A password generation system and a method based on slice graphics
A technology for generating systems and graphics, applied in the field of information security, can solve the problems of small password space, low security, inconvenient input, etc., and achieve the effect of resisting the threat of shoulder peeping, resisting violent attacks, and convenient input operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments. This embodiment is carried out on the premise of the technical solution of the present invention, and detailed implementation and specific operation process are given, but the protection scope of the present invention is not limited to the following embodiments.
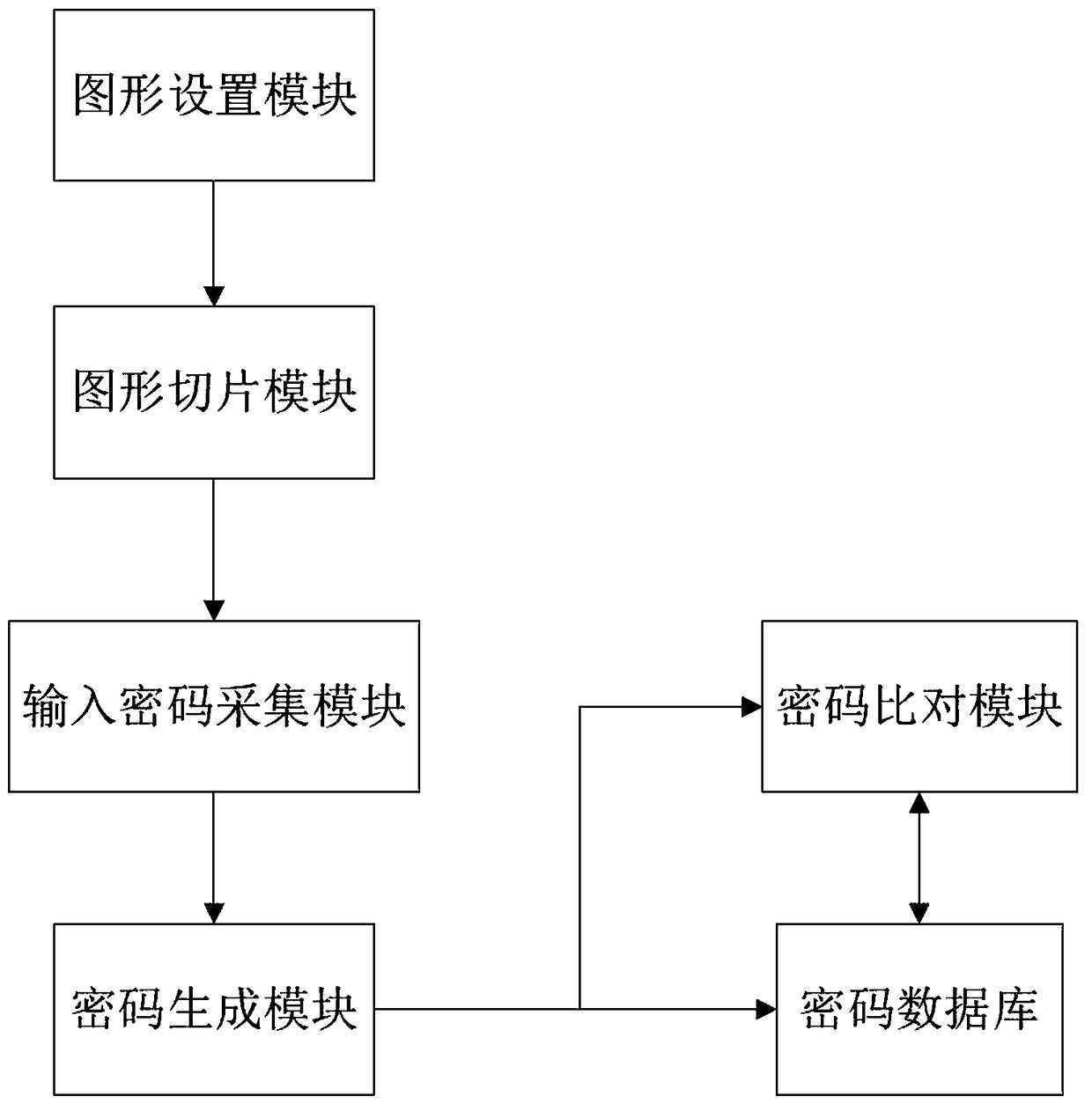
[0039] Such as figure 1 As shown, a password generation system based on sliced graphs includes:
[0040] The graphic setting module is used for selecting the graphic and its quantity for password input. Graphics are classified into general graphics and custom graphics according to the setting type.
[0041] General-purpose graphics can be set to some common and distinctive graphics in the world, such as blue sky and white clouds pictures of WINDOWS, etc.; custom graphics can be set to personal pictures that users like, such as personally designed pictures, Selfie pictures or even ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com