Multi-Image Encryption Method Based on Logarithmic Polar Coordinate Transformation
A logarithmic polar coordinate, encryption method technology, applied in the field of information security, can solve the problems of plaintext crosstalk, reduce the quality of restored images, etc., to achieve the effect of enhancing security, eliminating crosstalk, and resisting statistical attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The present invention will be further described below in conjunction with the embodiments and drawings, but the protection scope of the present invention should not be limited thereby.
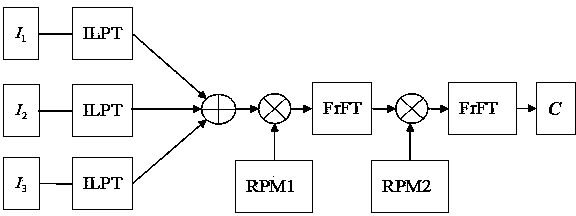
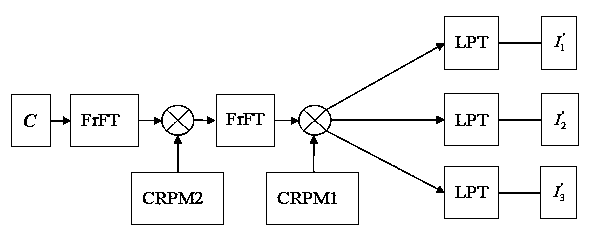
[0059] Step 1: Select three digital images as the images to be encrypted, namely Lena, Peppers and Baboon, grayscale images with a level of 255, and a size of 512*512 pixels. figure 1 is the specific process of encryption, where , , represent three images to be encrypted respectively, RPM1 and RPM2 are two random phase templates whose values are independently distributed in of white noise.
[0060] Step 2: Inversely transform the logarithmic polar coordinates of the three images respectively. In order to make the superimposed image after the transformation the same size as the original image, select an appropriate radius parameter. The maximum radius is selected as 255, and the size of the composite image is 511* 511. Let the first image radius parameter be selected as , th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com