A multiple certification method and system
An authentication method and authentication system technology, applied in the field of access control systems and security systems, can solve the problems of not significantly improving the security protection level of the system, wrong authentication, counterfeiting of fingerprint information, etc., and achieve both convenience, high complexity and strength. The effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
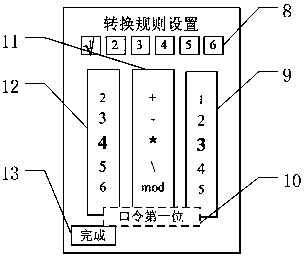
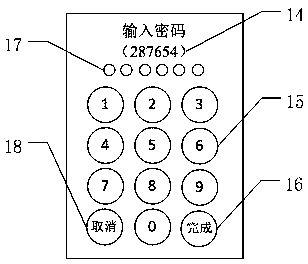
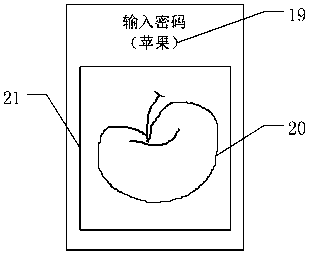
[0052] The following will be combined with the attached figure 1 The access control system in the invention is described. The authentication system according to the present invention is an authentication system that implements multiple authentications. It basically includes three main components: an authentication host, a user terminal, and an authentication execution device. The authentication host can perform authentication operations on the user terminal, and can communicate with The user terminal negotiates to determine the secret parameter information required for authentication, and stores preset shared information and qualified response information; the user terminal can generate random challenge information, and store the operation rules preset by the user, and receive The information input by the user communicates with the authentication host, and the authentication execution device receives the control information of the authentication host and performs corresponding...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com