Random blocking chaotic image encryption method
An encryption method and image technology, applied in the field of information security, can solve problems such as security risks, single encryption structure, and vulnerability to attacks, and achieve the effect of improving security and high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the drawings in the embodiments of the present invention.
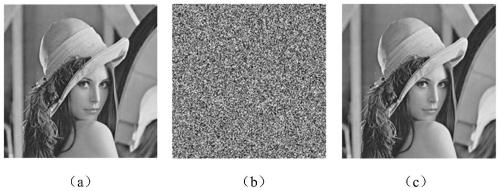
[0048] The invention discloses a chaotic image encryption method of random blocks, the steps of which are as follows:
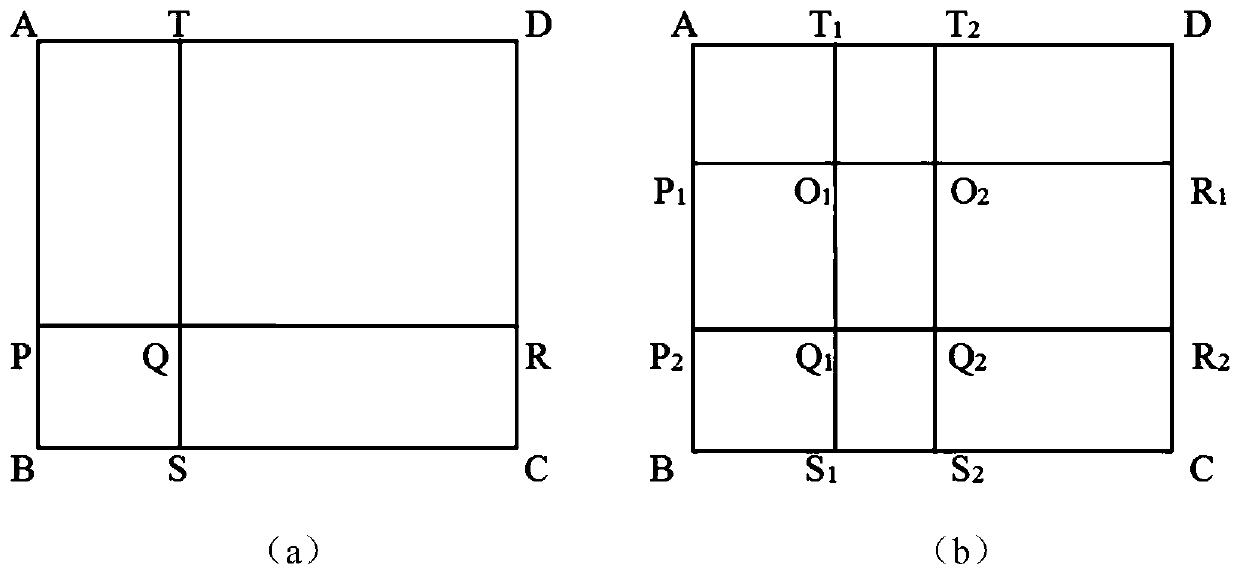
[0049] S1: Read the plaintext image A, set the size of the plaintext image A to be M×N, and a ij Represents the pixel in row i and column j in image A;
[0050] S2: Set keys x0, y0, z0, r and s0(1);
[0051] S3: Scramble the image:
[0052] S4: Decompose the replaced image into four sub-images A(1), A(2), A(3), A(4); swap the pixel values at (0,0) and (a,b); where the initial value is set to (x 0 +mean{A} / 256mod 1,y 0 +mean{A} / 256mod 1), where mean{A} represents the average of the sum of pixels in image A.
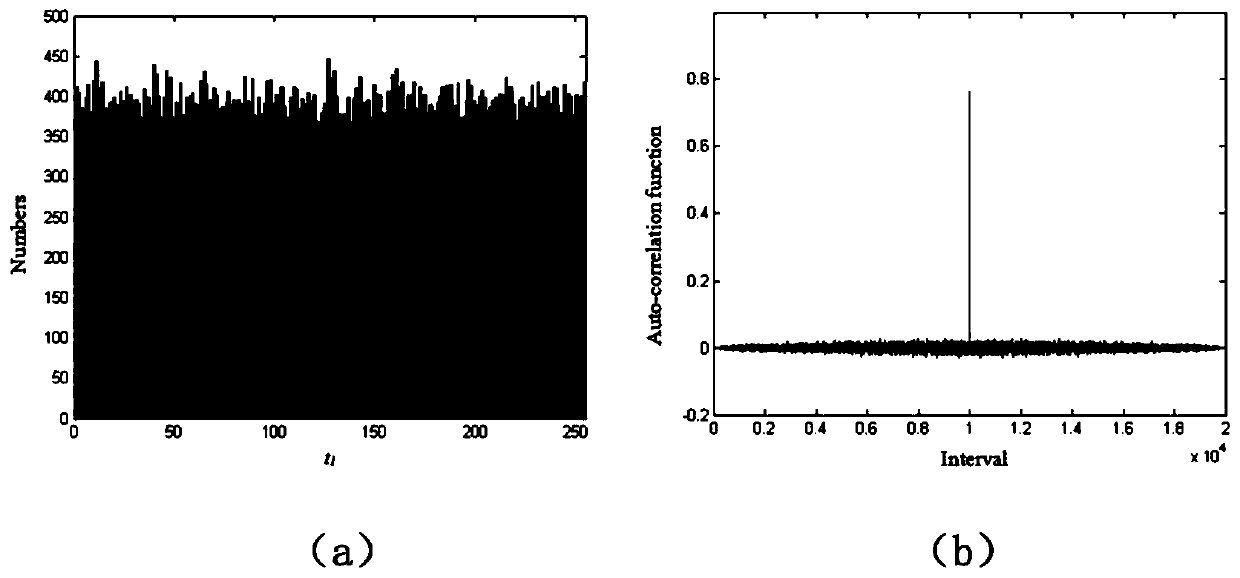
[0053] S5: Use the initial value z 0 +mean{A} / 256mod 1, according to Logistic mapping z i+1 =f(z i )=rz i (1-z i ) and m p =floor(z p 10 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com