RFID system secret-key wireless generation method
A system key and key generation technology, applied in the field of radio frequency identification, which can solve problems such as security defects, hidden dangers, and inability to perform large-scale calculations.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
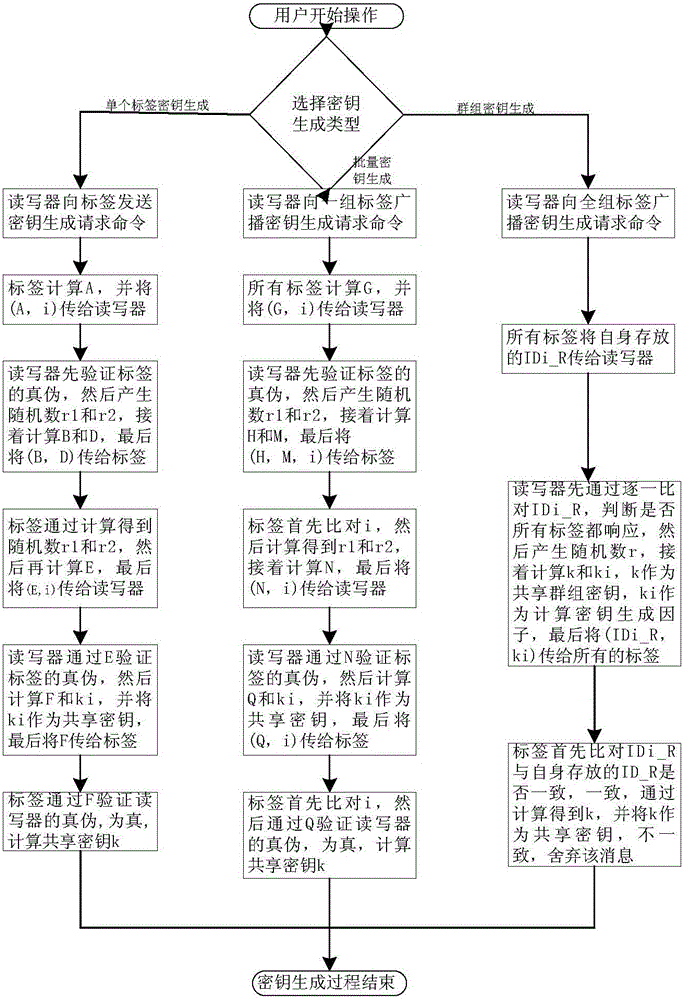
[0043] like figure 1 As shown, a method for wirelessly generating an RFID system key, the RFID system includes a label, a display screen, and a reader-writer, the display screen is connected to the reader-writer, and the reader-writer includes a background database for storing tags. The corresponding tag identifier ID.
[0044] Specifically include:
[0045] The reader / writer determines the key generation type; specifically, the key generation type button is displayed on the display screen, and the key generation type includes single label key generation, batch key generation and group key generation, the user selects the type, reads and writes The device determines the type of key generation;
[0046] According to different key generation types, a shared key is generated between the reader and tag.
[0047] The single tag key generation type specifically generates a shared key for a tag, and the specific process is as follows:
[0048] S1.1 The reader sends a key generati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com