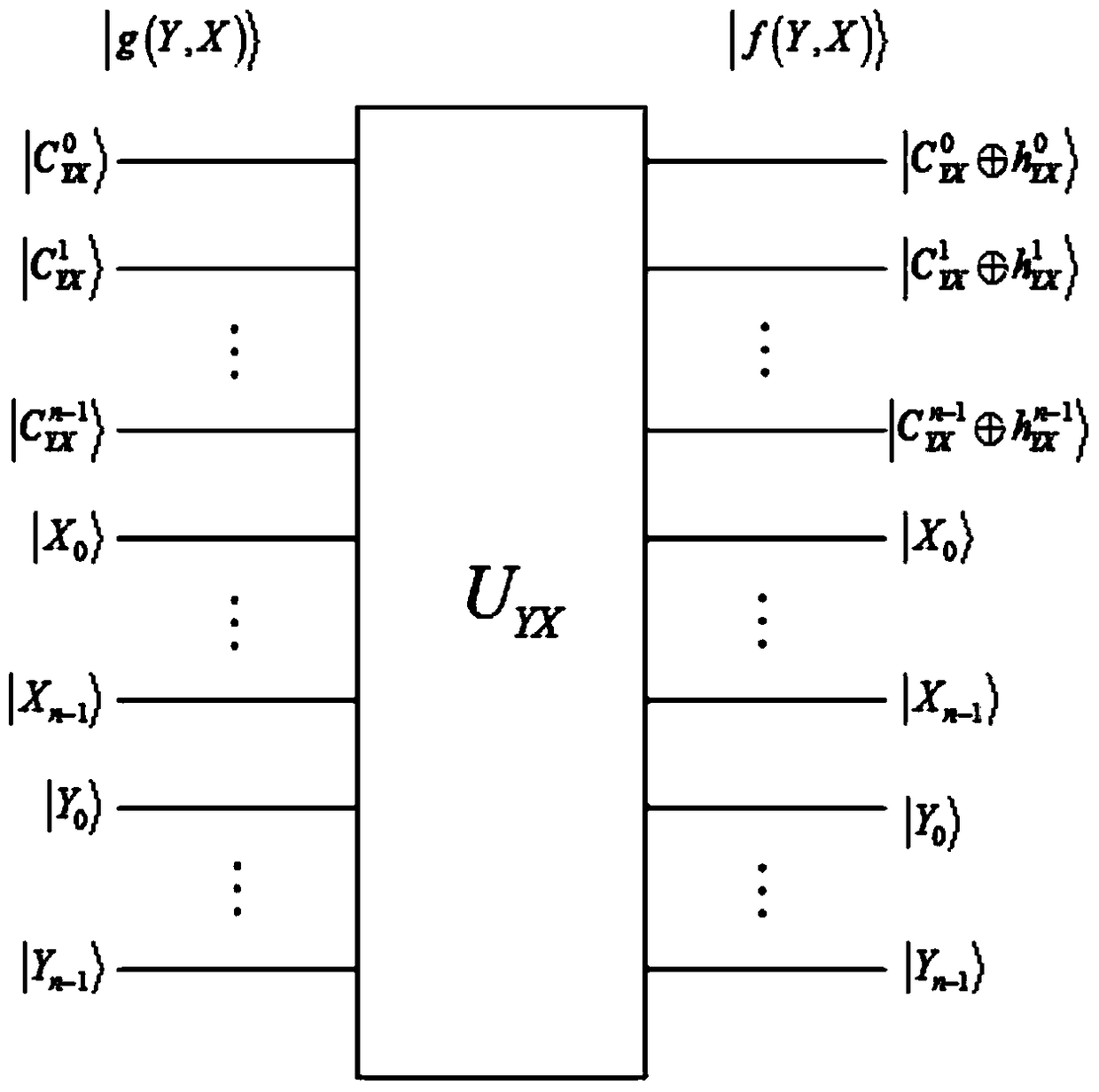
[0033] Step 3: In order to perform the quantum XOR operati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com