Color image encryption and hiding method based on PT-LCT and DWT-SVD
A PT-LCT, color image technology, applied in the fields of information security and optical information processing, can solve problems such as chosen plaintext attack and known plaintext attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
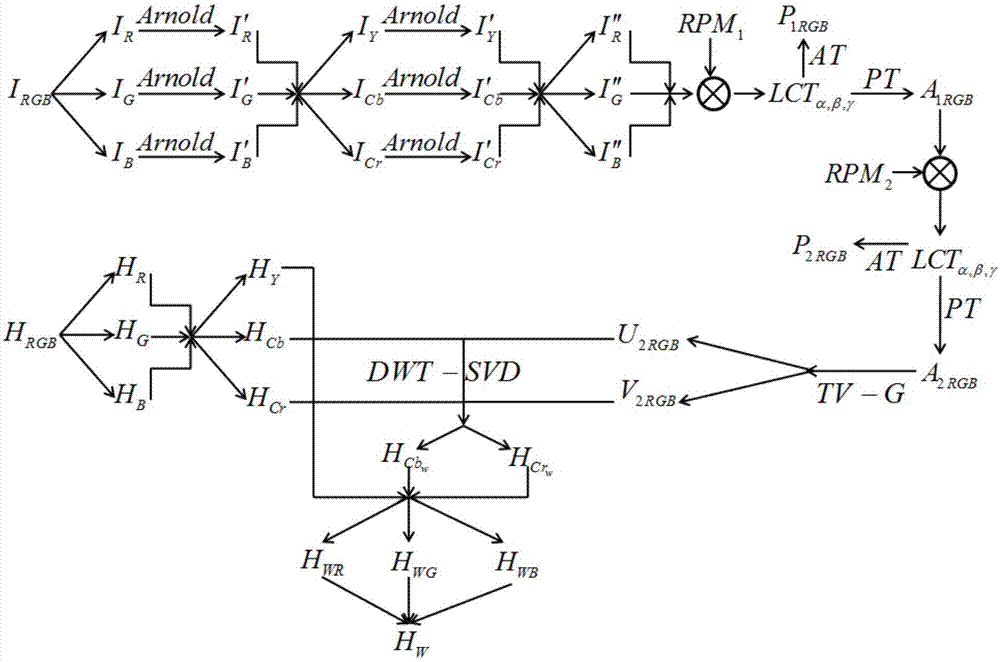
[0051] A color image encryption and hiding method based on PT-LCT and DWT-SVD, the schematic diagram of its encryption and embedding principle is as follows figure 1 (Since the extraction and decryption process is the reverse process of the embedding and encryption process, the schematic diagram of the extraction and decryption principle is omitted here). The method consists of the encryption part of the color image to be hidden, the embedding part of the color encryption image, the extraction part of the color encryption image and the decryption part of the color image.
[0052] (1) The encrypted part of the color image to be hidden:
[0053] In the encryption process, the color image to be hidden is processed in the following steps to achieve the purpose of encrypting the color image. (1) the color image I to be encrypted RGB Decomposed into RGB three color channels I R , I G , I B , and perform generalized Arnold scrambling on each color channel; (2) convert the scram...
Embodiment 2
[0062] Combine below figure 1 1. The design principle introduces the scheme in embodiment 1 in detail, see the following description for details:
[0063] A color image encryption and hiding method based on PT-LCT and DWT-SVD, the schematic diagram of its encryption and embedding principle is as follows figure 1 shown. The method consists of the encryption part of the color image to be hidden, the embedding part of the color encryption image, the extraction part of the color encryption image and the decryption part of the color image. The specific implementation manners of these four parts will be described in detail below.
[0064] (1) The encrypted part of the color image to be hidden:
[0065] In the encryption process, the color image to be hidden is processed in the following steps to achieve the purpose of encrypting the color image.
[0066] A. The color image I to be encrypted RGB Decomposed into RGB three color channels I R , I G , I B , and generalized Arno...
Embodiment 3
[0141] Below in conjunction with specific accompanying drawing, the scheme in embodiment 1 and 2 is carried out feasibility verification, see the following description for details:
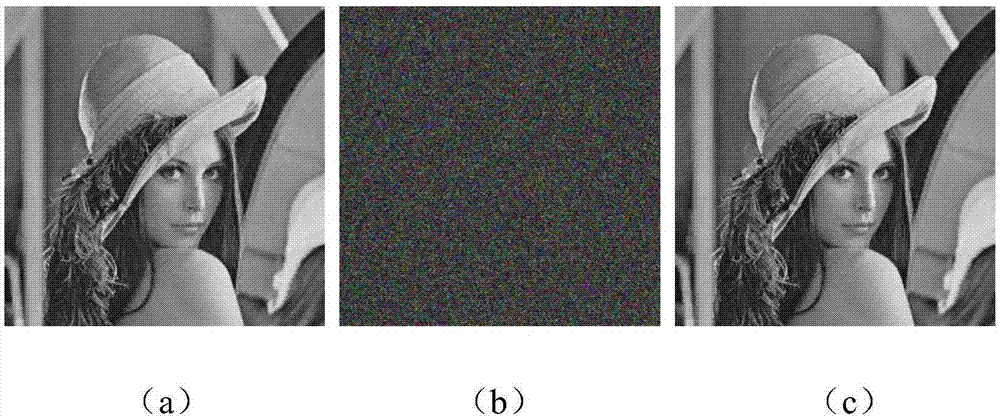
[0142] Adopt the image encryption that the present invention provides and concealment method to a color image (as figure 2 As shown in (a), after encryption, the obtained encrypted image is as follows figure 2 (b) shown. Depend on figure 2 (b) It can be seen that any information of the original image is hidden. It shows that the encryption of the image to be hidden by this system is successful.
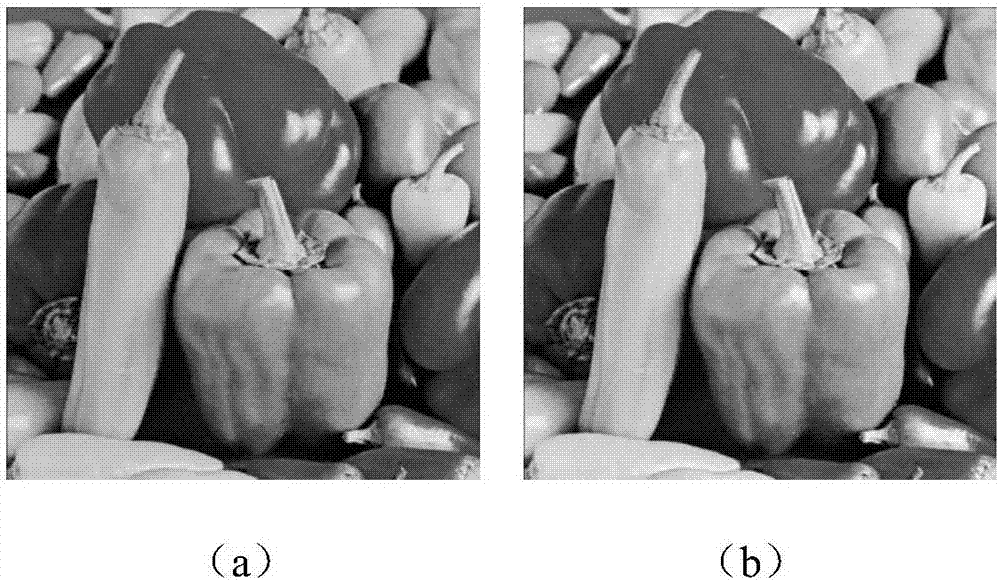
[0143] Adopt the image encryption that the present invention implements to provide and hiding method will figure 2 The encrypted image shown in (b) is embedded as image 3 In the carrier image shown in (a), get as image 3 Cover image containing the secret image shown in (b). Depend on image 3 (b) and 3(a), it can be seen that the human eye cannot distinguish the difference between the two im...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com