A verification code generation method based on hidden graphics
A verification code and graphic technology, applied in the fields of digital data authentication, electronic digital data processing, program/content distribution protection, etc., can solve the problems of machine automatic identification and user identification contradiction, the verification code input is not convenient enough, etc., to achieve convenient identification and verification code and input verification code, reduce the difficulty of identification, the effect of easy identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0038] The present invention provides a verification code generation method based on implicit graphics,
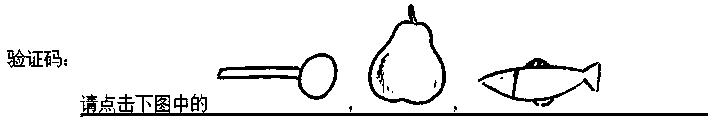
[0039] Step S1: if figure 1 As shown, the preset M large graphics, each of which contains N sub-graphics; the large graphic in this embodiment is a graphic from "Hidden Picture" from the Internet, and 13 sub-graphics are hidden in the figure, marked The part of is a subgraph.
[0040] Step S2: Carry out naming and individual graphic processing to these sub-graphics, wherein the naming method can use multiple languages, which can be Chinese or other languages, and the sub-graphics can also undergo various deformations. right figure 1 The 13 sub-graphics in the name and individual graphic processing, naming and individual graphic processing such as Figure 10 As shown:
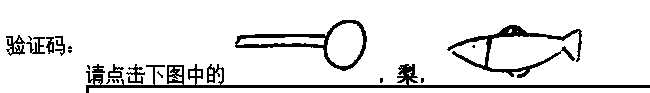
[0041] Step S3: Randomly select J graphics and corresponding K sub-graphics ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com