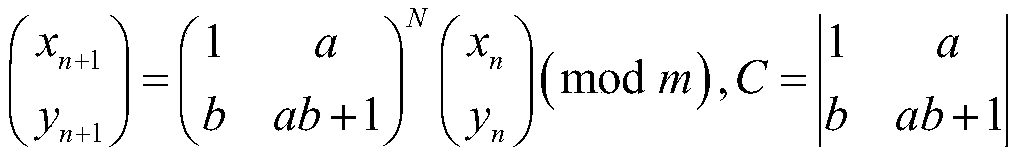Patents
Literature
30results about How to "Resistance to brute force attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Highly precise safe palm recognition method encrypted based on phase characteristic of Log-Gabor mixed filtering
InactiveCN101308542AAvoid the effects of identificationHigh expressionCharacter and pattern recognitionComputation complexityPrivacy protection
The invention discloses a high-precision security palmprint identification method based on 2D Log-Gabor mixed-phase characteristic encryption. The method adopts a 4-directional mixed 2D Log-Gabor mixed filter to filter the preprocessed palmprint images; then the method adopts a phase encoding way to extract the phase characteristics from the filtering result, and then carries out encryption operation to the extracted mixed-phase characteristics by a cipher sequence through XOR processing; finally, the two encrypted palmprint mixed-phase characteristics obtained after the encryption operation are matched through Hamming distance matching algorithm to obtain a matching result. The algorithm is less affected by acquisition light conditions; the encryption operation to the palmprint mixed-phase characteristics by a cipher sequence through XOR processing can increase the distance between classes without changing the inner-class distance, so as to improve the palmprint identification accuracy and reduce the computational complexity; besides, the user can protect the privacy protection by changing the cipher, so the system has high security.
Owner:SOUTHWEST JIAOTONG UNIV
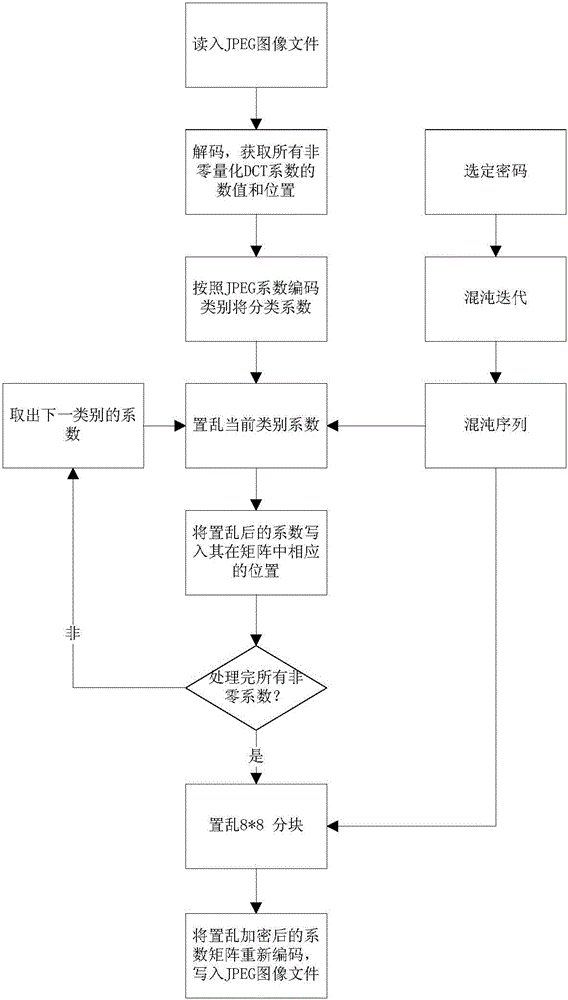
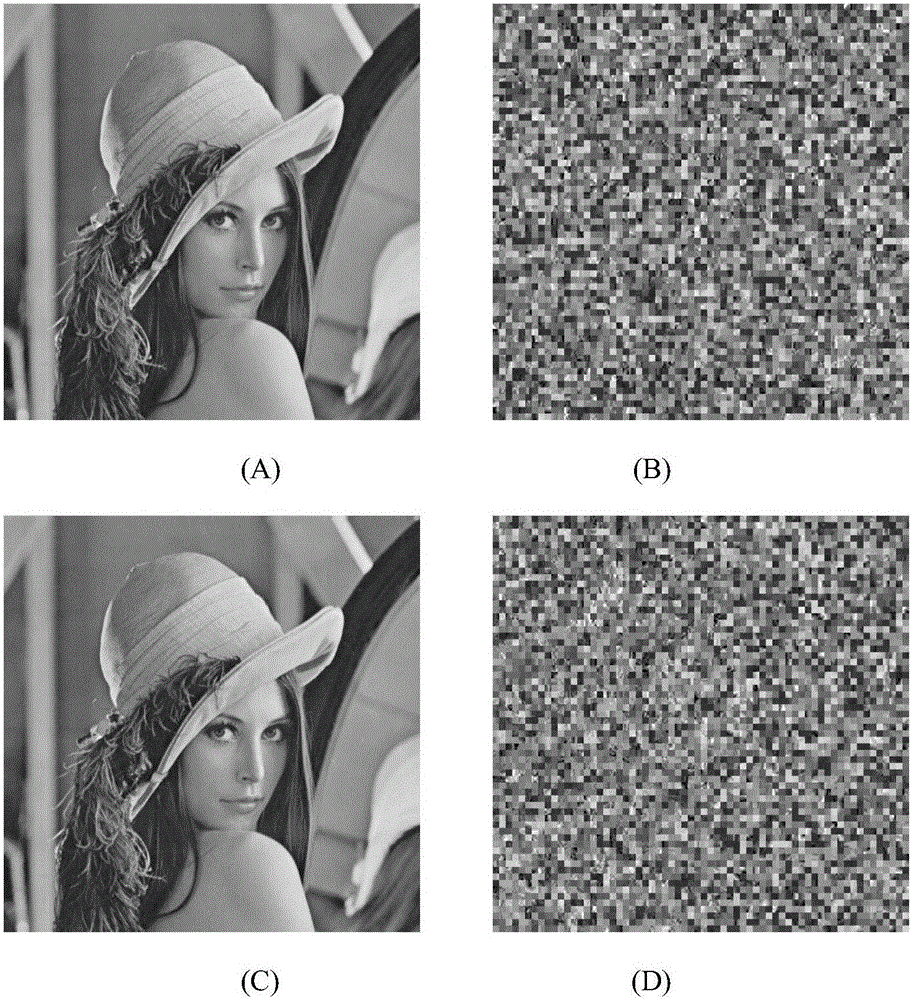
Intra-class coefficient scrambling-based JPEG image encryption method
InactiveCN105975866AIncrease the compression ratioExpand the key spaceImage codingDigital data protectionPlaintextAc coefficient
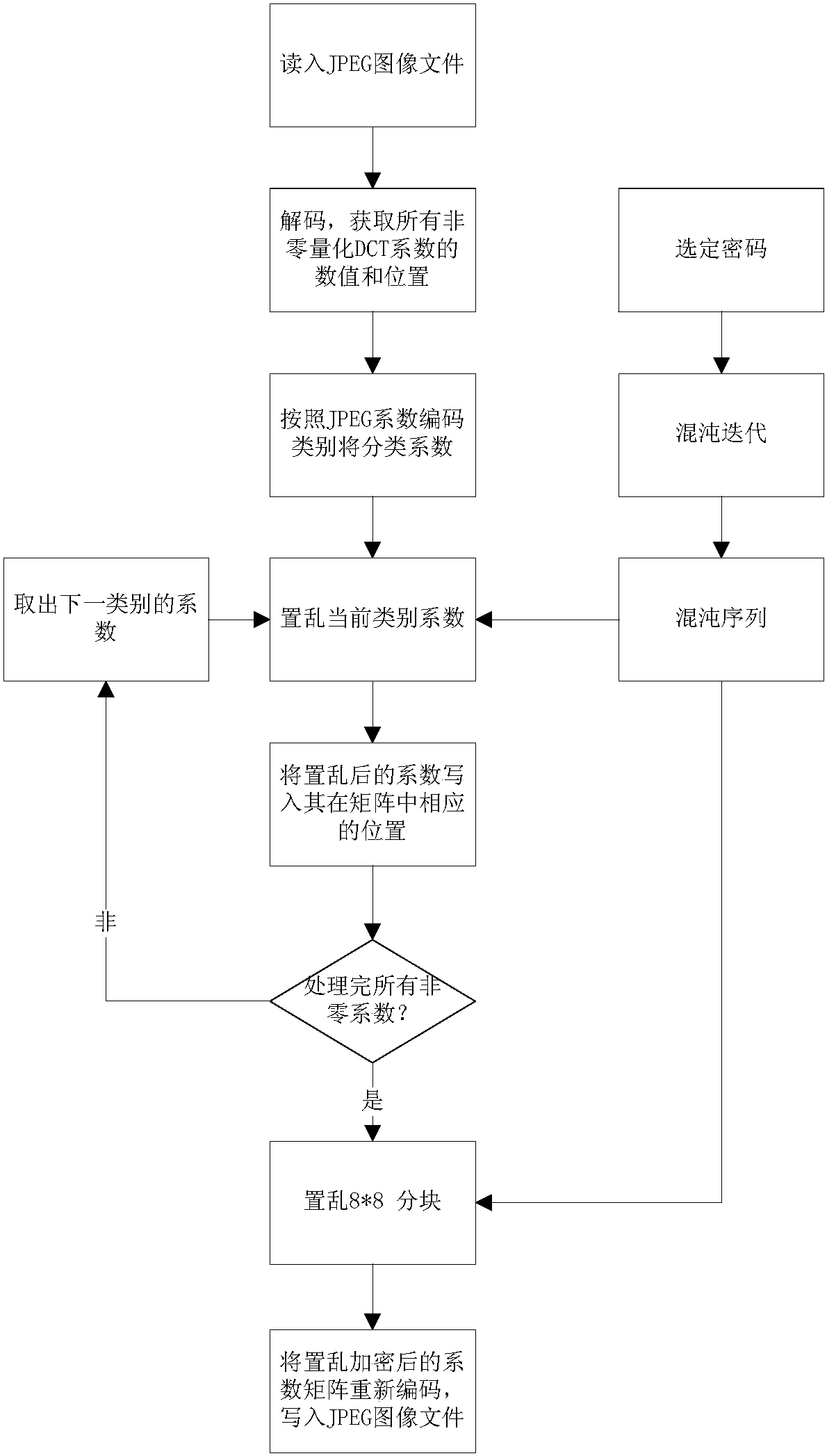
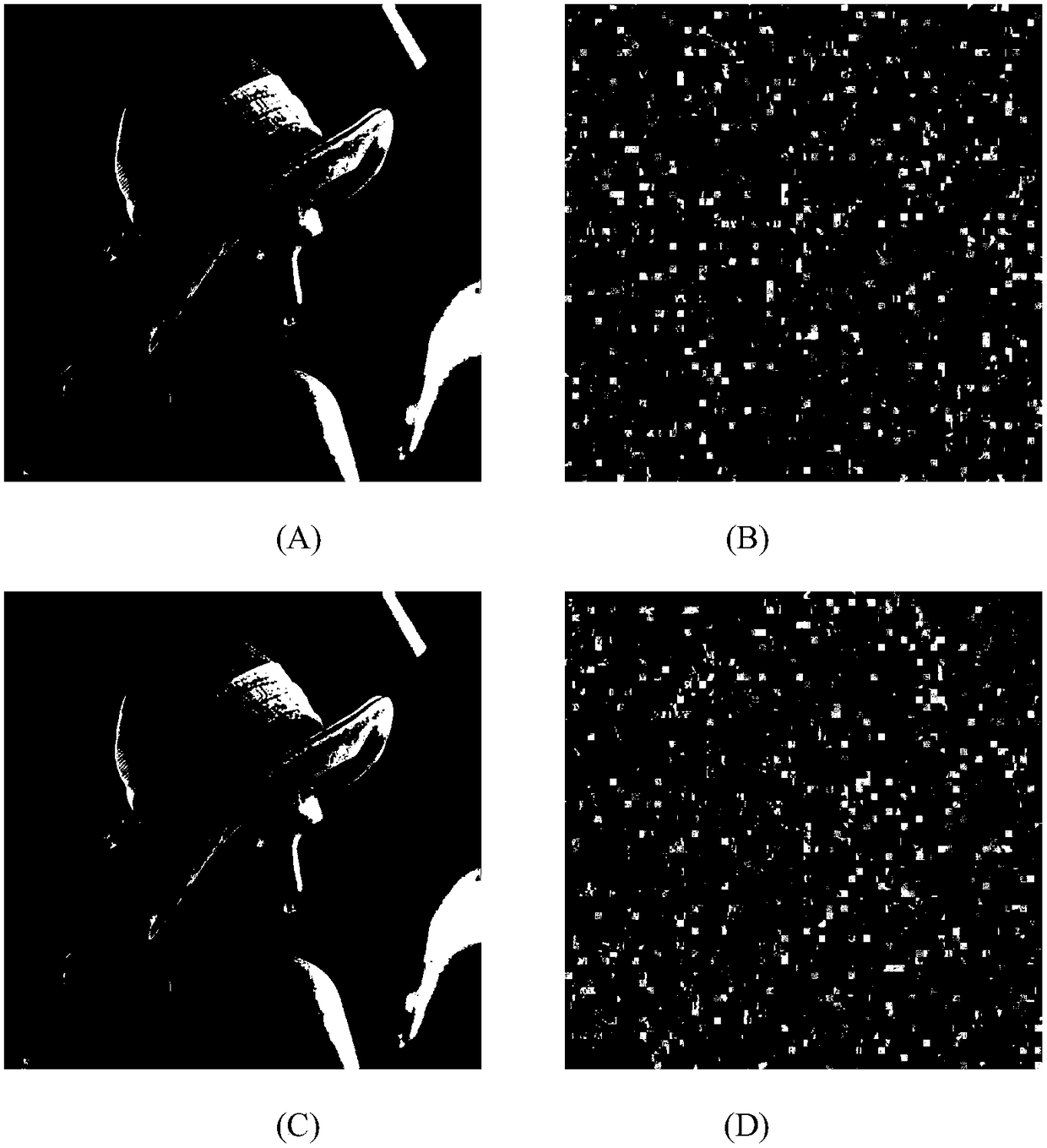
The invention relates to an intra-class coefficient scrambling-based JPEG image encryption method. The method comprises the following steps: firstly reading in a JPEG image file, acquiring a Huffman coding table and image data which undergoes JPEG coding compression, carrying out decoding to acquire all the non-zero quantized DCT coefficient numerical values and positions and carrying out classification; selecting a password, carrying out chaotic iteration by utilizing the password, so as to generate a chaotic sequence, and scrambling the non-zero coefficients and 8*8 block of each class by utilizing the chaotic sequence; and carrying out entropy coding on a scrambled quantized DCT coefficient matrix, and writing the coded data into the JPEG image file so as to complete intra-class coefficient scrambling-based JPEG image encryption. According to the method disclosed in the invention, scrambling is carried out on different classes of quantized DCT coefficients through the chaotic sequence, and the quantized DC coefficients and the non-zero AC coefficients are processed by directly using one encryption scheme, so that the safety and the high efficiency are both considered; and the encrypted images are similar to clear text image files in the aspect of size, and have high compression ratios.
Owner:CHANGAN UNIV
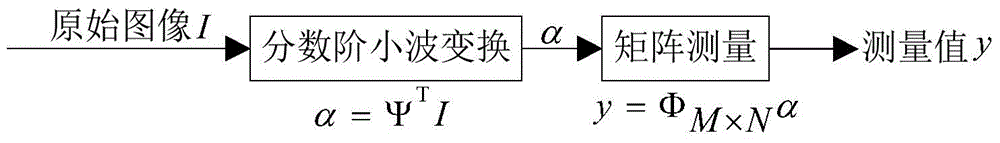
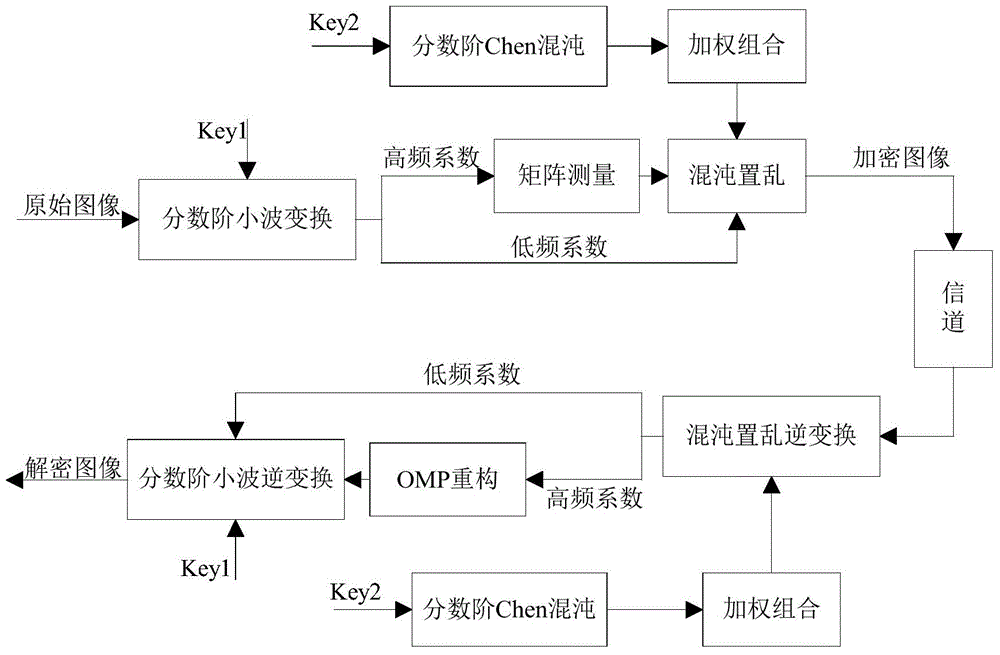
Image compression sensing and image encrypting method based on sparse matrix control
InactiveCN104463765AImprove scrambling effectImprove securityImage data processing detailsImage transferCiphertext
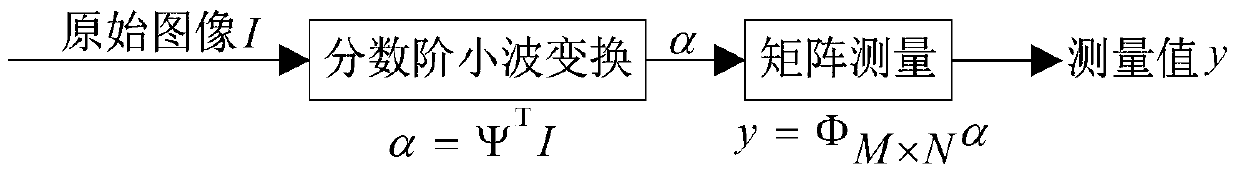
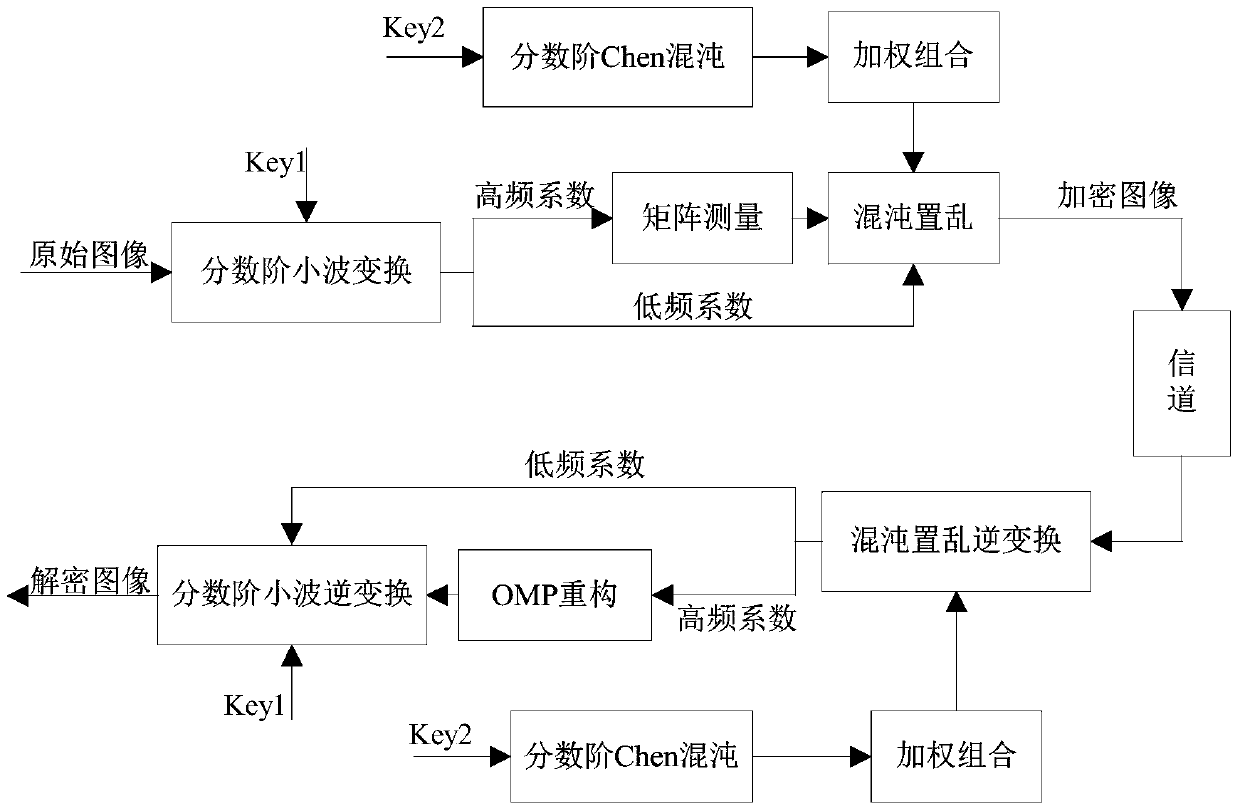
The invention provides an image compression sensing and image encrypting method based on sparse matrix control. An order is used as a secret key for controlling generation of a fraction wavelet transformation sparse matrix, and then the sparse matrix is used for carrying out sparse expression for an image to obtain a low-frequency coefficient matrix and a high-frequency coefficient matrix of the image; measurement matrixes of the number of corresponding measurement times are constructed according to the sparseness of the coefficient matrixes, and sparse coefficients are measured to obtain a compressed and encrypted image. In order to improve the safety of an encryption algorithm, fraction Chen chaos sequences of a weighted array are used for scrambling measurement values to obtain a ciphertext. The fraction wavelet transformation and fraction Chen chaos scrambling are combined, and the non-linear characteristic of the fraction order property and the fraction chaos sequences is fully utilized. The image is encrypted while being compressed, the difficulty of the large data size when the image is transmitted can be effectively overcome, and image information leakage is prevented.
Owner:NANCHANG UNIV
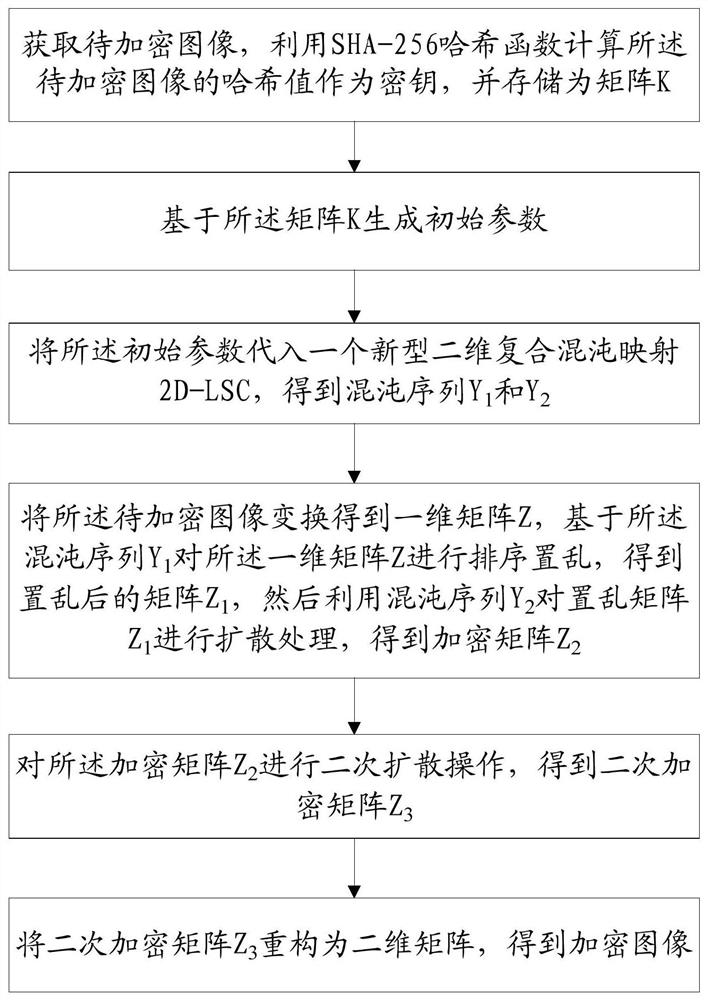
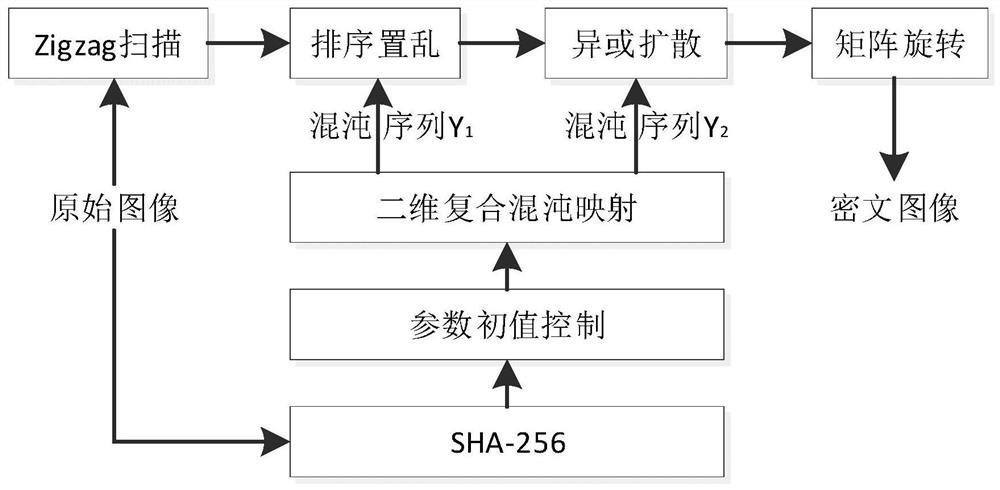
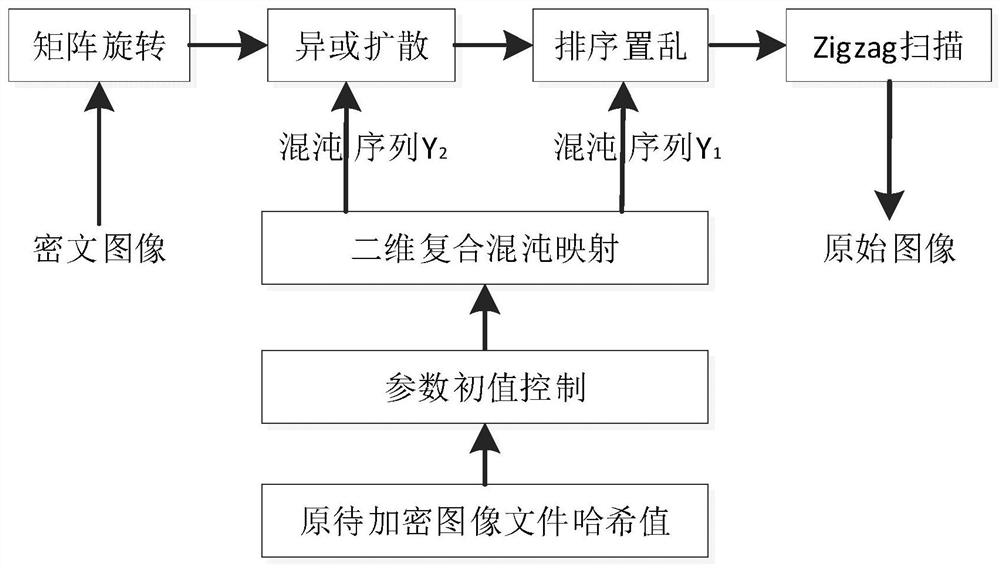
Image encryption method and device based on novel two-dimensional composite chaotic mapping and SHA-256
ActiveCN113538203ALow cost of executionIncreased complexityDigital data protectionImage data processing detailsKey spaceHash function
The invention provides an image encryption method based on novel two-dimensional composite chaotic mapping and SHA-256. The method comprises the following steps: calculating a Hash value of a to-be-encrypted image by using an SHA-256 Hash function, and taking the Hash value as a system input key; linking plaintext image information and the whole image encryption process closely by using the one-way irreversible characteristic of Hash calculation, therefore, the algorithm key space is expanded, and violent attacks of attackers can be effectively resisted; carrying out blocking and operation on the hash value to obtain an iterative initial parameter of the composite chaotic system; substituting into a composite chaotic system for iteration and processing to generate a chaotic sequence; converting the to-be-encrypted image into a one-dimensional matrix; sorting and scrambling the original image based on the chaotic sequence; performing primary diffusion processing on the matrix based on the chaos sequence to obtain an encrypted matrix; performing secondary diffusion processing on the encryption matrix through a parameter generated by a key to obtain a secondary encryption matrix; and finally, reconstructing to obtain an encrypted image. According to the invention, the security of image encryption is improved, and the execution cost is reduced.
Owner:HUAQIAO UNIVERSITY +1
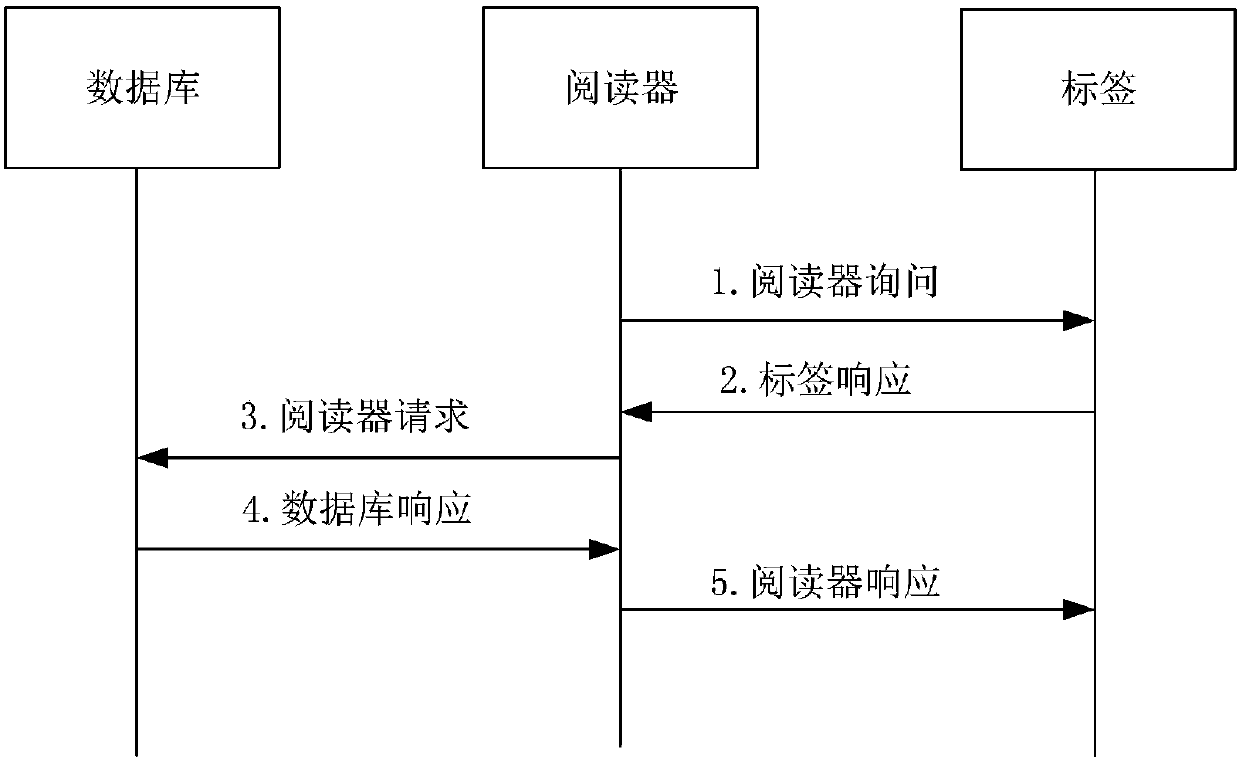
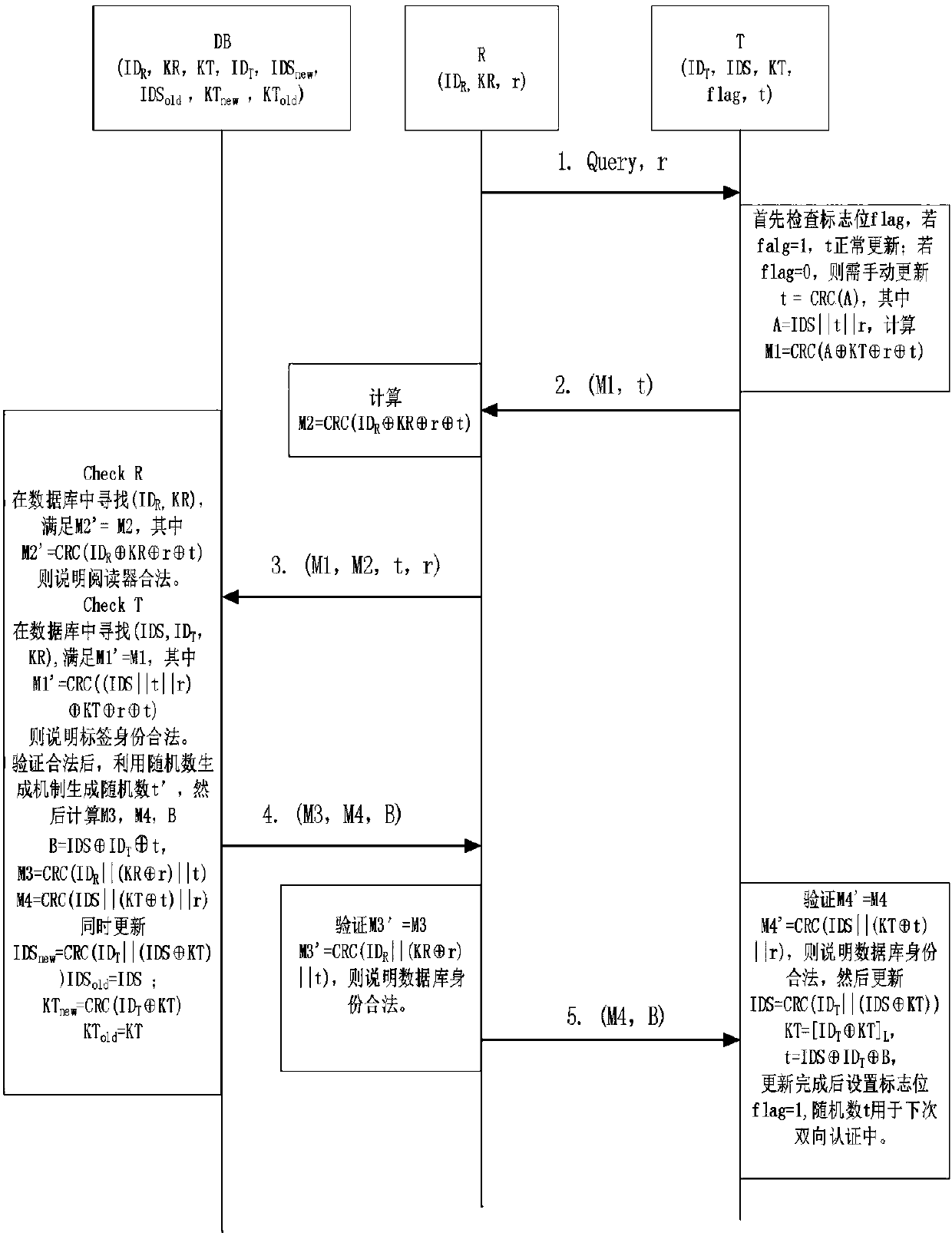
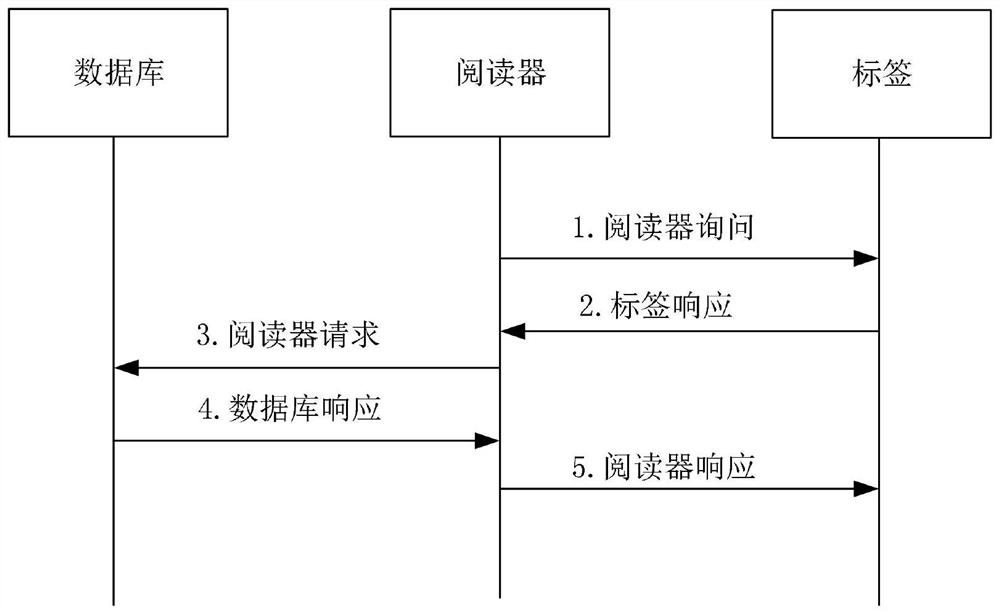
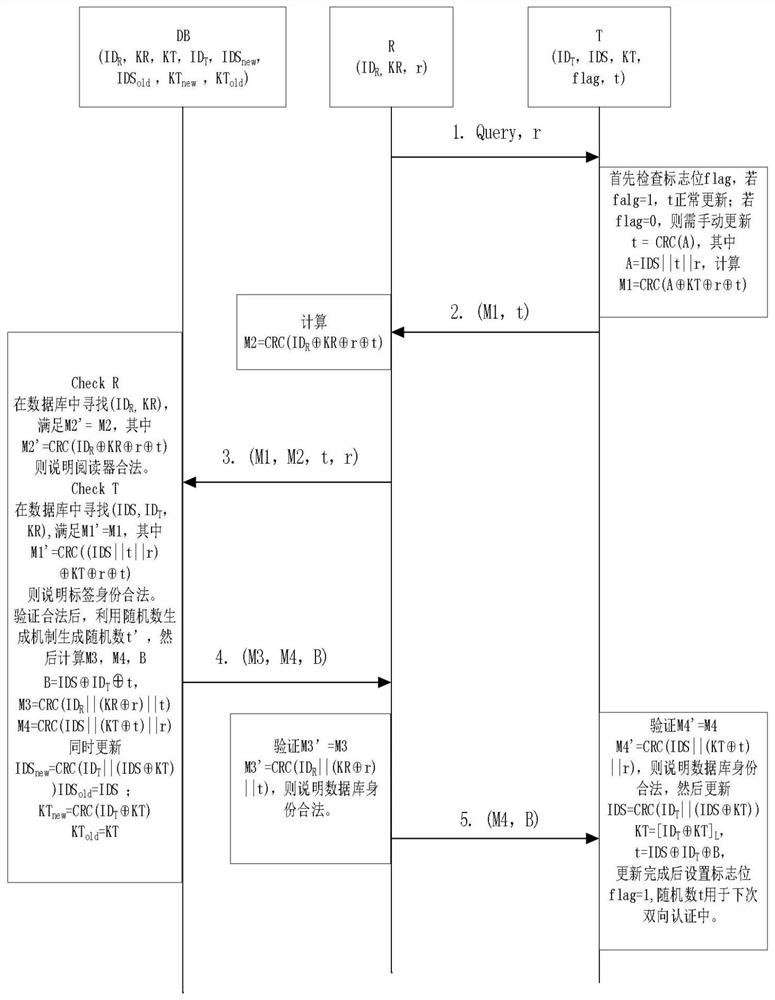
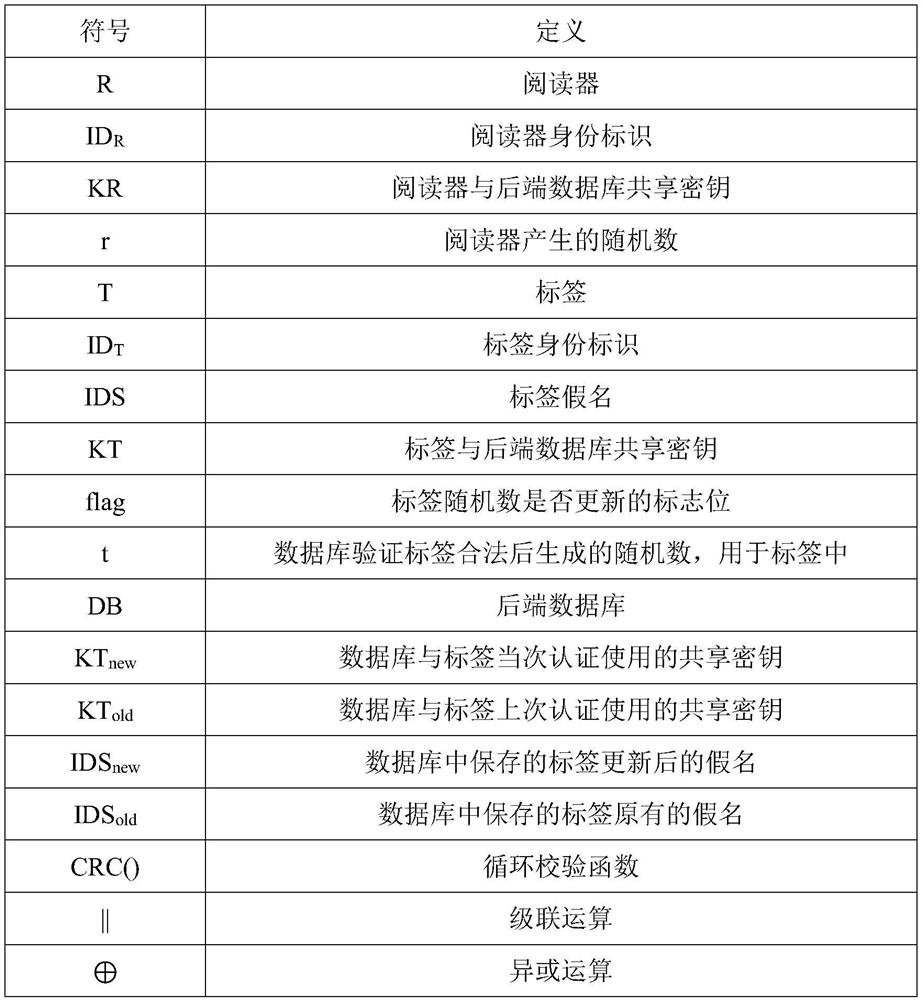
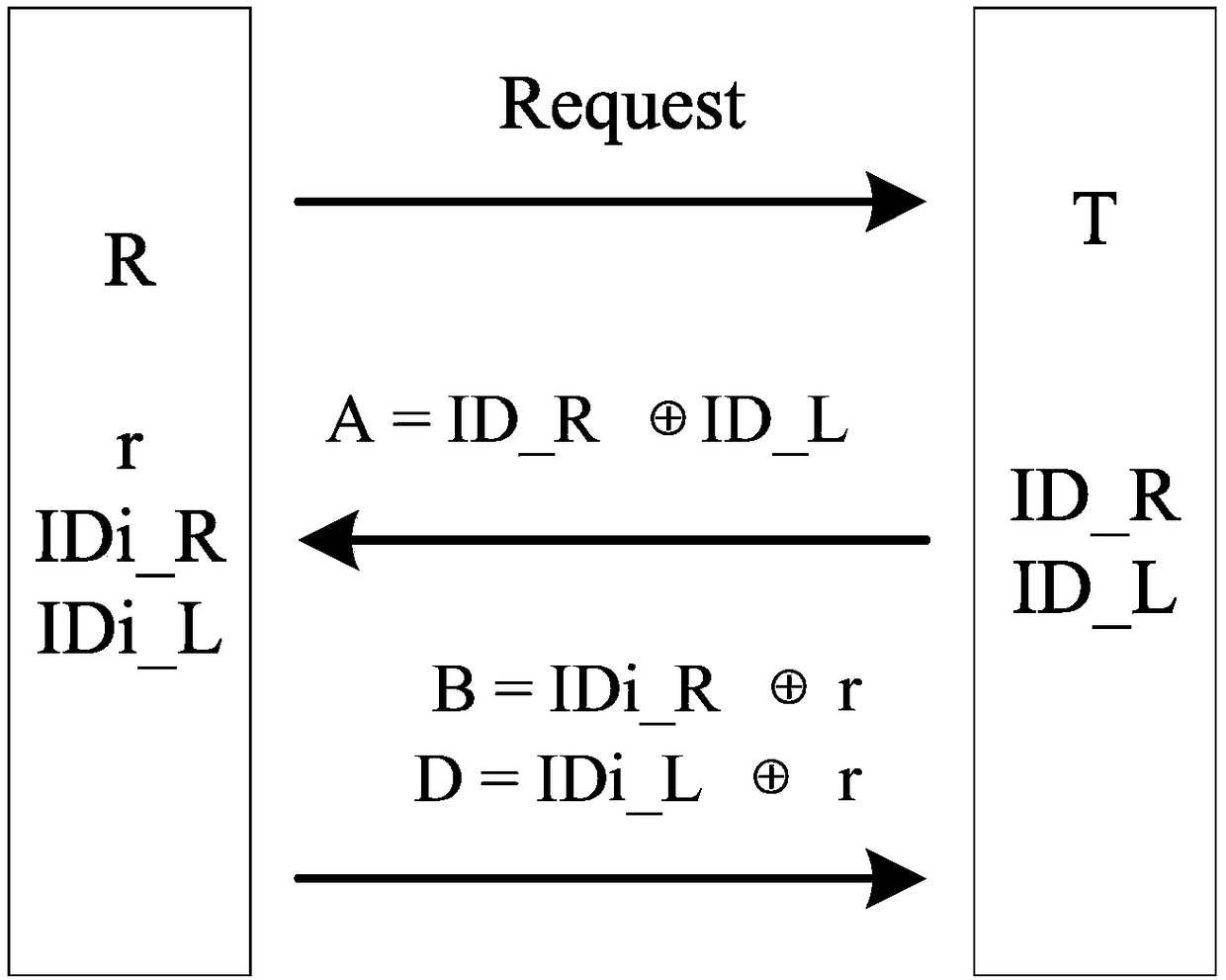
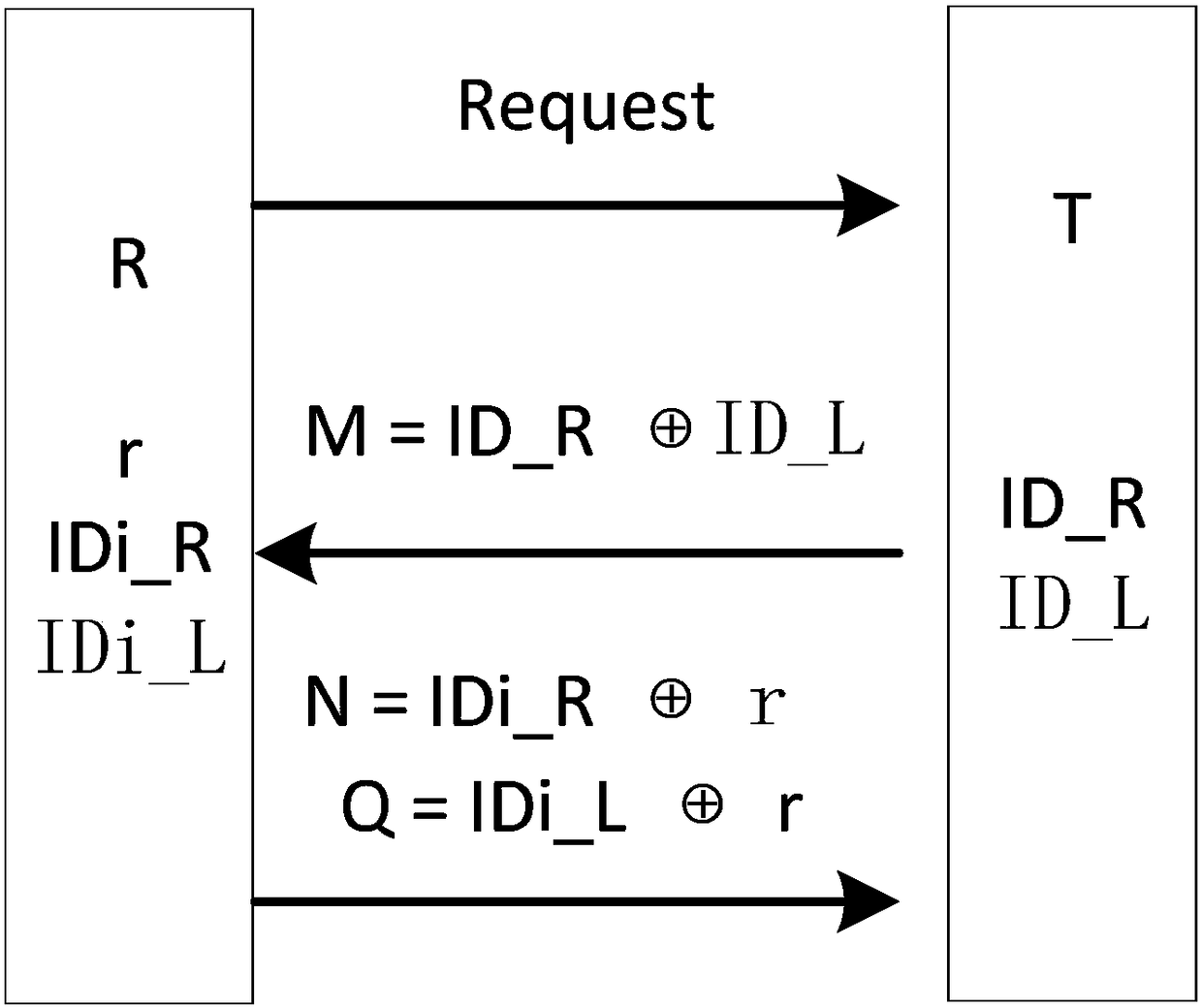
Bidirectional authentication method for ultra-lightweight mobile RFID system
ActiveCN108304902AReduce hardware costsSmall amount of calculationKey distribution for secure communicationCo-operative working arrangementsExclusive orSecure authentication
The invention relates to the technical field of communication, and particularly relates to the safety certification problem among a tag, a reader and a back-end database in a mobile RFID system. The method comprises the following steps: (1) the reader sends the request information to the tag; (2) the reader sends the tag response request information and the own information to the database; (3) thedatabase authenticates the reader and the tag; (4) the reader authenticates the database; (5) the tag authenticates the database. According to the invention, the protocol of the system adopts a cyclic checking function and a simple exclusive-or and cascade algorithm to encrypt the to-be-transmitted information. In this way, the anonymity of the tag and the bidirectional authentication of the system are realized. Meanwhile, the calculation amount of the database and the tag is effectively reduced. A tag random number is generated by a back-end database random number generation mechanism and then is forwarded to the tag or automatically updated through the cyclic checking function. Therefore, the hardware cost of the tag is reduced. According to the invention, a dynamic ID and a cyclic checking function mechanism are utilized, so that the system can resist various attacks.
Owner:XIDIAN UNIV
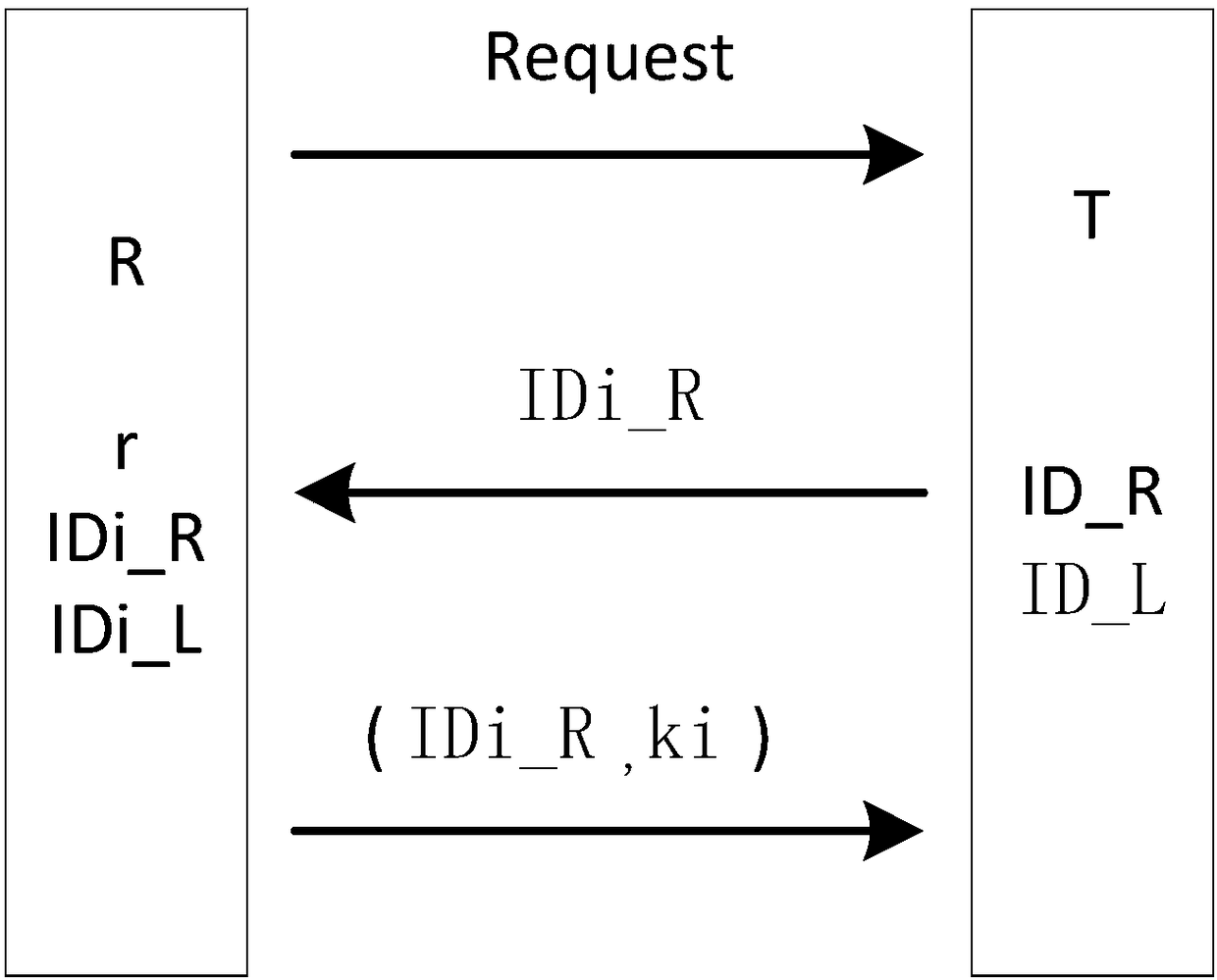
RFID system secret key generation method and devices based on tag ID
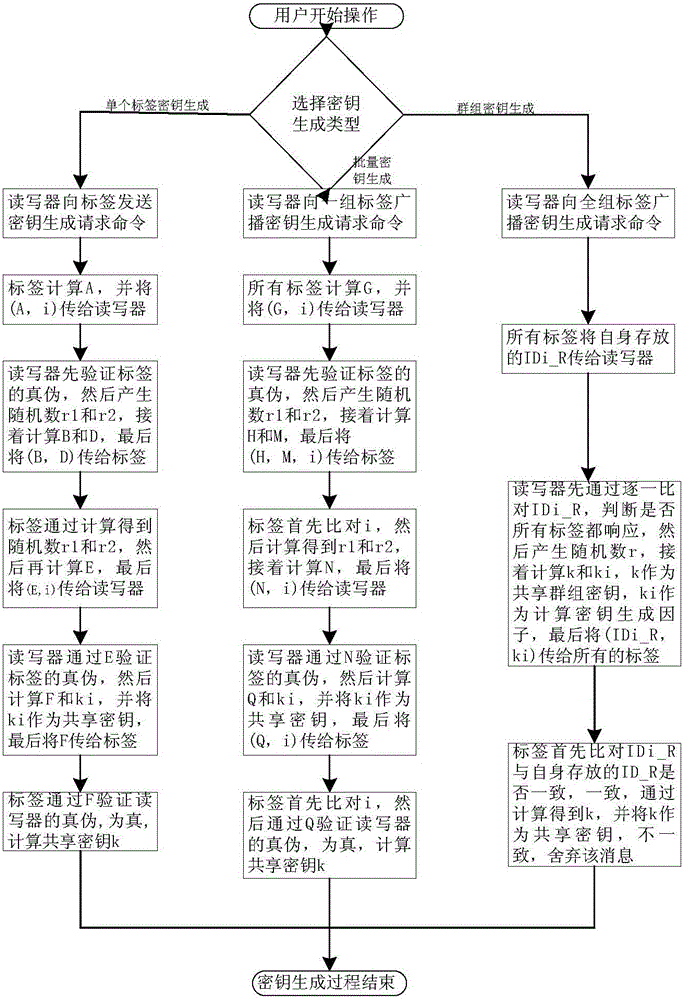
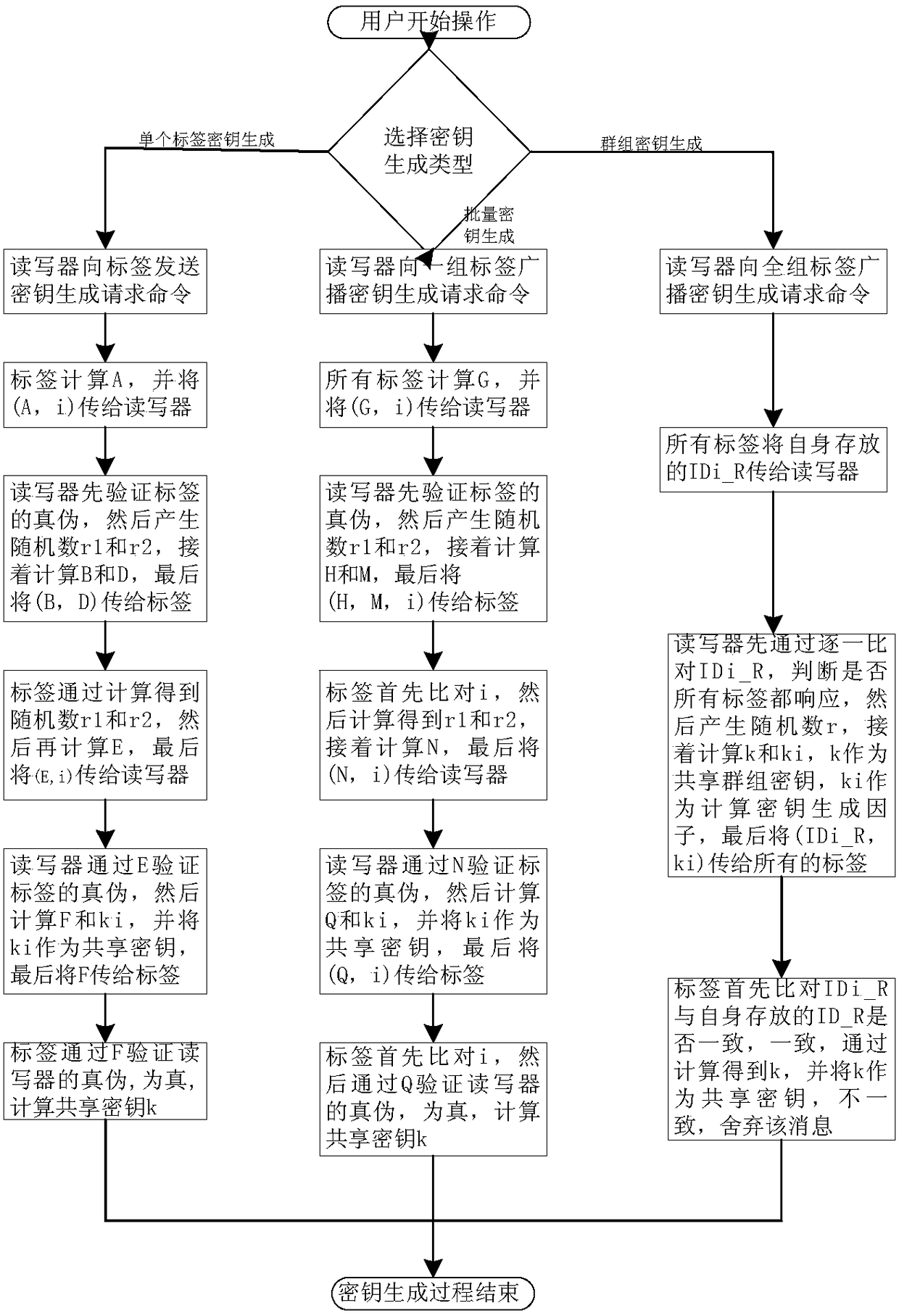
ActiveCN105721142ASolve potential safety hazardsSmall amount of calculationKey distribution for secure communicationNear-field in RFIDReader writerKey generation
The invention discloses an RFID system secret key generation method and devices based on tag ID. The method comprises the steps that firstly, a reader-writer determines to generate a secret key / secret keys for a tag or a batch of tags or a group of tags, determines the types of the generated secret keys and then sends a secret key generation request command to each tag, each tag feeds back corresponding information of the corresponding tag ID according to type difference, and the reader-writer and each tag generate a secret key shared by the reader-writer and the tag through certain calculation according to the information of the corresponding tag ID. By means of the secret keys, subsequent bidirectional authentication can be conducted. Based on all the types, the three types of secret key generation devices are specifically disclosed. By means of the method, read-write security of an RFID system is improved, the calculated amount at each tag end is greatly reduced, and tag cost is lowered.
Owner:GUANGDONG UNIV OF TECH
Biometric key extraction method based on fingerprint bit string and error correction coding
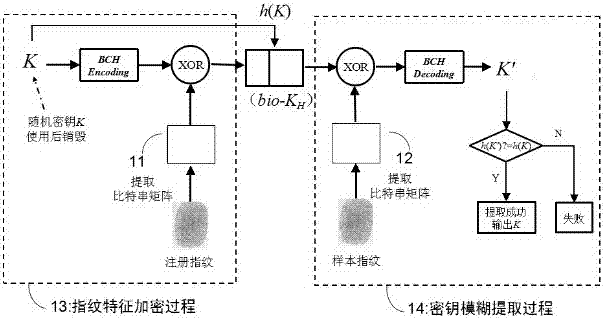
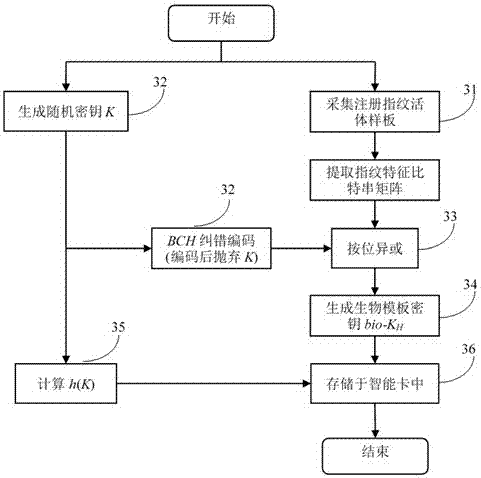
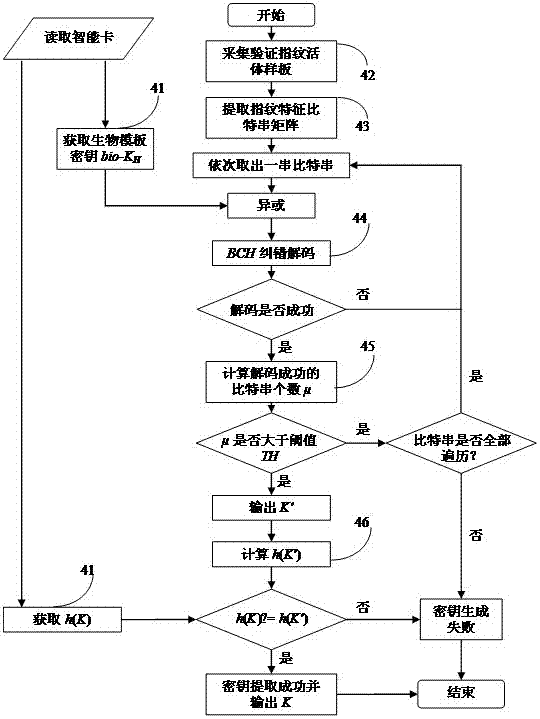
InactiveCN106936586AProtect fingerprint privacy informationResistance to brute force attacksKey distribution for secure communicationUser identity/authority verificationComputer hardwareRejection rate
The invention provides a biometric key extraction method based on a fingerprint bit string and error correction coding. The biometric key extraction method based on the fingerprint bit string and the error correction coding comprises the following steps: designing an irreversible and changeable variable function or parameter based on the fingerprint bit string and the error correction coding algorithm to transform the original biological features; transforming the original template into a conversion template; and generating a biological feature revocable template. According to the invention, the problem of automatic registration between the registration template and the verification template in the transform domain is solved by means of fuzzy extraction, therefore, the rejection rate of the biological authentication is low, and the availability of the authentication scheme is ensured. The invention takes the fuzzy extraction technology as the main line and combines the error correction coding technology to extract the unique and stable key from the fingerprint images with certain randomness and fuzziness, and any step does not need to store original fingerprint information, therefore, the user fingerprint privacy information can be maximally protected while realizing the fingerprint feature encryption; the biometric key extraction method based on the fingerprint bit string and error correction coding can resist the brute force attack, the tampering / intercepting template database attack and the multi template cross matching attack based on ARM homologous fingerprints.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Color image encryption and hiding method based on PT-LCT and DWT-SVD
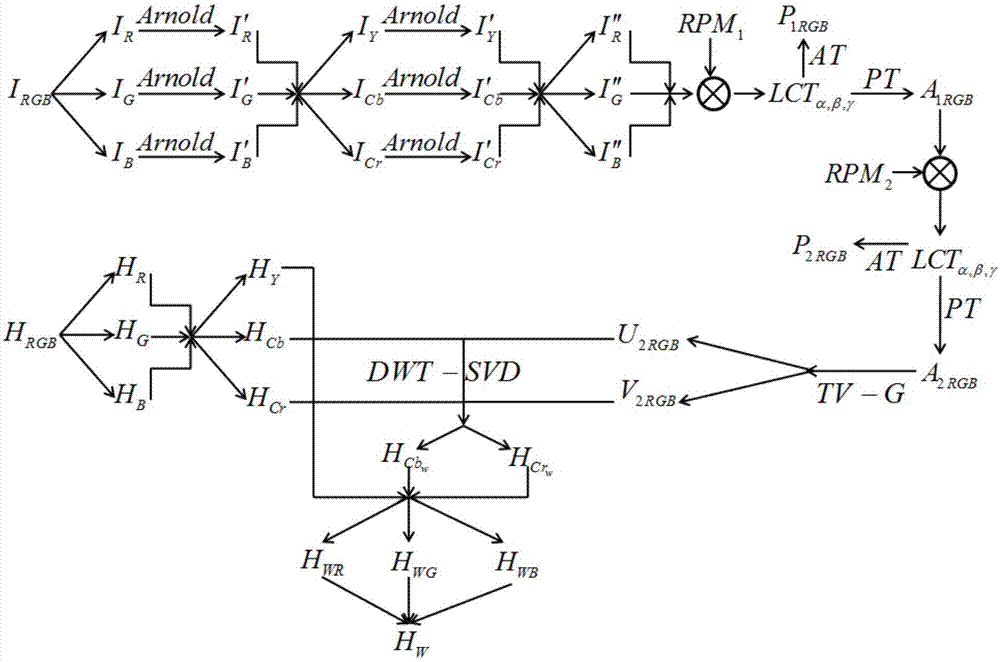
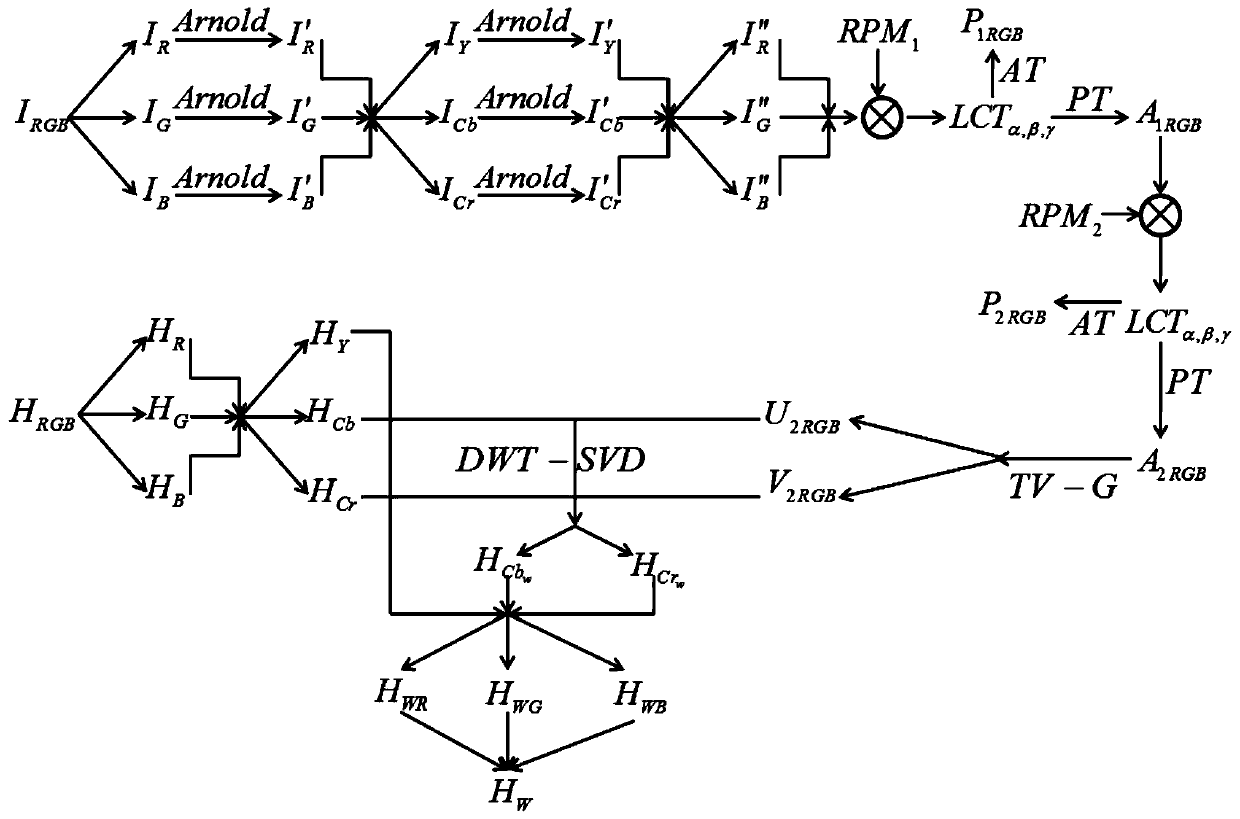
InactiveCN107516332ARobustResistance to brute force attacksImage codingDigital video signal modificationSingular value decompositionInformation processing
The invention relates to the information safety and light information processing technology field and provides a color image encryption and hiding method based on PT-LCT and discrete wavelet transform-singular value decomposition (DWT-SVD). Finally, a color carrier image including a secret image is acquired. The color image encryption and hiding method based on PT-LCT and DWT-SVD is characterized by firstly, encrypting a color image to be hidden through Arnold scrambling and a PT-LCT system; then, converting the color carrier image from an RGB color space into a YCbCr space; and then, embedding the encrypted color image into Cb and Cr channels through a DWT-SVD method; and finally, converting the Cb and Cr channels including the secret image and a Y channel into the RGB color space so that the color carrier image including the secret image is acquired. The method is mainly applied to an information safety and light information processing occasion.
Owner:TIANJIN UNIV
RFID system secret-key wireless generation method
ActiveCN105791317ASolve potential safety hazardsSmall amount of calculationWireless commuication servicesTransmissionSingle labelKey generation
The invention discloses an RFID system secret-key wireless generation method. The an RFID system comprises a label and a reader and writer. The reader and writer determines a secret key generation type. The secret key generation type comprises single label secret key generation, batch secret key generation and group secret key generation. According to the different secret key generation types, the reader and writer and the label generate a sharing secret key. Through a safety analysis, by using the method, active attack and passive attack can be resisted, disadvantages in the prior art can be overcome and a brute force attack can be completely resisted.
Owner:GUANGDONG UNIV OF TECH +1
Image encryption method based on controlled magic cube and alternating quantum walks
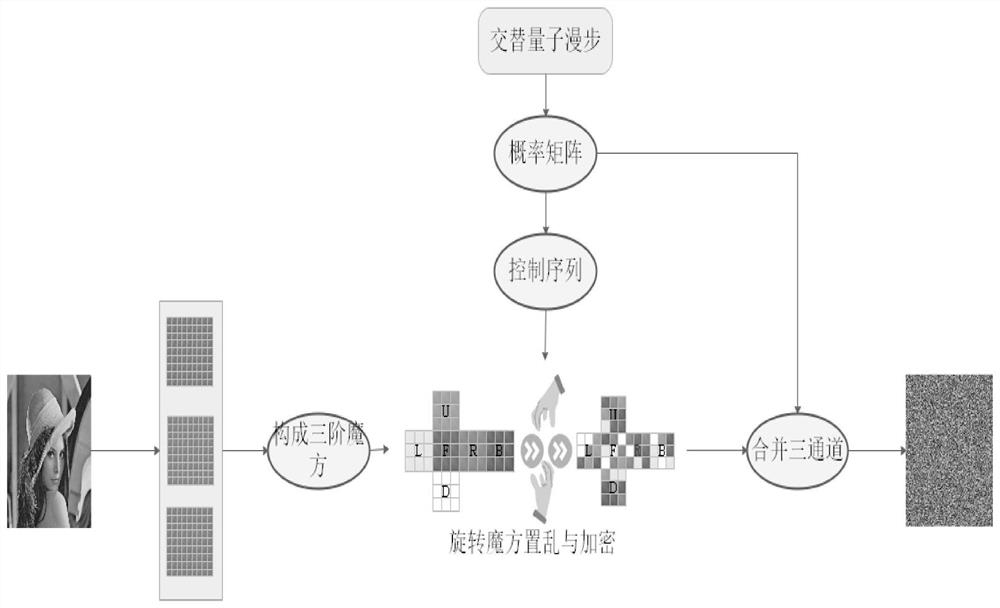
PendingCN114449127AGood random scramblingEvenly distributed pixelsKey distribution for secure communicationPictoral communicationQuantum walkAlgorithm
Owner:QINGDAO TECHNOLOGICAL UNIVERSITY
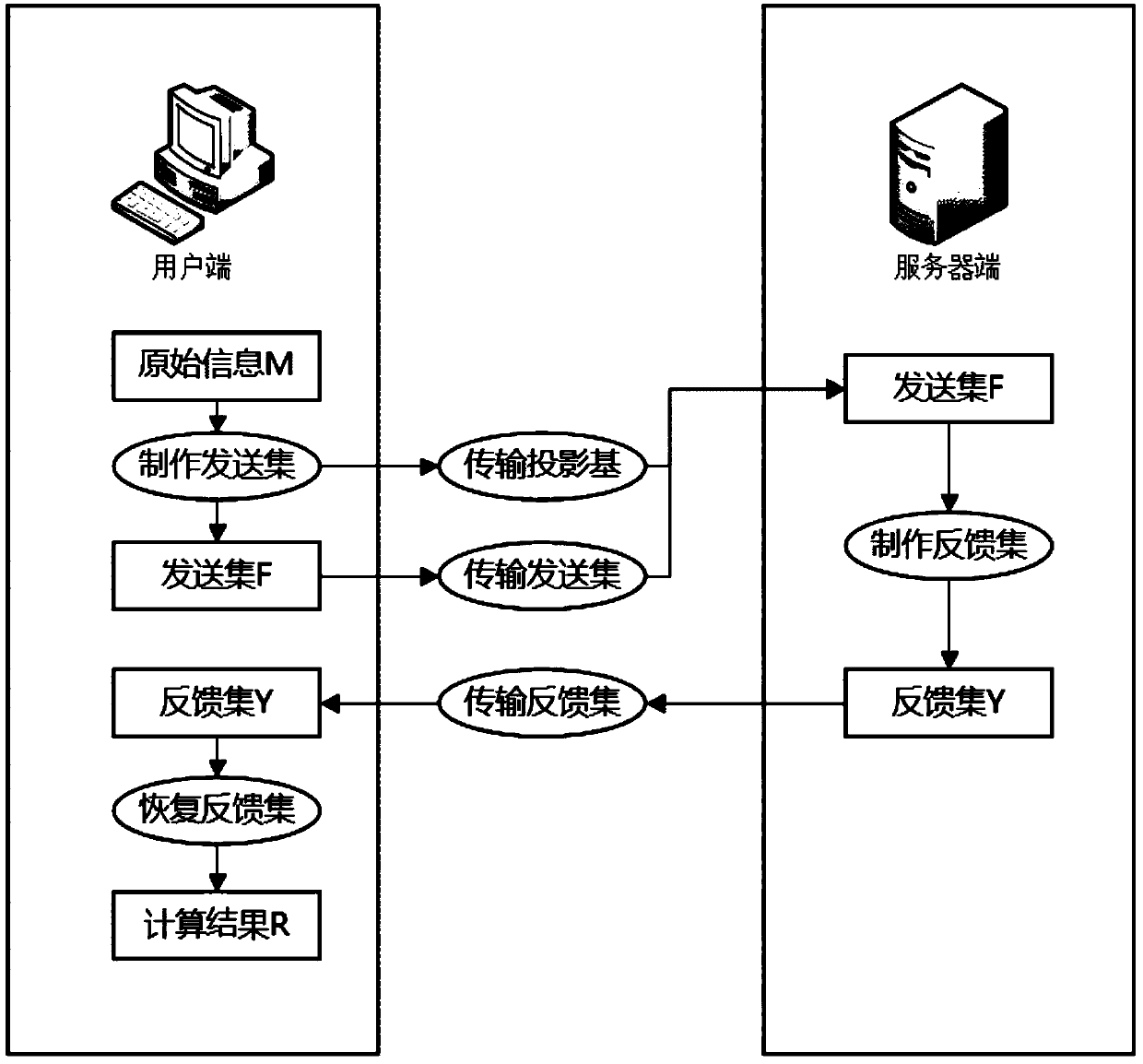
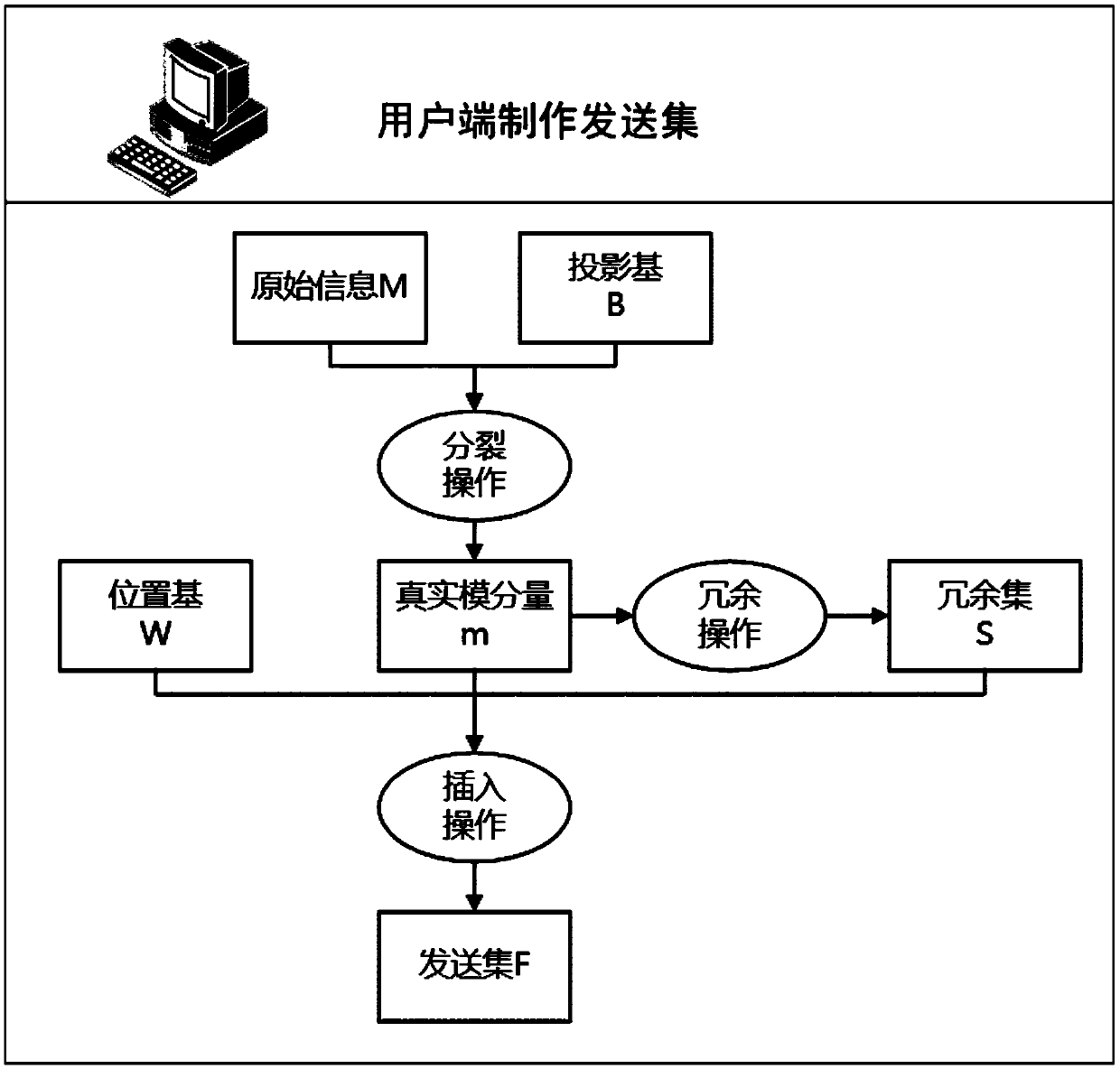
A privacy protection processing method based on modulus component homomorphism
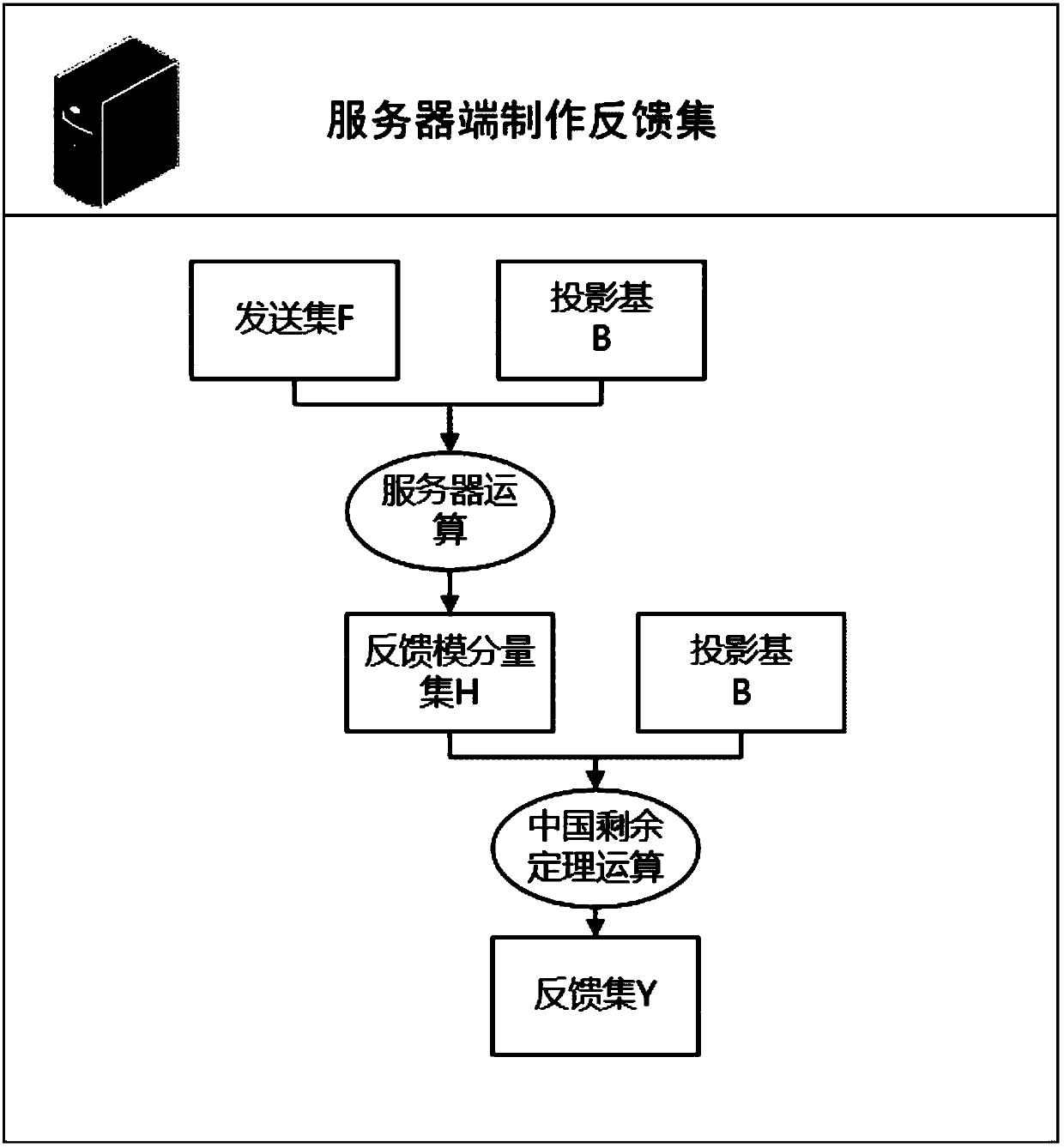
ActiveCN109543451ARealize the operationImplement privacy-preserving processingDigital data protectionOriginal dataChinese remainder theorem
The invention provides a privacy protection processing method based on modulus component homomorphism. The user end performs modulo operation on a group of bases by using original information, insertsthe obtained modulus component into redundant information, and then sends the obtained modulus component to the server end. The server end is unable to distinguish which is the real modulus componentand which is the redundant information. Because the modular operation (addition, subtraction, multiplication) has homomorphism, the operation of the modular component is equivalent to the operation of the original information. After obtaining the calculation result, the server obtains the feedback result according to the Chinese Remainder Theorem, and the client obtains the effective informationafter receiving the feedback result, and obtains the final calculation result of the server through calculation. Although the whole process server cannot get the original data, but the operation of the original data is realized, so even if the server reveals all the information, it will not pose a threat to the original information and its calculation results, and the privacy protection of the original data is realized.
Owner:中共中央办公厅电子科技学院 +1
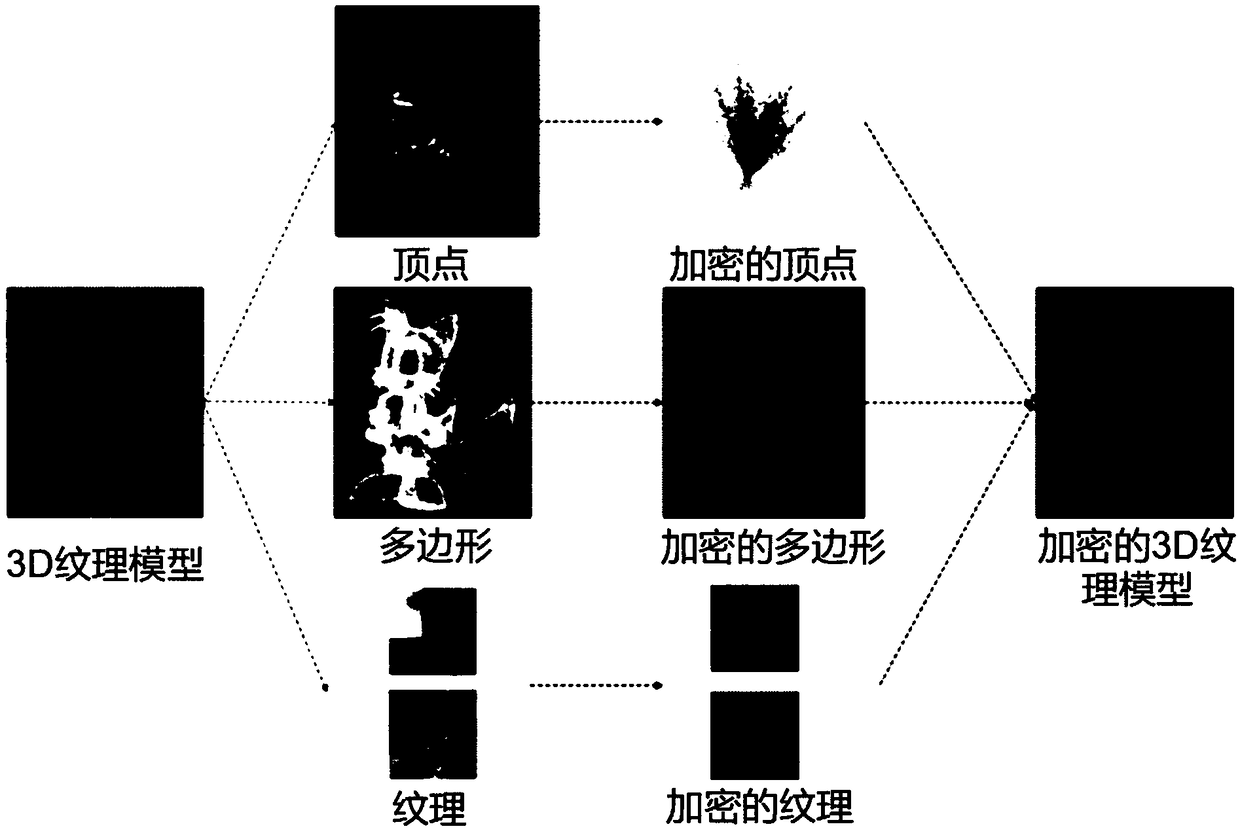
Encryption method of 3D texture model based on multi-level chaotic map
InactiveCN109039577AGood encryptionReduce contributionSecuring communication by chaotic signalsCryptographic attack countermeasuresPoint cloudTexture model
The invention provides an encryption method of 3D texture model based on multi-level chaotic map. Based on the contribution of the vertices (point clouds) of the 3D model, polygons and textures to 3Dmodel recognition, vertices that contribute most to identifying 3D models are encrypted using advanced 3D Lu mappings, and polygons and textures that contribute relatively little to identifying 3D models are encrypted using 2D Arnold mappings and 1D logistic mappings. The method is easily realized by software, and the invention can be widely applied to the fields of 3D printing, 3D modeling, 3D model secrecy and the like.
Owner:中共中央办公厅电子科技学院
A password generation system and a method based on slice graphics
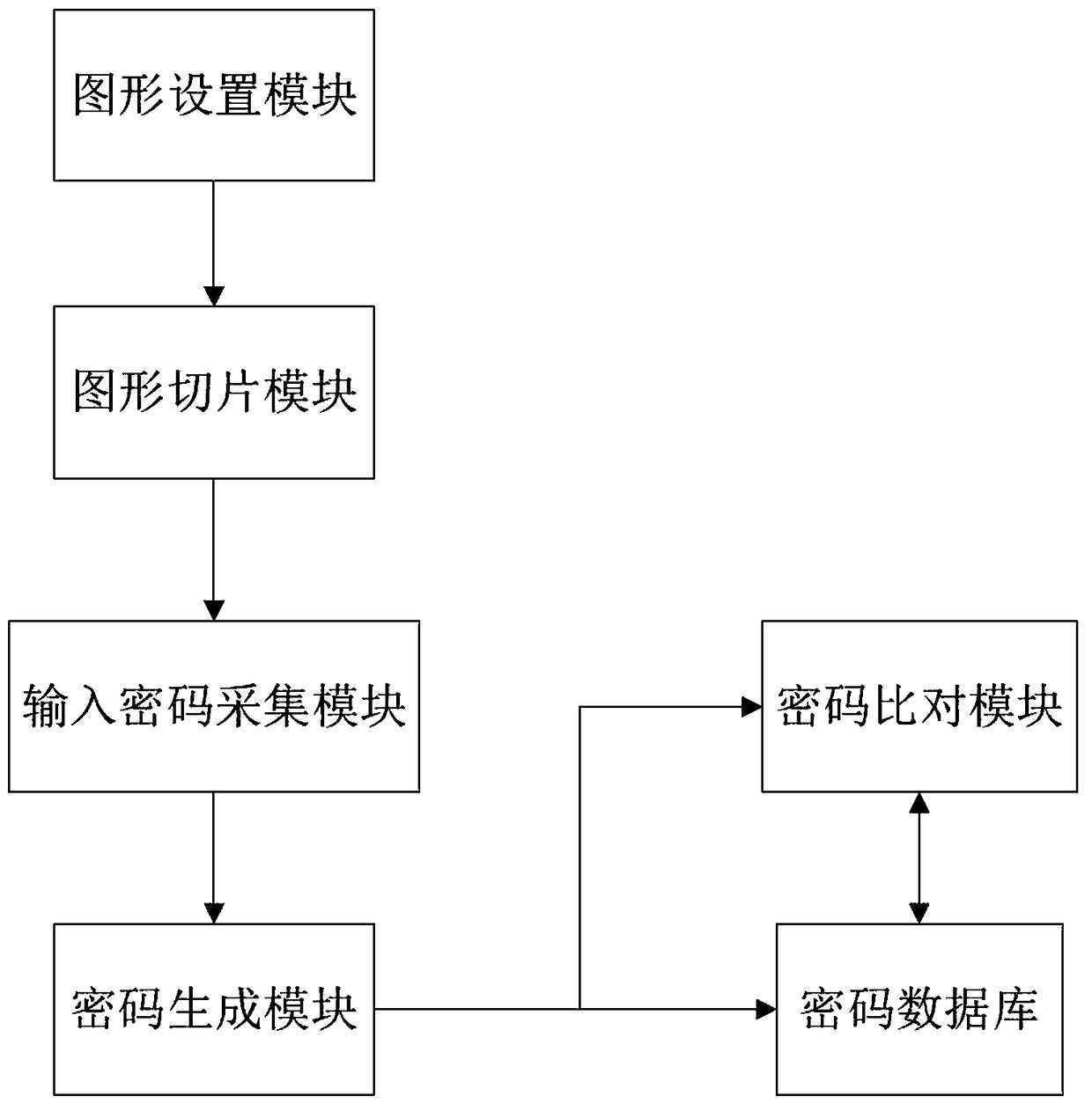
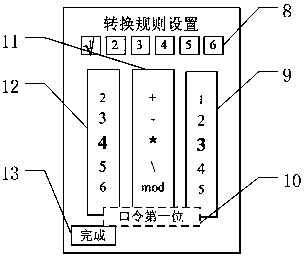
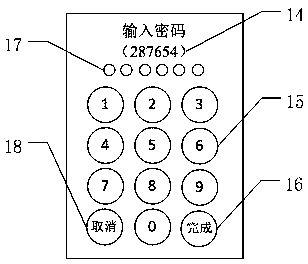
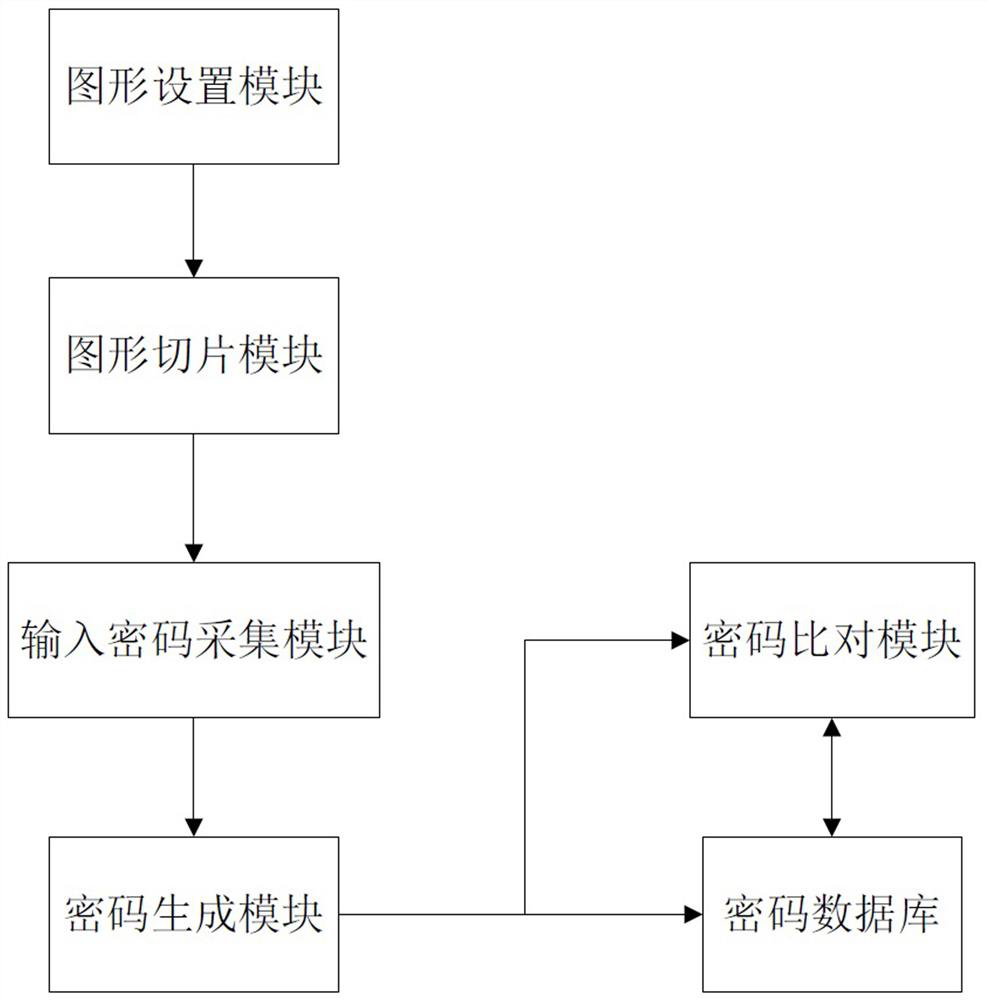
ActiveCN109145569AEasy to enterImprove securityDigital data authenticationGraphicsComputer graphics (images)
The invention relates to a password generation system and a password generation method based on slice graphics. The system comprises a graphics setting module, which is used for selecting graphics used for password input and the quantity thereof; a graphics slicing module which is used for setting the slicing mode and the number of slices of each graph, and slicing each graph according to the slicing mode and the number of slices; an input cipher collecting module, configured to collect input cipher information of a user, wherein the input cipher information refers to a graphics block selectedby the user and an order of selecting the graphics block; a cipher generation module, configured to code and convert the graphics blocks in the input cipher information to obtain text strings of thecorresponding graphics blocks based on the HASH algorithm, and store the text strings as ciphers according to the order of the selected graphics blocks in the input cipher information; a password database. Compared with the prior art, the invention has the advantages of simple and convenient operation, large cipher space, easy memory, small storage space, shoulder peep resistance and the like.
Owner:XIAMEN UNIV TAN KAH KEE COLLEGE
One-time password certification system token resynchronization method based on event
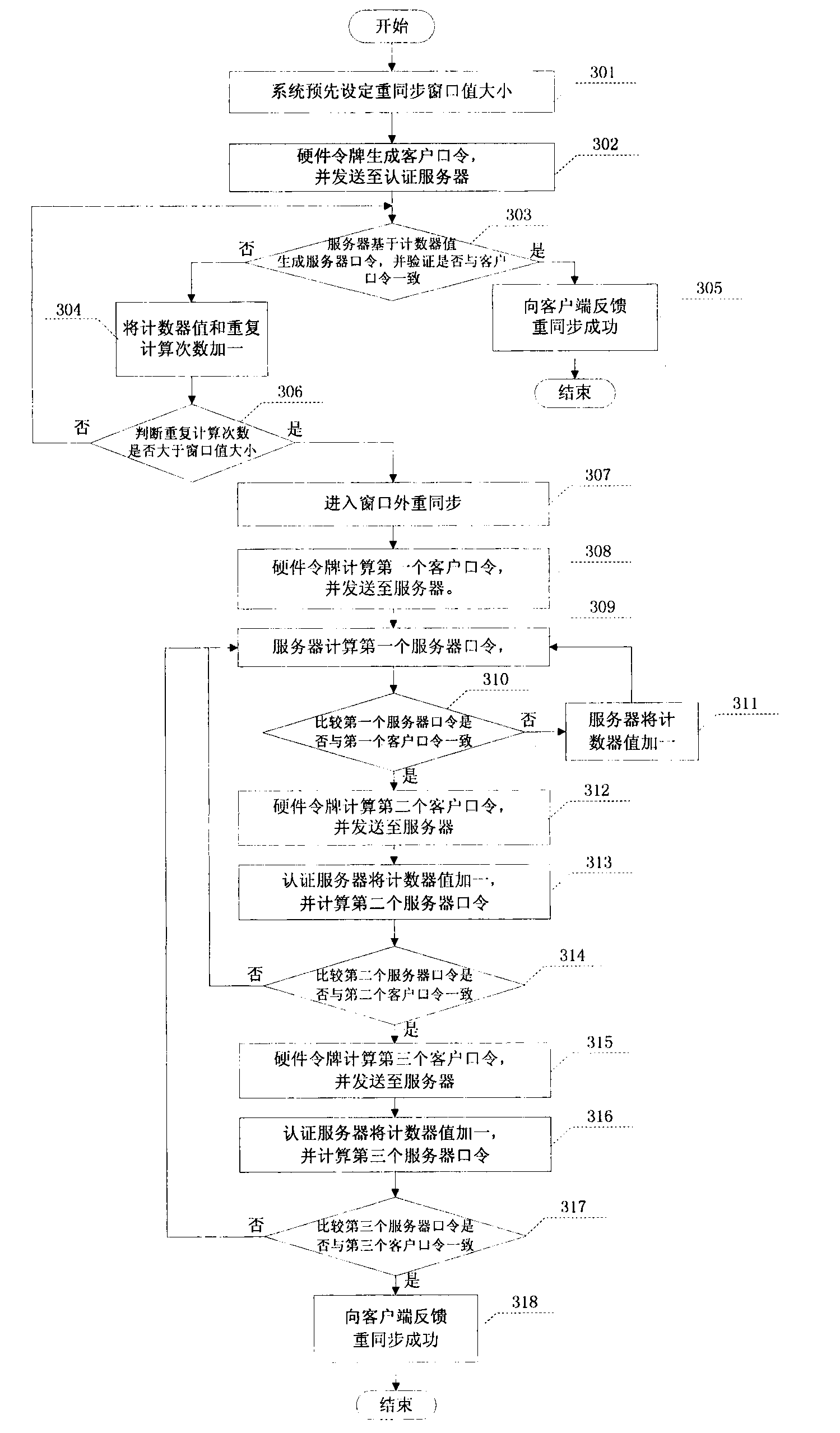
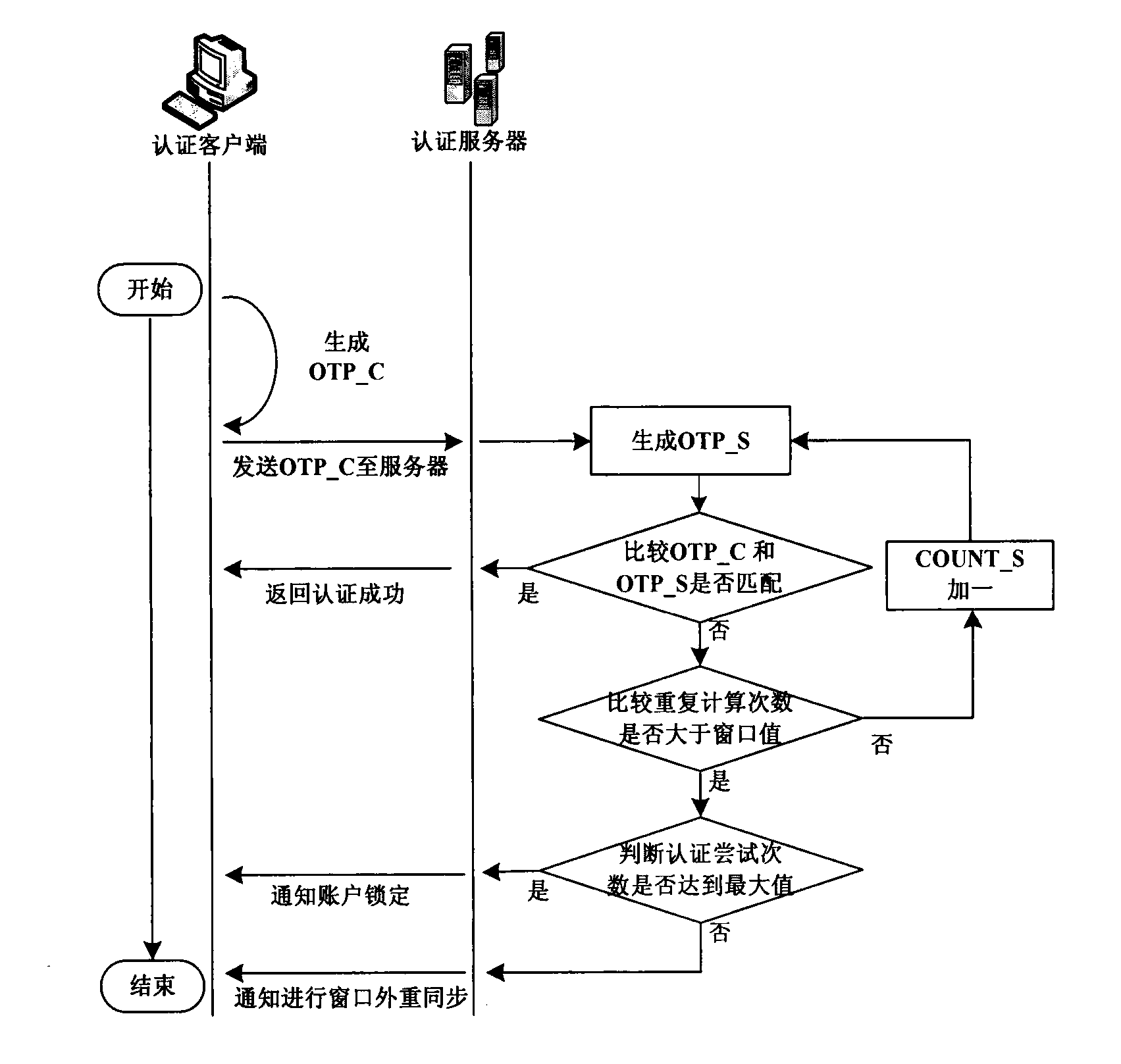
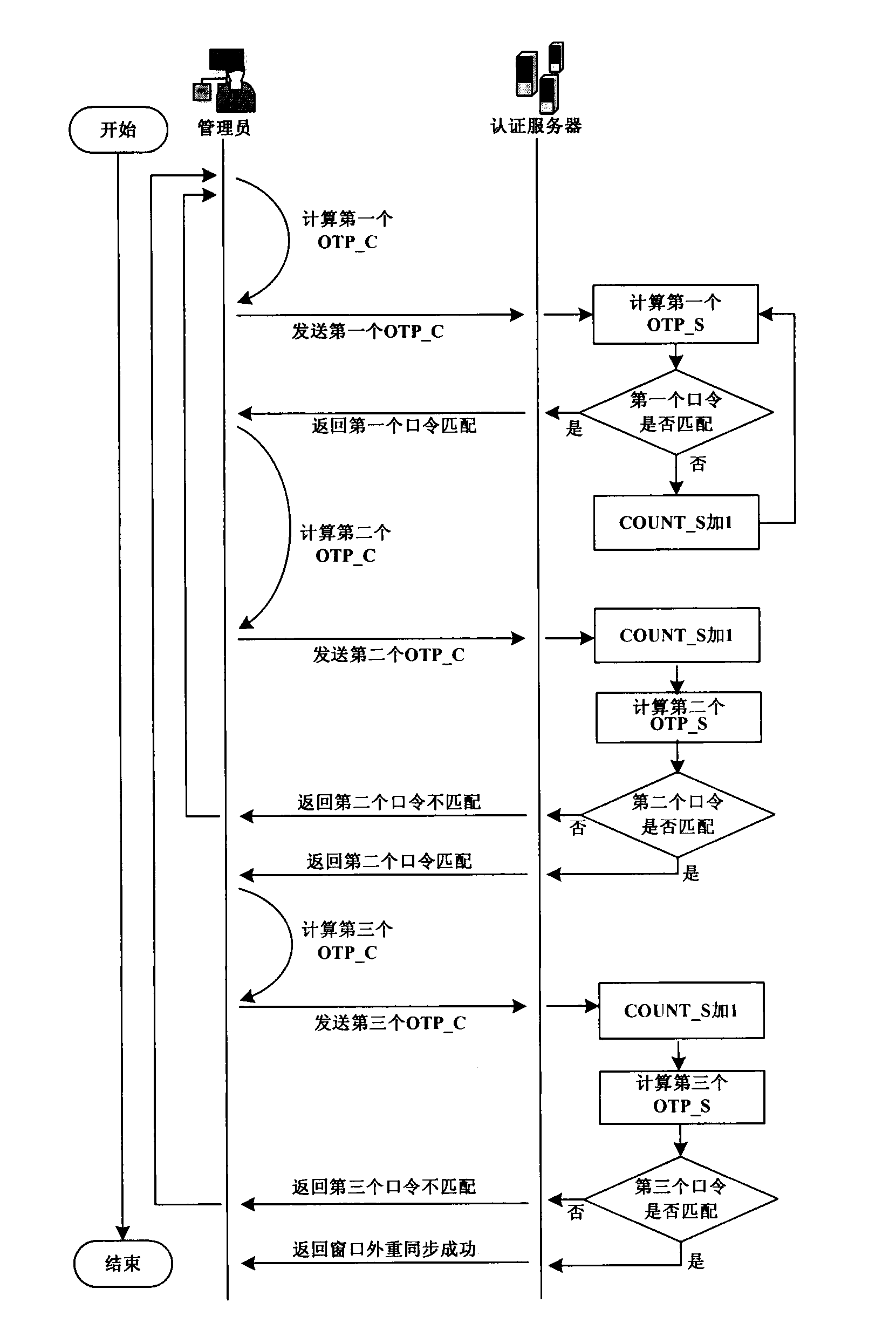
InactiveCN103138928AResistance to brute force attacksEfficient methodUser identity/authority verificationBrute forceAuthentication server
A one-time password certification system token resynchronization method based on an event aims to solve the problems of step out of the token due to inconsistency of counter values of a hardware token and an authentication server of the one-time password certification system based on the event and provides a resynchronization method. The method is divided into window inner resynchronization and window outer resynchronization on basis of a preset size of the window and the counter values as synchronization factors. When step out times of the hardware token and the server are within the size of the window, the window inner resynchronization is carried out, repetitive computation command times are smaller than or equal to the window size, and a group of consistent customer commands and service commands, and the resynchronization is achieved; if not, the widow outer resynchronization is carried out, at the moment if three customer commands and service commands are consistent continuously, the resynchronization is achieved, the whole execution process of the resynchronization method is divided into seven steps. The one-time password certification system token resynchronization method based on the event is highly-efficient, simple in computation, low in time consumption of operation, fast in operation speed, small in occupation space of system memory space, and capable of resisting brute force impact of the certification system.
Owner:李慧娟 +2
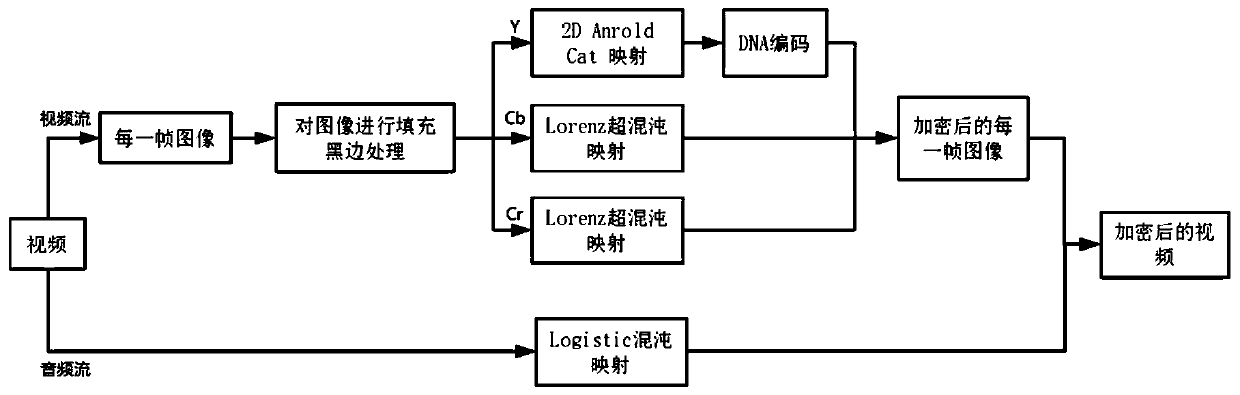
Video encryption method incompatible with video coding based on chaotic cryptography theory
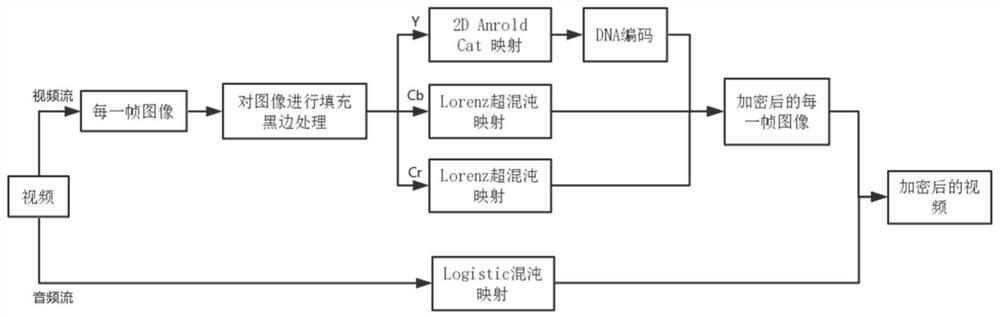
ActiveCN110381337AImprove the shortcomings of not being able to playImprove securitySecuring communication by chaotic signalsSelective content distributionComputer hardwareDna encoding
The invention relates to a video encryption method incompatible with video coding based on a chaotic cryptography theory. The method comprises steps of dividing a video file into a video stream and anaudio stream: regarding the video stream as frames of image, encrypting based on 2D Arnold Cat mapping, a DNA encoding technology and a Lorenz hyperchaotic system, and adopting different encryption methods for Y, Cb and Cr channels of the image; using logistic mapping for audio stream encryption. A video stream is regarded as common image data to be encrypted, and compared with an encryption algorithm compatible with video coding to selectively encrypt sensitive information in a video, the security is enhanced; high-dimensional chaotic encryption is adopted, so that exhaustion attacks can beresisted; and the encrypted images are automatically synthesized into a video, so that the defect that the video cannot be played after being encrypted by a traditional incompatible video coding encryption algorithm is overcome. According to the method, various attacks such as strong attacks, statistical attacks and related attacks can be effectively resisted.
Owner:SHANGHAI GOLDEN BRIDGE INFOTECH CO LTD
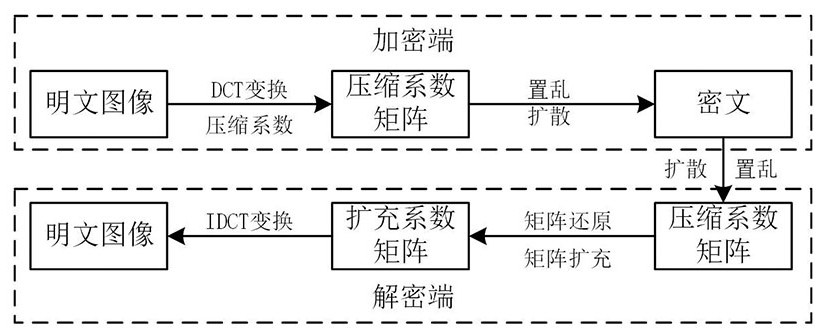
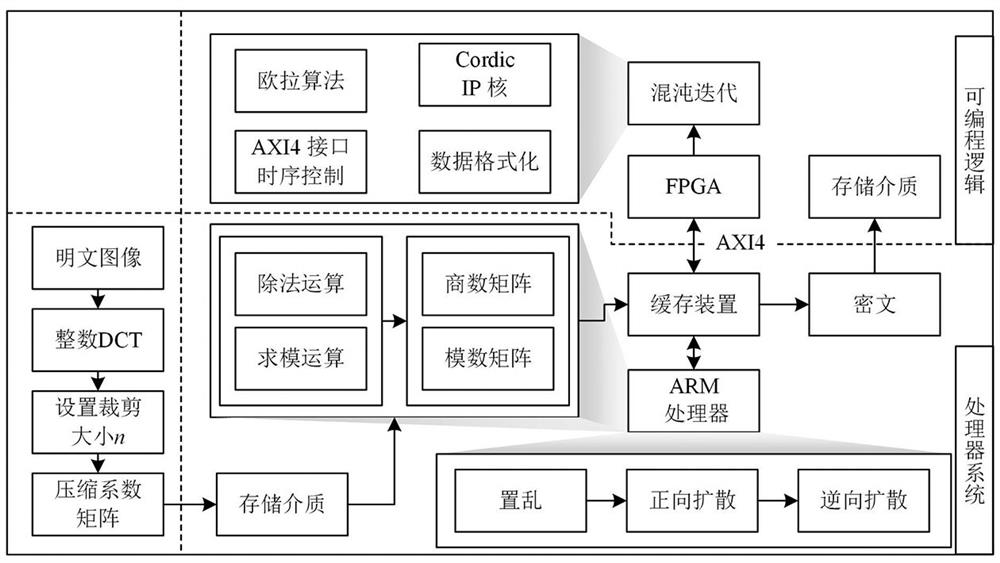
Compressible six-dimensional non-degenerate hyperchaotic image secrecy system and method
PendingCN113890722AImprove discretization speedReduce data volumeSecuring communication by chaotic signalsDigital video signal modificationConcurrent computationAlgorithm
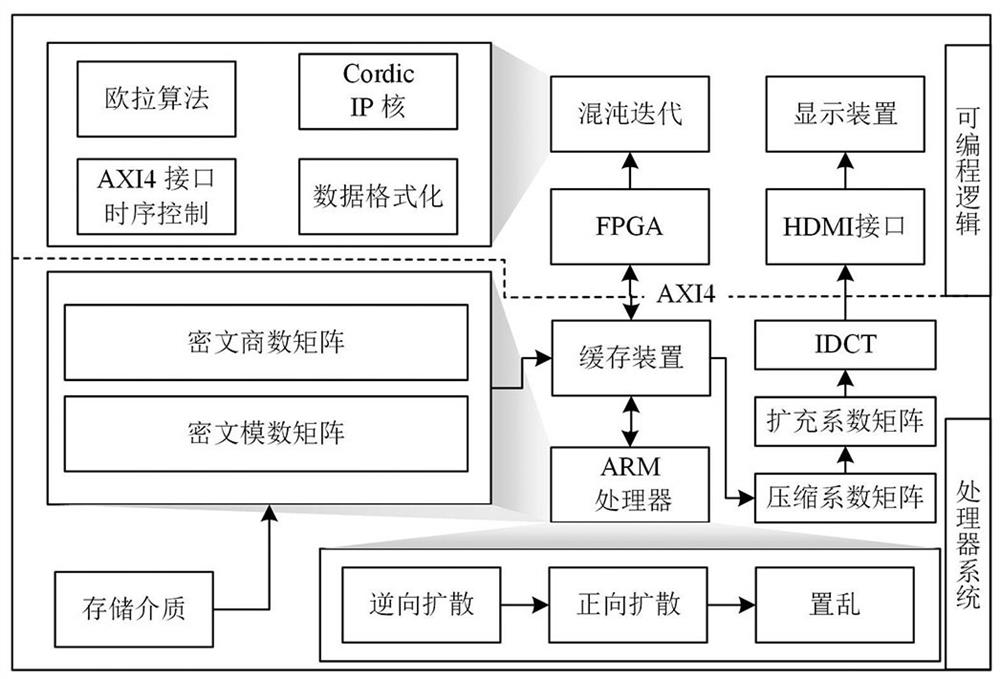
The invention discloses a compressible six-dimensional non-degenerate hyperchaotic image secrecy system and method. Image data are compressed at an encryption end to obtain a compression coefficient matrix, and the matrix is encrypted by combining a hyperchaotic sequence at the encryption end to obtain ciphertext data. And the decryption end sets an initial value of the hyper-chaotic system according to the key, decrypts the ciphertext data by a chaotic sequence of the hyper-chaotic system of the decryption end, and further reduces the ciphertext data to obtain a plaintext image. The encryption end and the decryption end complete encryption and decryption operations by using SOPC resources, the FPGA performs parallel acceleration on the hyperchaotic discretization process in the SOPC, and the ARM processor completes the image encryption and decryption process in combination with a chaotic sequence. According to the method, hardware resources can be effectively saved in the application process, the discretization speed of the hyperchaotic system is increased by applying the parallel computing advantages of the FPGA, and then the working efficiency of an image secrecy system is improved.
Owner:HUNAN UNIV OF SCI & TECH
JPEG image encryption method based on similar coefficient scrambling
InactiveCN105975866BIncrease the compression ratioExpand the key spaceImage codingDigital data protectionPlaintextJPEG
The invention relates to an intra-class coefficient scrambling-based JPEG image encryption method. The method comprises the following steps: firstly reading in a JPEG image file, acquiring a Huffman coding table and image data which undergoes JPEG coding compression, carrying out decoding to acquire all the non-zero quantized DCT coefficient numerical values and positions and carrying out classification; selecting a password, carrying out chaotic iteration by utilizing the password, so as to generate a chaotic sequence, and scrambling the non-zero coefficients and 8*8 block of each class by utilizing the chaotic sequence; and carrying out entropy coding on a scrambled quantized DCT coefficient matrix, and writing the coded data into the JPEG image file so as to complete intra-class coefficient scrambling-based JPEG image encryption. According to the method disclosed in the invention, scrambling is carried out on different classes of quantized DCT coefficients through the chaotic sequence, and the quantized DC coefficients and the non-zero AC coefficients are processed by directly using one encryption scheme, so that the safety and the high efficiency are both considered; and the encrypted images are similar to clear text image files in the aspect of size, and have high compression ratios.
Owner:CHANGAN UNIV
Highly precise safe palm recognition method encrypted based on phase characteristic of Log-Gabor mixed filtering
InactiveCN100593790CAvoid the effects of identificationHigh expressionCharacter and pattern recognitionComputation complexityPrivacy protection
Owner:SOUTHWEST JIAOTONG UNIV
A method for wireless generation of rfid system key
ActiveCN105791317BSolve potential safety hazardsSmall amount of calculationWireless commuication servicesTransmissionComputer networkAttack
The invention discloses a wireless key generation method for an RFID system. The RFID system includes a tag and a reader, specifically: the reader determines the key generation type; the key generation type includes a single tag key generation , batch key generation and group key generation; according to different key generation types, a shared key is generated between the reader and the tag. The security analysis shows that this method can not only resist active attack and passive attack, but also can make up for the deficiencies of existing technologies, and can completely resist brute force attack.
Owner:GUANGDONG UNIV OF TECH +1
A multiple certification method and system
PendingCN108777672AImprove securityDeploy and useIndividual entry/exit registersTransmissionBrute forceInformation device
The invention relates to a multiple certification method and system adopting a customized rule. A certification host, a user terminal and a certification executing device are adopted. Multiple certification design is adopted, verification is performed on users through the user terminal which uses random challenge information and a preset operation regulation, peep attack and brute force cracking attack are defended, even if the hardware is lost, an illegitimate users still cannot normally use the user terminal to pass through the verification of the certification host. A hand-drawn graph having customized meaning is used as verification information in a second certification phase, the brute force cracking attack is avoided, the calculating capability of the certification user terminal andthe certification host can be fully utilized, redundancy information is added into interaction, and playback attack is defended. The system can be used as an access control system or an access controlsystem of an information device.
Owner:上海求敏信息科技有限公司
Bit-level image encryption method based on composite Tent chaotic mapping
PendingCN114422104AIncreased complexityLarge parameter rangeKey distribution for secure communicationMultiple keys/algorithms usageKey spaceAlgorithm
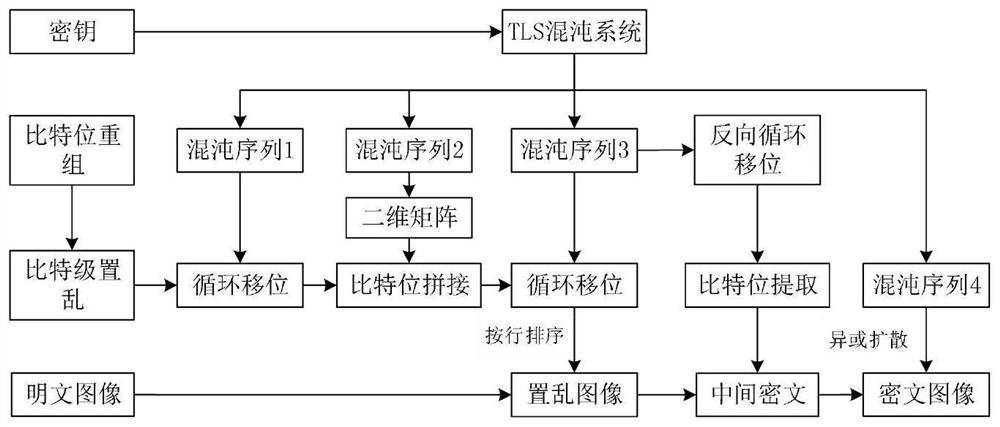
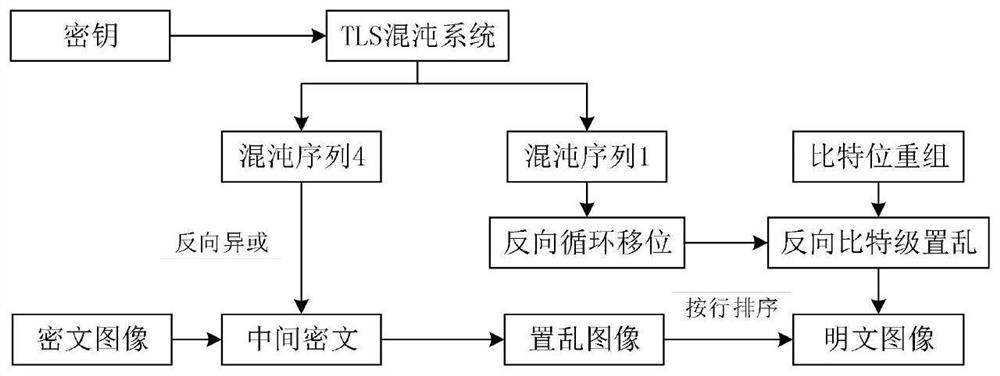
The invention proposes a bit-level image encryption method based on composite Tent chaotic mapping, and the method comprises the steps: firstly, carrying out the coupling of Tent mapping, Logistic mapping and Sine mapping, obtaining a composite chaotic mapping TLS, improving the complexity of a chaotic system, enhancing the randomness of a secret key sequence, enabling the parameter range of the chaotic system to be expanded, and achieving the encryption of a bit-level image. Therefore, the security of the encryption system is effectively improved. And compared with a high-dimensional chaotic system, the execution cost of the one-dimensional chaotic system is lower. A plurality of composite chaotic systems are introduced in the encryption process to increase the number of keys, the key space of the algorithm is expanded, and the algorithm can well resist violent attacks. A matrix splicing method is used in the scrambling process, and the problem of bit limitation during bit scrambling is solved. Two rounds of XOR operation are used in the diffusion process, and the differential attack resistance of the encryption system is effectively improved.
Owner:ANHUI UNIV OF SCI & TECH
Key system for digital television broadcast condition receiving system
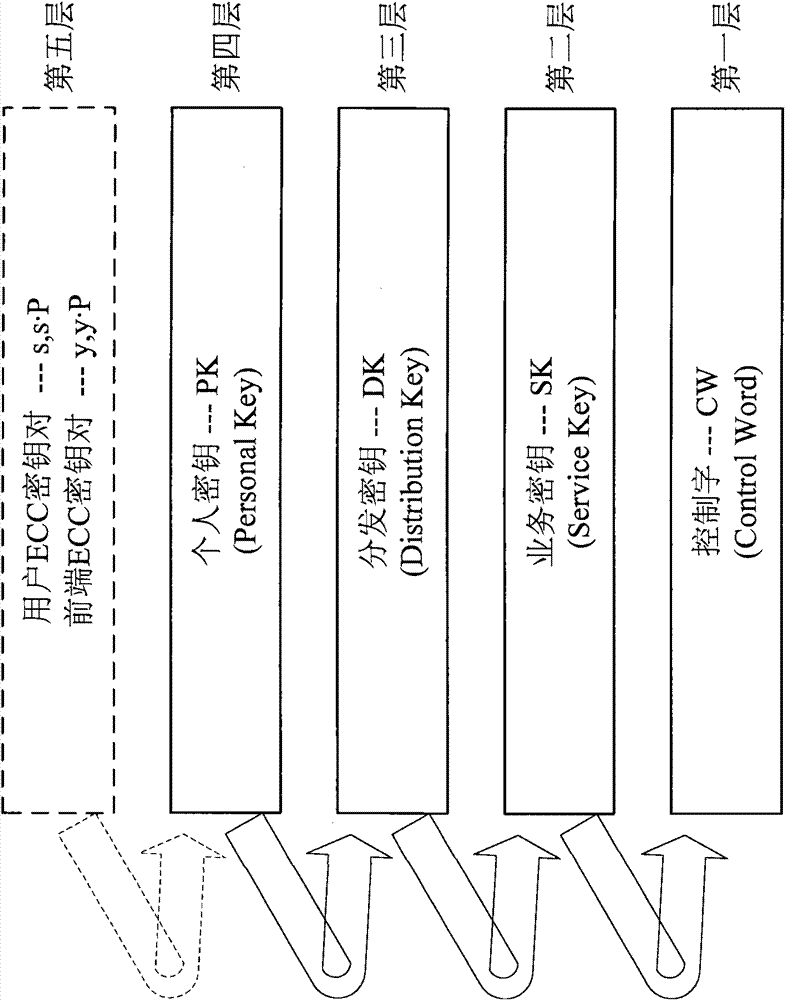
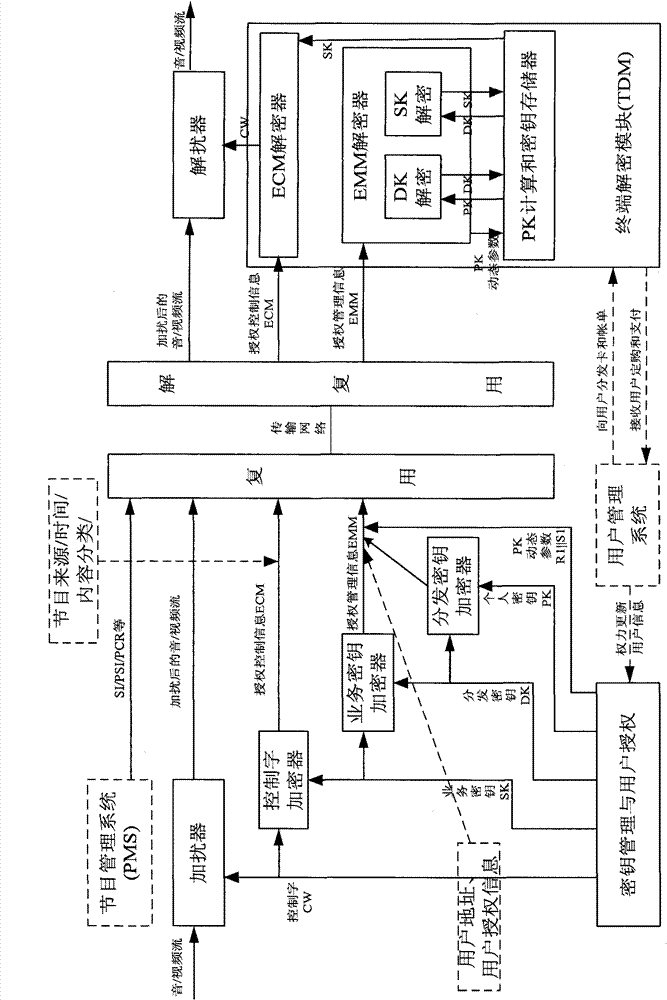
ActiveCN102111681BHigh strengthResistance to brute force attacksKey distribution for secure communicationSelective content distributionNon symmetricBrute force
The invention provides a key system for a digital television broadcast condition receiving system. The key system comprises five layers of keys, namely four layers of symmetrical keys and one layer of asymmetrical key, wherein the four layers of symmetrical keys comprises a control word (CW), a service key (SK), a distribution key (DK) and a personal key (PK); and the one layer of asymmetrical key is an error correction code (ECC) key pair. All the password algorithms which are used in the invention are designated by State Cryptography Administration and comply with the requirements in regulations on state commercial passwords. The intensity of the password algorithms is high, so that the brute force attacks based on a digital television broadcast network can be effectively resisted.
Owner:AEROSPACE INFORMATION
An ultra-lightweight two-way authentication method for mobile RFID systems
ActiveCN108304902BReduce hardware costsSmall amount of calculationKey distribution for secure communicationDatabase updatingAttackEngineering
The invention relates to the technical field of communication, and more specifically relates to the issue of security authentication among tags, readers and back-end databases in a mobile RFID system. The implementation steps are: (1) the reader sends request information to the tag; (2) the reader sends the tag response request information and its own information to the database; (3) the database authenticates the reader and the tag; (4) the reader authenticates the database ; (5) Label authentication database. This protocol uses a circular check function and simple XOR and cascade operations to encrypt the message to be transmitted, realizes the anonymity of the tag and the two-way authentication of the system, and effectively reduces the calculation amount of the database and the tag. The tag random number is generated by the random number generation mechanism of the back-end database and then forwarded to the tag or self-renewed by using the cycle check function, thereby reducing the hardware cost of the tag. The present invention utilizes the dynamic ID and the circular check function mechanism to enable the system to resist various attacks.
Owner:XIDIAN UNIV
A password generation system and method based on slice graphics
The present invention relates to a system and method for generating passwords based on sliced graphics. The system includes: a graphics setting module for selecting graphics and their quantity for password input; a graphics slicing module for setting the slicing mode and Slicing quantity, and slice each graphic according to the slicing mode and the slicing quantity; input password collection module, for collecting the user's input password information, said input password information refers to the graphic blocks selected by the user and the order of the selected graphic blocks; Password generating module, for converting the graphic blocks in the input password information into encoding conversion based on the HASH algorithm to obtain the text strings of the corresponding graphic blocks, and storing each text string as a password in the order of selecting graphic blocks in the input password information; password database. Compared with the prior art, the present invention has the advantages of simple and convenient operation, large password space, easy memory, small storage space, anti-shoulder peeping and the like.
Owner:XIAMEN UNIV TAN KAH KEE COLLEGE
Color image encryption and hiding method based on pt-lct and dwt-svd
InactiveCN107516332BRobustResistance to brute force attacksImage codingDigital video signal modificationPattern recognitionInformation processing
The invention relates to the information safety and light information processing technology field and provides a color image encryption and hiding method based on PT-LCT and discrete wavelet transform-singular value decomposition (DWT-SVD). Finally, a color carrier image including a secret image is acquired. The color image encryption and hiding method based on PT-LCT and DWT-SVD is characterized by firstly, encrypting a color image to be hidden through Arnold scrambling and a PT-LCT system; then, converting the color carrier image from an RGB color space into a YCbCr space; and then, embedding the encrypted color image into Cb and Cr channels through a DWT-SVD method; and finally, converting the Cb and Cr channels including the secret image and a Y channel into the RGB color space so that the color carrier image including the secret image is acquired. The method is mainly applied to an information safety and light information processing occasion.
Owner:TIANJIN UNIV
Method and device for generating key of rfid system based on tag id
ActiveCN105721142BSolve potential safety hazardsSmall amount of calculationKey distribution for secure communicationNear-field in RFIDReader writerKey generation
The invention discloses a method and device for generating a key for an RFID system based on tag ID. The method is: the reader first determines whether to generate a key for one tag, a batch of tags, or a group of tags, and determines the type of key generation. , and then send a key generation request command to the tag. The tag feeds back the information corresponding to the tag ID according to the type. The reader and the tag form a shared key between them through certain calculations based on the tag ID information. Using this key, subsequent two-way authentication can be performed. Based on the above types, the present invention specifically discloses three types of key generation devices. The method of the invention improves the reading and writing security of the RFID system, greatly reduces the calculation amount on the tag side, and reduces the cost of the tag.
Owner:GUANGDONG UNIV OF TECH
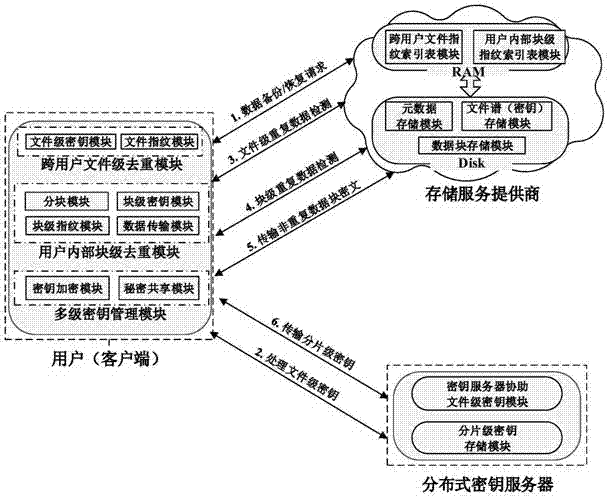
An efficient security data deduplication method and system based on user perception
ActiveCN104917609BResistance to brute force attacksGuaranteed confidentialityKey distribution for secure communicationSpecial data processing applicationsBrute forceConfidentiality
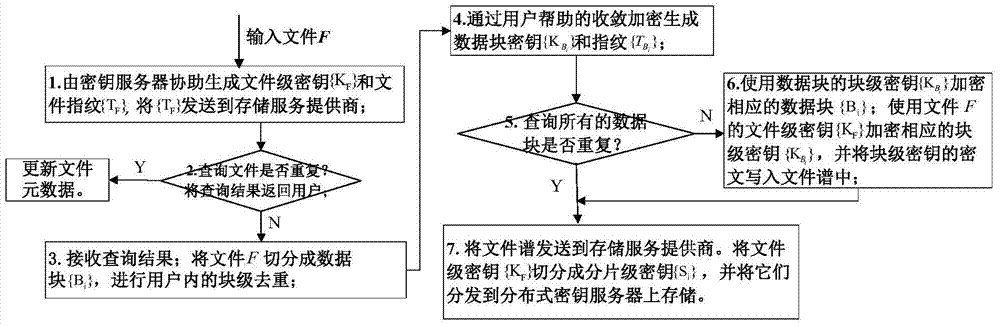
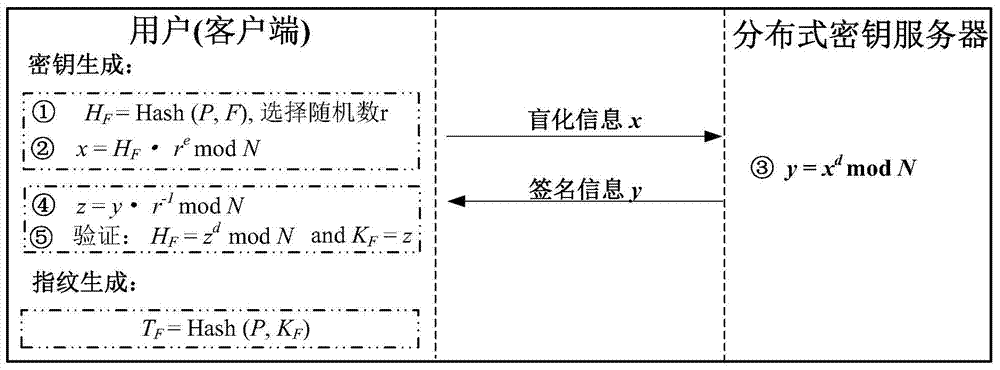
The present invention provides an efficient and secure data deduplication method based on user perception, including: the client adopts hash-based convergent encryption assisted by a key server to deduplicate cross-user file-level data; Convergent encryption performs block-level deduplication within users; adopts multi-level key management, uses file-level keys to encrypt block-level keys, and uses secret sharing to divide file-level keys into shard-level keys and store them in distributed keys server. The invention also provides an efficient security data deduplication system based on user perception. The present invention adds random information by using hash-based convergent encryption assisted by a key server at the file level and user-assisted convergent encryption at the block level to randomize the user's file-level and block-level keys, which can effectively resist the opponent's Brute force cracking attacks ensure the confidentiality and security of user data; a multi-level key management scheme is used to ensure key security and reduce key space overhead.
Owner:HUAZHONG UNIV OF SCI & TECH
A Video Encryption Method Based on Chaotic Cryptography Incompatible Video Coding
ActiveCN110381337BImprove the shortcomings of not being able to playImprove securitySecuring communication by chaotic signalsSelective content distributionAlgorithmTheoretical computer science
The invention relates to a video encryption method based on chaotic cipher theory and incompatible video encoding, which divides video files into video streams and audio streams: the video stream is regarded as a frame of images, and the encryption is based on 2D Arnold Cat mapping and DNA encoding technology And the Lorenz hyperchaotic system, different encryption methods are used for the Y, Cb and Cr channels of the image; the audio stream encryption uses Logistic mapping. The video stream is encrypted as ordinary image data, which enhances security compared with the selective encryption of sensitive information in the video using an encryption algorithm compatible with video coding; high-dimensional chaotic encryption is used to resist exhaustive attacks; after encryption The image is automatically synthesized into a video, which improves the disadvantage that the traditional incompatible video encoding and encryption algorithm cannot play the video after being encrypted. The invention can effectively resist various attacks such as strong attack, statistical attack and related attack.
Owner:SHANGHAI GOLDEN BRIDGE INFOTECH CO LTD
Image Compression Sensing and Image Encryption Method Based on Controlled Sparse Basis
InactiveCN104463765BImprove scrambling effectImprove securityImage data processing detailsPattern recognitionCiphertext
Owner:NANCHANG UNIV
Image encryption method and device based on double-entropy source hyperchaotic system and storage medium
ActiveCN112543093AEnsure safetyIncreased sensitivityKey distribution for secure communicationSecuring communication by chaotic signalsKey spaceCiphertext
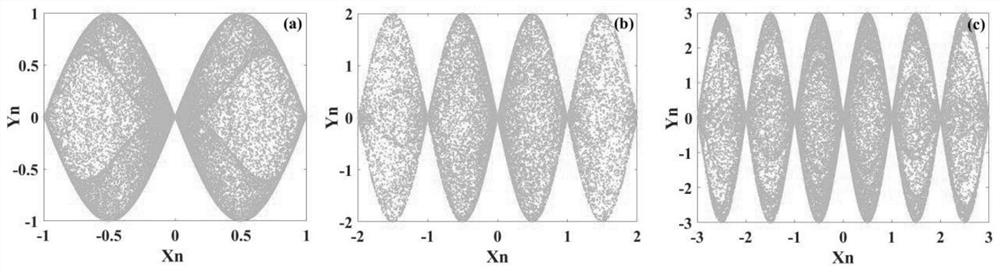
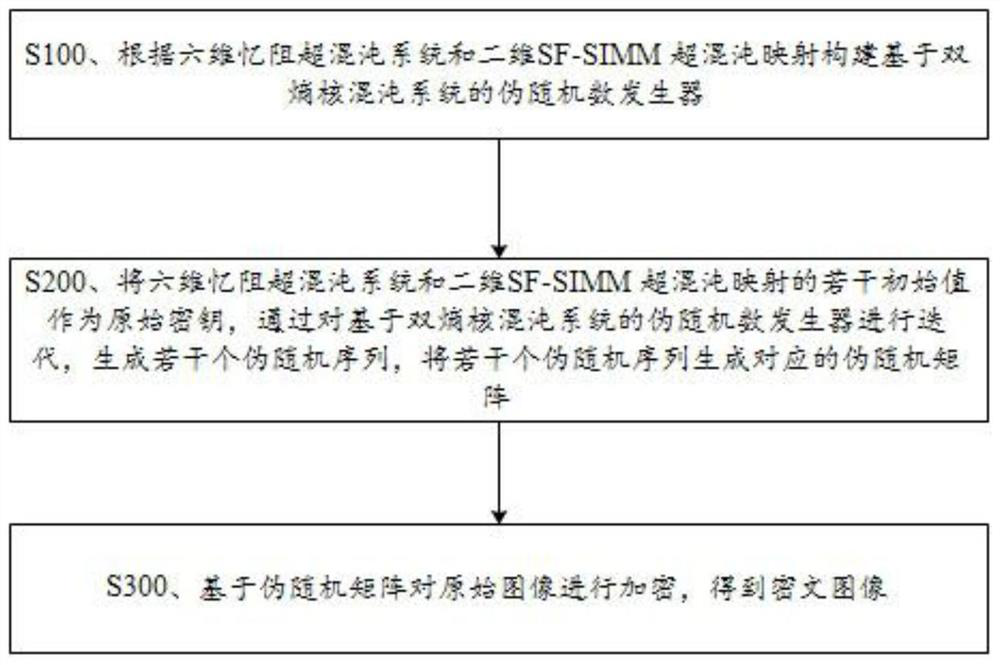
The invention discloses an image encryption method and device based on a double-entropy source hyper-chaotic system and a storage medium, and the method comprises the steps: firstly constructing a pseudo-random number generator based on a six-dimensional memristor hyper-chaotic system and two-dimensional SF-SIMM hyper-chaotic mapping, and obtaining a complex sequence with a double-entropy source structure; performing iteration by a pseudo random number generator to obtain a corresponding pseudo random matrix; and finally, diffusing pixels of the original image based on the obtained pseudo-random matrix, and encrypting the original image into a ciphertext image. According to the method, a six-dimensional memristor hyper-chaotic system and two-dimensional SFSIMM hyper-chaotic mapping are combined and applied to image encryption, a new image encryption method is provided, and the method has high key sensitivity and high differential attack resistance; the secret key space is far large, and violent attacks can be effectively resisted; the information of the ciphertext image can be well hidden, and the security of the ciphertext image is ensured; the information entropy of the ciphertext image is very close to a theoretical value, and the method has high entropy attack resistance.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com