Compressible six-dimensional non-degenerate hyperchaotic image secrecy system and method
A security method and hyper-chaotic technology, which are applied in secure communication through chaotic signals, transmission systems, image communication, etc., can solve the problems of image encryption algorithm, such as large computational load, low computational efficiency, low time series complexity, etc., to improve discrete speed, randomness, and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
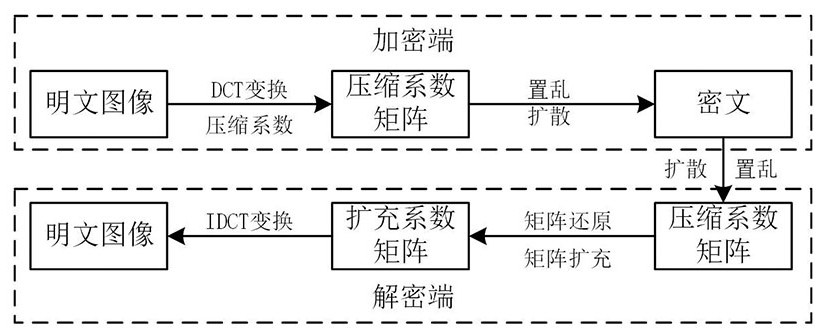
[0056] Specific implementation mode one: combine figure 1 To describe this embodiment, figure 1 It is a flow chart of system operation of the present invention. A compressible six-dimensional non-degenerate hyper-chaotic image security system, the plaintext image is subjected to DCT transformation at the encryption end to form a coefficient matrix, and the coefficient matrix is compressed to form a compression coefficient matrix; the compression coefficient matrix is scrambled and diffused. The ciphertext is formed; the decryption end diffuses and scrambles the ciphertext to obtain the decrypted compression matrix, and expands the decrypted compression matrix to the size of the original coefficient matrix with 0 and performs IDCT transformation to obtain the plaintext image.
specific Embodiment approach 2
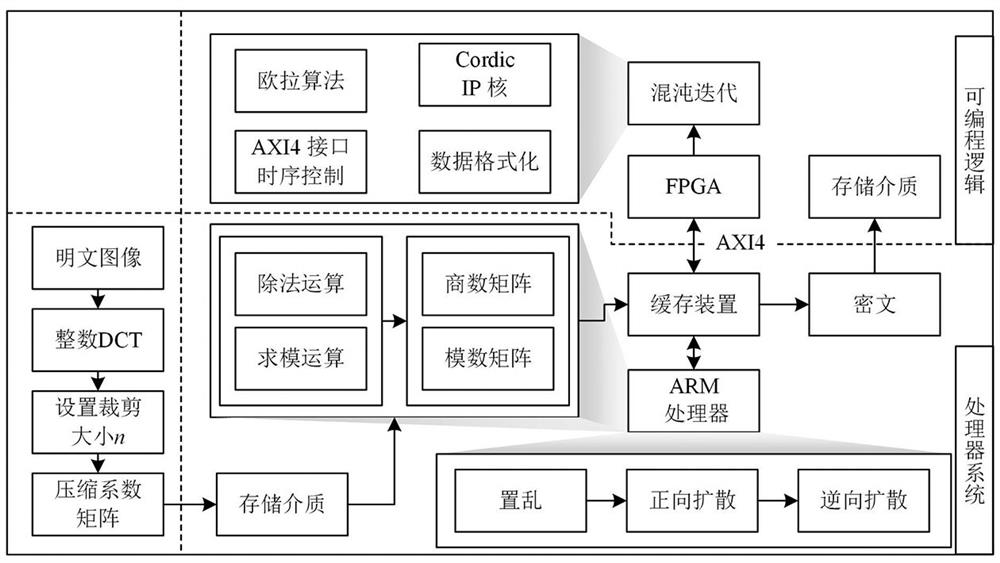
[0057] Specific implementation mode two: combination figure 2 To describe this embodiment, figure 2 It is a block diagram of hardware implementation of the encryption system of the present invention. The plaintext image is transformed by integer DCT to form a coefficient matrix, and the cropping size of each transform block coefficient matrix is set to n x m , before extracting each transform block coefficient matrix n Front row m The columns recombine the compression factor matrix, forming the size w' x h' The compression factor matrix. The ARM processor in the SOPC further processes the compression coefficient matrix into a quotient matrix and a modulus matrix, and stores them in the data cache device at the encryption end. The FPGA in the SOPC uses the 32-bit fixed-point Euler algorithm to discretize the hyper-chaotic system at the encrypted end, and the discretized results are stored in the data cache device at the encrypted end through the AXI4 (Advanced Extens...
specific Embodiment approach 3
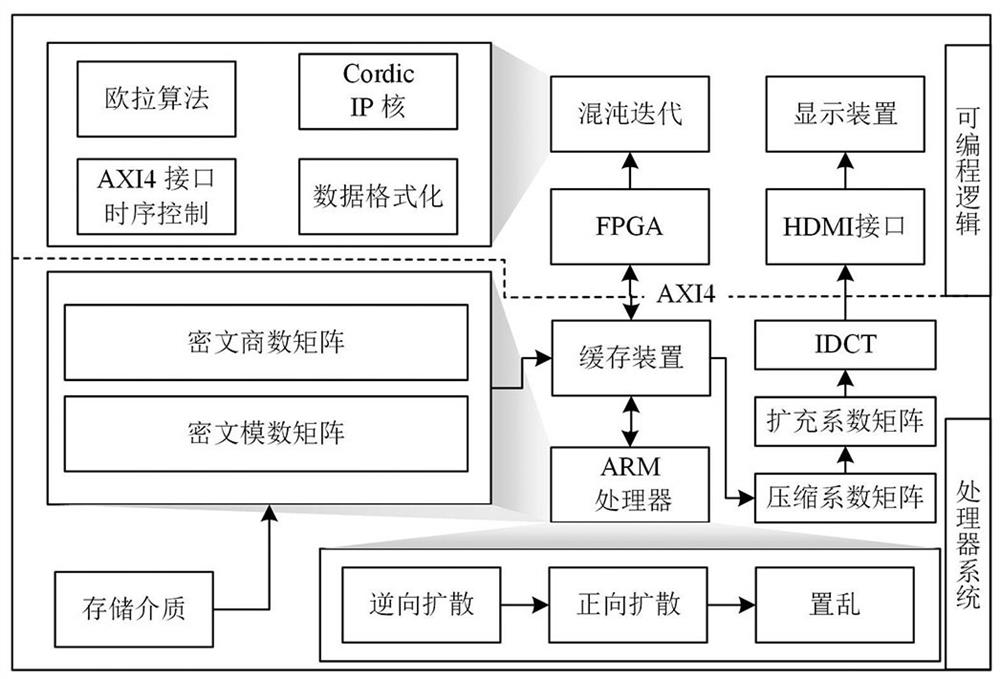
[0058] Specific implementation mode three: combination image 3 To describe this embodiment, image 3 It is a block diagram of hardware realization of the decryption system of the present invention. The ARM processor reads the ciphertext in the storage medium to the cache device, and the FPGA in the SOPC uses the 32-bit fixed-point Euler algorithm to discretize the hyper-chaotic system at the decryption end, and the discretized results pass through the AXI4 interface stored in cache. The ARM processor performs reverse diffusion, forward diffusion, and scrambling decryption operations on the ciphertext quotient matrix and ciphertext modulus matrix in combination with the hyperchaotic discretized sequence. The decrypted quotient matrix and modulus matrix are restored to a compression coefficient matrix, and the compression coefficient matrix of each transform block is expanded with 0 to a transform block expansion coefficient matrix with a size of 32×32. All transformation bl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com