One-time password certification system token resynchronization method based on event
A password authentication and resynchronization technology, applied in the field of computer and information security, can solve problems such as out-of-sync and remain unchanged, and achieve the effect of fast running speed, ensuring security, and simple calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The token resynchronization method of the event-based one-time password authentication system of the present invention has been fully and detailedly introduced above. The technical features and implementation methods of the present invention will be further described below in conjunction with the accompanying drawings.
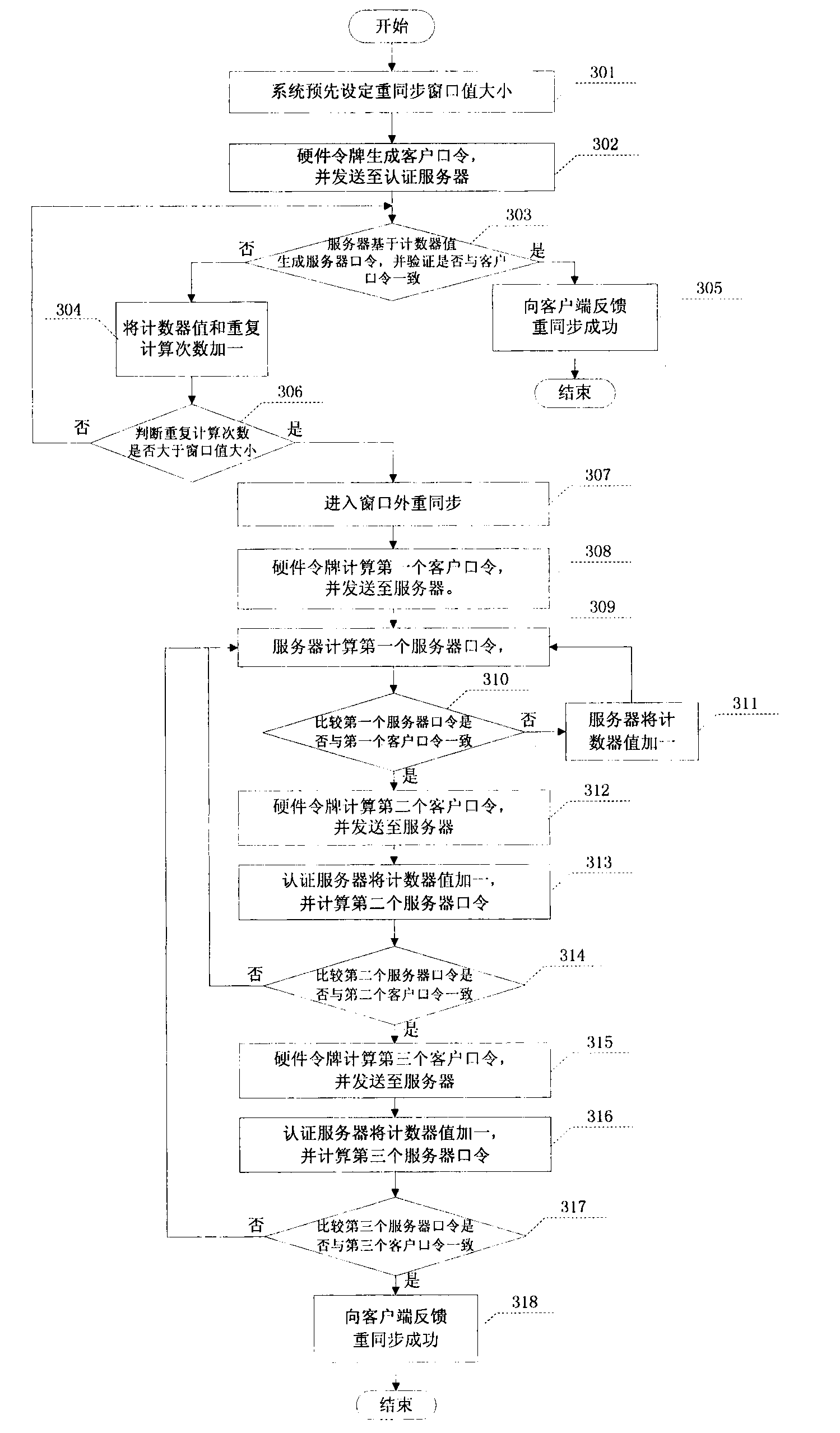
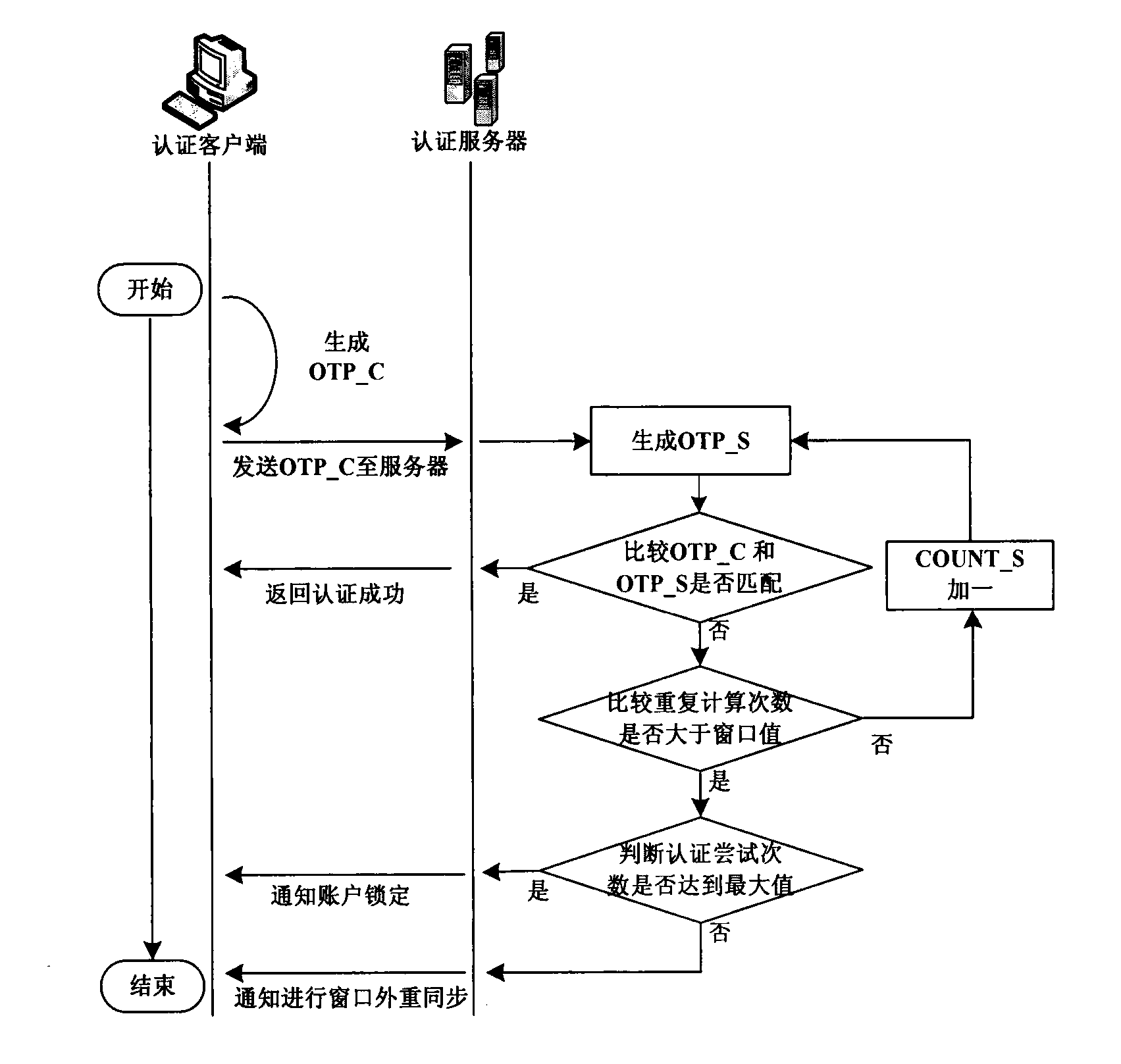
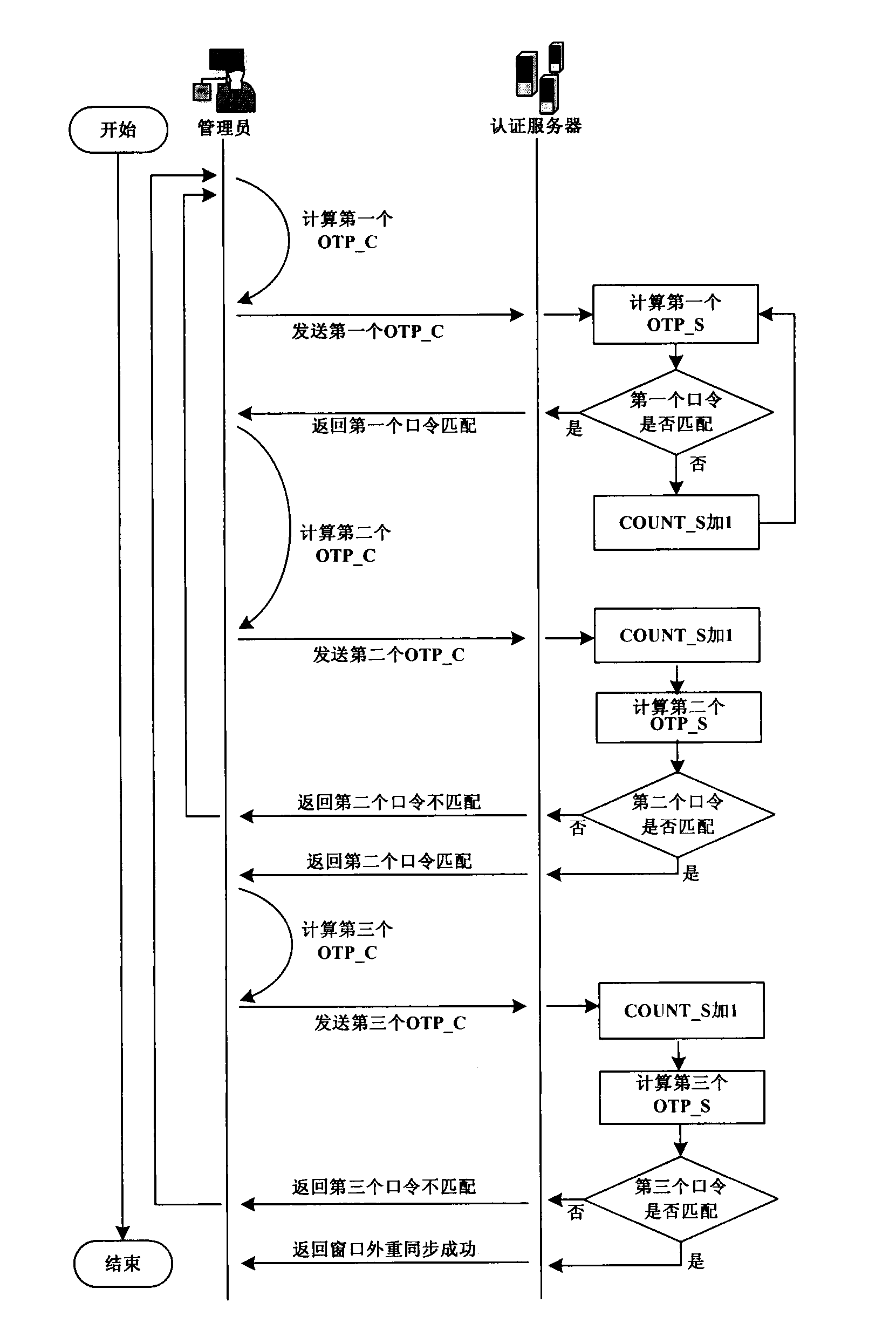
[0038] This implementation example provides a complete event-based one-time password authentication system token resynchronization method, see figure 1 , is a flowchart of the event-based one-time password authentication system token resynchronization method, specifically including:
[0039] Step 101, the system presets the resynchronization window size;
[0040] Step 102, the hardware token generates a client password and sends it to the authentication server;
[0041] Step 103, the authentication server receives the client password sent in step 102, and at the same time, generates a server password based on the counter value, and compares whether the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com