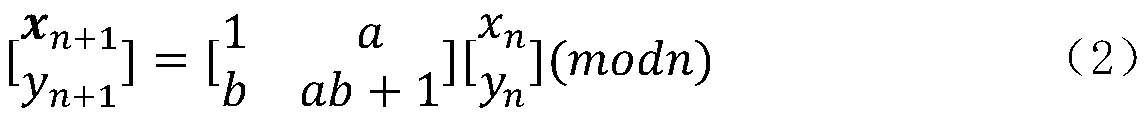Video encryption method incompatible with video coding based on chaotic cryptography theory
A technology of video coding and chaotic ciphers, which is applied in the direction of secure communication through chaotic signals, selective content distribution, digital transmission systems, etc., can solve problems such as inability to play, and achieve the effect of enhancing security and resisting violent attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
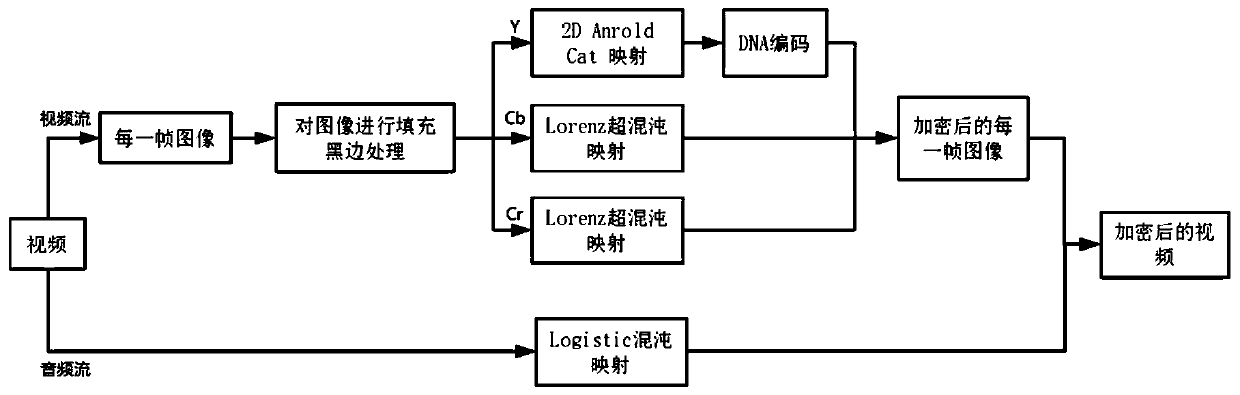
Image
Examples
Embodiment Construction
[0015] In order to better understand the present invention, some basic concepts are firstly explained.
[0016] 1. Logistic mapping:
[0017] Logistic mapping is a classic model for studying the behavior of complex systems such as dynamical systems, chaos, and fractals, and iterates repeatedly according to the following equation (1):
[0018] x(t+1)=μx(t)(1-x(t)) (1)
[0019] t is the iterative time step, in order to ensure that the x(t) obtained by any number of iterations is always in [0, 1], then μ∈[0,4].
[0020] 2. Arnold Cat mapping
[0021] In mathematics, the Arnold Cat map is named after Vladimir Arnold, who demonstrated its effect in the 1960s using images of cats, hence the name. The Arnold Cat transformation is used to shuffle the pixel value position of the color image, but cannot change the value of the image pixel. That is, the pixel position is transformed by Arnold Cat mapping, and the image is encrypted by scrambling. Equation (2) is used for image encry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com