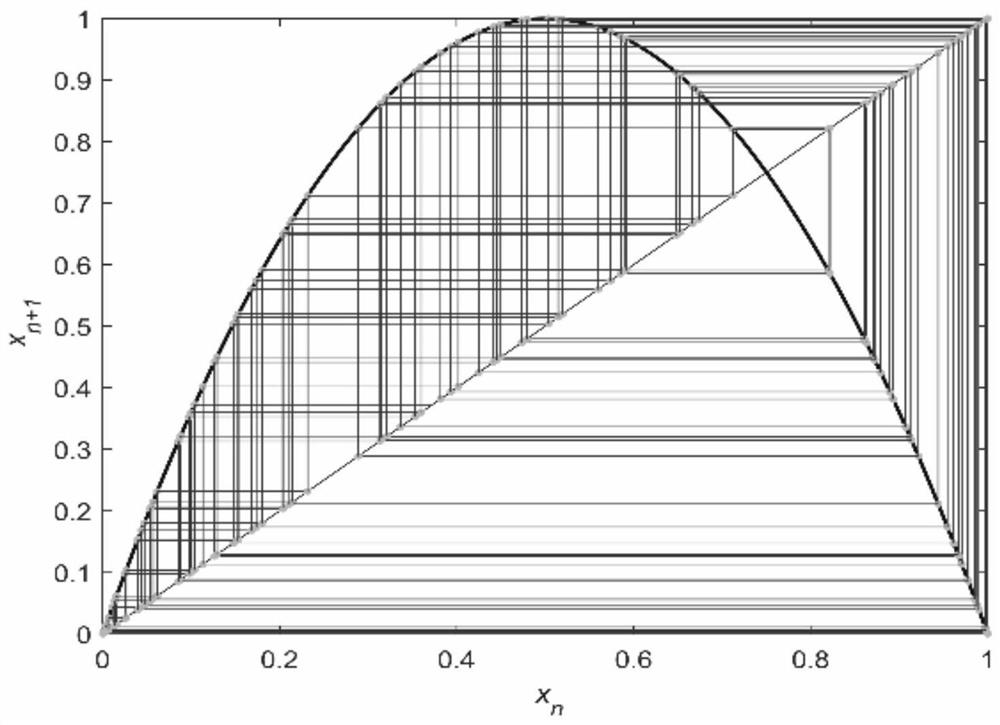
A fpga-based zuc encryption system ip core construction method
A construction method and encryption system technology, which is applied in the field of FPGA-based ZUC encryption system IP core construction, can solve the problems of leaving traces, reducing security and confidentiality performance, and being easy to be cracked, so as to resist exhaustive attacks and improve confidentiality The effect of performance and convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
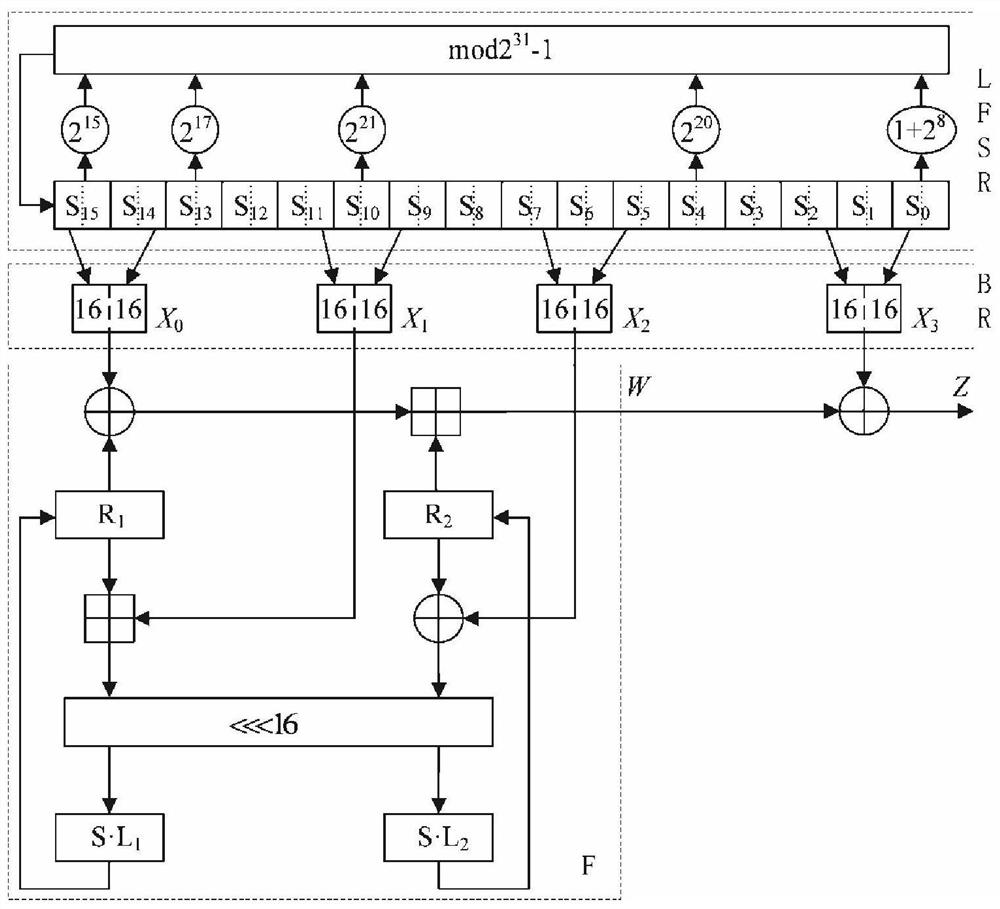
[0038] An IP core construction method for an FPGA-based ZUC and chaotic encryption system, the steps are as follows:
[0039] Step 1: The FPGA adopts the flow management mode, defines the top-level design, and determines the function of each module, as shown in the top-level signal list in Table 1;
[0040] Table 1 Top-level signal list
[0041]
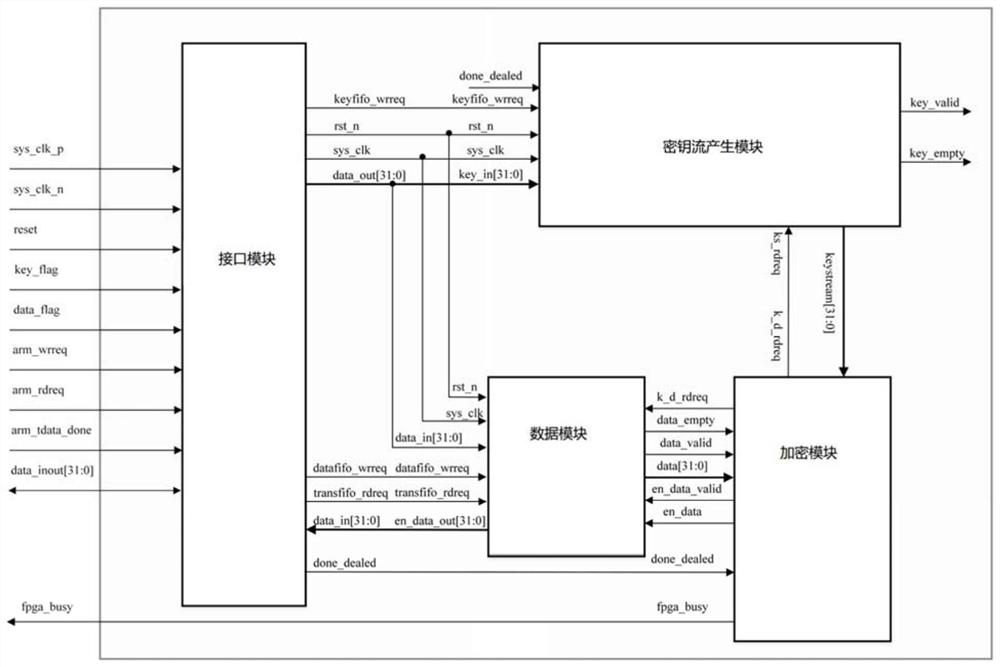
[0042] Step 2: Build an interface module, use the receiving FIFO memory and the transmitting FIFO memory to complete the control and conversion of the three-state gate, and receive data from the outside: including the key KEY and the data to be processed, and send the processed data; such as Figure 5 As shown, the module mainly has a phase-locked loop to generate the clock required by the system, the asynchronous reset and synchronous release module generates a global synchronous reset signal, and the function module collects the falling edge of the external signal to synchronize to the clock domain of the system. FIFO memory wr...
Embodiment 2
[0047] The working process of the encryption system is as follows. First, the key key is input externally, and the key flag signal is given. When the interface module detects that the key flag signal is high, it will send the received data to the key module, and the module will generate 1Mbit key stream, when the interface module detects that the data flag signal is high, it will send the received signal to the data module. When the encryption module detects the data completion signal, it means that the data transmission is completed, and the module will send the key to the key stream at the same time. The module and the data module send a read request signal, and the data and key enter the encryption module for encryption at the same time. At this time, the encryption module pulls the busy signal high, indicating that the FPGA is encrypting, and then writes the encrypted data to the data module and saves it. When all data encryption is completed, the busy signal will be pulled...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com