Image encryption method and device based on double-entropy source hyperchaotic system and storage medium
An encryption method and chaotic system technology, which can be used in secure communication through chaotic signals, transmission systems, digital transmission systems, etc., and can solve problems such as poor key sensitivity, insufficient key space, and cracking.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example ;
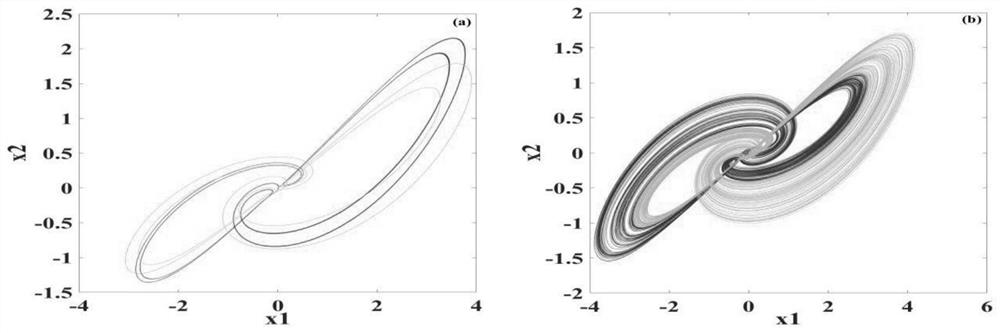
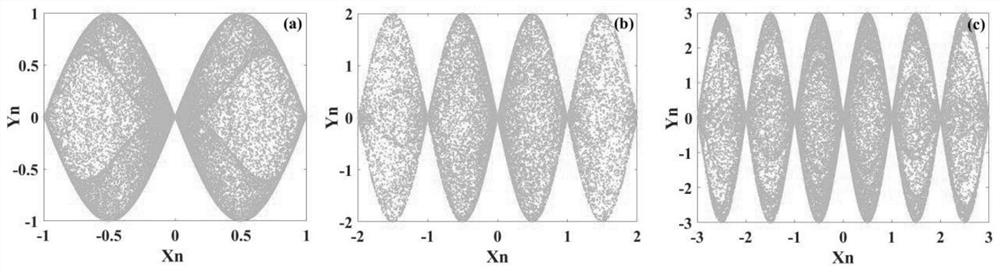
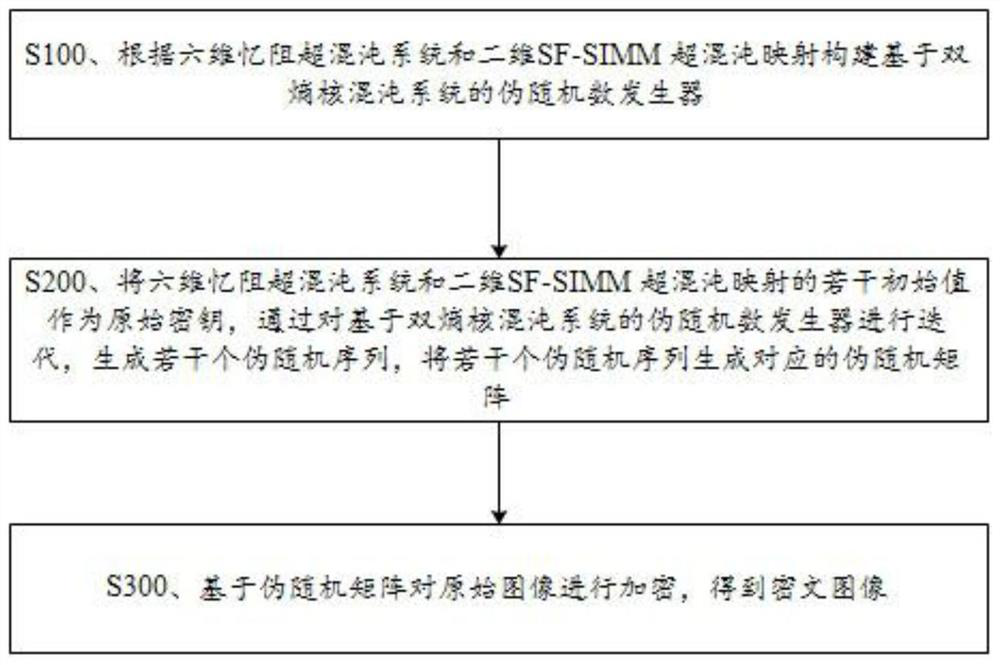
[0043] refer to image 3 , an embodiment of the present invention provides a kind of image encryption method based on double entropy source hyperchaotic system, and this method can realize under MATLAB environment, and method comprises the following steps:
[0044] S100. Construct a pseudo-random number generator based on a dual-entropy source chaotic system according to the six-dimensional memristive hyperchaotic system and the two-dimensional SF-SIMM hyperchaotic map.
[0045] S200. Generate several pseudo-random sequences by iterating the pseudo-random number generator based on the dual-entropy source chaotic system, wherein several initial values of the six-dimensional memristive hyperchaotic system and the two-dimensional SF-SIMM hyperchaotic map are used as the original key.
[0046] The initial value in this step refers to the initial conditions or system parameters of the six-dimensional continuous memristive hyperchaotic system and the two-dimensional discrete SF-S...
no. 2 example ;
[0052] refer to Figure 4 , as an implementable manner, step S400 in the first embodiment includes the following steps:
[0053] S401. Generate a first image by diffusing a plaintext image according to a corresponding pseudo-random matrix.
[0054] S402. Shuffle the first image into a second image according to the corresponding pseudo-random matrix.
[0055] S403. Diffusion forward the second image from the last pixel according to the corresponding pseudo-random matrix until the second image is diffused into a ciphertext image.
[0056] Of course, step S400 may also use a diffusion-scrambling encryption structure commonly used in this field. Compared with the existing diffusion-scrambling encryption structure, the method of this embodiment adopts the encryption structure of scrambling-diffusion-scrambling, which can make the spatial distribution and gray level distribution of image pixels more uniform, and improve the robustness of image encryption .
no. 3 example ;
[0058] refer to Figure 14 , provides a specific example of an image encryption method based on a dual-entropy source hyperchaotic system, the method includes the following steps:
[0059] S100. Construct a pseudo-random number generator based on a dual-entropy source chaotic system according to the six-dimensional memristive hyperchaotic system and the two-dimensional SF-SIMM hyperchaotic map.
[0060] S200. By iterating the pseudo-random number generator based on the dual-entropy source chaotic system, several pseudo-random sequences are generated, wherein some initial values of the six-dimensional memristive hyperchaotic system and the two-dimensional SF-SIMM hyperchaotic map, and The iterated transition value as the original key. Note that Figure 14 The DECHCS in The said pseudo-random number generator.
[0061] In this embodiment, (x 1 (0),x 2 (0),x 3 (0),x 4 (0),x 5 (0),x 6 (0), r 1 ,r 2 ,y 1 (0),y 2 (0))=(0.05,0,0.2,1,0,0.5,35,201,1,1) as the original ke...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com